Researchers at Infoblox and Eclypsium have discovered that a powerful attack vector in the domain name system (DNS) is being widely exploited across many DNS providers. We have found that over a dozen Russian-nexus cybercriminal actors are using this attack vector to hijack domain names without being noticed. We call this the Sitting Ducks attack. There are over a million exploitable target domains on any given day, and the attack is:
- Easy to perform
- Almost totally unrecognized
- Difficult to detect
- Entirely preventable

In a Sitting Ducks attack, the actor hijacks a currently registered domain at an authoritative DNS service or web hosting provider without accessing the true owner’s account at either the DNS provider or registrar. Once the actor has control of the domain, they can conduct any form of malicious activity under the guise of the legitimate owner. This includes malware delivery, phishing campaigns, brand impersonation and data exfiltration. Exploitable domains are not rare; we estimate that over a million domains are exploitable on any given day and we have identified multiple methods to identify vulnerable domains.
We discovered Sitting Ducks while studying the infrastructure used for the so-called 404TDS, a Russian hosted traffic distribution system (TDS) first identified by Proofpoint.1 The domains used for this TDS were clearly hijacked, but the breadth of registrars and domain owners involved created a perplexing picture. That is, until we discovered the threat actor’s method. We initially thought the attack vector was unpublished. Recently we learnt that Matt Bryant had previously described the attack vector in his blog, The Hacker Blog, both in August and December 2016.2,3 Two years after his initial advisory, Sitting Ducks was used to hijack thousands of domains for use in a series of global spam campaigns that included bomb threats and sextortion.4
Eight years after it was first published, the attack vector is largely unknown and unresolved. Sitting Ducks is easier to perform, more likely to succeed, and harder to detect than other well-publicized domain hijacking attack vectors, such as dangling CNAMEs.5 At the same time, Sitting Ducks is being broadly used to exploit users around the globe. Our analysis showed that the use of Sitting Ducks has grown unabated over several years and unrecognized in the security industry.
At the heart of Sitting Ducks attacks are incorrect configurations at the domain registrar and the inadequate prevention at the DNS provider, both of which are solvable problems. There are several variants of the Sitting Ducks attack, none of which require the attacker to register a domain themselves, making it fundamentally different from commonly discussed DNS hijacking attacks.
Attackers can use the Sitting Ducks attack vector under the following conditions and in several variations:
- a registered domain or subdomain of a registered domain uses or delegates authoritative DNS services to a different provider than the domain registrar; this is called delegation
- the delegation is lame, meaning that the authoritative name server(s) of the record does not have information about the domain and cannot, therefore, resolve queries
- the authoritative DNS provider is exploitable, meaning that the attacker can “claim” the domain at the provider and set up DNS records without access to the valid owner’s account at the domain registrar
Variations within this attack include partially lame delegation and redelegation to another DNS provider. Figure 1 shows the conditions for a basic attack.
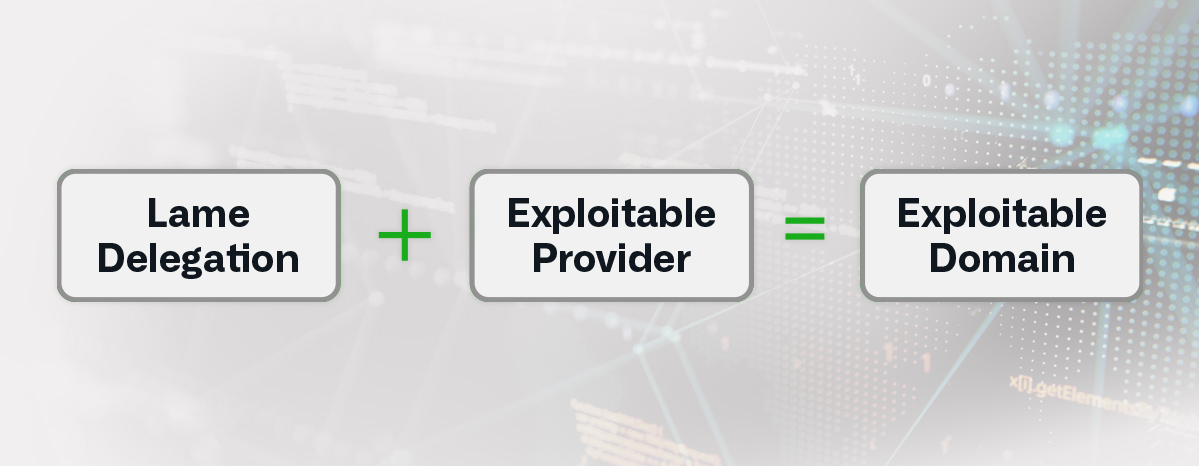 |
| Figure 1. Conditions for a Sitting Ducks Attack |
While these conditions may seem unusual, they are not. Multiple threat actors are actively exploiting this attack vector, and we expect the true exploitation to be larger than is currently known.
Although a Sitting Ducks attack is easy at many popular DNS and website hosting providers, some providers are not exploitable. We performed a large-scale analysis of domain delegations, evaluated about a dozen DNS providers and uncovered widespread use of the attack, most prominently by Russian cybercriminals. Hundreds of domains are hijacked every day, and Infoblox is tracking multiple actors who use this attack.
We found hijacked and exploitable domains across hundreds of TLDs. Hijacked domains are often registered with brand protection registrars; in many cases, they are lookalike domains that were likely defensively registered by legitimate brands or organizations. Because these domains have such a highly regarded pedigree, malicious use of them is very hard to detect.
Figure 2 depicts a common Sitting Ducks attack scenario. In this example:
- a domain, brand[.]com, is registered with Registrar A by Brand Inc.
- the domain owner, Brand Inc., establishes authoritative DNS services with the provider Auth DNS B, which may optionally be the web hosting provider
- the domain brand[.]com is used by Brand Inc. as a website
- after some time, Brand Inc. no longer actively uses the domain brand[.]com, but retains ownership of the domain name through Registrar A
- the authoritative DNS, or web hosting, service for brand[.]com with Auth DNS B expires
- the attacker creates an account with provider Auth DNS B
- the attacker “claims” the domain brand[.]com
- the attacker creates a fake Brand Inc. website and configures DNS at Auth DNS B to resolve IP address record requests to the fake website address
- the attacker sends phishing emails to victims impersonating Brand Inc.
- the victim is infected with malware
- the legitimate domain owner Brand Inc. attempts to configure DNS records for brand[.]com at DNS provider Auth DNS B and is denied
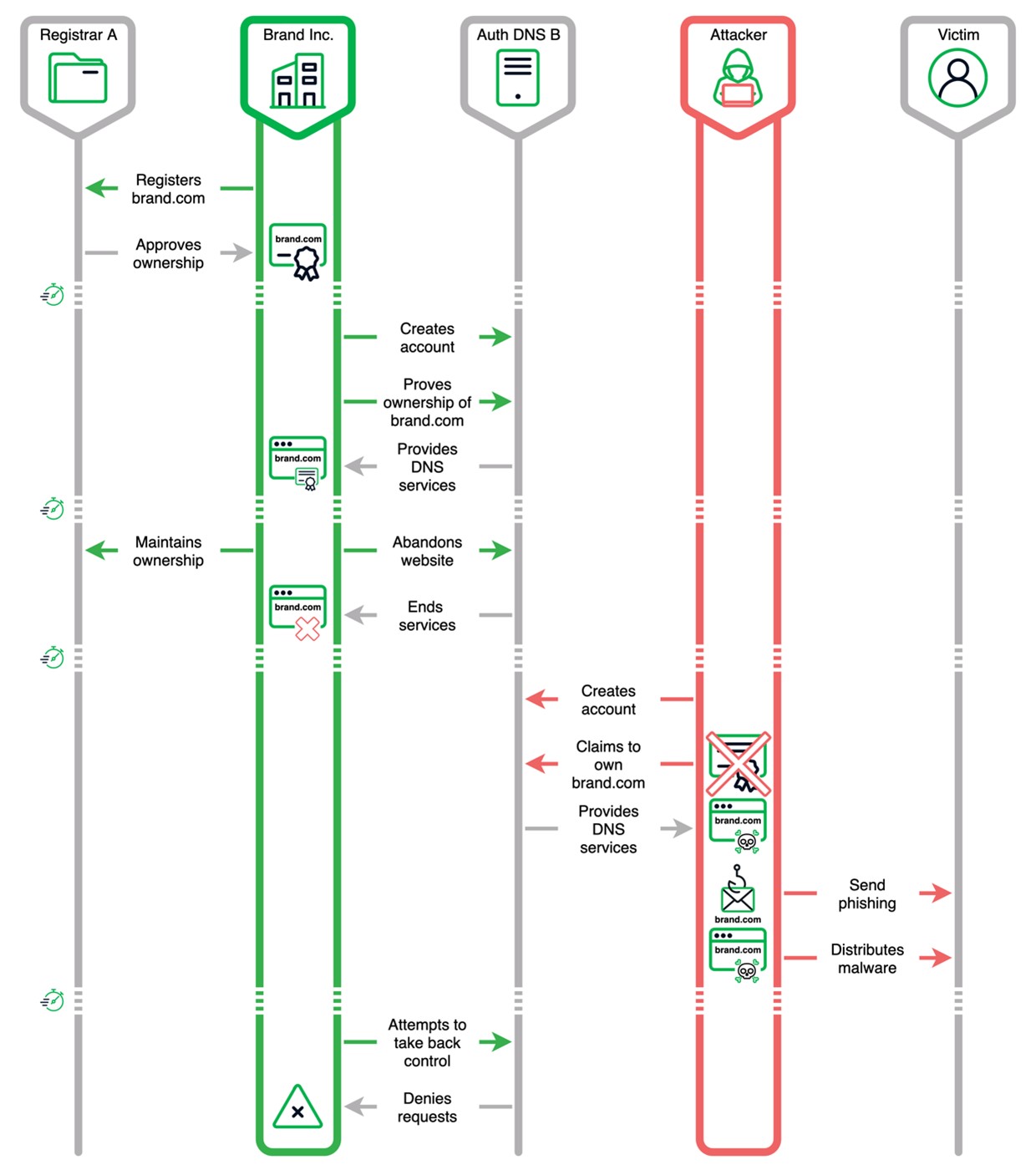 |
| Figure 2. A common Sitting Ducks attack sequence |
Unlike many other types of cybercrime, Sitting Ducks attacks are preventable. The attack is possible because of gaps in how domain names and DNS records are managed, maintained, and authorized. Prevention requires everyone to play a part: domain name holders, registrars, authoritative DNS providers, web hosting providers, standards bodies, government regulators, and the cybersecurity community. Recommendations for addressing the problem are included at the end of this blog.
Our discovery of the Sitting Ducks attack leveraged reporting by Proofpoint, independent research by Randy McEoin, and contributions from David Safley. We are grateful for their information sharing and collaboration. We began ethical disclosure notification shortly after validating the attack vector.
Read the Eclypsium coverage of Sitting Ducks here.
Exploitation in the Wild
We have discovered over a dozen seemingly different threat actors conducting Sitting Ducks attacks on several exploitable authoritative DNS services. Each of these has some Russian nexus and one might argue that certain DNS providers have become a veritable Russian cybercriminal playground that has been allowed to grow unchecked for years. Our research revealed that the Sitting Ducks vector has been used to hijack over 35k domains since 2018, although the true number is likely much higher. The earliest known threat actor is Spammy Bear, who appears to have begun hijacking domains in late-2018 at GoDaddy. However, many more providers are exploitable, and we have confirmed hijacking on six DNS providers to date.
Often, a single domain was hijacked by different actors over time. Some exploitable DNS providers are being treated in essence as a “domain lending library,” where threat actors use free accounts to “borrow” a domain for 30-60 days at a time. The rotational use by different actors creates additional obfuscation that makes Sitting Ducks hard to detect. In other cases, an actor has hijacked domains at DNS providers that do not offer free accounts. Similarly, while those with free accounts are typically hijacked for short periods of time, we have seen threat actors hold a domain for over a year. Frequently the hijackers host the stolen domains on notorious Russian providers such as Stark Industries and Evil Empire.6 Threat actors have obtained SSL certificates for the domains in many cases, both from free services like Let’s Encrypt and paid services like DigiCert.7 In Table 1 we demonstrate the domain lending library concept as different actors hijacked blizzaktires[.]com over time.
| Dates of Use | Malicious IP | Notes |
|---|---|---|
| June 11 – July 11, 2022 | 45.136.49.35 | Suspicious porn TDS transmitted through spam |
| April 4 – May 2, 2023 | 178.250.243.30 | Unknown actor and use |
| June 11 – June 27, 2024 | 81.19.135.241 | Vacant Viper 404TDS |
| Table 1. Demonstration of exploitation of blizzaktires[.]com by different actors over time | ||
There are two sets of victims in Sitting Ducks exploitation:
- the true domain name owners
- and the targets of malicious activity.
Both types of victims vary widely. While a large percentage of the hijacked domains are owned by large brands, many of them belong to small businesses and individuals. Some were registered by regional and local governments. In many cases, the domains seem to have been configured to auto-renew at the registrar, but the authoritative DNS or hosting services were not renewed. We have even seen actors use the Sitting Ducks vector to hijack domains from other threat actors: there is no honor among thieves.
Once the malicious actor has control of the domain at the name server, they can do whatever they like with it, and analysis of confirmed exploitation indicates that the hijackers have done all manner of bad things.
There are multiple traffic distribution systems (TDSs) operating on stolen domains using the Sitting Ducks attack.8 The operators of a TDS serve a criminal customer base, and the role of a TDS provider, like a traditional ad broker, is to connect potential victims to malware, phishing, or scams that suit their victim profile. In addition to the threat actor behind 404TDS, who we call Vacant Viper, we have seen VexTrio Viper hijack domains at multiple DNS services.9 A special form of TDS, there are multiple malicious link shortening services built on hijacked domains.10
Vacant Viper began using Sitting Ducks in December 2019, possibly earlier, and has hijacked approximately 2500 domains each year. In addition to use in 404TDS, they use the stolen domains for spam operations and what appears likely to be command and control (C2) domains. VexTrio first hijacked a domain using Sitting Ducks in early 2020, and several of their affiliates also use the attack vector. TDSs are particularly dangerous as they facilitate cybercrime for hundreds of actors. Vacant Viper is known to affiliate with TA571, for which the 404TDS delivered IcedID and other malware.11 VexTrio Viper runs the largest and oldest known TDS with over 165 affiliates including SocGholish and ClearFake. We have discovered multiple other yet unnamed actors using Sitting Ducks to create a TDS.12
Hijacked domains have also been used directly in phishing attacks and scams, as well as large spam systems. One threat actor appears to use the domains exclusively for shipping-related fraud.13 Multiple actors are using the domains to distribute porn or dating related content.14 There is evidence that some domains were used for Cobalt Strike and other malware command and control. Other attacks have used hijacked domains in targeted phishing attacks by creating lookalike subdomains. A few actors have stockpiled hijacked domains for an unknown purpose.
One of the most active threat actors we have discovered hijacks domains from multiple DNS providers. They distribute investment scams through Facebook ads, and possibly other mediums. These ads have targeted over thirty countries and often use lures of government infrastructure programs and investment summits. We intend to publish more about this actor and their history soon – stay tuned!
A Vulnerable Attack Surface
Sitting Ducks is a pernicious attack that is fundamentally different from other well-publicized techniques designed to take control of domains or subdomains. It requires no access to the registrar and is extremely hard to detect or distinguish from credential theft. Indeed, Infoblox assumed for several months that the hijacking conducted by an actor we were tracking was due to credential theft at the authoritative DNS provider.
As mentioned in the introduction, the earliest known description of Sitting Ducks was in August 2016 by Matt Bryant. We also unearthed a handful of other reports that included special cases or variations of the attack vector.
Group-IB published a special case of Sitting Ducks via Russian media outlets in November 2020.15 The attack they describe involves a lapse in the web hosting provider service, whereas we have observed Sitting Ducks attacks that abuse vulnerable authoritative DNS providers in addition to web hosting providers. According to Group-IB’s blog, the attack vector was reported to Russian registrars and hosting providers, regional registrars, and unnamed international hosting providers. Unfortunately, like Bryant’s alerts in 2016, the attack was not picked up by mainstream media, or in the Russian case, widely reported to the international community.
Sitting Ducks is only the latest example of how attackers exploit misconfigurations in DNS. While DNS serves as the backbone for internet communication, it is often overlooked as a strategic attack surface. Published attack vectors against DNS may be dismissed as inevitable and not receive the same level of mitigation as a software bug, creating a perfect attack surface for malicious actors. Most recently, a default configuration by Squarespace left domain names acquired from Google vulnerable to hijacking.16
In DNS, a lame delegation occurs when a name server is delegated, or assigned, to provide authoritative DNS records but does not have the information to do so. In certain cases, the registration for the delegated name server may have expired. A lame delegation attack occurs when the malicious actor registers the expired name server’s domain name. In this attack, the actor gains control of all domains that point to that name server. In addition to expired name server domains, this attack can leverage typos made by the domain owner when entering their name server information at the registrar. Researchers released an extensive study of the lame delegation attack surface in 2021.17
In our research on Sitting Ducks exploitation, we identified multiple active attacks using typosquat name server domains. These attacks require the actor to register a domain but can be very effective, especially when the delegation is only partially lame, meaning that only some of the name servers are incorrectly configured.
While lame delegation attacks take advantage of faulty name server record assignments, these attacks can be generalized to other DNS record types. A dangling DNS record generally refers to a record containing invalid information, typically due to a forgotten configuration. For example, a dangling CNAME attack takes advantage of DNS CNAME records in which the DNS response “redirects” to a domain name whose registration has lapsed. In this attack scenario, the malicious actor registers the lapsed domain and gains pedigree through the forgotten record. Dangling CNAME attacks typically involve subdomains and are considered a type of subdomain hijacking attack. These attacks are actively used by actors and were the subject of recent reporting by Guardio Labs.18 Dangling CNAME attacks require the actor to register a domain.
Other types of dangling DNS records can be used to hijack domains. Where a subdomain points to a cloud resource that is no longer in use, an attacker may be able to gain access to this resource. Certitude Consulting detailed several examples of this attack in a recent report.19 During our research, we found several instances of dangling A records, some dating back more than five years. These attacks require the attacker to gain access to the hosting resource.
Chinese academic researchers have published multiple studies of dangling DNS records and outlined specific methods for identifying exploitable domains. Their papers include dangling CNAME attacks, attacks against cloud hosting providers and special cases of a Sitting Ducks attack. While these papers do not include active exploitation, they do outline the dangers of dangling DNS records and lame delegation.20,21,22
Domain shadowing is another form of attack that might be confused with Sitting Ducks. This type of attack was highlighted by the U.S. Cyber and Infrastructure Security Agency (CISA) in 2018.23 The attack allows the malicious actor to create new DNS records within the valid owner’s account. Domain shadowing attacks require the actor to access the existing account at the registrar or the DNS provider. Domain shadowing attacks rely on credential theft and are fundamentally different from DNS delegation or record attacks.
Finally, in 2021, researchers demonstrated that in certain cloud providers they could poison the DNS resolution path and gain access to sensitive internal DNS traffic. Their work focused specifically on Amazon Web Services (AWS).24 While the researchers did not find active exploitation of the weakness, it highlighted the complexities of delegated name server management for providers. AWS fixed this issue prior to publication, and it has not been reported as a vector for other providers.
Recommendations
Neither Infoblox nor Eclypsium offers commercial authoritative DNS service, and our product offerings are not vulnerable to this attack. However, our customers may still be impacted depending on how they have chosen to operate DNS for the domains they register. We recommend that all domain name owners evaluate their risk.
Everyone has a role in stopping Sitting Ducks attacks.
We recommend that all domain name owners evaluate their risk, particularly those who have held domain names for over 10 years. Three factors are required to be at risk for a Sitting Ducks attack. Readers can use Figure 3 to determine if they are at risk. Table 1 provides methods to evaluate and mitigate each of the criteria necessary for successful exploitation.
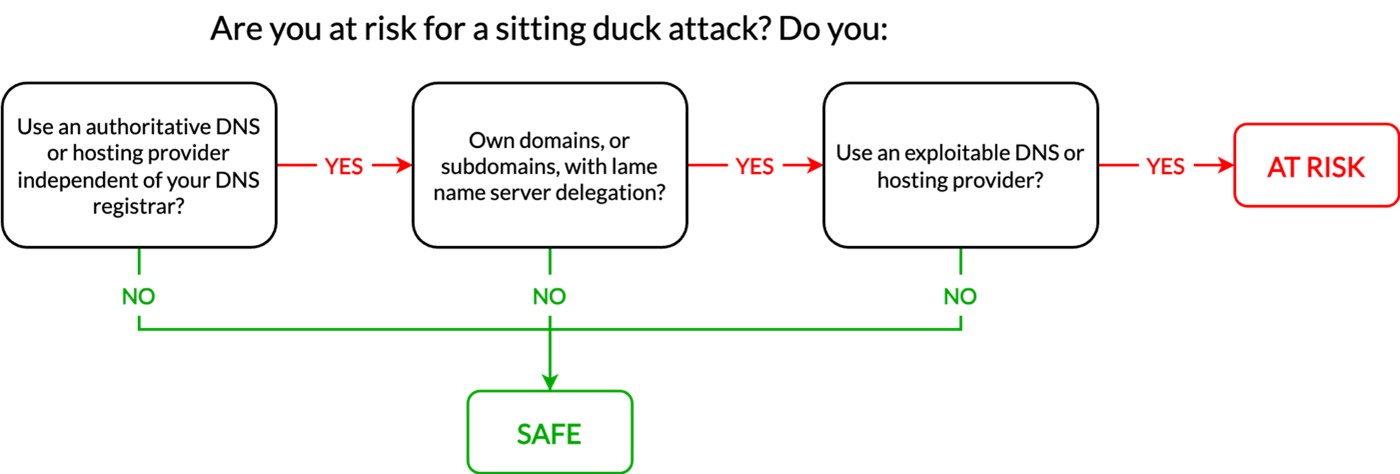 |
| Figure 3. These three questions can help determine if an organization is at risk for a Sitting Ducks attack |
| Exploitation Criteria | Evaluation | Mitigation |
|---|---|---|
| Do you use a commercial authoritative DNS provider independent of your DNS registrar? Do you use a website hosting provider independent of your DNS registrar? | Check the account at the domain registrar for name server delegation. | N/A. External authoritative name server delegation is not inherently a risk. |
| Do you own domains or subdomains with lame name server delegation? These domains or subdomains would point to DNS providers, including hosting providers, where you have no active service agreement. | We urge domain owners to review their name server delegations and ensure that they have active service relationships with any DNS providers in the delegation. We are not providing public information that would allow attackers to identify vulnerable domains. | Replace lame delegation records at the registrar and/or authoritative name server with updated delegation. |
| Can your DNS or hosting provider be exploited via a Sitting Ducks attack vector? | Contact your authoritative DNS or hosting provider to inquire how they mitigate the risks of the Sitting Ducks attack vector. Authoritative DNS providers need explicit measures in place to reduce the risk of these attacks due to their nature. | Replace lame delegation records at the registrar and/or authoritative name server with updated delegation.
Encourage your DNS or hosting provider to follow best practices to prevent Sitting Ducks attacks and to publicly document their mitigations. |
| Table 1. Evaluation and mitigation of Sitting Ducks exploitation criteria: successful exploitation requires all three circumstances to occur | ||
While Sitting Ducks attacks cleverly leverage misconfigurations in DNS, those misconfigurations are not impossible to mitigate. Our research found that certain DNS providers were not exploitable even when lame name server delegations existed. These providers had procedures in place that we consider best practices for the industry. We recommend that all authoritative DNS providers, including web hosting providers, incorporate mechanisms to close off the Sitting Ducks attack vector:
- To claim a domain name, the best practice providers gave the account holder random name server names that required a change at the registrar.
- The best practice providers used various mechanisms to ensure that the newly assigned name server hosts did not match previous name server assignments.
- The best practice providers did not allow the account holder to modify the name server names after their assignment.
DNS providers who cannot implement defensive techniques such as the above can take other measures. For example, they can:
- Report domain names for which they receive lame requests back to the registrars and TLDs. These organizations could alter the delegation until the domain owner establishes proper DNS hosting. Creating a “name server of last resort” to sinkhole lame queries would hobble these attacks when supported by DNS providers, registrars, and the TLD name servers.
- Streamline processes for the threat intelligence community to report active Sitting Ducks hijacks and act quickly to take down offending accounts.
- Develop methods to identify large-scale free account creation and block those accounts.
Registrars can:
- Prevent assignment of lame name servers by requiring users to confirm they have established DNS service before propagating the name server delegation.
- Proactively check the zones within their control for lame delegations and alert users where possible.
- Alter lame delegations to either remove delegation or point to a sinkhole name service that cannot be hijacked.
- Educate users on the risks of lame delegation.
The TLD servers and others in the resolution chain could thwart attacks by establishing mechanisms to identify and remove lame delegation.
Government organizations, regulators, and standards bodies should consider long-term solutions to vulnerabilities in the DNS management attack surface. Regulators should ensure that organizations within their scope use only providers that can thwart the Sitting Ducks attack vector.
Without cooperation and active effort, Sitting Ducks attacks will continue to rise. This attack already plays a part in cybercrime targeting dozens of countries around the world, costing consumers an untold amount of money and loss of privacy. But the potential threat of these attacks is far greater than what we have uncovered thus far in our research. We encourage readers to help educate others and help ensure that those who can help stop these attacks do so.
Footnotes
- https://www.proofpoint.com/us/blog/threat-insight/screentime-sometimes-it-feels-like-somebodys-watching-me
- https://thehackerblog.com/floating-domains-taking-over-20k-digitalocean-domains-via-a-lax-domain-import-system/
- https://thehackerblog.com/the-orphaned-internet-taking-over-120k-domains-via-a-dns-vulnerability-in-aws-google-cloud-rackspace-and-digital-ocean/
- https://krebsonsecurity.com/2019/01/bomb-threat-sextortion-spammers-abused-weakness-at-godaddy-com/
- https://guard.io/subdomailing
- https://krebsonsecurity.com/2024/05/stark-industries-solutions-an-iron-hammer-in-the-cloud/
- A DigiCert certificate was created for dalesradio[.]net and hijacked by Vacant Viper in 2023.https://crt.sh/?id=9563057978
- https://urlscan.io/result/e82e39de-6222-4b63-98ea-5a5c8e4422ad/
- https://urlscan.io/result/2beb948a-b1d7-4378-9915-7eb4f6bc05ef/
- https://urlscan.io/result/8ee644c6-2ad3-4cd9-a0e6-e05ad01ade5d/
- https://www.proofpoint.com/us/blog/threat-insight/security-brief-ta571-delivers-icedid-forked-loader
- https://urlscan.io/result/b0e9dbe8-421c-433f-bf43-cb18711dc1f2/
- https://urlscan.io/result/843011dc-0b10-410e-87fc-1232041358a1/
- https://urlscan.io/result/f7577199-a3fb-4c38-b733-52020821d445/
- http://web.archive.org/web/20201206011159/https://www.group-ib.ru/media/cert-legal-domain-phishing/
- https://krebsonsecurity.com/2024/07/researchers-weak-security-defaults-enabled-squarespace-domains-hijacks/
- https://cseweb.ucsd.edu/~gakiwate/papers/unresolved_issues-imc20.pdf
- https://labs.guard.io/subdomailing-thousands-of-hijacked-major-brand-subdomains-found-bombarding-users-with-millions-a5e5fb892935
- https://certitude.consulting/blog/en/subdomain-hijacking/
- Wolf in Sheep’s Clothing: Evaluating Security Risks of the Undelegated Record on DNS Hosting Services, Zhang, et al, Proceedings of the 2023 ACM on Internet Measurement Conference, last accessed 2024-07-14, https://dl.acm.org/doi/abs/10.1145/3618257.3624839
- Ghost Domain Reloaded: Vulnerable Links in Domain Name Delegation and Revocation; Li, et al; Proceedings of the 30th Annual Network and Distributed System Security Symposium; last accessed 2024-07-14; https://doi.org/10.14722/ndss.2023.23005
- DareShark: Detecting and Measuring Security Risks of Hosting-Based Dangling Domains; Zhang, et al; Proceedings of the 2023 ACM Special Interest Group on Measurement and Evaluation; last accessed 2024-07-14; https://lixiang521.com/publication/sigmetrics23/sigmetrics23-zhang-dareshark.pdf
- https://www.cisa.gov/sites/default/files/publications/CISAInsights-Cyber-MitigateDNSInfrastructureTampering_S508C.pdf
- https://www.wiz.io/blog/black-hat-2021-dns-loophole-makes-nation-state-level-spying-as-easy-as-registering-a-domain