Author: Stelios Chatzistogias
Executive summary
Emotet is a notorious malware family that has evolved significantly over the years: from a simple banking trojan to a botnet to an infrastructure for content delivery.1 Infoblox has been monitoring Emotet and providing insights2,3,4,5,6 on its activity all along.
Emotet has been around since 2014.7 It survived its January 2021 takedown by law enforcement agencies from the Netherlands, UK, and US and from Germany, France, Lithuania, Canada, and Ukraine. During the takedown, Emotet was offline for 11 months.8
The frequency of Emotet-related malspam campaigns increased from January to May 2022 as the malware authors changed techniques to evade Microsoft’s increasing countermeasures on VBA Macro security.9 The Max Planck Institute for Plasma Physics was attacked on 12 June 2022,10 and recent reports put Emotet back at the top of the list of malware families with impact that spans the globe.11 Infoblox has been monitoring the increase in Emotet activity, and our insights are captured in this report.
Analysis
Emotet delivery vehicles
Since the 2021 takedown, a consistent feature of Emotet has been its use of email as a delivery vector. Microsoft Office documents have been the attachments of choice, and Excel files have been the most prevalent of these documents.
Since May 12, 2022, we have observed more than 60,000 malspam campaigns distributing 13 thousand file hashes.
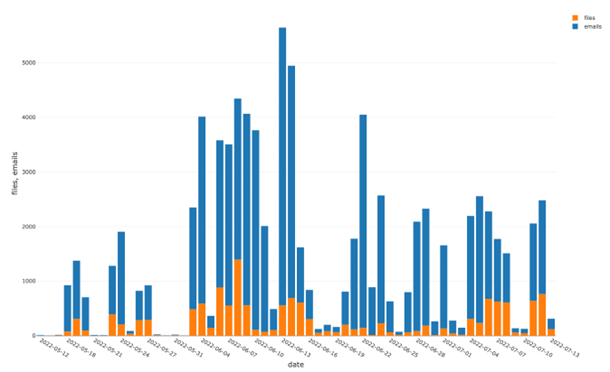
Figure 1: Distribution of Emotet’s unique email IDs and file hashes from 12 May to 13 July 2022
The campaigns share some characteristics. In particular, they use “RE:”, “FW:”, and other well-known, tried-and-true generic lures in the subject lines. They also use generic shipping- and invoice-related keywords, presumably to make the messages appear legitimate. Some subject lines contain Ukraine-themed lures, which make the emails appear up-to-date with important events happening in the world. Figure 2 shows the subject lines and the most common themes used across the malspam campaigns spreading Emotet.
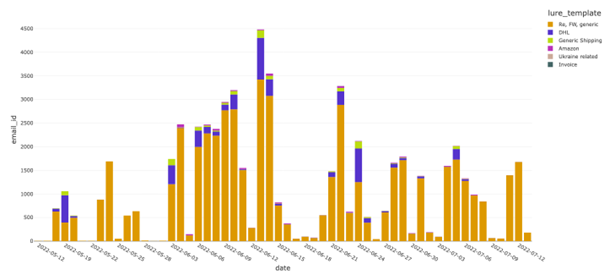
Figure 2: Distribution of subject lines across malspam email campaigns
Figure 2 illustrates that the primary non-generic lures used by Emotet aim to trick recipients into believing that the messages relate to Amazon or DHL deliveries. This technique has been used by attackers for several years and is not exclusive to Emotet. The next part of the analysis focuses on files attached to the emails.
File attachments analysis
The subject and body of an email that delivers Emotet are designed to trick a recipient into opening the attachment. Once opened, the attachment triggers malicious XLM macros and starts the chain of an Emotet infection.
Most email attachments contain a single Microsoft Excel file with XLM macros that include a link; clicking the link fetches the Emotet payload DLL. However, some attachments are zip archives. Figure 3 shows the distribution of all file types that Emotet used during our investigation. The graph clearly shows that Excel documents are most prevalent, followed by zip archives. In all cases where the attachment is a zip archive, the contents are an Excel document. One possible reason Microsoft Excel files are the preferred attachment type is that the corporate world moves slowly, and the patches or Microsoft updates are deployed very slowly, and this buys attackers additional time to infect the victims’ computers. The attackers continue to use these infection techniques that capitalize on corporate users’ tendencies to rely on outdated versions of Microsoft Office or to completely disable protection.12
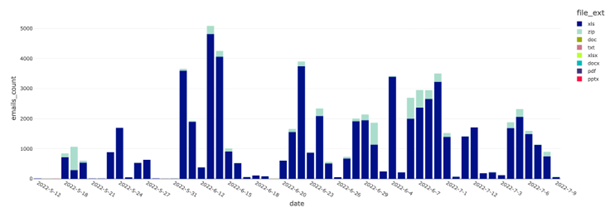
Figure 3: Distribution of Emotet-related emails per file type over time
The file attachments deploy well-known techniques13,14 for bypassing Windows protections and downloading the Emotet DLL file. In January 2022, in an effort to protect users against threats that leverage this technique, Microsoft released its latest advisory on disabling Excel XLM macros.15 However, because this will always remain a configurable feature, Infoblox continues to observe high volumes of malspam with macro-enabled attachments.
Malicious payloads domain distribution
To understand where the threat actors store the malicious DLL payloads, we analyzed approximately 13,000 attachments from Emotet emails; in addition, we extracted not only the URL pointing to the malicious Emotet DLL payload but also the hosting domains. We discovered that most of the domains being used to host the Emotet DLL payloads are compromised websites that are either poorly developed or badly maintained, and as such, provide a soft target for the attackers. To test this, we used Infoblox’s patent-pending InfoRanks16 algorithms, which rank websites according to how frequently they are queried by Infoblox customers. In this case, the ranking indicates that the more popular or highly ranked a website is, the greater the likelihood is that the user is navigating to a legitimate but infected or compromised domain, rather than a domain owned by the threat actor.
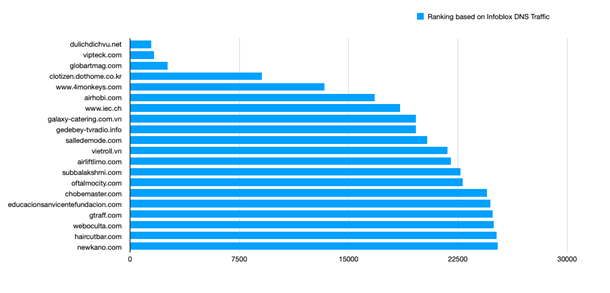
Figure 5: Most popular compromised websites (qnames) hosting or having hosted Emotet DLLs in the past four months, based on Infoblox customer traffic
Our research also highlights the importance of the longevity of a hosting domain. By evaluating the first and last times a domain is referenced in the Emotet email attachments, we can get a sense of the average period of time a compromised site is used by the Emotet actors.
Figure 6 shows the top 20 compromised domains. The score was determined from the number of compromised domains names extracted from Emotet-related file attachments.
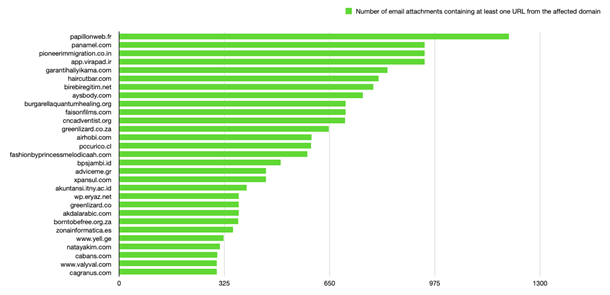
Figure 6: Top 20 compromised domains whose names were extracted from Emotet-related email file attachments
None of the top domains hosting the Emotet DLL payloads were newly registered. The following table displays some key statistics that can offer insights into why attackers consider compromised domains to be a preferable vector for distributing malware. The “Count of malicious file attachments” column shows the number of different files that used the same qname embedded in the XLMacro code for fetching the Emotet payload. The “Days used in Emotet campaigns” column shows the observed usage, in days, of the compromised domains. Essentially, this is the difference between the first and last days on which we spotted an Emotet-related Excel file with the specific qname embedded as part of the XLMacro code. Last but not least, the domain age is the number of days from the creation date of the specific SLD up to the day of our analysis.
| qname | Count of malicious file attachments | Days used in Emotet campaigns | Domain age |
| papillonweb[.]fr | 1204 | 26 days | 3012 days |
| www[.]pioneerimmigration[.]co[.]in | 944 | 10 days | 682 days |
| panamel[.]com | 944 | 10 days | 5091 days |
| app[.]virapad[.]ir | 943 | 2 days | – |
| www[.]garantihaliyikama[.]com | 829 | 13 days | 750 days |
| haircutbar[.]com | 801 | 11 days | 4570 days |
| www[.]birebiregitim[.]net | 785 | 11 days | 1453 days |
| aysbody[.]com | 752 | 20 days | 628 days |
| burgarellaquantumhealing[.]org | 699 | 14 days | 2056 days |
| faisonfilms[.]com | 699 | 14 days | 1509 days |
| cncadventist[.]org | 698 | 14 days | 2291 days |
| greenlizard[.]co[.]za | 648 | 12 days | 6677 days |
| airhobi[.]com | 594 | 7 days | 841 days |
| pccurico[.]cl | 592 | 6 days | 4356 days |
| fashionbyprincessmelodicaah[.]com | 581 | 0 days | 815 days |
| bpsjambi[.]id | 498 | 36 days | 413 days |
| xpansul[.]com | 454 | 13 days | 7590 days |
| adviceme[.]gr | 454 | 13 days | – |
| akuntansi[.]itny[.]ac[.]id | 393 | 6 days | 1270 days |
| wp[.]eryaz[.]net | 370 | 32 days | 6951 days |
Table 1: Most frequently used qnames in malspam file attachments downloading Emotet
Analysis of C&C infrastructure
After the Emotet DLL payload is executed, the command and control (C&C) communication is initiated. Emotet C&Cs consist of IP addresses accompanied by specific ports. Here, we analyze the C&C IPs to better understand the Emotet botnet and infrastructure. During the course of our analysis, we extracted and reviewed the C&C IPs from approximately 200 Emotet DLLs.
Emotet’s global footprint
The C&C IP distribution is depicted on the world maps shown in Figures 7 and 8. We used data from the Feodo Tracker17 to compare the current Emotet C&Cs to the pre-takedown Emotet C&Cs. The map in Figure 7 shows the distribution of C&C IPs per country before the takedown. Comparison of the maps in Figures 7 and 8 reveals that Emotet C&Cs continue to be hosted primarily in the U.S., but there is also a strong presence of Emotet in Europe. For example, the number of C&C server hosts has increased in Germany and France. The maps also show that the United States, Germany, France, India, and Indonesia are currently the countries of choice for hosting Emotet C&C infrastructure.
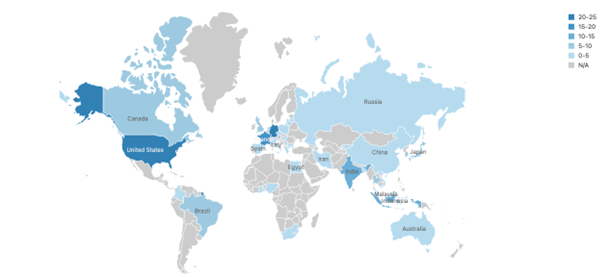
Figure 7: Post-takedown distribution of Emotet C&C servers
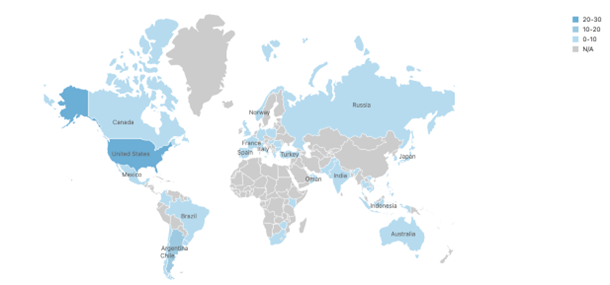
Figure 8: Pre-takedown distribution of Emotet C&C servers
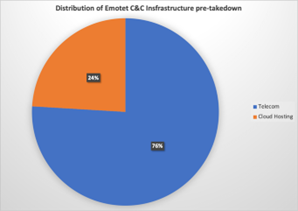
Our analysis indicates that the C&C IPs are part of the virtual private cloud (VPC) infrastructure, which suggests that the current group operating Emotet chooses to pay for this service. In particular, we have observed that the use of Digital Ocean amongst other VPC providers has increased considerably. Before the takedown, most of the hosting providers used were telecommunications providers. Since the takedown, there has been an increase in the number of hosting providers that offer VPC solutions, which provide more privacy and make it more difficult for law enforcement agencies to conduct takedowns. Figures 9 and 10 show the significant shift from Telecom-related hosting infrastructure to cloud hosting infrastructure. Nevertheless, there is still 16% of the infrastructure hosted in telcos. Some company names that stand out are Korea Telecom, 1&1 AG, PT Telkom Indonesia and SK Broadband.
 |
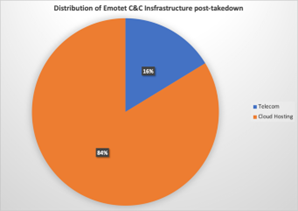 |
| Figure 9: Ratio of telecommunications vs hosting provider companies and organizations hosting Emotet C&C servers before the takedown | Figure 10: Ratio of telecommunications vs hosting provider companies and organizations hosting Emotet C&C servers after the takedown |
Prevention and mitigation
Despite its high-profile takedown in April 2021, Emotet remains active. In addition, our analysis indicates that the actors behind Emotet have made some attempts to protect the network from further takedowns. Perhaps unsurprisingly, the use of compromised websites and of email as a delivery vector has persisted, and this has enabled us to reliably identify and track Emotet’s activity. Our view of the threat landscape affords a detailed understanding of not only the current prevalence of Emotet in malspam but also of the location and services used in its infrastructure.
As we continue to research and monitor Emotet’s behavior, we will provide protection by denying access to the compromised domains used to host the Emotet payload, and we will offer vital, actionable intelligence on Emotet’s C&C infrastructure.
We recommend the following actions for protection from this kind of an attack:
- To mitigate the risk of infection from known threats, keep security software up to date and patched.
- Conduct security awareness training in the organization. It is important for everyone to be up to date with the latest techniques used by attackers to trick users who receive malicious emails.
- Enhance network perimeter security. 99% of successful attacks involve some type of network communication. Having the right tools in place can help identify and minimize the impact of a threat like Emotet before they cause damage.
Indicators of compromise
The table below provides a sample list of the IOCs relevant to our recent findings. The complete list as of the time of this paper is found in our GitHub repository18.
| Indicator | Type |
| www[.]cicerosd[.]com | Emotet payload DLL download domain |
| chainandpyle[.]com | Emotet payload DLL download domain |
| www[.]visionsfantastic[.]com | Emotet payload DLL download domain |
| ent[.]draftserver[.]com | Emotet payload DLL download domain |
| www[.]evosp[.]com[.]br | Emotet payload DLL download domain |
| www[.]clinicaportalpsicologia[.]com[.]br | Emotet payload DLL download domain |
| greycoconut[.]com | Emotet payload DLL download domain |
| harleyqueretaro[.]com | Emotet payload DLL download domain |
| drviniciusterra[.]com[.]br | Emotet payload DLL download domain |
| dscaluya[.]6te[.]net | Emotet payload DLL download domain |
| www[.]concivilpa[.]com[.]py | Emotet payload DLL download domain |
| helmprecision[.]com | Emotet payload DLL download domain |
| www[.]megakonferans[.]com | Emotet payload DLL download domain |
| disperindag[.]garutkab[.]go[.]id | Emotet payload DLL download domain |
| www[.]ergbox[.]com | Emotet payload DLL download domain |
| blessingsource[.]com | Emotet payload DLL download domain |
| deadcode200[.]c1[.]biz | Emotet payload DLL download domain |
| cs14productions[.]com | Emotet payload DLL download domain |
| djunreal[.]co[.]uk | Emotet payload DLL download domain |
| fisika[.]mipa[.]uns[.]ac[.]id | Emotet payload DLL download domain |
| grouprobust[.]com | Emotet payload DLL download domain |
| jimlowry[.]com | Emotet payload DLL download domain |
| balticcontrolbd[.]com | Emotet payload DLL download domain |
| www[.]druck-grafik[.]at | Emotet payload DLL download domain |
| dl[.]choobingroup[.]ir | Emotet payload DLL download domain |
| www[.]dl5[.]zahra-media[.]ir | Emotet payload DLL download domain |
| astrogurusunilbarmola[.]com | Emotet payload DLL download domain |
| brittknight[.]com | Emotet payload DLL download domain |
| www[.]hayalkatibi[.]com | Emotet payload DLL download domain |
| wmwifbajxxbcxmucxmlc[.]com | Emotet payload DLL download domain |
| kevinley[.]com | Emotet payload DLL download domain |
| appyhorsey[.]com | Emotet payload DLL download domain |
| www[.]graduate[.]cmru[.]ac[.]th | Emotet payload DLL download domain |
| www[.]lakor[.]ch | Emotet payload DLL download domain |
| erp[.]pinaken[.]com | Emotet payload DLL download domain |
| corporateissolutions[.]com | Emotet payload DLL download domain |
| perpustekim[.]untirta[.]ac[.]id | Emotet payload DLL download domain |
| iciee[.]untirta[.]ac[.]id | Emotet payload DLL download domain |
| ikatemia[.]untirta[.]ac[.]id | Emotet payload DLL download domain |
| tm[.]gamester[.]com[.]tr | Emotet payload DLL download domain |
| dencker[.]info | Emotet payload DLL download domain |
| www[.]escueladecinemza[.]com[.]ar | Emotet payload DLL download domain |
| escueladecinemza[.]com[.]ar | Emotet payload DLL download domain |
| www[.]mobiles-photostudio[.]com | Emotet payload DLL download domain |
| iprd[.]net[.]phtemp[.]com | Emotet payload DLL download domain |
| charmslovespells[.]com | Emotet payload DLL download domain |
| ewingconsulting[.]com | Emotet payload DLL download domain |
| francite[.]net | Emotet payload DLL download domain |
| educacionsanvicentefundacion[.]com | Emotet payload DLL download domain |
| clotizen[.]dothome[.]co[.]kr | Emotet payload DLL download domain |
| gmhealthcare[.]dothome[.]co[.]kr | Emotet payload DLL download domain |
| kwinglobal[.]dothome[.]co[.]kr | Emotet payload DLL download domain |
| withvac001[.]dothome[.]co[.]kr | Emotet payload DLL download domain |
| onepieceark[.]dothome[.]co[.]kr | Emotet payload DLL download domain |
| www[.]zvdesign[.]info | Emotet payload DLL download domain |
| natdemo[.]natrixsoftware[.]com | Emotet payload DLL download domain |
| www[.]fcstradesolutions[.]com | Emotet payload DLL download domain |
| demo-re-usables[.]inertiasoft[.]net | Emotet payload DLL download domain |
| www[.]guedala[.]com[.]br | Emotet payload DLL download domain |
| www[.]berekethaber[.]com | Emotet payload DLL download domain |
| bruidsfotografie-breda[.]nl | Emotet payload DLL download domain |
| fontecmobile[.]com | Emotet payload DLL download domain |
| document[.]vpservice-online[.]com | Emotet payload DLL download domain |
| atperson[.]com | Emotet payload DLL download domain |
| frascona[.]com[.]ar | Emotet payload DLL download domain |
| cashmailsystem[.]com | Emotet payload DLL download domain |
| www[.]clasite[.]com | Emotet payload DLL download domain |
| kairaliagencies[.]com | Emotet payload DLL download domain |
| gedebey-tvradio[.]info | Emotet payload DLL download domain |
| decorusfinancial[.]com | Emotet payload DLL download domain |
| zachboyle[.]com | Emotet payload DLL download domain |
| www[.]boraintercambios[.]com[.]br | Emotet payload DLL download domain |
| peicovich[.]com | Emotet payload DLL download domain |
| www[.]federation-sardaniste[.]fr | Emotet payload DLL download domain |
| weboculta[.]com | Emotet payload DLL download domain |
| earthmach[.]co[.]za | Emotet payload DLL download domain |
| www[.]drcno[.]sk | Emotet payload DLL download domain |
| www[.]forensisbilisim[.]com | Emotet payload DLL download domain |
| www[.]fullwiz[.]com[.]br | Emotet payload DLL download domain |
| evashopping[.]thietkewebsitechuanseo[.]com | Emotet payload DLL download domain |
| travel[.]pkn2[.]go[.]th | Emotet payload DLL download domain |
| www[.]anglicanjoburg[.]org[.]za | Emotet payload DLL download domain |
| www[.]joburg[.]org[.]za | Emotet payload DLL download domain |
| mtc[.]joburg[.]org[.]za | Emotet payload DLL download domain |
| dotcompany[.]com[.]br | Emotet payload DLL download domain |
| comecebem[.]com | Emotet payload DLL download domain |
| collabsolutions[.]co[.]za | Emotet payload DLL download domain |
| borntobefree[.]org[.]za | Emotet payload DLL download domain |
| wp[.]eryaz[.]net | Emotet payload DLL download domain |
| akuntansi[.]itny[.]ac[.]id | Emotet payload DLL download domain |
| nycom[.]narasoft[.]com | Emotet payload DLL download domain |
| cupsolution[.]com | Emotet payload DLL download domain |
| wordpress[.]agrupem[.]com | Emotet payload DLL download domain |
| www[.]olsav[.]sk | Emotet payload DLL download domain |
| www[.]aseguradosaldia[.]com | Emotet payload DLL download domain |
| www[.]nomatenalmono[.]org | Emotet payload DLL download domain |
| www[.]diarioaldia[.]com[.]ar | Emotet payload DLL download domain |
| ftp[.]yuecmr[.]org | Emotet payload DLL download domain |
| contabilidadeplenus[.]com[.]br | Emotet payload DLL download domain |
| fashionbyprincessmelodicaah[.]com | Emotet payload DLL download domain |
| chaledooleo[.]com[.]br | Emotet payload DLL download domain |
| greenlizard[.]co[.]za | Emotet payload DLL download domain |
| nellydwiputri[.]co[.]id | Emotet payload DLL download domain |
| www[.]llev[.]com[.]br | Emotet payload DLL download domain |
| starluckycentre[.]com | Emotet payload DLL download domain |
| 3dstudioa[.]com[.]br | Emotet payload DLL download domain |
| survei[.]absensi[.]net | Emotet payload DLL download domain |
| haircutbar[.]com | Emotet payload DLL download domain |
| www[.]garantihaliyikama[.]com | Emotet payload DLL download domain |
| dusangerzicgera[.]com | Emotet payload DLL download domain |
| ybp[.]rpmediateam[.]com | Emotet payload DLL download domain |
| www[.]controlnetworks[.]com[.]au | Emotet payload DLL download domain |
| app[.]virapad[.]ir | Emotet payload DLL download domain |
| 54[.]37[.]106[.]167 | Emotet C&C IP |
| 78[.]47[.]204[.]80 | Emotet C&C IP |
| 202[.]28[.]34[.]99 | Emotet C&C IP |
| 210[.]57[.]209[.]142 | Emotet C&C IP |
| 118[.]98[.]72[.]86 | Emotet C&C IP |
| 37[.]44[.]244[.]177 | Emotet C&C IP |
| 196[.]44[.]98[.]190 | Emotet C&C IP |
| 195[.]77[.]239[.]39 | Emotet C&C IP |
| 139[.]196[.]72[.]155 | Emotet C&C IP |
| 54[.]37[.]228[.]122 | Emotet C&C IP |
| 62[.]171[.]178[.]147 | Emotet C&C IP |
| 202[.]134[.]4[.]210 | Emotet C&C IP |
| 85[.]214[.]67[.]203 | Emotet C&C IP |
| 93[.]104[.]209[.]107 | Emotet C&C IP |
| 88[.]217[.]172[.]165 | Emotet C&C IP |
| 103[.]41[.]204[.]169 | Emotet C&C IP |
| 87[.]106[.]97[.]83 | Emotet C&C IP |
| 85[.]25[.]120[.]45 | Emotet C&C IP |
| 202[.]29[.]239[.]162 | Emotet C&C IP |
| 36[.]67[.]23[.]59 | Emotet C&C IP |
| 175[.]126[.]176[.]79 | Emotet C&C IP |
| 103[.]56[.]149[.]105 | Emotet C&C IP |
| 178[.]62[.]112[.]199 | Emotet C&C IP |
| 104[.]248[.]225[.]227 | Emotet C&C IP |
| 188[.]225[.]32[.]231 | Emotet C&C IP |
| 103[.]85[.]95[.]4 | Emotet C&C IP |
| 104[.]244[.]79[.]94 | Emotet C&C IP |
| 157[.]230[.]99[.]206 | Emotet C&C IP |
| 103[.]126[.]216[.]86 | Emotet C&C IP |
| 157[.]245[.]111[.]0 | Emotet C&C IP |
Endnotes
- https://malpedia.caad.fkie.fraunhofer.de/details/win.emotet
- https://www.infoblox.com/wp-content/uploads/threat-intelligence-report-how-emotet-stole-christmas.pdf
- https://blogs.infoblox.com/cyber-threat-intelligence/cyber-campaign-briefs/italian-emotet-campaign/
- https://www.infoblox.com/wp-content/uploads/threat-intelligence-report-emotet-gets-political.pdf
- https://www.infoblox.com/wp-content/uploads/threat-intelligence-report-return-of-emotet.pdf
- https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–101
- https://heimdalsecurity.com/blog/emotet-malware-history/
- https://threatpost.com/emotet-back-new-tricks/179410/
- https://www.welivesecurity.com/2022/06/16/how-emotet-is-changing-tactics-microsoft-tightening-office-macro-security/
- https://www.mpg.de/18941175/emotet-malware-max-planck-institute-plasma-physics
- https://www.theregister.com/2022/04/21/emotet-resurgence-email/
- https://duo.com/decipher/emotet-office-macros-abuse-continues-despite-microsoft-protections
- https://duo.com/decipher/emotet-office-macros-abuse-continues-despite-microsoft-protections
- https://blogs.vmware.com/security/2022/02/emotet-is-not-dead-yet-part-2.html
- https://techcommunity.microsoft.com/t5/excel-blog/excel-4-0-xlm-macros-now-restricted-by-default-for-customer/ba-p/3057905
- https://blogs.infoblox.com/security/inforanks-infoblox-rankings-give-insights-into-the-stability-of-a-domains-popularity/
- https://feodotracker.abuse.ch/
- https://github.com/infobloxopen/threat-intelligence/tree/main/cta_indicators








