Network security teams know that getting visibility into the activity of your organization’s devices can be a monumental challenge. The growing influence of bring your own software, or BYOS, can make things even worse. BYOS can bring a lot of concerns to security teams, particularly Shadow IT, Insider Threats, and maintaining Compliance.
Here are some basic explanations of what these challenges are:
- Shadow IT is when a user installs and uses their own software or cloud application without ITs knowledge or approval. These apps may or may not be secure, or even permitted by corporate policy.
- Insider Threats, where users exfiltrate data from your organization by using their personal cloud storage account, or via other means. This type of action may be benign, or worst case, malicious.
- Compliance, where some governing bodies have regulations that may require monitoring and tracking application use, or an organization may need to restrict certain applications to avoid going afoul of certain regulations. If an organization fails to comply with compliance mandates they may lose the ability to do business with certain entities/regions.
What are some ways of gaining insight into application usage, and solving these concerns? Sure, you could block what your users have access to, but sometimes that just isn’t possible. For example, a business partner might require the usage of a specific cloud storage platform, or web conferencing software. Thankfully, Infoblox® has released a new feature called Application Discovery in BloxOne™ Threat Defense® that can help.
As you may know, a key strength of BloxOne Threat Defense is that it can leverage existing DNS infrastructure to gain insight into user and device activity. Application Discovery leverages this unique position to discover what applications are in use in your organization. Sally is using a Cloud storage platform that puts your organization at risk? You can see that! Drew is using a VPN that prevents you from seeing their internet traffic? You can see that! Best of all, using it is as easy as logging in to the Infoblox Cloud Services Portal if you have the BloxOne Threat Defense Advanced license.
As noted before, it can be extremely difficult to simply ‘block’ every application that might pose a risk. So the primary benefit of this feature is the visibility it gives you to understand what applications are in use, how often, and by whom. In many cases, this tool helps reveal applications that are truly necessary for conducting business even if it is just a cloud file sharing site that is required for only one specific partner. IT can work with users to officially recognize (and secure) some applications, and other users may simply need to be educated on the availability and use of already approved applications to change their behavior. However, when harsher methods are called for, Application Discovery can be used to identify applications as ‘approved’ or ‘unapproved’, and provides options to allow, alert, log or block access as necessary.
To access Application Discovery, log in to the CSP, and navigate to Reports → Application Discovery.
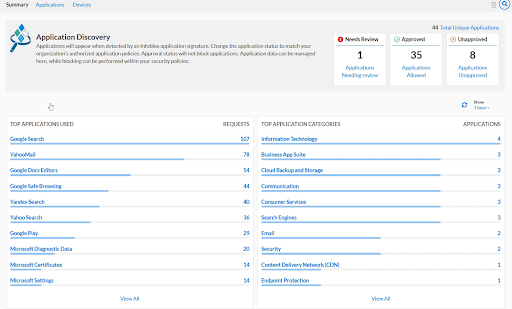
In the Application Discovery interface we can view a variety of tables containing the following information: top applications, categories of applications used, top applications that are needing review, top devices that are using unapproved applications, and top unapproved applications. Here and on the Applications page, highlighting an application will show more information about it. Also, clicking any hyperlinked text will take us to the Applications tab with a filter that matches the hyperlink that was clicked.
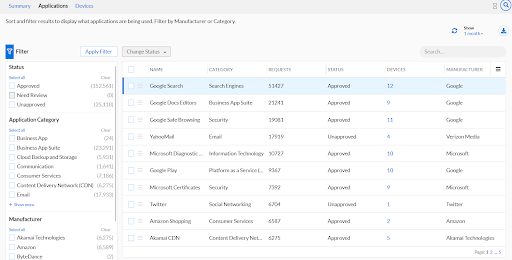
On the Applications tab we can drill down into the data that was summarized on the Summary tab. On this page we can filter based on the status of the application, the application category, and manufacturer of the application. For each individual application we can view its name, category, amount of requests made, status, devices that have accessed it, and the manufacturer.
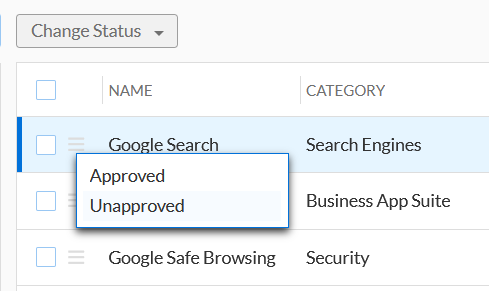
By clicking on the hamburger icon of any application we can choose to assign it as Approved, or Unapproved. Note that this action alone does not designate whether or not a device can access this application, but it helps us filter on the summary page. This information can prove to be invaluable for security teams in helping them in their investigation and response activities, reaching compliance, and monitoring both Shadow IT and insider threats.
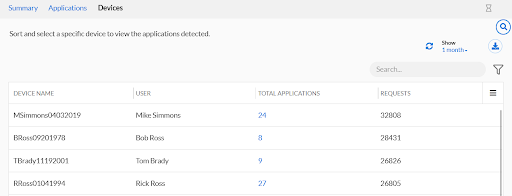
Finally, the Devices tab allows us to see a breakdown of each device’s application usage.
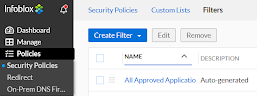
So let’s say you’d like to block all unapproved applications, or maybe log all email usage. Well, application filters can help accomplish that. Navigate to Policies → Security Policies → Filters (tab).
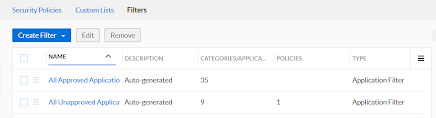
On this page we can see a couple predefined Application filters: All Approved Applications and All Unapproved Applications. As you’d guess, these filters are populated with the approved and unapproved applications from BloxOne’s Application Discovery.
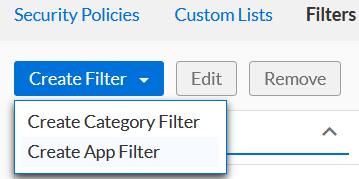
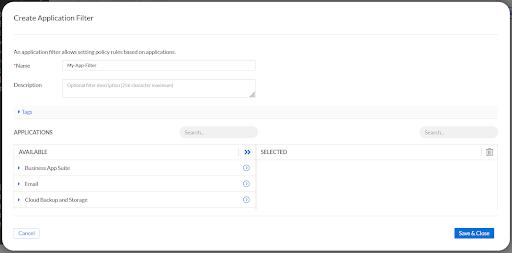
You can even create your own filters if desired. This is easily done by clicking Create Filter, then selecting Create App Filter in the drop-down
In the Create Application Filter panel you create a filter with any of the predetermined application types.
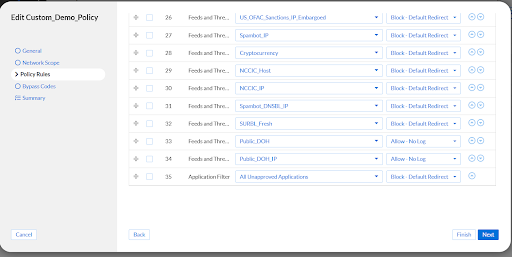
Adding an application filter to a security policy is similar to adding a custom list, or a feed to a policy. In the Policy Rules tab of any policy Application filters can be added. In the screenshot you can see that I added the automatically generated ‘All Unapproved Applications’ list, and set it to block with a redirect (and logging).
With BloxOne’s Application Discovery you can easily enhance your security toolkit. Application Discovery provides IT with tools to quickly filter activity in reports to get useful insights and make informed policy decisions about applications to allow, block, or to simply monitor. By leveraging this tool you can better protect against Shadow IT, Insider Threats (intentional and accidental), and prove your organization’s compliance. If you’d like to know more about Application Discovery, check out the Application Discovery feature solution note, this short video on: https://www.youtube.com/watch?v=Ohg1TblE_fU, or review the Application Discovery documentation at docs.infoblox.com.









