Several operational challenges plague the IT security teams in companies today. To protect themselves from an ever-growing number of cyber-attacks, companies have deployed too many security products, which are generating too many alerts, and they do not have enough IT staff with cybersecurity skills to triage and respond to these alerts.
- Too Many Products: Large enterprises have deployed 30+ security products on an average, and they have staff or expertise to manage only 12 of them.
- Alert Fatigue: 92% of companies get more than 500 alerts per day. A single security analyst can handle only 10 alerts per day.
- Cybersecurity Skills Shortage: The global IT security skills shortage has surpassed 4 million, according to ISC2. Only 4% of the alerts get investigated – there are not enough humans to keep up with the security alerts.
Need for SOAR to Speed Up Incident Response
IT security organizations are looking for ways to improve threat detection efficiencies and speed up incident response by replacing repetitive manual tasks with automated workflows, so a limited set of security analysts can focus on the tougher security problems that truly require their deeper analysis and triage skills.
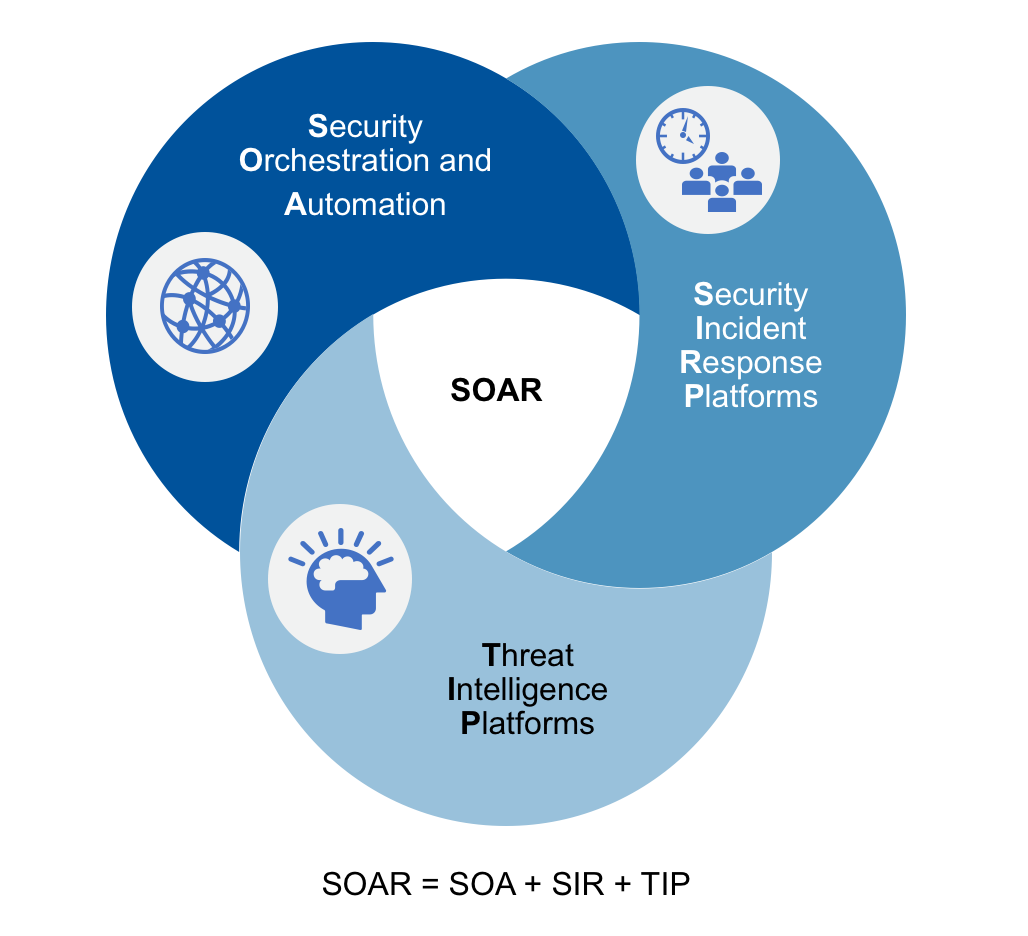
Gartner defined the market segment of security technologies/solutions that enable IT security to reduce the incident response time by taking mitigation actions using automated workflows as Security Orchestration Automation and Response (SOAR). Such solutions can be achieved by integrating security products that detect security incidents with products that can respond to these incidents using automated scripts/APIs.
SOAR solutions represent a substantial leap forward in cybersecurity, by automating the mundane mitigation tasks to reduce the meantime to respond to an incident. It includes a combination of technologies that provide the following types of functions as shown in Figure 1 below.
- Security Orchestration and Automation (SOA): technologies that handle the orchestration and automation of workflows using scripted playbooks, processes, policy execution and enables reporting.
- Security Incident Response (SIR): enables organizations to apply some form of enforcement to mitigate the threat. Some may lockout a user whose credentials have been compromised or quarantine an infected laptop that is beaconing to a C&C server.
- Threat Intelligence Platforms (TIP): take one or more threat feeds and curate them by analyzing further looking for unusual patterns to mine valuable data that can be used to respond to a threat.
Figure 1: Gartner SOAR Solution Types
Infoblox Contextual Intelligence
To fully deliver the promise of SOAR, you need contextual data and precise visibility into the network activity associated with the rogue user/system/device. This can be obtained from the deep contextual intelligence gathered by the network infrastructure services – Domain Name Service (DNS), Domain Host Control Protocol (DHCP), and IP Address Management (IPAM) in the Infoblox DDI platform – collectively referred to as ‘DDI’.
As shown in Figure 2, Infoblox can provide SOAR solutions with crucial device and security event information automatically and in real-time. On receiving data on IP addresses, network devices, and malicious events from Infoblox, any SOAR platform can use that data to block or unblock domains, check information on IP, host, network, and domains and enrich other security tools in the stack with that information.
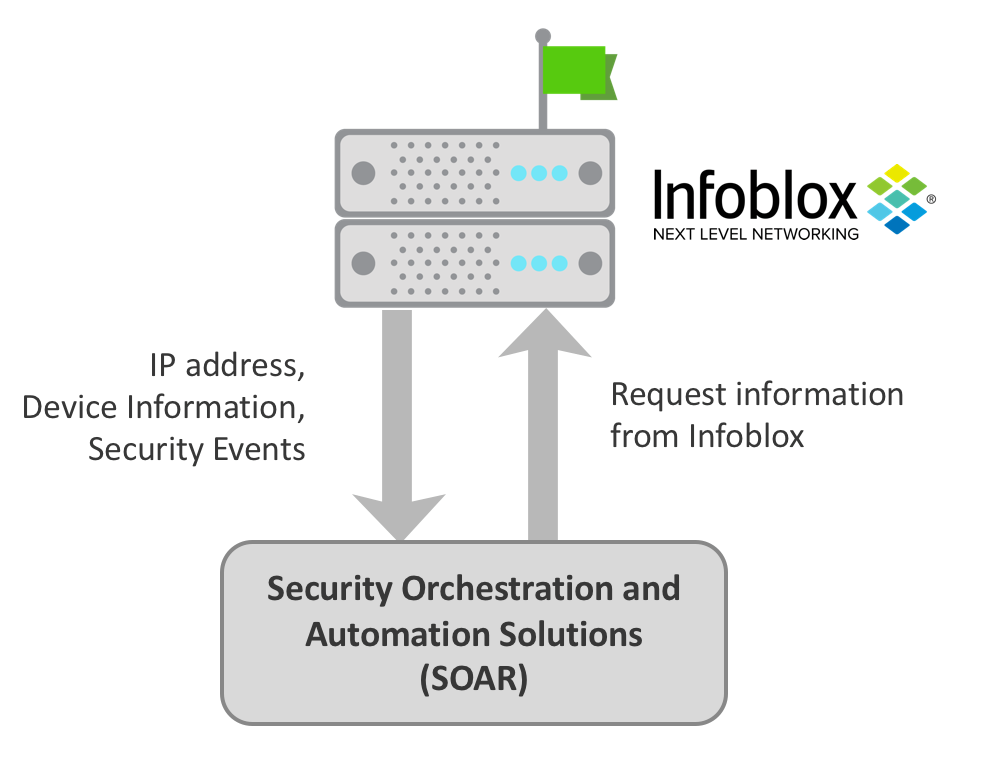
Figure 2: Infoblox Data Integration with SOAR
While the Infoblox BloxOne™ Threat Defense security solution enables threat intelligence sharing throughout the security stack, and delivers many unique automation capabilities, it integrates with partner solutions, including SOAR solutions, with the understanding that our security stacks must better coordinate to address the realities of modern security requirements.
Infoblox Partner Integrations Powering SOAR Solutions
Infoblox Ecosystem Exchange is a set of partner integrations that enable organizations to eliminate silos, optimize SOAR solutions, and improve the ROI of their cybersecurity ecosystem of multi-vendor products.
Infoblox offers more than 30 API-level partner integrations to power SOAR solutions as shown in Figure 3 below, enabling IT security and network teams to reap the following benefits:
- Reduce cost associated with manual intervention and human errors
- Decrease the time to remediate by two-thirds with automated api-based response
- Make threat analysts three times more productive by providing contextual intelligence
- Get better ROI on existing security and network investments
- Optimize SOAR solutions by automatically sharing contextual threat information
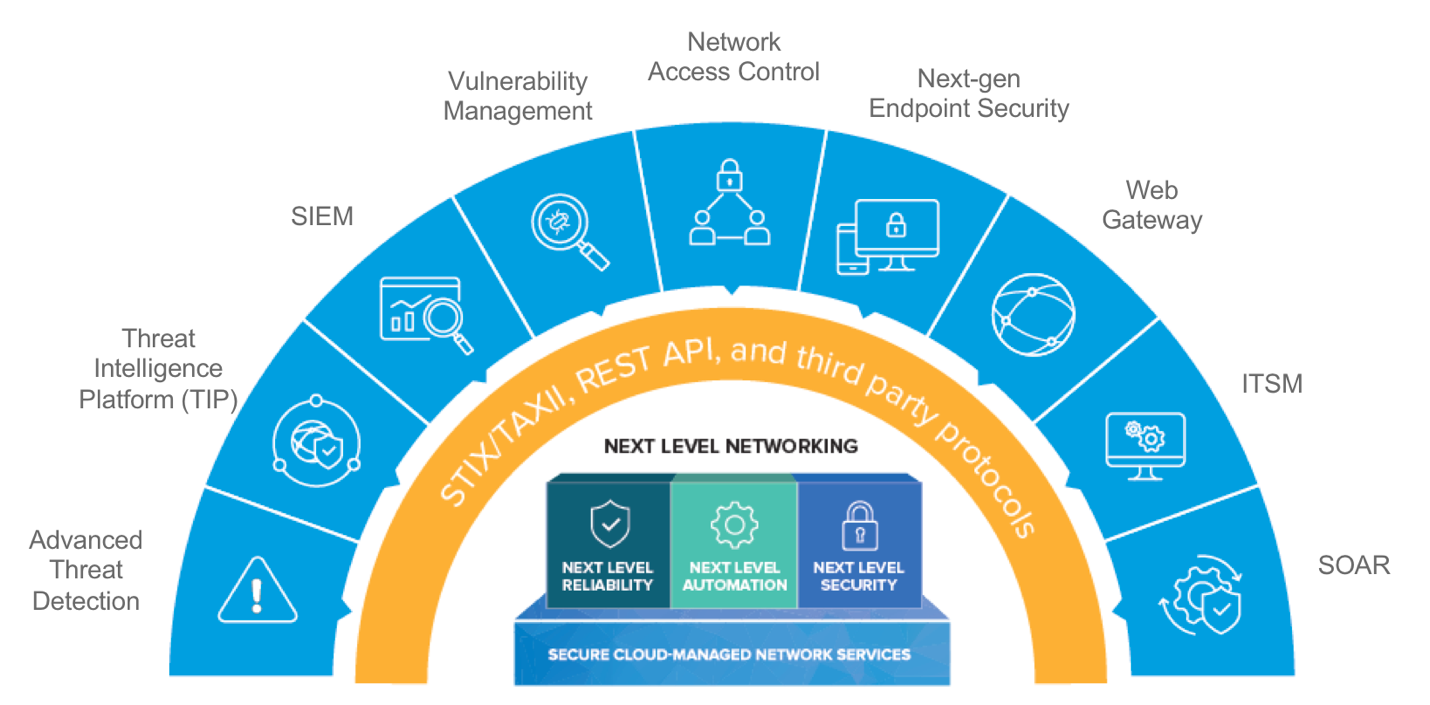
Figure 3: Infoblox Ecosystem Exchange: Set of Partner Integrations Powering SOAR
To better illustrate the extent of integrations Infoblox enables, let’s take a look at the top 5 partner solution areas that enable IT security organizations to better mitigate advanced threats and improve incident response leveraging the ecosystem of security products that you may have already deployed in your enterprise.
| Ecosystem Technology | Integration Overview | Benefits |
| Next Generation Firewall
(Palo Alto Networks) |
· Infoblox sends IP address, domain-name, URL of command & control server to NG Firewall.
· NG Firewall blocks network traffic malicious C&C server to stop data exfiltration |
· Provides vital context for threat prioritization
· Speeds up incident response by automatically blocking malicious traffic
|
| NG Endpoint Protection
(Carbon Black, McAfee ePO) |
· Infoblox detects DNS based malware communication and informs NG EPP technology · NG EPP can kill rogue process and quarantine the endpoint |
· Prevents DNS based endpoint communication to malicious domains
· Automatically responds to endpoint threats by reducing dwell time |
| Web Gateway
(McAfee) |
· BloxOneTM Threat Defense blocks DNS based data exfiltration, as well as DNS requests to malicious domains, before forwarding traffic to McAfee Gateway
· Web Gateway scans web traffic for further inspection with URL filtering, SSL and more |
· Provides broader protection by unifying domain blocking and application (http) security
· Speeds detection of malicious traffic originating from infected endpoints regardless of location |
| Threat Intelligence Platform (TIP)
(ThreatConnect, Cisco Threat Intelligence Director, Checkpoint ThreatCloud) |
· Infoblox Threat Intelligence Data Exchange (TIDE) sends information on malicious host names, IP address and URLs to the TIP platform
· TIP acts a repository of threat intelligence that other security products can query and take action |
· Curated information in TIP reduces false positive
· Improve situational awareness of network and security organizations |
| Security Information and Event Management (SIEM)
(LogRythm, Splunk McAfee, IBM QRadar, Micro Focus ArcSight) |
· Infoblox sends context intel – IP address of infected device, suspicious DNS requests/ responses to SIEM
· SIEM uses this information to do threat analysis and take action |
· Provides visibility into suspicious device activity
· Supplies context for more accurate prioritization |
Learn more about the rest of 30 or more Infoblox partner integrations by reading the solution note on Infoblox Ecosystem Exchange.