Author: Christopher Kim
1. Overview
Distributed Denial-of-Service (DDoS) is a cyber attack that causes mass-disruption of services. From 1996 (when first reports about DDoS attacks emerged)1 to 2010, threat actors primarily used DDoS for promoting themselves or political agendas, and for encouraging social change; in recent years, the financial motive has been more prevalent, and more DDoS activities have made extortion a major part of their strategy. In addition, prior to 2020, DDoS actors usually sent empty threats and did not follow up with attacks; since the second half of 2020, and throughout 2021, actors have made good on their threats and have followed up with attacks more frequently. Although threat actors have monetized DDoS threats or attacks in the past, we believe that the popularization of cryptocurrency, willingness of some organizations to meet extortion demands (as was seen in the ransomware attack on Colonial Pipeline2), and the affordability of DDoS-as-a-service (DDoSaaS) have encouraged threat actors to pursue these kinds of activities.
In nearly all recent attacks, the attackers have named themselves after well-known advanced persistent threat (APT) actors. Since 2014, companies across multiple industry verticals have received DDoS extortion letters from DDoS actors who have attempted to portray themselves as Cozy Bear, DDoS for Bitcoin (DD4BC), Sednit, Fancy Bear, Armada Collective, Lazarus, or Lazarus Group. The cyber intelligence community has not found a direct connection between the DDoS actors and the APT actors whose names they have borrowed. Usually, APT actors target specific kinds of entities according to a common characteristic, such as a geo-location or a business type; however, targets of the DDoS extortion campaigns are widely distributed across the globe and belong to various industries. Many researchers have speculated that the DDoS actors identify themselves as well-known APT actors to build credibility and increase the probability of extorting money from their targets.
The actors paused their campaigns for one month in spring 2020 but returned with new APT group names and changed tactics, techniques, and procedures (TTPs). Since, the attacks have been more frequent and the extortion emails have come from dynamic addresses unique to the target organizations, not from static addresses that include the actors’ self-assumed aliases. In addition, the actors have adjusted the bitcoin demands in response to the cryptocurrency’s price fluctuations.
To perform a DDoS attack with enough power to disrupt enterprise-level services, threat actors must use large botnets, which they can rent or develop. In addition, many actors use multiple attack vectors in one large assault; this makes mitigation difficult because no single DDoS protection system can resolve all types of attack methods. Over the past several years, actors who have successfully monetized DDoS campaigns via extortion have used the following DDoS attack vectors most often: DNS flood, DNS amplification, ARMS amplification, SNMP reflection, SYN flood, GRE flood, WS-discovery amplification, CLDAP reflection, TFTP amplification, NTP amplification, WordPress XML-RPC amplification, simple service discovery protocol (SSDP), and portmapper amplification.
So far in 2021, DDoS extortion attacks have been almost evenly distributed across various industries: energy, financial, insurance, manufacturing, public utilities, retail sectors, travel and hospitality, retail and e-commerce, high-tech and software, consumer packaged goods, and internet service providers.3 DDoS is one of the costliest cyber threats to mitigate, because it directly affects the availability of services crucial to business operations. Bulletproof’s 2019 annual cybersecurity report4 indicated that a DoS or DDoS attack could cost a small company up to $120,000 and an enterprise up to $2 million in damages.
2. Categories of DDos attacks
At a high level, DDoS attacks can be categorized as volumetric, application-layer, and protocol-based, and they typically target layers 3, 4, and 7 in the Open Systems Interconnection (OSI) model.5
- Volumetric DDoS attacks abuse mostly layer 7 protocols of the OSI model, especially DNS and network time protocol (NTP), and they attempt to reduce a network’s bandwidth capacity by flooding the network with high amounts of traffic or with request packets. Some volumetric DDoS attacks are large enough to max out the bandwidth capacity of upstream internet service providers (ISP) or datacenters, and this prevents legitimate traffic from connecting to websites.Because generating a high number of requests is relatively easy, volumetric attacks are popular among DDoS actors. The requests are small, but they command a large response to the victim’s server, such as a DNS resolver.
- Like volumetric attacks, application-layer DDoS attacks target mostly layer 7 of the OSI model. Unlike volumetric attacks, they try to exhaust server resources by attacking applications’ backend processes that are computationally expensive. In addition, they generate less traffic and use less total bandwidth but can inflict at least as much damage. The two most common web server requests in an application-layer DDoS attack are HTTP GET and HTTP POST. To direct their requests, the attackers that operate an application-layer attack must have deep knowledge of the application and its supporting endpoints.Application-layer attacks are effective because the server expends considerably more resources in responding to requests than the client does in generating them. If the conditions are right—for example, if the target application is not optimized or cannot manage CPU- and RAM-intensive operations due to low resource capacity—some attacks can disable web applications by using just one machine.
- Protocol-based DDoS attacks target weaknesses in protocols in layers 3 and 4. These kinds of attacks are difficult to mitigate because the majority of online devices use internet communication protocols. Some protocols are complex and difficult to reengineer for resolving new vulnerabilities. Additionally, even if vendors release security patches relatively quickly, businesses might take a long time to deploy them, because the patches are often incompatible with existing systems.One of the oldest (first detected in 2014) and most common types of protocol-based DDoS attacks is a TCP synchronization (SYN) flood. This attack occurs when a DDoS actor sends a large number of SYN packets to the victim’s server; these packets often contain a modified source address, to hide the sender’s identity. The victim’s server responds to each of the connection requests and leaves a port open to receive the final ACK packet. However, the actors do not send the ACK packet but continue to send additional SYN packets until the server exhausts all available ports. This prevents the server from functioning normally or even processing legitimate requests.6,7
3. Attack chains
DDoS extortion campaigns typically follow one of two kinds of attack chains (the Appendix includes attack chain diagrams):
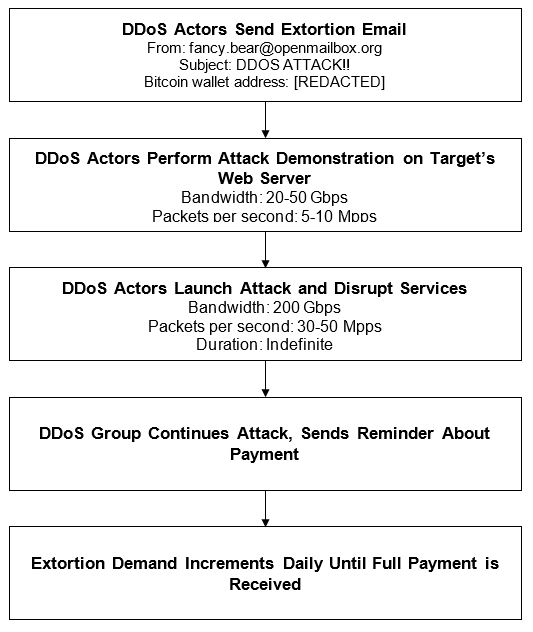
- The actors start with a DDoS demonstration: a show of force and an attempt to prove that the threat is real. They target a specific resource that belongs to the organization’s web service or network infrastructure. The demonstration is large enough to slow down the organization’s services but not large enough to knock them offline.After or during the demonstration, the actors send an extortion email, where they threaten to launch a larger DDoS attack if the organization does not make the specified bitcoin payment to the group’s cryptocurrency wallet. If the organization does not make the payment by the deadline, the actors follow up with the main DDoS attack and increase the extortion amount every day after the due date, until they receive the full payment.
- The actors send the extortion email before the attack. The email contains the extortion demand, bitcoin wallet address, deadline, the attack’s capacity, and other details. The group might also use the email to boast about their ability to send several terabytes’ worth of traffic packets per second. However, in some cases, organizations reported that the threats were bluffs and that follow-up attacks never occurred.8, 9, 10
4. Mitigation
When planning for DDoS mitigation, organizations should understand not only the details of their business obligations to keep services up and available, but also the amount of temporary service disruption they and their customers can tolerate. The Australian Cyber Security Centre provides some basic guidance that organizations can take to reduce the likelihood and potential impact of a DDoS attack:
- Determine which functionality is truly critical to the operations of an organization. Create all backups necessary to keep it running despite the attack, and allocate enough resources (if necessary, by moving them from non-critical functionality) to maintain it during the attack and, ultimately, to restore it once the attack has been managed.
- With service providers, discuss the details of DDoS prevention and mitigation strategies, namely:
- the capacity to withstand DDoS attacks
- any costs likely to be incurred by customers
- thresholds for notifying customers or for turning off their online services during DDoS attacks
- pre-approved actions that can be taken during DDoS attacks
- arrangements made with upstream (for example, Tier 2) service providers to block malicious traffic as far upstream as possible
- Protect organization’s domain names by using registrar locking and by confirming that the domain registration details are correct.
- Ensure that customers maintain details of their service providers’ 24×7 contacts and that service providers maintain details of their customers’ 24×7 contacts.
- Establish additional out-of-band contact details—for example, mobile phone numbers and non-organizational email addresses—that service providers would use when normal communication channels fail.
- Implement availability monitoring with real-time alerting, to detect DDoS attacks and measure their impact.
- Prepare a static version of a website that requires minimal processing and bandwidth to facilitate continuity of service during DDoS attacks.
- Use cloud-based hosting from a major cloud service provider—preferably from several major cloud service providers, to ensure redundancy—with high-bandwidth content-delivery networks that cache non-dynamic websites. If using a content-delivery network, avoid disclosing the IP address of the web server that is under the organization’s control (referred to as the origin web server), and use a firewall to ensure that only the content-delivery network can access this web server.
- Use a DDoS mitigation service, because it offers a variety of in-depth defense approaches that can be implemented in the infrastructure and application layers.
Effective DDoS mitigation postures will take into account all requirements and constraints of a business, and they will implement controls focused on cloud infrastructure, on-prem systems, or a hybrid of thereof. As a general rule, the more complex the mitigation system, the more likely it is to fail due to misconfigurations or failed integration points. Organizations that are considering DDoS protection for the first time should start with simple systems that can be monitored and refined.
DDoS attacks, just as other cyber security threats, are constantly evolving in complexity and effectiveness; therefore, cyber defenders must never stop improving their TTPs and defenses against DDos attacks. This applies to DDoS mitigations, which require careful planning to ensure adequate maintenance and cutting-edge protection.
The following Appendix offers in-depth descriptions of the trends, types, TTPs, and history of attacks.
…
Appendix: Primer and Threat Landscape
1. Strategic shifts and trends
Over the past two and a half years, security vendors have seen a rise in frequency, persistence, and complexity across DDoS attacks. Prior to August 2020, most DDoS extortion attacks occurred during peak business times, such as the holidays.11, 12 DDoS threat actors take advantage of these times because they are when businesses handle heavy customer traffic spurred by online shopping deals. Furthermore, businesses reduce their IT staff during the holidays, and this makes mitigating threats more challenging for the businesses.
The number of DDoS extortion attacks surged in the middle of August 2020, and some of them caused a shutdown of the stock exchange and generated record-breaking bandwidths.13, 14 Since, DDoS extortion attacks have been occurring more frequently and with shorter breaks. NETSCOUT’s ATLAS Security Engineering and Response Team (ASERT) reported that the number of identified DDoS attacks in 2020 was 20% higher than in 2019.15 Kaspersky Lab reported that the number of DDoS attacks in Q2 of 2020 was three-fold higher than in Q2 2019.16 This contradicts the trend that Kaspersky observed in 2019 and prior years, when DDoS activity was high at the beginning of the year and decreased by late spring or early summer.
NETSCOUT and Kaspersky attribute the rise in the frequency and continuity of DDoS extortion attacks to the COVID-19 lockdowns, which have increased the amount of business conducted online. Akamai, for example, saw an increase in the number of customers who have shifted their focus toward protecting VPNs and communication endpoints and away from data centers, to address security concerns related to remote work and the expansion of their digital footprint. Although some countries have lowered their COVID-related travel restrictions, security vendors are still seeing a constant stream of inquiries and subscriptions for protection against DDoS attacks, and they believe this is driven by the rise in bitcoin’s value and in extortion attacks’ successes.
Prior to August 2020, DDoS extortion actors had targeted various industries, with a strong preference for the gaming sector. Since August 2020, however, they have focused on economic sectors, such as finance, travel, and e-commerce. As a result, the number of attacks on the gaming sector has decreased. This is another indication that the actors behind DDoS attacks are formalizing their campaigns into a business model and are no longer as interested in simply disrupting gaming services for the sake of revenge or electronic vandalism.17
Since late 2020, the actors have also been more persistent and have circled back to organizations they targeted previously. The actors who posed as Fancy Bear, Armada Collective, or Lazarus Group in August and September 2020 revisited their targets in late December 2020 and early January 2021. The organizations that received the second extortion messages did not pay in response to the first campaign, nor did they reply via email or share the first extortion letter with public sources or media. The second extortion emails made references to the emails sent in the previous campaign, and they included the following text:
“Maybe you forgot us, but we didn’t forget you. We were busy working on more profitable projects, but now we are back.We asked for 10 bitcoin to be paid at to avoid getting your whole network DDoSed. It’s a long time overdue and we did not receive payment. Why? What is wrong? Do you think you can mitigate our attacks? Do you think that it was a prank or that we will just give up? In any case, you are wrong.”
Because the first and second campaigns had similar TTPs, security vendors believe the same actors are responsible for both campaigns.18
The intensity of the DDoS extortion attacks in later 2020 and 2021 was notably higher than that of the previous attacks. The campaigns of 2014 and 2015 launched DDoS attacks with bandwidths of 30 Gbps or less. The campaigns in August 2020, however, delivered bandwidths of 200+ Gbps; by mid-September, the campaigns’ bandwidths had grown to 500+ Gbps; finally, in an attack on a European gambling company, the bandwidth jumped to 800+ Gbps.
As mentioned in earlier sections of this report, most DDoS protection tools specialize in countering only a handful of attack vectors. Actors take advantage of this limitation by using complex tools that can exploit various network protocols and by rotating their methods until the victims succumb to the attack. Netscout observed that towards the end of 2020, DDoS campaigns had applied 15 to 25 different attack vectors.19 In spring 2021, Akamai witnessed a DDoS attack that was using a new vector to exploit the Datagram Congestion Control Protocol (DCCP).20
2. DDoS attack vectors
By using multiple attack vectors to send large amounts of traffic packets to their targets, DDoS actors attempt to exhaust the targets’ resources and prevent them from processing legitimate traffic. Many actors use multiple attack vectors in one larger assault; this makes mitigation difficult because no single DDoS protection system can resolve all types of attack methods. Over the past several years, actors who have successfully monetized DDoS campaigns via extortion have used the following DDoS attack vectors most often:
2.1. DNS flood
This DDoS is a layer 7 attack and a variant of the User Datagram Protocol (UDP) flood attack (DNS relies on UDP to perform name resolution). A DNS flood targets one or more DNS servers assigned to a zone and attempts to impede the DNS server’s ability to perform name resolution. Unlike DNS amplification attacks, a DNS flood is symmetric: it uses multiple compromised botnet machines to run malicious scripts that flood and exhaust the target server’s resources (for example, memory and CPU) via UDP requests. Some actors also spoof the UDP packet information to make the attack appear to be coming from other sources; this technique helps the attack bypass DDoS protection mechanisms, such as IP filtering.
2.1.1. DNS amplification
This is a volumetric DDoS attack that abuses the functionality of open DNS resolvers to attack a target server with an amplified amount of traffic. The concept of this attack is simple: get more for less. The attack begins when a bot uses a spoofed IP address (the target server’s IP address) to send a UDP packet to an open DNS resolver. The request is crafted; for example, it might contain the argument ANY, to command a very large response from the resolver. As a result, the target server receives response packets many times larger than the original request, and this eventually exhausts the server’s network infrastructure and causes a DoS. This method is extremely powerful because the computing cost of generating the request is much smaller than the cost of processing the response. Therefore, even a small botnet can successfully conduct a DNS amplification attack.
2.1.2. ARMS amplification
Apple Remote Management Service (ARMS) is part of Apple Remote Desktop (ARD): a feature built into macOS systems. When users enable ARD, the ARMS service starts on UDP port 3283 and listens for incoming commands designed for remote macOS devices. Cyber criminals have discovered that they can abuse the service to perform DDoS amplification attacks by bouncing traffic off of ARD-enabled macOS devices and use them as intermediary points to relay traffic towards victims’ servers. ARMS has an amplification factor of 35.5, and this means that actors can command a large set of responses with only a small set of requests. In 2019, BinaryEdge scanned the internet and found almost 40,000 public-facing ARD-enabled macOS systems.21
2.1.3. SNMP reflection
Systems use the Simple Network Management Protocol (SNMP) to configure and collect information from servers, hubs, switches, routers, printers, and other network devices. An SNMP reflection attack occurs when a perpetrator sends out a large number of SNMP queries with a forged IP address to many connected devices. As per the SNMP, these devices respond to the forged address. Eventually, the collective volume of the SNMP requests overwhelms the target and knocks it offline. An SNMP reflection attack can send bandwidths of hundreds of gigabits per second and can be directed at targets from multiple broadband networks. Attacks can last several hours, are highly disruptive to business services, and can be difficult to mitigate.
2.1.4. SYN flood
SYN flood attacks exploit the TCP handshake process to render web servers unavailable. Under normal conditions, a client initiates a connection by sending a SYN packet to the server. The server acknowledges the communication by responding with a SYN/ACK packet. Finally, the client acknowledges the SYN/ACK response by returning an ACK packet. When this sequence is completed, a TCP session is established for continuous communication.
In a SYN flood attack, the client never sends the final ACK packet; instead, the actors continue to send SYN packets. Because each SYN packet causes the server to maintain a new port connection, the number of SYN requests will eventually deplete all available ports, and this will prevent the server from functioning normally.
2.1.5. GRE flood
Generic Routing Encapsulation (GRE) is a tunneling protocol that can encapsulate various network layer protocols. In the context of networking, encapsulation means wrapping a data packet of one protocol within a data packet of another protocol. To simplify connections between separate networks, devices use GRE to set up a virtual point-to-point connection over an IP network. Large amounts of traffic data can be encapsulated by using GRE, and DDoS actors use the protocol to overload the servers of their targets. A target goes offline when it expends too much processing power to reassemble fragmented IP packets. This is what happened in September 2016, when the Mirai botnet performed a GRE flood attack against KrebsOnSecurity.22
The source IP address of a GRE packet cannot be forged; this is one of the features that distinguishes GRE from other protocols. Therefore, to launch a large GRE DDoS attack, the perpetrator must control a large botnet.
2.1.6. WS-Discovery amplification
Web Services Dynamic Discovery (WS-Discovery) is a UDP-based communications protocol that printers, cameras, and Windows OS features use to discover web-based services inside networks. Often, these devices are misconfigured and, as a result, end up listening and responding to WS-Discovery protocol requests over the internet. Actors take advantage of this weakness and hide the source of their DDoS traffic by reflecting it through these open devices. In September 2019, Akamai conducted an internal study and discovered that actors could amplify the original request’s byte size by as much as 15,300%.23
2.1.7. CLDAP reflection
A Connectionless Lightweight Directory Access Protocol (CLDAP) reflection attack exploits a weakness in the CLDAP protocol to deliver an amplified amount of traffic to a target IP address and thus render the target’s backend processes unavailable. To deliver the attack, an attacker-controlled bot sends a CLDAP request to a public Lightweight Directory Access Protocol (LDAP) spoofed with the target’s IP. The server sends a bulked-up response to the target IP, and this clogs its work queue with illegitimate traffic. In April 2020, a CLDAP reflection attack on DOSarrest customers reached peak bandwidths of 300+ Gbps24 and amplified the payload of original queries up to 70 times.25
2.1.8. TFTP amplification
Trivial File Transfer Protocol (TFTP) is a UDP-based file transfer protocol that runs on port 69. Network devices use the protocol to remotely fetch firmware and configuration files. Some TFTP servers are configured to listen to the open internet. Because TFTP is a UDP-based protocol, it does not support authentication and other security-related features. Actors take advantage of this and send, via a spoofed IP address, request packets to the TFTP servers that are open to file transfer. What reduces the likelihood of higher amplification of a single request is that the TFTP protocol sends out data in blocks of specific sizes only and requires acknowledgement of each block received.
2.1.9. NTP amplification
Network Time Protocol (NTP) allows devices connected to the internet to synchronize their internal clocks. The NTP amplification method is a reflection-based volumetric DDoS attack that sends the monlist command to public NTP servers. The command prompts an NTP server to return the last 600 IP addresses that it has received. The response payload is 206 times larger than the request packet. When responses from a botnet are sent to the spoofed IP address in the original UDP packets, the target’s server resources are locked up and the server cannot function normally.
2.1.10. WordPress XML-RPC amplification
WordPress’s Extensible Markup Language-Remote Procedure Call (XML-RPC) Pingback is a layer 7 attack that DDoS actors use to launch HTTP-based attacks on target websites by using third-party WordPress blogs. This attack takes advantage of a vulnerability in WordPress’s XML-RPC API and makes an HTTP POST request to a public WordPress blog site that has the /xmlrpc.php endpoint open. The actors include a callback URL (the target website’s address) in the HTTP POST packet request, and this prompts the WordPress site to make a separate HTTP GET request to the callback URL. The method thus obfuscates the actors’ real IP, and from the victim’s point of view, the attack appears to be coming from the WordPress site. Although this attack does not amplify traffic significantly, the perpetrator can make the attack more effective by setting the callback URL to a computationally expensive endpoint.
2.1.11. Simple Service Discovery Protocol (SSDP)
Universal Plug and Play (UPnP) devices use Simple Service Discovery Protocol (SSDP) to broadcast their existence to other devices on the network. A sequence of requests starts when a UPnP device broadcasts its IP address, and the final response includes a complete list of descriptions and services that is sent from the UPnP device to the requester. An SSDP reflection DDoS exploits this final response by crafting a request packet with a spoofed IP that belongs to the target.
2.1.12. Portmapper amplification
Portmapper is a service built into all UNIX servers as well as some Windows devices that integrate with UNIX systems. The program runs on network nodes that provide Remote Procedure Call services, and it always runs on TCP or UDP port 111. A Portmapper amplification attack takes place when a perpetrator sends, to public Portmapper servers, UDP packets that contain spoofed IP addresses. These servers reply to the spoofed IP addresses (those on the target server) with a list of networking services to map to. The response packets can be 7 to 28 times larger than the originating request.26
3. DDoS extortion campaigns
The majority of DDoS campaigns disrupt legitimate business services with the intent of bringing awareness to a social or political issue; this is called hacktivism. Other motives include retribution (in one instance, gamers attacked a gaming platform because they believed it instituted unfair changes in policy); boosting the reputation and profile of the actors within the hacking community; and entertainment.
A DDoS extortion campaign, on the other hand, is more self-sustaining and business oriented. Its objective is to monetize the DDoS activity by extorting funds from the victim. The actors send the extortion demand message via an email or a traffic payload, and they threaten to perform or continue a high-bandwidth DDoS on the target’s infrastructure unless a payment is submitted. The FBI discourages companies from paying DDoS extortions, because meeting cyber criminals’ demands empowers them financially and does not guarantee that they will stop their attacks.
3.1. Strategy
In a typical DDoS campaign, the actors do not interact with the victim. In a typical DDoS extortion campaign, however, the actors not only interact with the victim but do so often. In addition, they see it as their top priority to deliver an extortion message that would convince the victim about the legitimacy of the threat.
In the early years of DDoS extortion campaigns, actors used simple messages and demanded payments in the form of U.S. dollars:
Figure 1: A simple extortion email from a campaign that targeted Meetup in 201427
Date: Thu, Feb 27, 2014 at 10:26 AM
Subject: DDoS attack, warningA competitor asked me to perform a DDoS attack on your website. I can stop the attack for $300 USD. Let me know if you are interested in my offer.
In spring 2015, DDoS actors started using messages that are longer and include references to the actors’ previous DDoS attacks. By doing this, the actors attempt to elevate their reputation and to build credibility with the organizations they attack. For example, in a recent attack, the DDoS extortion group DD4BC included not only Akamai reports about the group’s previous campaigns but also the link to the target-specific status page that the group used in the previous attack on that target. In addition, more threat actors have demanded that victims pay with bitcoin rather than national currencies. Here is an example:
Figure 2: Extortion email from DD4B28
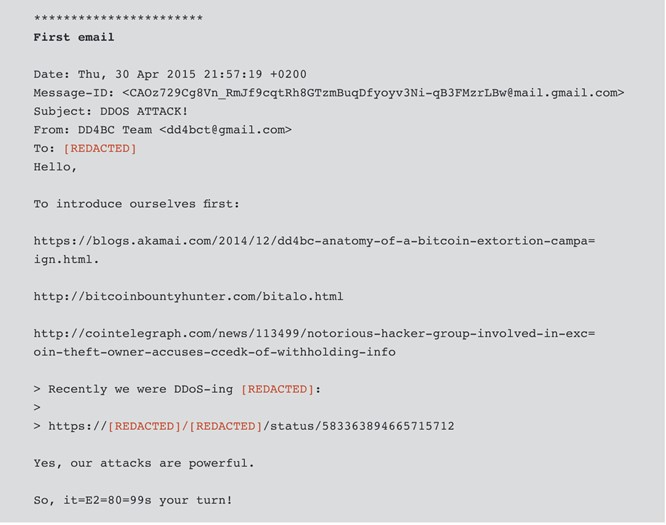
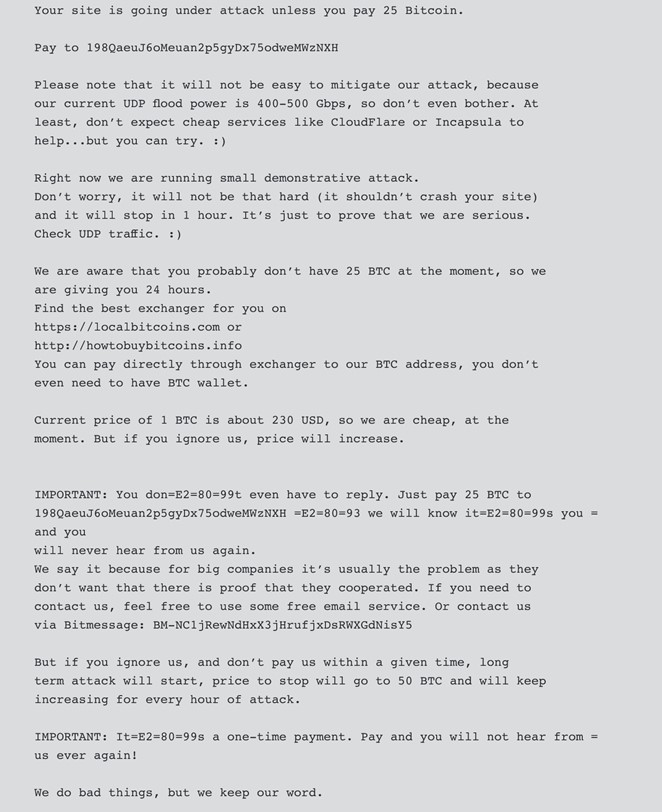
Email is DDoS actors’ preferred method for delivering extortion demands, but many target organizations use filters that stop spam from reaching the intended recipients. To get around this obstacle, some actors deliver their demands via other mediums, such as memcached server files. In March 2018, for example, Akamai reported that one of its customers fell victim to a DDoS attack that sent amplified traffic at a rate of 1.3 Tbps. Before the attack started, the actors uploaded a text file to the memcached public servers; the file contained repeated strings instructing the victim to send 50 XMR, the virtual currency also known as Monero, to the actors’ wallet address.
Figure 3: An extortion message uploaded to a memcached server29

In fall 2019, businesses in various sectors saw a change in the extortion email templates. Actors consistently identified themselves with aliases they had borrowed from famous APT groups, such as Fancy Bear and Lazarus Group, and they instructed the victims to google the groups’ names to confirm their reputation. Typically, the actors gave a victim one week to prepare the payment, and they threatened to increase the extortion amount each day past the deadline. The actors have continued using these tactics, and although some of the threats have been bluffs, organizations should assume that all threats are real until proven otherwise. To this end, all organizations should have DDoS mitigation solutions enabled to weather such attacks if they materialize.
Figure 4: An extortion message from the fake Cozy Bear campaign30
We are the Cozy Bear and we have chosen [REDACTED] as target for our next DDoS attack. Please perform a google search for “Cozy Bear” to have a look at some of our previous work.
Your network will be subject to a DDoS attack starting at Wednesday next week (in 6 days). (This is not a hoax, and to prove it right now we will start a small attack on [REDACTED] that will last for 30 minutes. It will not be heavy attack, and will not cause you any damage so don’t worry, at this moment.)
This means that your website and other connected services will be unavailable for everyone.
We will refrain from attacking your servers for a small fee. The current fee is 2 Bitcoin (BTC). The fee will increase by 1 Bitcoin for each day after deadline that passed without payment.
Please send Bitcoin to the following Bitcoin address:
[REDACTED]
Once you have paid we will automatically get informed that it was your payment. Please note that you have to make payment before the deadline or the attack WILL start!
If you decide not to pay, we will start the attack on the indicated date and uphold it until you do, there’s no counter measure to this, you will only end up wasting more money trying to find a solution (Cloudflare, Sucuri, Imperva and similar services are useless, because we will hit your network directly). We will completely destroy your reputation and make sure your services will remain offline until you pay.
Do not reply to this email, don’t try to reason or negotiate, we will not read any replies. Once you have paid we won’t start the attack and you will never hear from us again.
Please note that Bitcoin is anonymous and no one will find out that you have complied.
3.2. Targets
DDoS extortion actors have often attacked the gaming industry and services related to online video games. The scope of the attacks has broadened over the last few years. From 2019 to 2020, Akamai observed a 400% increase in DDoS attacks on financial services (mainly banking, stock exchanges, and currency exchanges), an 800% increase in attacks on retail and consumer services, and the emergence of attacks on business services.31
Figure 5: DDoS attacks by industry (source: Akamai)
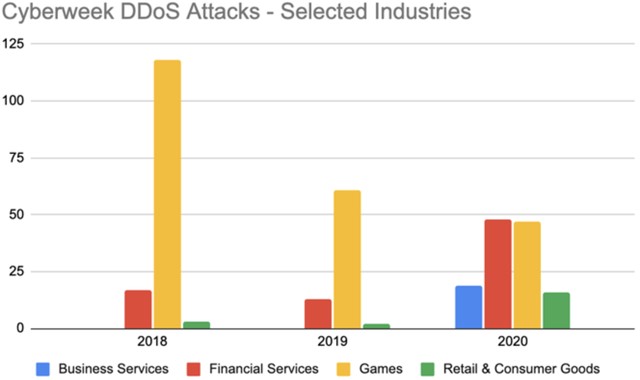
So far in 2021, DDoS extortion attacks have been almost evenly distributed across various industries. In several DDoS extortion campaigns that involved actors posing as Fancy Lazarus, Proofpoint saw targets related to the following industry categorizations: energy, financial, insurance, manufacturing, public utilities, retail sectors, travel and hospitality, retail/e-commerce, high-tech/software, consumer packaged goods, and internet service providers.32
3.3. Attack chain diagrams
DDoS extortion campaigns typically follow one of two kinds of attack chains.
Figure 6: A scenario in which a DDoS attack begins with a demonstration
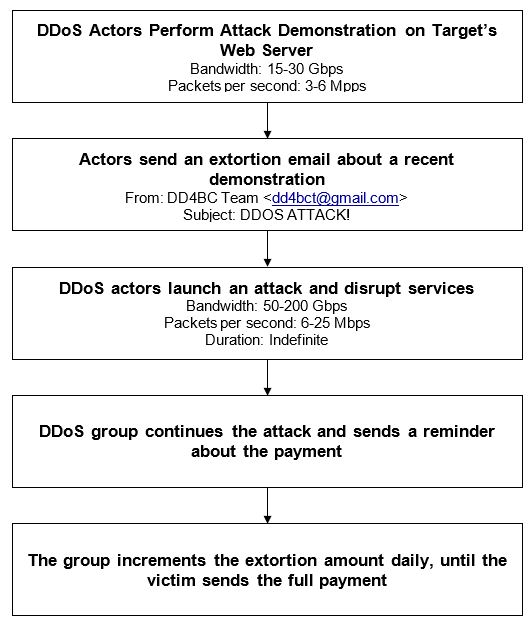
Figure 7: A scenario in which a DDoS attack begins with an extortion email
In rare cases, some actors, such as those calling themselves Armada Collective, warn victims not to discuss details of the extortion letter with the media. If the victims do, the actors launch a long-lasting DDoS attack immediately, or at least threaten to launch one.
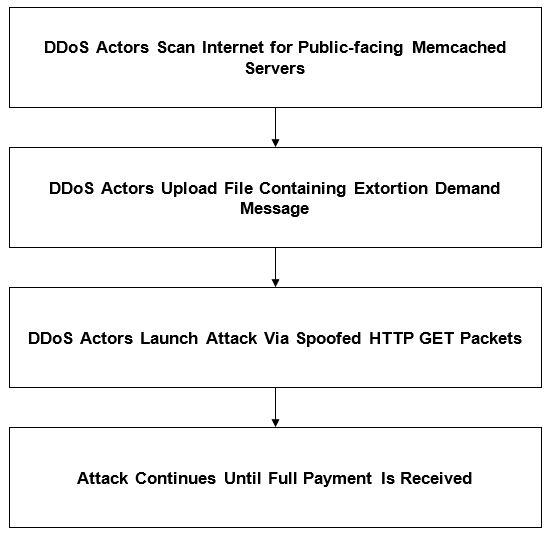
In other rare cases, the threat actors embed the extortion message directly in the traffic payload. In March 2018, for example, DDoS extortion actors uploaded a file that contained the repeated string “Pay_50_XMR_To_” to memcached servers open to the internet. Next, they sent HTTP GET requests to the file, with a spoofed IP address that belonged to the target.
Figure 8: A memcached amplification attack
3.4. Impact
DDoS is one of the most costly cyber threats to mitigate, because it directly affects the availability of services crucial to business operations. Bulletproof’s 2019 annual cybersecurity report indicated that a DoS or DDoS attack could cost a small company up to $120,000 and an enterprise up to $2 million in damages.33 Over the years, many large organizations have fallen victim to DDoS extortions and have received substantial damage both to their finances and public reputation. The following is a non-exhaustive list of DDoS extortion events that have publicly revealed the vulnerability of well-known and large organizations to DDoS attacks:34
- In February 2000, 15-year-old Michael Calce, a.k.a. Mafiaboy, brought down the websites of Amazon, CNN, Dell, eBay, E-Trade, and Yahoo! by using a botnet that he controlled with a tool called TFN2. This attack prevented customers from reaching these companies’ websites and adversely affected the stock market. Total damages from this attack are estimated to be $1.2 billion.
- In September 2012, a hacktivist group named Izz ad-Din al-Qassam Cyber Fighters took credit for 200+ DDoS attacks that targeted major banks, including Bank of America, JPMorgan Chase, Citigroup, U.S. Bank, Wells Fargo, and PNC. As a result, banking customers were unable to access their online accounts and pay bills.
- In March 2013, an employee at Dutch ISP Cyberbunker launched a DDoS DNS reflection attack on Spamhaus: a non-profit organization that helps protect billions of mailboxes worldwide by providing enterprises with intelligence they can apply to their spam email filters. The attack disabled Spamhaus’ website and email servers and prevented the organization from updating its feeds with the latest spam data. Spamhaus suspects that the motive behind the attack was the inclusion of Cyberbunker’s servers in Spamhaus’ blocklists.
- In October 2016, a botnet that consisted of tens of millions of Mirai-infected IoT devices attacked Dyn, a former DNS provider. The bandwidth of the DDoS attack was 1 to 1.2 Tbps and left many parts of North America and Europe without internet access. Famous entities that experienced reduced availability of services included Airbnb, Twitter, Visa, PayPal, CNN, BBC, and Netflix.
- In August 2020, a DDoS extortion group calling themselves Fancy Bear delivered extortion letters to and launched DDoS attacks on major money-transfer services, such as MoneyGram, YesBank India, Worldpay, PayPal, Braintree, and Venmo. They also targeted the New York Stock Exchange and New Zealand’s Exchange (NZX), which experienced DDoS for five consecutive days and halted trades on its platform. Akamai confirmed that at its peak, the DDoS attack showed bandwidths of 200 Gbps.35
3.5. Extortion payments
As we described in the strategy section of this report, early DDoS extortion campaigns, such as the one that attacked Meetup in March 2014, demanded payments in U.S. dollars. As cryptocurrency became more popular, more actors started to demand that victims make payments in Monero and bitcoin. Bitcoin’s high value and anonymity have made it the actors’ favorite. The following table shows the payment values demanded by actors in each major campaign. We normalized these values (by calculating their USD equivalents at the time of each campaign) to address the fluctuation of bitcoin price over time.
Table 1. History of major extortion payments by campaign
| Period | Actor | Currency | Payment Value | Target |
| March 2014 | Unidentified | U.S. Dollars | $300 | Meetup |
| September 2014 – July 2015 | DD4BC | Bitcoin | $230 – $23,000 | Banks, credit unions, currency exchanges, media, entertainment, online gaming, Retail, and consumer goods |
| March 2018 | Unidentified | XMR | $15,000 | KrebsOnSecurity |
| November 2019 | Cozy Bear | Bitcoin | $17,500 | Finance |
| August 2020 | Fancy Bear, Armada Collective | Bitcoin | $57,000 – $227,000 | MoneyGram, YesBank, Braintree, Venmo, and New Zealand Stock Exchange |
| October 2020 | Lazarus | Bitcoin | $230,000 | Travelex |
| December 2020 – January 2021 | Fancy Bear, Armada Collective | Bitcoin | $30,000 | Targets received an extortion letter from the same actor in August 2020. Specific targets are not known. |
| May 2021 | Fancy Lazarus | Bitcoin | $76,000 | Energy, financial, insurance, manufacturing, public utilities, and retail |
3.6. Actors and groups
In the early years of DDoS extortion, actors operated without names, most likely because they were pursuing quick payouts and did not want to attract attention from law enforcement and security researchers. Additionally, the actors did not begin formalizing DDoS extortion into a business until 2014. When DD4BC first launched their campaigns in 2014, they were among the very few groups—if not the only group—of DDoS extortion actors who used an alias. Since November 2015, however, more and more actors have been using names to build their credibility with the victims. The following are the aliases and major campaigns of some well-known DDoS extortion groups:
3.6.1. DD4BC
DD4BC ran DDoS extortion campaigns from September 2014 to July 2015. During this time, the actors targeted finance, currency exchange, online gaming, retail, and consumer goods industries. The actors were more persistent and aggressive towards organizations that lacked DDoS protection. DD4BC usually began their campaign by performing a demonstration attack that lasted from 30 minutes to 1 hour. Then, it sent an extortion letter and demanded a bitcoin payment, to avoid further attacks. If the victim did not pay, then DD4BC launched a larger-bandwidth DDoS attack that lasted several days. Some victims received up to five extortion letters and threats to publicise the ongoing DDoS attacks. Across all DDoS attacks related to DD4BC, Akamai recorded a peak bandwidth of 50 Gbps. The actors applied multi-vector DDoS attacks and even performed WordPress pingback amplification.
After Akamai published its case study on DD4BC in September 2015, there was a sharp decrease in the actors’ activities.36 We assess with medium confidence that the group sought to avoid attention from law enforcement and the public. Nevertheless, in January 2016, Europol announced that law enforcement agencies from several European countries and the U.S. worked in coordination with police to arrest two members of DD4BC.37 The cyber intelligence community suspects that after the arrests, other DD4BC actors might have continued DDoS campaigns under a different alias.
3.6.2. Fancy Bear, Armada Collective
In November 2015, new DDoS extortion actors, who identified themselves as Armada Collective, conducted DDoS attacks. Because similar TTPs and extortion message templates were used in the campaigns, initially, Akamai speculated that they were conducted by DD4BC, but under the new alias. However, after witnessing attack bandwidths that were a fraction of the size of the DD4BC DDoS attacks, Akamai assessed the campaigns were the work of copycat cyber criminals piggybacking off the efforts of DD4BC. In the campaign’s extortion letters, the actors claimed that they had the capacity to deliver an attack bandwidth of 1 Tbps. However, Akamai recorded a peak of only 772 Mbps, across all observed attacks.38
In August 2020, DDoS extortion actors identifying themselves as Fancy Bear and Armada Collective launched campaigns that focused on large global finance organizations but also targeted companies in the pharmaceutical, healthcare, retail, oil and gas, travel and hospitality, logistics, airlines, and high-tech industries. The extortion demands in the campaign ranged from $50,000 to $300,000 worth of bitcoin. Before launching the attacks, the actors reconnoitered the victims’ environments to identify vulnerable IP spaces and network-based attack vectors, such as DNS amplification. Demonstration attacks showed bandwidths from 20 to 50 Gbps. The actual attacks, however, showed much higher bandwidths; the peak of 800+ Gbps was recorded in the attack against a European online-gambling organization.39
3.6.3. Fake Cozy Bear
In November 2019, DDoS extortion actors calling themself Cozy Bear conducted attacks against various organizations. Cozy Bear is a state-sponsored Russian APT that is not known for DDoS activities. Akamai believed this was another example of copycats piggybacking off of high-profile actors to invoke fear and panic.40 After identifying themselves as Cozy Bear, the actors suggested the victims google the group’s name—a tactic used to build credibility with the target—and gave the victims approximately 6 days to pay $17,500 in bitcoin. The actors then launched a 30-Gbps demonstration attack, which abused several of the target’s protocols, including DNS, ARMS, CLDAP, TFTP, PortMap, and WSD.
CERT NZ reported similar attacks against New Zealand’s finance sector.41 The attacks used reflective DDoS techniques and abused protocols similar to those reported by Akamai. There has been no evidence that the attackers followed through with the main DDoS attack after the victims failed to pay by the deadline.
3.6.4. Fancy Lazarus
In May 2021, DDoS extortion actors who posed as Fancy Lazarus conducted campaigns that targeted energy, financial, insurance, manufacturing, public utilities, retail, and other industries. The name Fancy Lazarus is a combination of the names of APT groups Fancy Bear and Lazarus. Because Fancy Lazarus used TTPs, targets, and attack capacity similar to those used by Fancy Bear and Armada Collective, researchers at Proofpoint believed that Fancy Lazarus were the same actors as those in Fancy Bear and Armada Collective. As in the Cozy Bear campaigns, the Fancy Lazarus actors:42
- Gave targets seven days to pay $75,000 in bitcoin
- Instructed the targets to google “NZX DDoS” or “New Zealand Stock Exchange DDoS”
- Took credit for previous extortion events
- Claimed to have reconnoitered their targets
- Threatened to attack specific IPs and subnet blocks managed by the target organizations
- Sent their emails to recipient addresses that belonged to individuals working for the targets
3.7. TTPs
Since 2020, DDoS actors have reconnoitered their targets more heavily than in previous years. Instead of directing their attacks at public or vulnerable connection points, the actors thoroughly scan target infrastructure to identify weak points or vulnerabilities. The artifacts from the August 2020 DDoS extortion campaigns by Fancy Bear, for example, indicated that reconnaissance had improved since the previous campaigns. In the extortion letters, the actors stated that they had not only uncovered specific weaknesses across the target’s public-facing infrastructure but also identified IPs that were critically important to their targets’ revenue. The attacks that followed proved that the actors’ threats were not a bluff, because the victims received malicious traffic aimed at their data centers, ports, and business-critical protocols.43
According to Roger Barranco, vice president of global security operations at Akamai, DDoS actors research their targets more extensively than ever. They aim not only to disrupt business operations directly but also to damage facilities and internal systems. Regarding a DDoS incident that occurred in 2020, Barranco said, “It is one of the first times we’ve seen them go after things other than services. What I mean by services is their website, transaction site, or their mail server. This time, they were also going after buildings, for example, to knock a building offline. It’s an example of something attackers are going to look at for the future for sure. If I can’t hurt the enterprise, I’m going to hurt the workers who are trying to reach it.”44
3.7.1. Botnets
Prior to 2020, it was common for targets to receive empty threats and no follow-up attacks. Since the latter half of 2020 and 2021, however, DDoS extortion actors have been following up with attacks more frequently. To perform a DDoS attack with enough power to disrupt enterprise-level services, actors require access to large botnets. There are typically two ways to obtain them: rent a botnet or develop one.
3.7.1.1. Botnets rented via DDoSaaS platforms
Actors can rent botnets via DDoSaaS platforms, which are marketed in dark web forums or even in some popular social media channels.45 Technically unsophisticated actors have found DDoSaaS to be a cost-effective approach. Typically, the actors use a web service that lets them configure the number of bots and the attack’s duration, vector, and destination. DDoSaaS also lets them conduct attacks through a series of botnets; this, and the anonymity that the actors enjoy during the purchase of DDoSaaS, make it very difficult for law enforcement and security researchers to track the actors’ origins.46
Figure 9: DDoSaaS web service (source: Securelist)
3.7.1.2. DIY botnets
Alternatively, DDoS actors can develop their own botnets. This method requires a deep understanding of system vulnerabilities and weaknesses. In addition, amassing a botnet made up of thousands or millions of compromised devices requires a non-trivial amount of time.
Some devices, such as IoT devices, are easier to take over than others; in the case of Mirai, the botnet expanded its population by scanning for telnet servers running on ports 23 and 2323. After finding such servers, the botnet tried to pass authentication by using a set of known default credentials. Because many IoT devices are deployed with default factory settings, cyber criminals can access them by using generic credentials, such as “admin” and “password.”
Compromising other kinds of devices requires special conditions, exploits, or even human interaction. The Pushdo (aka Cutwail) botnet, for example, sends spam emails from infected Windows host machines. To install the Pushdo trojan downloader on a target system, the botnet depends on human recipients to open a malicious attachment or link. Once compromised, the device can function as a DDoS bot for launching attacks on SSL-encrypted websites over port 443.
3.8. Timeline of news and events
The first known DDoS attack occurred in 1996, when ISP Panix went offline after it was attacked with a TCP SYN flood. Since then, threat actors have used DDoS to disable millions of legitimate services. In 2018 alone, security vendors and affected organizations reportedly observed 7.9 million DDoS attacks. Researchers believe that in 2023, the number of attacks will double and exceed 15 million.47
Today, threat actors still use TCP SYN flood, ICMP flood, UDP flood, and other DDoS attack vectors that were used in the earlier days. However, as stress-testing and DDoS tools (such as Low Orbit Ion Cannon (LOIC) and High Orbit Ion Cannon (HOIC) become more affordable, the attacks become more complex and numerous.48 Also, more DDoS campaigns use a combination of multiple attack vectors in a single attack. These factors make it increasingly difficult for network vendors to protect their infrastructure, because no single security solution can protect against all DDoS attack vectors. Furthermore, new DDoS attack vectors have emerged, such as Constrained Application Protocol (CoAP), Web Services Dynamic Discovery (WS-DD), Apple Remote Management Service (ARMS), and the Jenkins web-based automation software. Cyber criminals used all four of these vectors to launch DDoS attacks in 2020.49
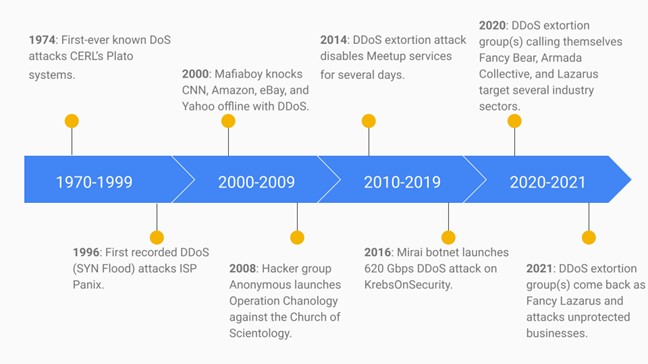
The following timeline describes notable events in the history of DDoS and focuses on newly discovered attack vectors and actors, campaigns that have caused high impact on business, and development of game-changing mitigation solutions. The timeline suggests that the objectives of DDoS attacks have shifted from personal notoriety and vandalism to achieving lucrative gains by following mature business models.
Figure 10: History of notable DDoS attacks
1974: First known DoS attack
A 13-year-old high school student named David Dennis found a poorly designed command, external, that runs on Computer-Based Education Research Laboratory’s (CERL) Programmed Logic for Automatic Teaching Operations (PLATO) terminals. PLATO is one of the first computing systems for multi-user sharing and learning. The command allows PLATO to interact with external devices connected to the terminals. However, if the command runs on terminals that do not have external devices attached, it locks up the system and requires users to re-power it to regain functionality. David wrote a program that sent the command to multiple PLATO terminals simultaneously, and he tested the program at the CERL campus; this caused 31 users to power off at once.
1996: First known DDoS attack
An unidentified adversary targeted Panix, the oldest ISP in New York.50 The attack used a SYN flood: a method that exploits the three-way TCP handshake by sending a large volume of illegitimate SYN packets via spoofed IP addresses. Security researchers speculated that the attack was retribution for Panix’s newly installed systems that locked out bulk email spammers. It took Panix roughly 36 hours to recover from the attack and bring its servers back online.
2000: Mafiaboy knocks major companies offline
15-year-old “Mafiaboy” launched a DDoS attack that knocked offline the websites of Amazon, CNN, Dell, E*Trade, eBay, and Yahoo!. Because Yahoo! was the largest search engine at the time, this incident garnered tremendous media coverage. To accomplish this feat, Calce first compromised multiple university networks, so that he could use the combined computing power of their connected devices. He adopted the attack tool TFN2 to control the botnet and launch distributed attacks against the target websites. In an interview, Calce said the purpose of the attack was to intimidate other hacker groups.51 This was a common motive for DDoS attacks at the time; large and successful attacks helped hackers build their reputation and credibility.
2008: Operation Chanology
Hacker group Anonymous conducted Operation Chanology as part of a protest against practices by the Church of Scientology.52 Anonymous launched a 220-Mbps DDoS attack that took down the organization’s website. The attack utilized open source stress-testing tools (Low Orbit Ion Cannon and High Orbit Ion Cannon) to control botnets via Internet Relay Chat (IRC) servers and to direct malicious traffic to the target website; this overwhelmed the website’s resources and disabled its services.
2014: DDoS extortion attack against meetup
A DDoS actor attacked and sent an extortion letter to the social networking website Meetup.53 The letter demanded $300 USD to stop the attack, which continued for three days and disrupted Meetup’s website and applications. Meetup did not submit to the perpetrator’s demands: reportedly, Meetup believed that (1) there was no guarantee that the attacks would stop and that (2) submitting to the perpetrator’s demands would set a bad precedent and potentially invite more ransom demands in the future.54
2016: Mirai botnet attacks OVH, KrebsOnSecurity, and Dyn
In September, a DDoS attack delivered a traffic load of up to 1.1 Tbps to an unidentified organization that was using OVH servers.55 This attack lasted about seven days and was carried out by the Mirai botnet: a group of compromised Internet of Things (IoT) devices, such as IP cameras, home routers, and video players. The next day, the Mirai botnet used a traffic load in excess of 620 Gbps to bring down KrebsOnSecurity: a blog website that discusses security topics and is managed by well-known security journalist Brian Krebs.
In October, attackers used Mirai to attack DNS provider Dyn with a traffic load of up to 1.5 Tbps, a new record at the time.56 The traffic involved tens of millions of unique IPs and disabled Dyn services, rendereding Github, HBO, Twitter, Paypal, Reddit, Netflix, Airbnb, and many other websites unavailable.
Prior to the Dyn attack on 30 September 2016, someone claiming to be the Mirai software author released the source code on multiple hacker forums. Since then, other cyber criminals have replicated the Mirai DDoS platform and created several variants.
2020: DDoS extortion groups pose as Fancy Bear and Armada Collective
During the middle of August 2020, both Radware and Akamai observed that DDoS extortion groups were targeting institutions in multiple sectors, including banking, finance, retail, travel, and e-commerce.57 These institutions are based in APAC, EMEA, and North America regions. The groups claimed to be the well-known advanced persistent threat (APT) actors named Fancy Bear, Armada Collective, and Lazarus Group. The campaigns began with an extortion email that demanded $113,000 in bitcoin; some campaigns demanded up to $226,000. In their extortion message, the actors claimed to have a DDoS capacity of 2 Tbps and threatened to increase the ransom by $113,000 for everyday the victims failed to pay. The bitcoin wallet’s address was unique for each target, and this enabled the actors to keep track of each victim’s payment. Although many organizations did not suffer a follow-up attack after the deadline, those that did reported seeing traffic of up to 200 Gbps and multiple attack types, including ARMS, DNS Flood, GRE Protocol Flood, SNMP Flood, SYN Flood, and WSDiscovery Flood.
2021: DDoS extortion groups return as Fancy Lazarus
After a month-long break, the DDoS extortion groups that had previously gone by the names of Fancy Bear, Lazarus, Lazarus Group, and Armada Collective resumed their campaigns on 12 May 2021,58 under the name Fancy Lazarus: a composite of the real APT groups’ names Fancy Bear and Lazarus. The campaigns targeted U.S. and global companies in the energy, financial, insurance, manufacturing, public utilities, retail, and other industries. This time, the actors lowered their ransom demands from 10 to 2 bitcoins, to account for the cryptocurrency’s price fluctuations. The extortion email’s body and attributes were similar to those of the August 2020 campaigns.
Several conditions in the technology industry have facilitated the rise in the number of DDoS activities and extortion campaigns over the past several years:
- The technical barrier to entry for DDoS is lower than for many other forms of attacks. For example, to launch a volumetric attack, perpetrators are not required to understand application-level details.
- The cost of renting a botnet or launching a DDoS attack via DDoSaaS, such as Anubis DDoS, has gone down significantly in 2020.59 This indicates that the number of suppliers of DDoSaaS has increased in the underground market and that criminals now have more options. Also, the suppliers of these tools have added capabilities that enable threat actors to launch attacks via multiple vectors simultaneously and thus make their attacks more complex.
- Evidence that organizations are willing to pay extortion demands to avoid future attacks has encouraged cyber criminals to pursue extortion tactics and monetize DDoS campaigns.
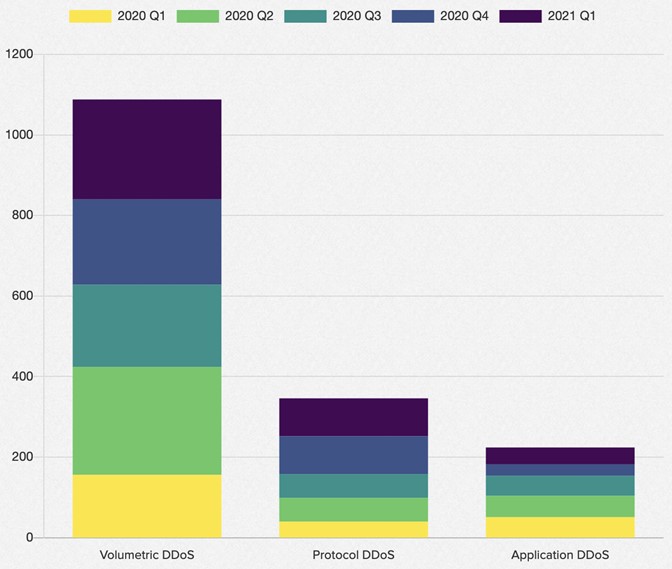
To determine trends in and impact of DDoS attacks on organizations, the network solution provider F5 studied 15 months’ worth of data from incidents logged by the F5 Silverline Security Operations Center (SOC) and the F5 Security Incident Response Team (SIRT).60 The data showed the following:
- Between January 2020 and March 2021, DDoS attacks increased by 55%, and 54% of the attacks employed multiple DDoS attack vectors.
- The largest DDoS attack recorded a bandwidth of 500 Gbps and employed at least five different attack vectors.
- The technology sector was targeted the most: it received 27% of all DDoS attacks.
- Volumetric DDoS accounted for 73% of all attacks. Of those DDoS attacks, 53% were reflection-based, meaning the perpetrators delivered the attacks from other vulnerable systems rather than directly from the bots that generated requests.
- The number of application DDoS incidents increased by 16%.
Figure 11: DDoS attacks by type, from January 2020 to March 2021 (source: F5)
Since 2014, the cyber intelligence community has observed a steady rise in the number of DDoS extortion attacks. Typically, these attacks occurred around holidays, and each attack delivered traffic of a bandwidth less than 50 Gbps. However, since the middle of August 2020, DDoS extortion attacks have occurred more consistently and the actors have taken fewer breaks between campaigns. The intensity of the attacks has increased as well, and traffic bandwidths have often exceeded 100 Gbps. Email has been the main medium for delivering messages, but on some occasions, the groups have sent extortion messages via HTTP GET requests to intermediary memcached servers. This practice might not have been effective for the actors, because organizations have not reported this kind of delivery method since 2018.
In earlier years, DDoS extortion groups opted to identify themselves with generic names or none at all. Since late 2019, extortion groups have regularly used aliases similar to or exactly the same as those used by APT actors, especially state-sponsored ones. Due to the strong contrast between the TTPs of extortion groups and of the real APT actors, we believe the extortion groups’ claims that they are well-known APT groups is a bluff used to intimidate victims, capitalize on the real APT actors’ names, and gain credibility.
Endnotes
- First known DDoS: https://www.a10networks.com/blog/5-most-famous-ddos-attacks/
- Colonial Pipeline Ransomware Attack: https://blogs.infoblox.com/cyber-threat-intelligence/cyber-threat-advisory-darkside-ransomware-attack-on-colonial-pipeline/
- Fancy Lazarus 2021: https://www.proofpoint.com/us/blog/threat-insight/ransom-ddos-extortion-actor-fancy-lazarus-returns
- BulletProof DDoS 2019 Study: https://www.bulletproof.co.uk/industry-reports/2019.pdf
- OSI Model: https://www.networkworld.com/article/3239677/the-osi-model-explained-and-how-to-easily-remember-its-7-layers.html
- A study by Akamai found that 13% of all DD4BC DDoS attacks were SYN floods. DD4BC SYN Flood: https://www.akamai.com/us/en/multimedia/documents/state-of-the-internet/dd4bc-operation-profile-bitcoin-extortion-ransom-case-study.pdf?_ga=2.235425537.1041443625.1624634401-239496092.1624634401
- In August 2020, groups that called themselves Armada Collective and Fancy Bear used SYN flood techniques to deliver 200 GB worth of packets per second. Armada Collective SYN Flood: https://blogs.akamai.com/sitr/2020/08/ransom-demands-return-new-ddos-extortion-threats-from-old-actors-targeting-finance-and-retail.html
- DDoS Scare: https://www.itgovernanceusa.com/blog/ransomware-evolution-chronicles
- Armada Collective No Threat: https://blog.cloudflare.com/empty-ddos-threats-meet-the-armada-collective/
- FBI Flash Alert: https://www.documentcloud.org/documents/7070798-FLASH-MU-000132-DD.html
- DDoS During Holidays: https://threatpost.com/ddos-attacks-cresting-pandemic/158211/
- DDoS Cyber Week: https://blogs.akamai.com/2020/12/cyberweek-2020-attracted-both-online-shoppers-and-ddos-attackers.html
- DDoS Extortion Bandwidth Record: https://blogs.akamai.com/sitr/2020/08/ransom-demands-return-new-ddos-extortion-threats-from-old-actors-targeting-finance-and-retail.html
- New Zealand Stock Exchange DDoS: https://www.zdnet.com/article/ddos-extortionists-target-nzx-moneygram-braintree-and-other-financial-services/
- NETSCOUT DDoS Trends: https://www.netscout.com/use-case/protecting-your-stateful-devices
- Kaspersky DDoS Trends: https://www.kaspersky.com/about/press-releases/2020_no-summer-vacation-ddos-attacks-tripled-year-on-year-in-q2-2020
- DDoS Extortion Sector Target Shift: https://blogs.akamai.com/sitr/2020/10/ddos-extortion-examination.html
- DDoS Actors Second Message: https://www.radware.com/security/ddos-threats-attacks/threat-advisories-attack-reports/ddos-extortions-back, https://www.securitymagazine.com/articles/94420-ddos-extortions-making-its-way-back
- Multiple Attack Vectors; https://www.csoonline.com/article/3618411/ddos-attacks-stronger-than-ever-and-increasingly-used-for-extortion.html
- New Attack Vector for DDoS Extortion: https://cyware.com/news/ddos-extortion-attacks-get-stronger-and-more-persistent-53e3ff83
- BinaryEdge ARD Scan: https://app.binaryedge.io/services/query?query=port:3283%20product:%22Apple%20Remote%20Desktop%22%20protocol:udp&page=1
- KrebsOnSecurity GRE Flood: https://krebsonsecurity.com/2016/09/krebsonsecurity-hit-with-record-ddos/
- Akamai WS-Discovery Research: https://blogs.akamai.com/sitr/2019/09/new-ddos-vector-observed-in-the-wild-wsd-attacks-hitting-35gbps.html
- DDOSarrest CLDAP: https://www.dosarrest.com/ddos-blog/cldap-reflection-attacks-back-in-style-for-the-spring-2020-collection/
- Akamai CLDAP: https://www.akamai.com/us/en/resources/our-thinking/threat-advisories/connection-less-lightweight-directory-access-protocol-reflection-ddos-threat-advisory.jsp
- Portmapper Amplification: https://threatpost.com/reflection-ddos-attacks-abusing-rpc-portmapper/114318/
- Meetup Extortion Email: https://threatpost.com/meetup-com-back-online-after-ddos-attacks-extortion-attempt/104625/
- DD4BC Extortion Email: https://www.akamai.com/us/en/multimedia/documents/state-of-the-internet/dd4bc-operation-profile-bitcoin-extortion-ransom-case-study.pdf
- Memcached Extortion Message: https://www.cybereason.com/blog/memcached-ddos-attack
- Cozy Bear Extortion Letter: https://blogs.akamai.com/sitr/2019/11/fake-cozy-bear-group-making-ddos-extortion-demands.html
- Akamai DDoS Extortion Stats: https://blogs.akamai.com/2020/12/cyberweek-2020-attracted-both-online-shoppers-and-ddos-attackers.html
- Fancy Lazarus 2021: https://www.proofpoint.com/us/blog/threat-insight/ransom-ddos-extortion-actor-fancy-lazarus-returns
- BulletProof DDoS 2019 Study: https://www.bulletproof.co.uk/industry-reports/2019.pdf
- High impact DDoS Incidents: https://www.cloudbric.com/blog/2021/04/most-notorious-ddos-attacks-in-history-2021-update/
- NZX DDoS Attack: https://www.zdnet.com/article/ddos-extortionists-target-nzx-moneygram-braintree-and-other-financial-services/
- DD4BC Case Study: https://www.akamai.com/us/en/multimedia/documents/state-of-the-internet/dd4bc-operation-profile-bitcoin-extortion-ransom-case-study.pdf
- DD4BC Arrest: https://www.europol.europa.eu/newsroom/news/international-action-against-dd4bc-cybercriminal-group
- Armada Collective 2015: https://blogs.akamai.com/2015/11/operation-profile-armada-collective.html
- August 2020 DDoS Extortion Fancy Bear: https://blogs.akamai.com/sitr/2020/08/ransom-demands-return-new-ddos-extortion-threats-from-old-actors-targeting-finance-and-retail.html
- Akamai Cozy Bear: https://blogs.akamai.com/sitr/2019/11/fake-cozy-bear-group-making-ddos-extortion-demands.html
- CERT NZ Cozy Bear: https://www.cert.govt.nz/it-specialists/advisories/ddos-extortion-campaign-targeting-financial-sector/
- Proofpoint Fancy Lazarus: https://www.proofpoint.com/us/blog/threat-insight/ransom-ddos-extortion-actor-fancy-lazarus-returns
- Improved DDoS Recon: https://blogs.akamai.com/2020/10/2020-ddos-extortion-campaign-a-sequel-more-thrilling-than-the-original.html
- DDoS Recon Internal Systems: https://searchsecurity.techtarget.com/news/252495371/Akamai-Extortion-attempts-increase-in-DDoS-attacks
- Renting a DDoS Botnet: https://www.enisa.europa.eu/publications/enisa-threat-landscape-2020-distributed-denial-of-service
- DDoSaaS: https://securelist.com/the-cost-of-launching-a-ddos-attack/77784/
- DDoS attack estimates: https://www.a10networks.com/blog/5-most-famous-ddos-attacks/
- DDoS Tools: https://github.com/NewEraCracker/LOIC
- DDoS New Attack Vectors: https://www.zdnet.com/article/fbi-warns-of-new-ddos-attack-vectors-coap-ws-dd-arms-and-jenkins/
- DDoS Attack on Panix: https://archive.nytimes.com/www.nytimes.com/library/cyber/week/0914panix.html
- Mafiaboy Interview: https://www.npr.org/sections/alltechconsidered/2015/02/07/384567322/meet-mafiaboy-the-bratty-kid-who-took-down-the-internet
- Operation Chanology: https://www.embeddedcomputing.com/technology/security/network-security/the-history-and-evolution-of-ddos-attacks
- Meetup DDoS Extortion: https://threatpost.com/meetup-com-back-online-after-ddos-attacks-extortion-attempt/104625/
- FBI DDoS Extortion Alert: https://www.documentcloud.org/documents/7070798-FLASH-MU-000132-DD.html
- OVH Mirai Attack: https://twitter.com/olesovhcom/status/779297257199964160/
- OVH Mirai Attack Capacity: https://www.a10networks.com/blog/5-most-famous-ddos-attacks/
- August 2020 DDoS Extortion Groups: https://www.radware.com/security/ddos-threats-attacks/threat-advisories-attack-reports/global-ransom-ddos-campaign-targeting-finance-travel-ecommerce/, https://blogs.akamai.com/sitr/2020/08/ransom-demands-return-new-ddos-extortion-threats-from-old-actors-targeting-finance-and-retail.html
- DDoS Extortion Activity Resumes: https://www.proofpoint.com/us/blog/threat-insight/ransom-ddos-extortion-actor-fancy-lazarus-returns
- DDoSaaS Cost: https://www.digitalshadows.com/blog-and-research/the-evolution-of-ddos-activity-in-2020/
- F5 DDoS Research: https://www.f5.com/labs/articles/threat-intelligence/ddos-attack-trends-for-2020
Read more 











