IoT, in all its forms including Industrial IoT, is fighting enterprise CISOs and CIOs in every possible way. The explosion of enterprise IoT–much of which is unauthorized and therefore Shadow IT–undercuts cybersecurity, compliance and data maps.
There are indeed ways to better track and control IIoT, approaches that can not only improve security and compliance, but can also boost efficiency, revenue and profits.
And as bad as IIoT problems are today, as 5G grows and gets deployed in more areas, the problems will sharply grow unless new approaches are implemented.
What are the key IIoT problems?
The tiny devices themselves are powerful and have, depending on various factors, access to enterprise networks, enterprise data and other assets, the ability to share that information outside the enterprise at whim (and can sometimes do it without even touching an enterprise LAN, which helps it avoid detection) and is often unknown to the appropriate authorities within in IT and Security.
One of the most frightening IoT problems (which absolutely impacts IIoT as well) is some form of Shadow IT. That is precisely what causes the visibility IoT problem for IT and Security. This can come from people in Facilities or Maintenance purchasing seemingly innocuous items such as lightbulbs or door locks. They think “I’ve been buying lightbulbs for this company for decades and I’ve never needed approval from IT.”
Then there are employees in a line of business that thinks nothing of purchasing a network extending router to make it easier to maintain a strong signal–oblivious to the fact that IT doesn’t know about and it therefore can’t protect it or protect the enterprise from it.
In short, the two security issues are unauthorized IoT devices (Shadow) and authorized IoT devices that exceed their authority, either by design or because an attacker has hijacked the IoT device. IoT devices forming botnets are worrisome and have been used recently to launch high-bandwidth DDoS attacks.
And as has always been the case, when Security has an issue, Compliance has an issue. Compliance needs all sensitive/protected data/assets to be protected, which means the enterprise authorities need to know about it. With IIoT issues, they don’t know about all of it, which is inviting yet more problems.
Industrial IoT shares the same security/compliance/visibility issues that does IoT, but because of the mission-critical nature of many IIoT systems, problems in IIoT can hurt the enterprise financially in ways that other forms of IoT can’t. Both can hurt the enterprise financially, but the nature of that impact differs. An IIoT problem can halt an assembly line, cutoff ships from the rest of the supply chain, can disrupt essential factory controls (such as sharply boosting the plant floor heat in an ice-cream unit). IIoT relies on data from many sensors, controllers, and attached servers, often across multiple, remote locations.
But the nature of IIoT provides some differences beyond the security/compliance/visibility issues. 5G will help facilitate critical IIoT use cases that require reduced latency, greater network throughput, reliability as well as improving data processing efficiencies. Unlike traditional IoT, IIoT demands will require many data processing tasks to be pre-performed at the telco edge and potentially even at the source rather than conventional cloud computing data centers.
The emergence of 5G is a wonderful development, helping to deliver robust communications with remote geographies. But 5G’s added speed just adds complexities to the IoT and IIoT problem. Even worse, the reliance on traditional cloud computing infrastructures for IIoT data processing no longer matches the needs of a complex IoT ecosystem that requires real-time data processing. IIoT relies on data from many sensors, controllers, and attached servers, often across multiple, remote locations.
Because of these and other factors, IIoT is going to move into 5G and away from private and shared enterprise clouds.
The good news is that 5G, done properly, can help security, compliance and revenue in several ways, including enabling far better content filtering and threat detection. For example, it is a lot easier to slice up 5G bandwidth for IIoT purposes than it is to do it in the cloud. This would allow retaining a dedicated slice of 5G for IIoT, a slice that won’t be impacted by how others use the rest of the 5G.
Consider emergency services. Today, a major emergency can severely tax communications. Perhaps it is a major flooding situation. At the precise moment when law enforcement, fire/rescue, ambulances need to communicate with each other and their various headquarters and hospitals, bandwidth can often plummet as worried residents call each other checking on friends and relatives. With 5G, emergency personnel can be issued their own slice of 5G, one that would be immune to bandwidth demands of anyone outside that group.
Or consider telcos. What if telcos offered a seamless security protection for their IIoT customers as a value-add to Internet services, one designed to protect users from IIoT issues on a massive scale?
IT and Security executives are well known for their abilities to project operations out for several years, predicting what their defenses and attack patterns (i.e. the threat landscape) are going to look like. But it’s just as critical to look at network communication issues.
Beyond 5G, encrypted DNS is increasingly becoming common, and HTTP/3 is getting close. Those are both going to seriously change the security and compliance realities for enterprises. And it’s not entirely under the control of any one enterprise. Clearly, enterprise teams can control whether/when their enterprise will embrace 5G, encrypted DNS and HTTP/3. But they can’t control what their competitors, suppliers, distributors and customers do. If everyone else makes the move, their landscape will change regardless of what they do. And if everyone around them makes the move, the odds are powerful that they will, too. Just like the networks themselves, the enterprise decisions about networks are also interrelated.
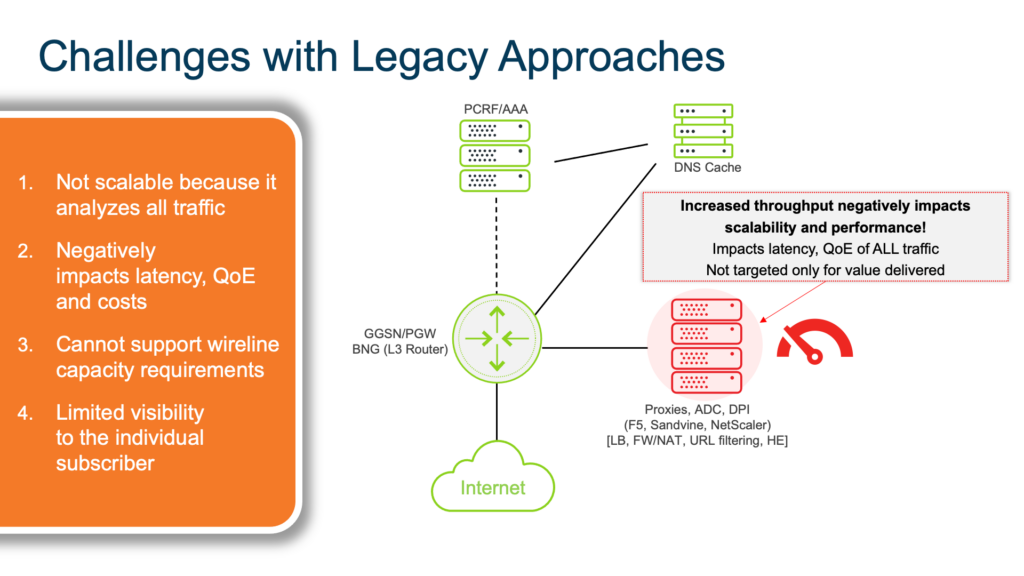
The good news is that enterprises can fare far better in this move to 5G–as well as encrypted DNS standards such as DNS over HTTPS (DoH) and potentially HTTP/3–by better leveraging their existing DNS data. DNS looks at behaviors and can then control that behavior if something bad is detected. DPI and Proxies might always be needed to some degree, but a DNS approach can do a ton of the work and augment DPI. A DNS approach might be able to handle 90 percent of detection and control, and only funnel 10 percent of the traffic to the DPI for additional analysis. That’s actually protecting your existing DPI investment.
Leveraging DNS is a more efficient way to see threats and stop attacks far earlier in the lifecycle. Traditional approaches leveraging deep packet inspections or proxies are subject to a severe limit on scalability, which can end up hurting an enterprise’s cost model. The old way is tolerable in 4G, but it falls apart in 5G. With over 80 percent of web traffic being HTTPS, traditional approaches lack visibility due to encryption. DNS can handle encrypted traffic, encrypted DNS protocols and can detect IIoT activity in ways that traditional approaches simply can’t.
When IT relies on traditional methods like DPI or proxy servers, they are forced to analyze all subscriber traffic. From a telco’s perspective, that’s bad. That means that the telco must deploy *a lot* of DPI/Proxies in order to accommodate an ever-increasing number of devices. And to scale? They’ll need to add *even more*. It kills telco business cases.
It’s one thing to think about 5G smartphones, but it’s another to consider what will happen when providers deploy Home 5G (or Business 5G) endpoints to homes and businesses that replace traditional cable/fiber broadband services. Consider all the devices in a typical home or small business. Those traditional DPI or proxy server technologies encumbered telcos to focus on their wireless users and not their wireline broadband users because of these scalability limitations–further limiting their reach and ultimately their revenue potential.
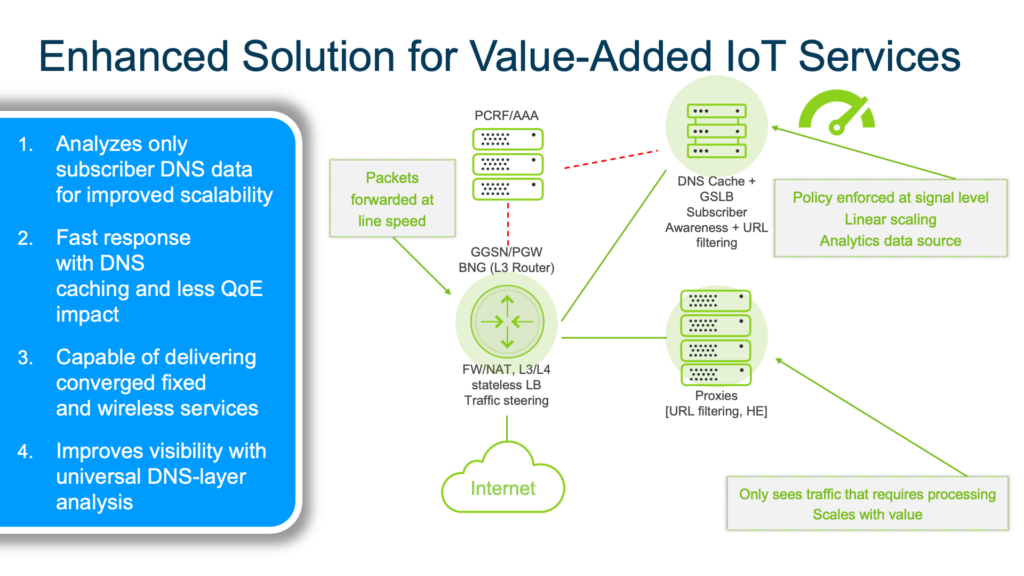
By using DNS, the only need is to analyze the DNS requests and not the traffic nor packets. Policies are enforced at the signaling level. Telcos can also segment their services to those subscribers paying for the service. Given that the telcos then do not need to worry about everybody and everything, it can reduce up-front investments while improving what it takes to scale.
It is essential that systems used to manage and control the nodes and devices provide consistency and efficiency and a unified view of the network. That is something DNS scans can deliver in a way that other existing technologies can. That is a strong benefit today, but with tomorrow’s technologies including 5G, encrypted DNS and HTTP/3, DNS scanning will become essential.









