Working from home could be the “new norm” for a little while. Companies, in order to ensure social distancing among their employees and curb the spread of COVID-19, have mandated that all non-essential workers stay and work out of their homes. Most conferences have been canceled, with the business impact of the cancellation of major tech events topping $1 billion in direct economic losses.
Given the precipitous nature of the pandemic, organizations have had very little time to prepare for such large-scale remote work, let alone think about how to secure ‘work from home’ users. These remote workers still need to access enterprise applications in the cloud, and work with and store corporate data on their devices.
Think Outside the Perimeter – Security Challenges of Working from Home
Security teams now have to think about how to continue to protect corporate resources and data, when most of their employees are not within the corporate perimeter. The existing security stack within the corporate network is no longer sufficient to protect these teleworkers. In addition, teleworking exposes a much broader attack surface as workers use BYOD devices and mobile devices that share home and public Wi-Fi networks, often with a much larger variety of internet of things (IoT) devices than found in a typical work environment. Public Wi-Fi networks present a higher probability that authentication and credentials may be accidentally compromised.
To take advantage of the chaotic nature of these times, bad actors and hackers have been busy launching coronavirus themed cyber-attacks and weaponizing well-known websites that try to provide useful, timely information for the general public. COVID-19 has become the subject line of choice for phishing/spear-phishing campaigns that seek to take advantage of the heightened level of fear and concern.
Let’s take a look at some rising threats that we could encounter.
Rising Threat #1 – Coronavirus Related Malware Campaigns
During the first week of March, our cyber intelligence unit noted that LokiBot infostealer joined the list of malware campaigns being distributed by cybercriminals taking advantage of the fear and interest in the spread of Coronavirus (COVID-19). From March 3rd – 6th 2020, we observed two malicious spam email campaigns distributing LokiBot under the guise of providing information on the Coronavirus impact to supply chains.
LokiBot has become popular with cybercriminals as an information stealer that collects credentials and security tokens from infected machines. LokiBot targets multiple applications, including but not limited to Mozilla Firefox, Google Chrome, Thunderbird, as well as FTP.
The email messages of the primary campaign had two subject lines, one of which alleged to be a supply chain update in the context of Coronavirus (COVID-19). The other subject had a more typical payment transfer theme. Both sets of messages had attached files with the same filename that delivered the malicious code.
Rising Threat #2 – Lookalike Domains
Another threat that could be on the rise is Lookalike Domains. Cybercriminals are moving to lookalike domains to fool victims in their efforts to impersonate the target organization or brand. Often phishing websites feature domains that impersonate the real brand. These are crafted by cybercriminals to resemble the legitimate brand’s domain. Character substitution is a popular technique employed by cybercriminals with the goal of manipulating users into exposing credit cards, passwords, and other sensitive data.
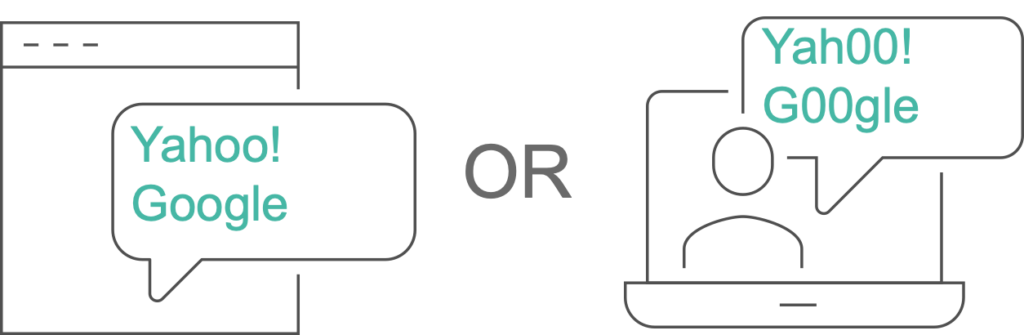
Figure 1 – Lookalike Domains
Researchers also found that cybercriminals are using valid Transport Layer Security (TLS) certificates which is an attempt to make the lookalike domains appear legitimate. In late 2019, researchers note that there were more than 100,000 lookalike domains impersonating legitimate retailers. Industries that can be heavily impacted by these types of attacks are retail and banking, where users typically enter their credentials to execute a transaction.
Rising Threat #3 – Data Exfiltration
Your work from home users are still accessing, interacting with and storing corporate data on their devices, as part of their day to day business operations. But they are now doing it outside the corporate perimeter. That data, even if stored on company-provided devices, could be exposed to theft. DNS tunneling or data exfiltration is an attacker technique that uses malware to gather sensitive data from a compromised system. It packages up the data into small chunks and embeds them within a string of DNS queries. The DNS queries carrying the data are then delivered to a server hosted by the attacker on the Internet, where the stolen data can be easily reassembled.
Rising Threat #4 – Non-Compliant Website Access
While this is not technically an attack or a malicious campaign launched by bad actors, companies could still be faced with the problem of their work from users accessing websites and destinations not in compliance with their policy during working hours using corporate provided devices. This could include websites related to social media, violence and adult content. While it’s second nature for employees working in the office to know that such access is not appropriate or compliant, at home those same employees may have more of a lax attitude.
Securing Work from Home Users with BloxOneTM Threat Defense
While there may be certain solutions available to protect your teleworkers, one of the best and most cost-effective ways to secure such a large scale tele-workforce is using a technology that is the foundation of the Internet – DNS. Every connection to the Internet goes through DNS and work from home users are using public DNS or DNS provided by their service providers. But these providers seldom do security enforcement on DNS. By that I mean, detecting DNS requests to sites that are known to host malware or checking for data exfiltration via DNS.
BloxOne™ Threat Defense from Infoblox protects users, devices, and systems no matter where they are, extending enterprise-level security to remote locations, and work from home environments. It:
- detects and blocks phishing, exploits, ransomware, and other modern malware, preventing teleworkers from accessing malicious web destinations using DNS as the first line of defense.
- blocks access to objectionable content restricted by policy.
- Uses unique patented technology to prevent DNS based data exfiltration and keep protected data safe, and
- monitors for advanced threats including the rising threat of lookalike domains.
Access to the cloud service is through the lightweight Infoblox endpoint agent, which is easy to deploy on your remote users’ devices from the cloud, simple to manage, and securely redirects the endpoint’s DNS to Infoblox cloud for any time, anywhere protection and monitoring.
To learn more about securing remote workers in the age of teleworking, read this whitepaper.
You can sign up for a free trial of BloxOne™ Threat Defense here.