Overview
As the layers of traditional security perimeters are changing, how we give access to a user is shifting from trust based on the location in the network to trust based on how we identify and authenticate a user. Validating a user’s access and authentication helps to determine whether an individual or a system is, in fact, who they declare they are. Organizations trying to manage their cyber maturity controls are looking for efficient and cost-effective ways to define and implement security access authentication controls to manage risk. This includes investing in security measures like multi-factor authentication, single-sign-on (SSO), managing incorrect access attempts, handling forgotten credential requests and ensuring that the identities are secure, access granted only what’s needed, and changes are logged.
Depending on where the organizations are on their technology roadmap journey, networking and security teams struggle to consistently manage their on-premises and multi-cloud infrastructures, and try to find solutions to the question – “How can we achieve user visibility in our on-premises and multi-cloud infrastructures?”
Challenges
Organizations are struggling to streamline their business processes to improve productivity and security for their identity life cycle management and user access control. With no identity and access authentication management strategy in place, processes are manual and not centralized. Having thousands of cloud applications to govern, limited visibility on tracking and monitoring user access to infrastructures makes it challenging to audit user events and changes.
In the absence of well-defined processes, it is likely that users may have inappropriate or excessive access to systems and services, increasing the risk of unauthorized access/use of systems and data. Having limited visibility on user activity results in delays to detect which user went to a bad domain and happened to perform a malicious activity, lengthening the remediation process to identify compromised hosts and their locations.
Lack of real time visibility could result in malicious code being executed or downloaded, and undetected command and control communications, resulting in compromised access to privileged accounts and making it easy for the threat vector to gain access to systems and data.
The administrative teams manually define user security policies for each role and grant user permissions, which makes it difficult to automate user based security in a large organization with different teams and roles.
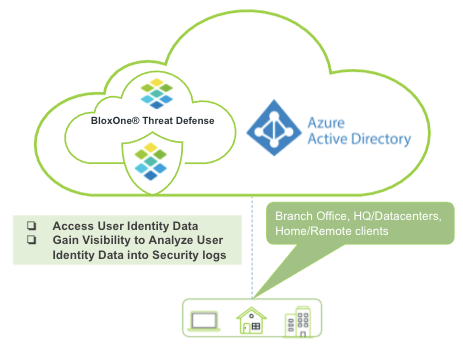
Enhance Visibility and Control Using BloxOne Threat Defense and Azure Active Directory Integration
Infoblox’s joint integration with Azure Active Directory is an effective solution to these challenges. Security teams can achieve user visibility and extend security to detect, block and remediate threats with the joint solution.
Infoblox’s BloxOne Threat Defense seamlessly integrates with Azure Active Directory to authenticate and identify users logging into the BloxOne platform, and assigning security policies based on user groups for appropriate access. The industry-leading cloud-based identity and access management service, Azure Active Directory, delivers single sign-on and multifactor authentication to help protect users and organizations.
Benefits
| Username identification and security policy management
Making it easier for administrative team members to have the sense of trust that the users joining their organization’s network are securely authorized, identify user’s location and track user activity. Also, have the ability to create security policies for user groups to restrict their level of interaction to the open internet. |
| DNS Security and Content Filtering
Being able to monitor and centrally manage all aspects of DNS, helps security and network team members to minimize evolving threats, see the specific DNS queries made by a user and any security events that are triggered and figure out which user was involved. With the ability to manage and gain user visibility, the administrator also gets the flexibility to create custom user group security policies to implement content filtering and block malicious sites to lower the risk of compromise to your organization’s network. |
| DNS Authentication
Authenticate users within Azure Active Directory to access the DNS system. This allows correlation of DNS queries to a specific username within Azure Active Directory, giving administrators a great mechanism for keeping unauthorized users off the network. |
| Threat Detection and Remediation
Gain the ability to detect and block malicious user activity with shortened remediation timelines by identifying compromised users. |
Read more about BloxOne Threat Defense here.