If you are safeguarding a business and its IT systems, you likely know about Security Information and Event Management (SIEM) systems and Security Orchestration, Automation, and Response (SOAR) systems. You have thousands, maybe millions of logs flowing from many different places. You need a central place to normalize and analyze these logs collectively and be notified when suspicious activity occurs.
Sentinel is Microsoft’s cloud security solution. Sentinel simplifies the process of gathering security data across your entire infrastructure, whether it is on-prem, cloud, or both, and normalizing varying formats so that you can aggregate and correlate it all. Sentinel is cloud based, so there is no need to allocate many resources setting up or maintaining it. Not only is it a log management solution, but also offers threat hunting, visualization, investigation, data analyzing, automatic remediation and more. And because Sentinel is built on Azure, and is a product of Microsoft, who dominates the computing market, it offers virtually unlimited compute power, scale, and storage.
When it comes to the rich DNS query and security data provided by Infoblox products, these features of Sentinel prove invaluable. Maybe you wish to do a little more with the logs generated by your Infoblox products than what is available on the CSP. An integration with Microsoft Sentinel and the Infoblox Cloud is built to fit this use case. Using the Infoblox Cloud Data Connector, a part of BloxOne Threat Defense, you can send your DNS query/response and security logs from the BloxOne platform to Microsoft Sentinel to be richly analyzed and monitored.
NEW!!
In addition to gathering DNS and security data, you can also ingest valuable Threat Intelligence Data Exchange (TIDE) indicators into Sentinel as threat intelligence. Threat intelligence can be used to provide essential context to unusual activity so your security teams can take quick action to protect your people and assets. You can even automatically enrich incidents and send emails with TIDE context so you can be as up to date as possible to keep your environment safe.
The Solution
The BloxOne and Sentinel integration is part of Microsoft’s emerging family of Sentinel Solutions, a one-stop shop for deploying templates directly into Sentinel with just a few clicks. The solution is packaged with five components:
- A data connector for getting CDC data into Sentinel.
- A parser to parse all the rich fields provided by the CDC, automatically created for you.
- An interactive workbook to visualize and drill down to the nitty gritty of your CDC data.
- Several analytics queries that check for specific, user-defined anomalous activity and notify you when it occurs.
- Playbooks to ingest various subsets of TIDE data into Sentinel as threat intelligence.
All components are highly customizable should you wish to tweak them to your needs. In fact, it is encouraged to do so!
To use the solution, simply create it from the Azure marketplace or portal, shown in the screenshot below, and content templates begin to appear in your selected Sentinel workspace. Then you can create and enable each component from the templates as needed. So, if you want to use only some of the playbooks and not others for example, you can!
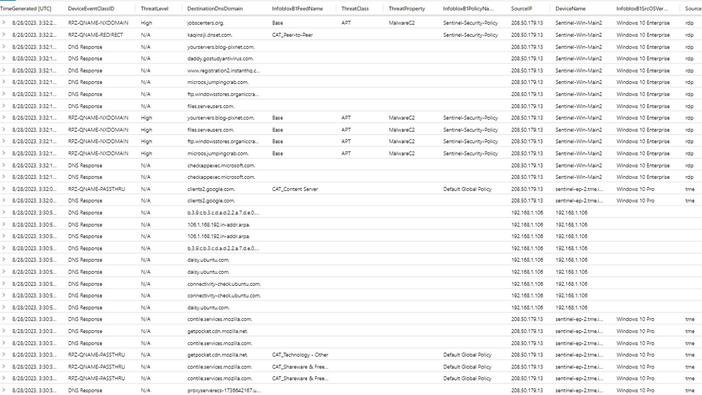
The below screenshots show some BloxOne DNS data ingested and visualized with the workbook in Sentinel.
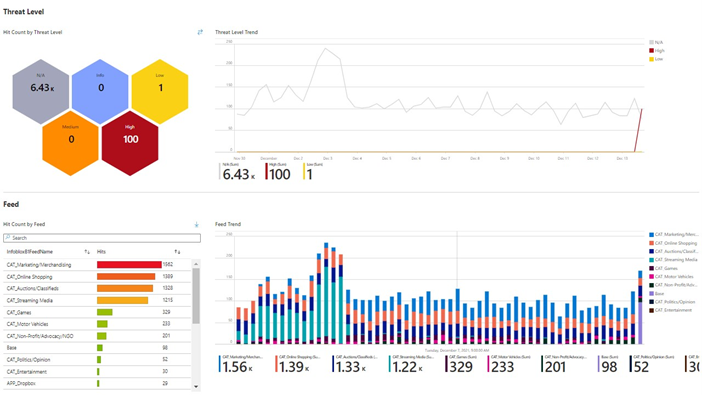
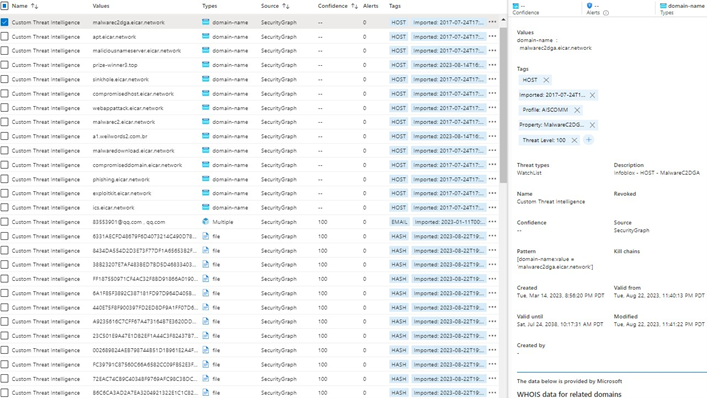
Here’s how the TIDE threat intelligence can be viewed in Sentinel.
Requirements
You’ll need a few things to get started.
- A Microsoft Sentinel account. You can register for a free trial on Microsoft’s website to try the solution out.
- A Sentinel subscription, resource group and Log Analytics workspace.
- An Infoblox Cloud Data Connector, which is a part of BloxOne Threat Defense. Find a quick start guide for deploying one, as well as other licensing and requirements info here.
- A Linux machine for installing the Microsoft log forwarding agent onto.
- If desired, a TIDE API key for ingesting TIDE data into Sentinel. You’ll also need to perform a couple extra steps to deploy and enable the playbooks found here.
Follow the simple deployment instructions packaged with the data connector, and CDC logs will start appearing in the Log Analytics workspace. Maximize your data with the accompanying workbook and analytics queries. Protect your environment with rich TIDE context. Try the solution out today!