“Everyone knows that eliminating spam is impossible to achieve, until an ignorant person who doesn’t know this comes along and starts sending some (Italian) spammer to jail. <beg>” —Lex Tutor, 2011
This quote is powerful when you realize that it is referring to progenitors of the notorious VexTrio traffic distribution system (TDS). “Lex Tutor” was an online moniker active in anti-spam communities for at least a decade. He not only complained about the endless torrent of spam plaguing internet users, but actively battled spammers in the courts as well. Through forum posts, Tutor documented a series of micro-companies he claimed were connected to persistent spam operations, referencing their “hideouts” in Lugano (Switzerland), fake identities, their practice of using abuse reports to clean email lists, and their alleged theft of personal data from various partner services to fuel more spam.
Although Tutor complained about spam, VexTrio is more widely known for their traffic distribution system (TDS). The TDS helps disguise digital fraud, the cost of which, according to the Association of National Advertisers (ANA), will grow to US$172 billion by 2028. Investment fraud scams alone reportedly brought in US$16.6 billion from U.S. victims in 2024, according to FBI reporting. VexTrio delivers scareware, dating scams, cryptocurrency scams, fake VPNs and ad blockers, among other types of fraud.
VexTrio gained our attention because of their affiliation with major malware actors and the seemingly ubiquitous presence of their TDS in the threat landscape. When we first reported on the actor in 2022, their domains were seen in over 50% of our customer networks. In 2024, nearly 40 percent of all compromised websites worldwide redirected to VexTrio’s TDS and led victims to a wide array of scams. Hundreds of sites hosted in a single WordPress provider have been hacked simultaneously to route visitors to VexTrio. As of July 2025, domains that support their core infrastructure rank in the top 10,000 most popular in the world, despite concerted security industry efforts to hobble their operations.
The Italian spammers that Tutor hoped would be sent to jail became part of what we know as VexTrio today. But the TDS technology was developed by a group from Eastern Europe. Until 2020, the Italians and Eastern Europeans appear to operate independently but then join forces and establish their headquarters in Lugano, Switzerland. The merger created a formidable suite of commercial entities that touch every part of the adtech industry. Relationships with black hats cemented their dominance in malicious traffic distribution. In the last few years, many of the original Italians appear to have moved on to other ventures.
So how did a few friends from Turin, Italy find themselves embroiled in a Russian-nexus cybercriminal organization with close ties to some of the most prolific website hackers in the world? It’s a complicated and murky story. But internet history shows the Italian group wasn’t innocent to start with: they were accused of spamming and scamming early on, using shell companies for cover and embroiled in lawsuits stemming from their spam. The group emerged around 2004 and was heavily invested in dating websites by 2009. They grew numerous adult brands, profiting from the growth of Facebook. Despite the accusations, their sites were enormously popular, and they garnered partnerships with multiple mobile providers. By 2015, this group’s primary company, Tekka, part of their holding company, Tekka Group, was led by two childhood friends and projected an image of leaders in website innovation: “Tekka is young, Tekka is fast, Tekka is digital.” A move to Lugano and the addition of another Italian, Guilio Cerutti, marked the kickoff of a new phase in their business, as they rebranded and began creating a series of new micro-companies.
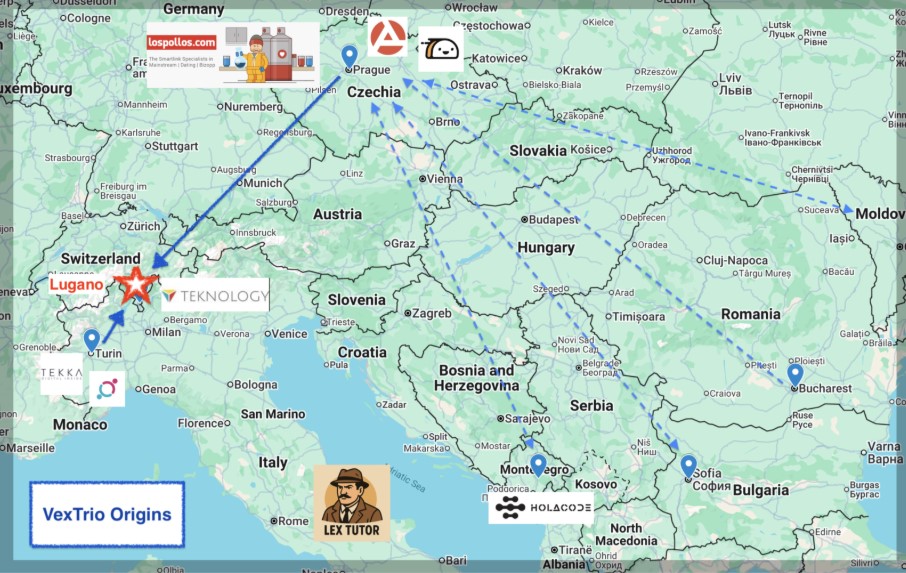
The Eastern Europeans, many originally from Belarus and Russia, developed the TDS and related technology stack. They established companies in several countries, including Bulgaria, Moldova, Romania, and Estonia, before ending up in Prague, Czechia in 2015. Like the Italians, there are numerous micro-companies with complex relationships. Their affiliate advertising firm Los Pollos, part of AdsPro Group, was identified by Qurium as the source of links distributed by the Russian disinformation actor Doppleganger. That discovery was made through analysis of a revealing YouTube video. While AdsPro claims headquarters in Switzerland, many of its employees work in Eastern Europe, including Czechia, Bulgaria, Montenegro, and Moldova; see Figure 1. In addition to AdsPro and Los Pollos, several other adtech firms are central to VexTrio’s operations, including Taco Loco and HolaCode.
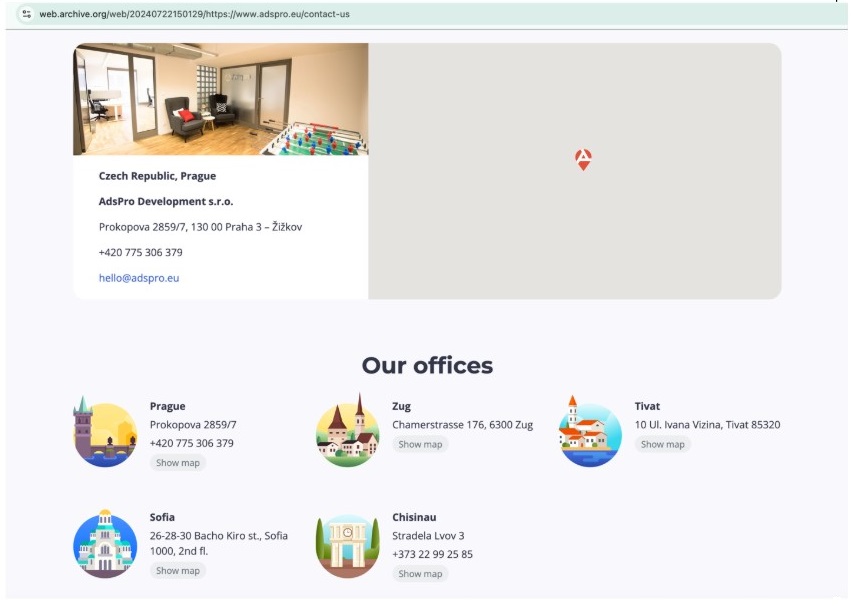
Figure 1. AdsPro office locations in July 2024 according to their website. Following public disclosure of AdsPro as part of VexTrio in December 2024, someone successfully had the company domains excluded from the Internet Archive project. Captured December 2024.
Over the last decade, VexTrio became the darling of many famous, and many other not so famous, malicious actors who used Los Pollos so-called smartlinks to funnel victims to scams from compromised websites, spam, and poisoned search engine optimization (SEO) results. Surprisingly, in affiliate marketing forums, Los Pollos acknowledged that some of their traffic came from black (illegal) sources. In our research, we also found self-described black hat hackers who claimed to work for Los Pollos. This online material supports the results of our previous research, showing that VexTrio has a long-term relationship with malware actors that drives their success in digital fraud.
In 2024, Los Pollos claimed 200,000 affiliates and over 2 billion unique users every month. VexTrio, as a parent enterprise, maintained an infrastructure across the globe, some of it hidden in bulletproof hosting providers and other elements in cloud providers. They still used the hosting originally established by the Italians, leasing IP addresses for multiple autonomous systems (ASs) from the Lugano-based ISP C41 (InternetOne) (AS203639, AS5398 and AS6898). These Swiss IP ranges are still used for dating scam landing pages, while the TDS and spam operations are run from several other hosting providers around the world, often with bulletproof hosting providers. The crypto scams are run out of ISPs in Eastern Europe.
Their many commercial entities are intertwined in ways that make traditional analysis difficult. For example, in Figure 2, Teknology, a VexTrio company created by the Italians, acts as a reference for Los Pollos, while several of the others listed as trusted brands are also owned by the actors. In some cases, they will present two companies as distinct, such as AdsPro and Apperito, but will have identical staff and claim ownership of the same “projects.” They register companies with names that are difficult to distinguish from other legitimate entities. The business relationships are so convoluted that separating VexTrio from their independent partners is a daunting task. While we’ve uncovered nearly a hundred firms created, and often dissolved, over the last two decades, we’re certain we’ve missed many.
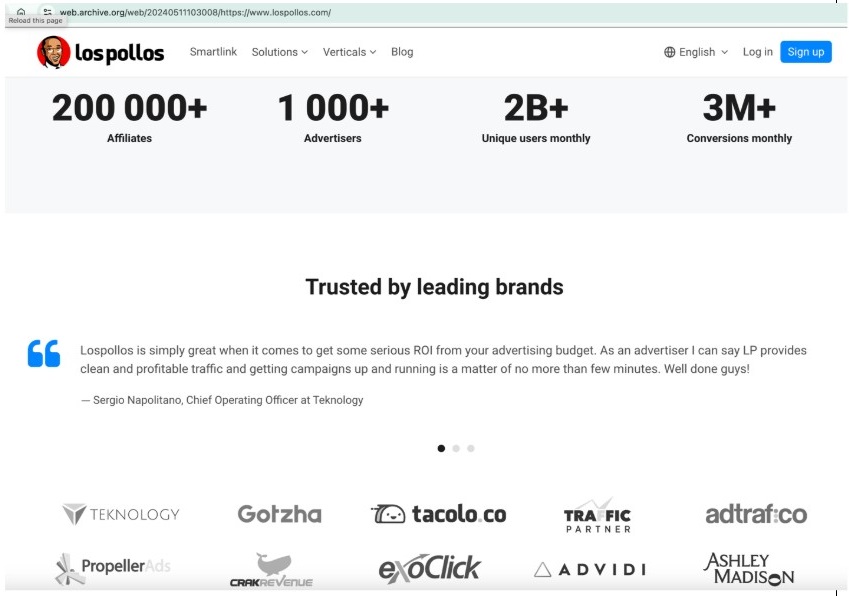
Figure 2. The Los Pollos website in May 2024, as recorded by archive.org, claimed 2 billion unique users. Several of the testimonial brands listed on the site, including Teknology, tacolo[.]co, and Adtrafico are part of VexTrio.
That’s the short version. What we know about VexTrio could cover hundreds of pages.
But VexTrio is only one player in malicious adtech. From a strategic perspective, this industry facilitates a vast array of cybercrime and has taken root, largely unnoticed, in the last decade. This corner of the advertising world has relied on plausible deniability while raking in vast sums from scams, phishing, and malware. They advertise openly and have convoluted relationships with each other that make it difficult to find where one company, or group, ends and a partner begins. Hopefully, this work will inspire others to join in the hunt.
For readability’s sake, we have split this research into three parts. This first segment describes the VexTrio enterprise and key figures, the second will discuss their cybercrime activities, and the third investigates their technology stack and infrastructure.
We have included numerous links to supporting evidence throughout this paper. All these hyperlinks were active in early July 2025. Names, domains, and companies may appear in this report only because of technical or business link to VexTrio; their mention alone does not mean they knew of or took part in any wrongdoing. Specific illegal activity claims are explicit and backed by cited evidence.
Defining VexTrio
Before we get started, let’s explain briefly how we got here. Infoblox Threat Intel has been tracking and chasing VexTrio since 2022. We’ve published multiple papers on the threat actor and collaborated with various folks in the industry along the way to better understand how they fit into the threat landscape. In the fall of 2024, researchers at Qurium and Sucuri/GoDaddy independently discovered that URL links that led to scams from the VexTrio TDS were owned by the commercial affiliate advertising company, Los Pollos. Qurium further connected AdsPro, Teknology, TacoLoco, and Guilio Cerutti. Qurium further identified, but did not publish, several key individuals, and we started collaborating.
Puzzle pieces began to fall into place. When we pulled the thread on the Los Pollos lead, we were able to unravel a complex network of companies and individuals that spanned many countries and years. We reported their domains to several providers and watched as tens of thousands of compromised websites that once directed traffic to VexTrio directed it elsewhere. We hinted at their misdeeds on LinkedIn, and they responded by pulling down material from websites and the Web Archive (archive.org), including that shown in Figure 1.
Using material found on the open internet dating back over two decades, we’ve spent thousands of hours assembling a picture that goes well beyond anything previously published. In total, the VexTrio enterprise includes nearly a hundred companies and brands. The scope of their activities includes malicious apps and large-scale spamming operations, and as we published a few months ago, they have a special relationship with numerous website hackers.
In this three-part report, we’ll introduce the people, the enabling technology, the companies, the hosting, and the activities of VexTrio, a name we use for both the actor and the TDS operations. VexTrio is the union of two independent groups; we use the term to encompass all the entities that the key figures are involved in because, as you’ll learn, finding the dividing line between what is and isn’t VexTrio is complicated. It is much cleaner to include all commercial links and all shared infrastructure into the name.
VexTrio was first recognized as a distinct actor in 2022 but has been delivering scams through their advertising networks since 2015. We assume the reader knows something about the threat actor and their affiliation with other malicious actors of various sorts, particularly WordPress hackers. If you want more background, there are many publications available including:
- VexTrio DDGA Domains Spread Adware, Spyware, and Scam Web Forms
- VexTrio Deployes DNS-Based TDS Server
- Sign1 Malware: Analysis, Campaign Highlights, and Indicators of Compromise
- From Google DNS to Tech Support Scams Unmasking the Malware Trail
- PFP Reinfector and Backdoor Malware Target WordPress Sites
- VexTrio Operates Massive Criminal Affiliate Program
We initially tracked VexTrio as a malicious TDS that led to a range of dating and adult content scams. The VexTrio TDS would redirect to legitimate decoy pages, like Amazon’s shopping website, when their links were visited from places or devices that didn’t match their desired victim profile. Over the years, and particularly over the last nine months, our understanding of the scope of VexTrio has dramatically changed. While we initially assumed they were “hackers in hoodies,” we now know they own commercial enterprises that extend well beyond those that support the TDS operations, including construction, energy, and even ski resorts.
When we say VexTrio now, we mean the controlling individuals and all the businesses they own. To determine what is VexTrio and what is not, we’ve used business and court records, trademark filings, social media and online archives, historical domain name system (DNS) records, software and infrastructure details, and more.
The People
The people are the heart of every successful operation, and VexTrio, is no exception. The people involved in VexTrio, if we consider consolidated enterprises, fall into three primary groups: the Italians, the Eastern Europeans, and the assorted frontmen. Unlike Chinese organized crime groups, VexTrio uses true identities in their commercial filings, which made it easier to tie people and companies together. Figure 3 shows connectivity between key figures and firms over the past two decades.
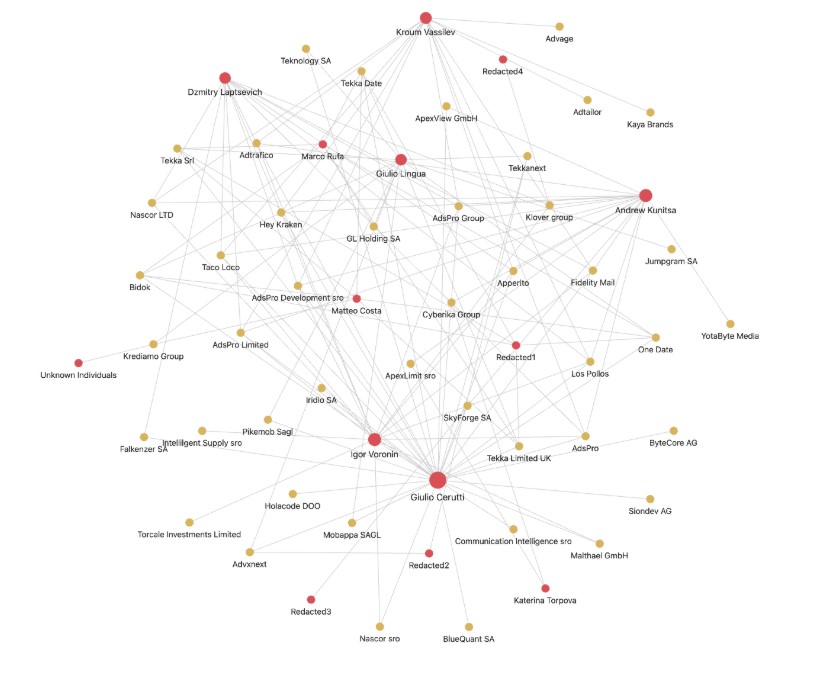
Figure 3. The relationship between key figures and select commercial entities that evolved into what is known as VexTrio today. Not all named businesses are currently operating and some listed individuals may not be involved in the core VexTrio businesses (e.g., Teknology, Los Pollos, AdsPro / Aimed Global, Adtrafico, Taco Loco, HolaCode).
Let’s start with the Italians. Not because they hold the power in VexTrio (they don’t), but because we can track their lineage back to 2004. The Italian crew, hailing predominantly from Turin, are the spammers that Lex Tutor so badly wanted jailed. They hold business degrees from the London School of Economics, Bocconi University, and elsewhere. Several of them hold tight friendships dating back decades, and they began working in the spam industry through a U.S. shell company, Crownstone LLC. Although the key players in Crownstone LLC are Italian, they had a “headquarters” in New York and established operations in Lugano very early on, which Lex Tutor referred to as the “hideout” that allowed them to skirt Italian law. See Figure 4.
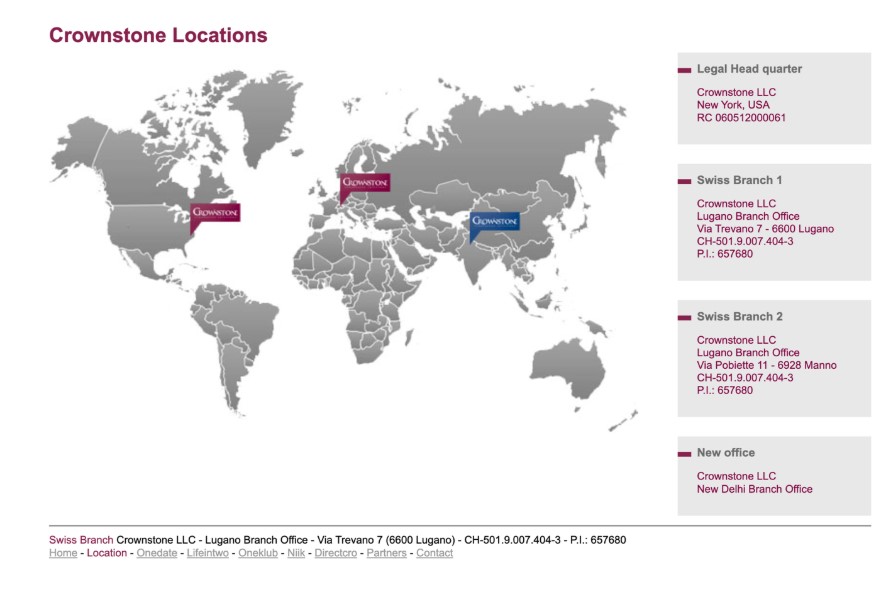
Figure 4. A historical record of the Crownstone LLC website, showing locations in New York City and Lugano. This site also identifies several of their key brands: Onedate, Lifeintwo, Oneklub, Niik, and DirectCro.
Crownstone dove deep into dating apps as Facebook took off and at one point had one of the fastest growing apps on the platform; see Figure 5. The primary brand Onedate took off in the mainstream, charging nearly twice what match[.]com did for membership in 2009, and they established several variants. Marketing reports indicate that Ondate was a top 20 Facebook app in 2012 by monthly active users.
Figure 5. A Google archive preview indicating that Onedate was one of the most explosive Facebook applications. The contents of this page are restricted to subscribers.
At first glance, none of their activities during these years seem suspicious. They appear to be young men off to make their fortune at a time when dating sites were booming. But when you dig a bit, there is a long history of scam and spam complaints about their fake dating websites. Their DNS records and WHOIS registration history show a pattern of sketchy domain names. We found multiple court records implicating Crownstone in spam operations. Trademarks for Onedate were shared with a now-defunct Italian nightclub in Sharm El Sheikh, Egypt. These are later conveyed to Tekka Digital, founded by Guilio Lingua and Matteo Costa. According to 2011 website archives, Tekka serves to acquire customers for Crownstone, but they also have relationships with major mobile carriers like Vodafone and Orange.
In 2015, there is a shift in their businesses. In what appears to be a time of great success for the pair (see Figure 6) they joined forces with another Italian businessman, Guilio Cerutti, who had traveled the world learning finance from CNH Industrial Capital. It’s unclear to us how they initially met Cerutti. They set up shop in Lugano (surprised?) and established a dizzying array of micro-companies, including Teknology SA, Tekka Next, Bidok SA, and GL Holding. A key figure from Crownstone, Marco Rufa, remained in the mix, as well; while he doesn’t seem involved in daily operations in 2025, he is named as a director on several of the entities. Marco Rufa is the signatory for Crownstone LLC in the transfer of trademark assets to Tekka and his name is on domain registration data for Crownstone domains.

Figure 6. December 2015 article about Tekka Digital and their founders. Captured November 2024.
From public records, Teknology attempts to grow their global presence in the years that follow. They create entities in multiple countries. A 2016 slide deck posted to SlideShare by a Tekka Digital employee claims that the company was created in 2007 and served over 80 million customers. They venture out into other areas, including a shopping club service they call Beseev, but the primary money maker for the next several years still seems to be the legacy from Crownstone: the scam dating websites like OneDate.
Things become very interesting when they join forces with Los Pollos sometime in 2020.
Los Pollos is a project that was created under the entity AdsPro (now Aimed Global) and, according to North Data (northdata[.]com), was controlled by three key individuals in 2024: Igor Voronin, Andrew Kunitsa, and Dzmitry Laptsevich (see Figure 7). While the Italians created numerous companies all over the world, this group of Russian speakers are connected to far more. To uncover and connect the entities, we have used open business records, DNS records, domain registration information, social media, and other public records. Their wives and others who appear to be “frontmen” are also found as directors or executive officers of many connected companies. There are also numerous variants of a single entity: AdsPro has AdsPro Group, AdsPro Europe, AdsPro Digital, AdsPro Web Services, and AdsPro Limited. They cleverly choose company names that are similar to legitimate services; for example, the name of their development group HolaCode is the same name as a nonprofit organization. They also use names, like Los Pollos, that will get lost in a sea of search results.
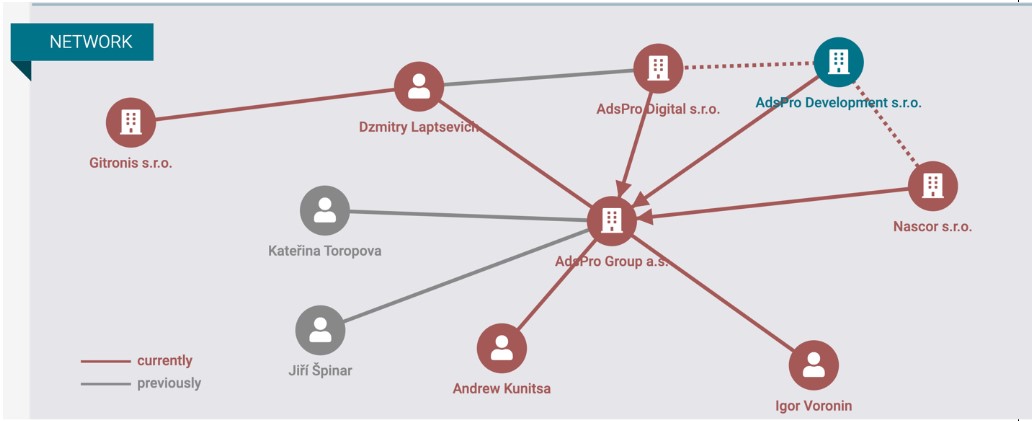
Figure 7. Chart from North Data showing the relationship between AdsPro Group, other entities, and individuals. Voronin, Kunitsa, and Laptsevich were listed as directors when this image was captured in November 2024. This chart also shows K. Toropova, who is connected to a VexTrio advertiser, Techintrade. Voronin and Kunitsa are named in official records for AdsPro.
This group has a much smaller public footprint than the Italians. Instead of rich LinkedIn profiles, for example, in November 2024, Igor’s simply said Igor Holacode; see Figure 8. We have found various pieces of evidence that tie each of the AdsPro founders to Russian or Belarussian backgrounds, but online information also indicates that they have all spent most of their lives in other countries, including Romania and Czechia (Prague).
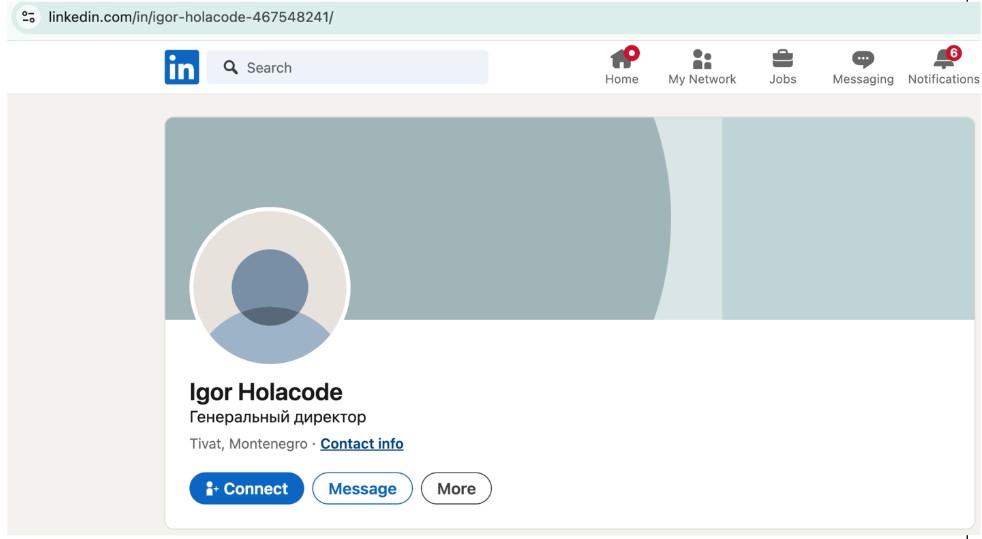
Figure 8. The LinkedIn profile believed to be Igor Voronin, general director of HolaCode. Captured November 2024.
Much of what we know about the key figures in AdsPro comes from business transparency records in various European countries. For example, North Data searches on the CEO of Teknology, Giulio Cerutti, demonstrate a variety of connections with the AdsPro trio; see Figures 9 and 10. We found additional supporting information in social media accounts and other online records that were available in fall 2024. Records from hlidacstatu[.]cz indicate not only Kunita’s relationships with Voronin and Laptsevich, but also the receipt of COVID-19 relief funding from the government.
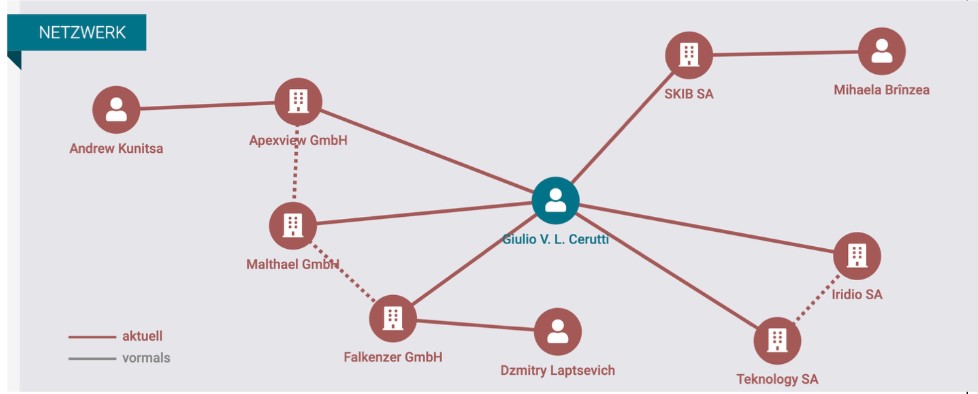
Figure 9. Guilio Cerutti business connections, according to North Data, December 2024.
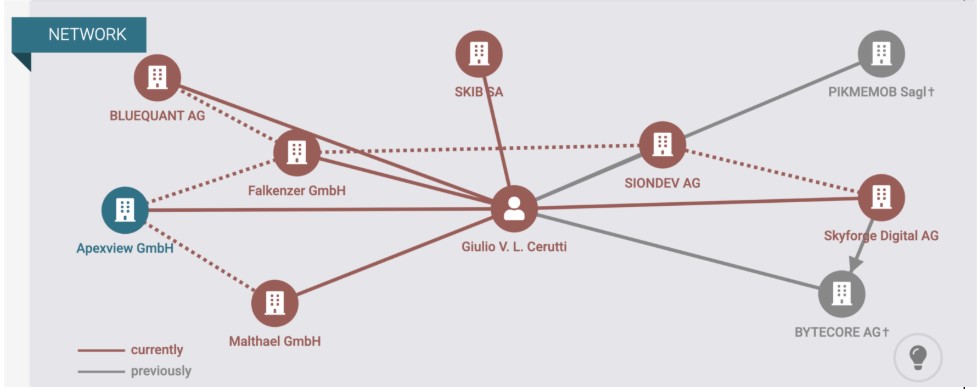
Figure 10. Business connections of Giulio Cerutti according to North Data in July 2025; Cerutti is connected to Andrew Kunitsa via Apexview GmbH, Igor Voronin via Malthael GmbH, and Dzmitry Laptsevich via Falkenzer GmbH.
Besides the directors of AdsPro, there are a handful of other key figures in this branch of the VexTrio family. Most notable is Kroum Vassilev, a Bulgarian-Canadian. According to his LinkedIn profile, Kroum was the co-founder and chief operating officer (COO) of AdsPro (now Aimed Global). He also claims to be the co-founder of Los Pollos.
Besides AdsPro and Los Pollos, Vassilev claims to be a founder or managing partner at several other firms. This includes Profine Energy, Immovlo, Enevlo, Kaya Brands, Adtailor, and Advage, with locations in Bulgaria, Czechia, and Canada. He lists the London School of Economics as his education.
Vassilev has a long history in the adult advertising industry. His LinkedIn profile claims he was the COO of bookmark[.]com from 2009-2012, during which time it was a pornography site, and his earlier firm, Marketing Extensions, also appears to have been in the same line of business. Like many of the individuals involved in VexTrio, Vassilev tries to balance a professional appearance with an adrenaline-filled lifestyle. He’s made appearances on Bulgarian TV for his energy company; see Figure 11. In contrast to the suit and tie, his social media shows his love of cars and the fast life. He posted video of a supersonic stratospheric flight (55,000 feet) from a Russian airbase in 2017; see Figure 12. The love of the fast life is a common theme among the key figures of VexTrio. They all seem involved in racing or driving expensive cars, as well as other adrenaline-filled sports.
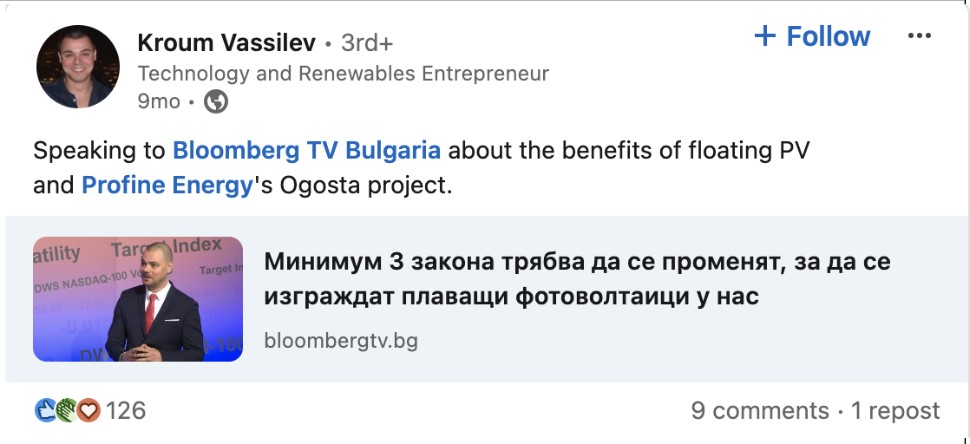
Figure 11. Kroum Vassilev posted on LinkedIn to announce a speaking slot on Bloomberg TV Bulgaria. Captured November 2024.
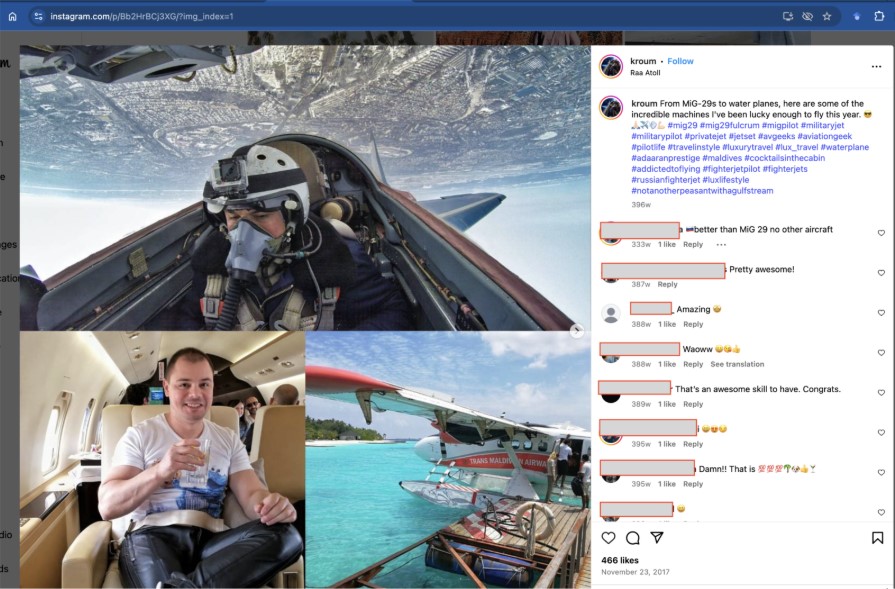
Figure 12. An Instagram post by Kroum Vassilev recapping adventures in planes. Captured June 2025.
VexTrio employs a few hundred people globally. It’s unclear how much the average VexTrio employee knows about the true business model. The companies tend to hire a lot of very young women for their public-facing roles and appear to hire development contractors from Eastern Europe. These employees often move between known VexTrio companies and partners, like iMonetizeIT. We know from the personal experience of one of our own researchers that employees of large scam operations may not be aware of the true nature of the business. While many employees move to other companies, some have been with VexTrio from the beginning. We suspect these longtime senior staff likely understand the scheme; still, we’ve decided not to name those people here.
The Enterprise
Over a hundred companies and brands have direct public ties to the eight key VexTrio figures we have named. We expect there are many more. The vast majority of entities are holding companies with a few owners and no product or service. Others are in industries ranging from payment processors to energy to construction companies. It is unclear which, if any, of these are legitimate companies. In many cases, people listed as having control over a firm appear to be fronts for the real owners; they include wives, attorneys, and employees. VexTrio companies and brands often have names similar to existing brands so that they would be difficult to discern in search engine results.
Los Pollos is part of a cluster of companies that pay homage to the popular television series Breaking Bad. The show centers on the drug trade and in the show Los Pollos is a chicken restaurant owned by drug runner Gus Fring. It is one of several businesses Gus used to launder money but ironically was also successful in its own right. Early images for VexTrio’s Los Pollos lift imagery, including drug manufacturing, directly from the show (see Figure 13).

Figure 13. An August 2017 advertisement for Los Pollos uses an image of Walter White from the Breaking Bad television show, as well as an altered tagline. Captured March 2025.
VexTrio has several Breaking Bad-themed entities under the AdsPro umbrella. HolaCode (holaco[.]de) is the software development group that is largely out of the public eye (Figure 14). According to online records, HolaCode DOO was registered in Montenegro in March 2022 by Cerutti. This group appears to have developers in several countries and a physical location in Montenegro. According to a Bosnian news article from 2024, HolaCode was among the most profitable software engineering micro-enterprises in the region. It is unrelated to the nonprofit organization HolaCode. A third company is TacoLoco, which claims to process over 1 million requests per second, and is used for push monetization.

Figure 14. HolaCode location in Montenegro. Captured November 2024.
The line between VexTrio partners and entities is blurry. For example, they will use their own companies and employees as references for services on websites. In Figure 15, an AdsPro website lists Los Pollos, TacoLoco, and Adtrafico as “partners and solutions” they rely on. After AdsPro was exposed they successfully lobbied the Internet Archive to remove archived scans from adspro[.]eu, as well as several other domains; the link shown in Figure 15 is no longer available. We know AdsPro is responsible for having the content removed because the Internet Archive does not remove content otherwise. They did forget some domains though, like adspro[.]group and adsprodigital[.]com. In 2023, the AdsPro website claimed their companies had over 50 million monthly active users. We will discuss the three main AdsPro companies, Los Pollos, TacoLoco, and Adtrafico in more detail in the section titled Smartlinks and TDS.
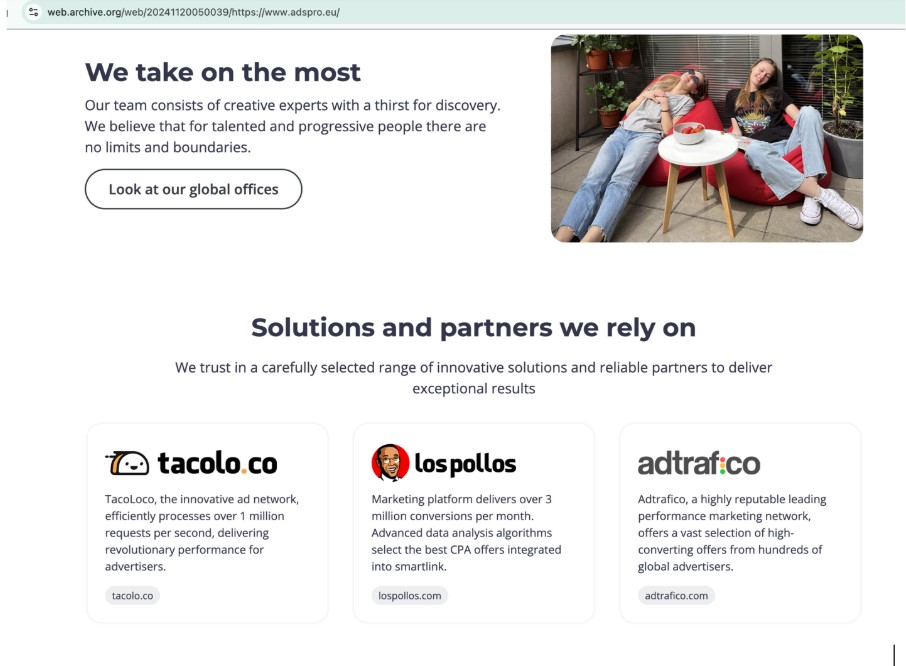
Figure 15. The AdsPro website as it existed November 20, 2024, shows TacoLoco, LosPollos, and Adtrafico. While it says these are solutions and partners, AdsPro owns all three. These entries in the Internet Archive were deleted in December 2024, due to a complaint from the domain owner.
The employees of AdsPro and another purportedly separate entity, Apperito, are the same. They even posted social media images of their company outings in the same locations. Apperito also has multiple projects—including an app development group, LocoMind (see Figure 16).
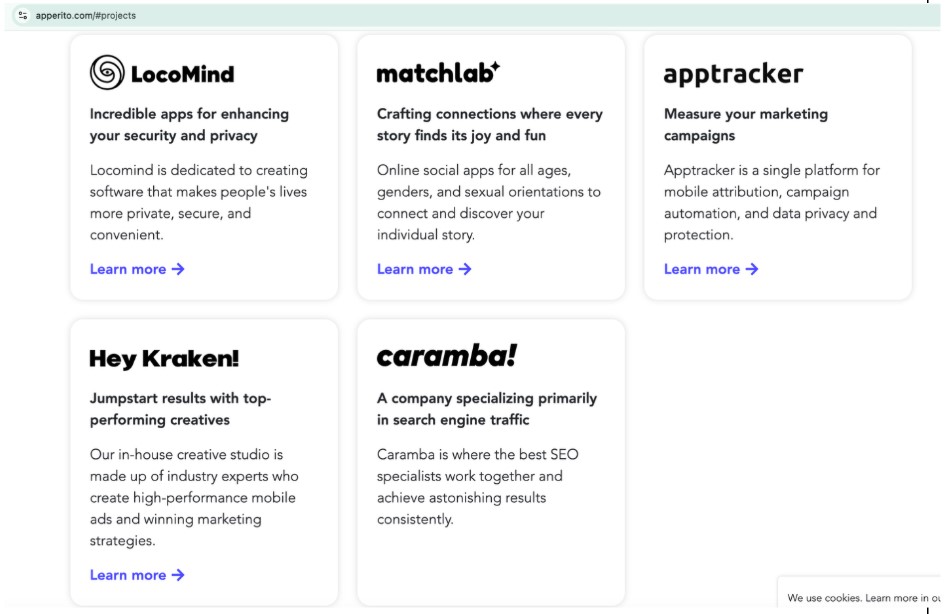
Figure 16. Apperito.com projects as shown on their website in November 2024
Part of their business model is developing fake apps, as we’ll see later in the blog. With Apperito, we start to see a further reach of VexTrio into other parts of the advertising ecosystem; they list search engine optimization, creative development, and trackers. In 2024, LocoMind (locomind[.]net) claimed over 500,000 downloads and 50,000 active users for their apps. They claimed to provide user security for mobile phones. There are at least seven apps historically associated with them, including a “RAM cleaner” and various VPNs, like FastVPN.
AdsPro and their related businesses were previously very active on social media, including LinkedIn and Facebook. They extensively marketed themselves and the quality of life for their employees. Following exposure by us in December 2024 on social media, they sanitized or deleted many of their accounts. Where possible, we archived those in various locations on the internet; in other cases, we kept screenshots as supporting evidence. For example, the AdsPro Facebook account actively promoted their services and people; they even had a series of posts on their cats (see Figure 17).

Figure 17. Image from the now-deleted AdsPro Facebook account in a series of posts about the cats of AdsPro. This image shows employee names logged into the RocketChat portal. Image captured November 2024.
VexTrio also runs a wide range of spam-related services. For example, they operate mail[.]sendgrid[.]rest. It’s somewhat surprising that they have gotten away with the use of a lookalike domain to the large email marketing company SendGrid since September 2021. They also control the domain, mailgun[.]fun. As far as we know, they have nothing to do with the company Mailgun. The sendgrid[.]rest and mailgun[.]fun mail servers run on the holaco[.]de infrastructure along with a wide range of related domains. According to shodan[.]io in June 2024, other domains include not only those related to Los Pollos, but fidelitymail[.]com, related to Fidelity Mail, an email marketing firm. See Figure 18 for these and other VexTrio service domains. Other domains on this IP address include fake apps they have developed and Pay Salsa, a payment processing service owned by VexTrio.
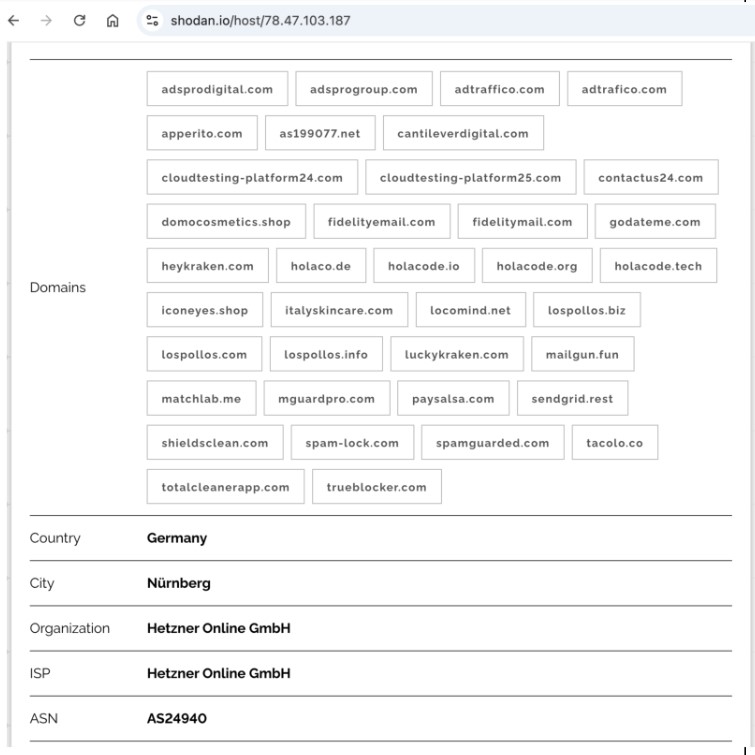
Figure 18. Shodan information for the IP address 78[.]47[.]103[.]187 shows several VexTrio company domains and app names. Image captured June 2025.
In the Swiss networks associated to the firm Teknology, VexTrio hosts landing pages for the different scams, as well as some spam-related services. They offer email validation services through DataSnap, previously called Articheck (Figure 19). These examples highlight how they have attempted to hide their operations by blending into existing legitimate company names. While the email validation service was hosted under the name articheck[.]ch, a Google search on Articheck will give results about the art-related company, articheck[.]com. DataSnap claims to have a 99.9 percent accuracy in validating emails for direct email marketing. All VexTrio scams obtain email addresses for the victims, which likely makes email validation easier.
Figure 19. The DataSnap website. Captured July 2025.
The key figures tied to VexTrio are involved in dozens of companies, many of them holding companies. Sometimes the line between a company and a brand is blurred and indistinguishable. We show a sample of the companies and brands that we uncovered in Table 1. These companies were found in open-source research through a combination of corporate record sites, information on known company websites or apps, social media postings, DNS records, and domain name registration history. We suspect there are many more entities than we have discovered.
| Adschain srl AdsPro AdsPro Digital AdsPro Global Adtailor Adtrafico Advage Advxnet Alcorvo Alphascale Media GmbH AlphaScale SA Alpine Robe SA Amgest SA ApexView GmbH ApLabz Apperito Apple Digital Srl Articheck BlueQuant AG Bright Media OOD ByteCore AG CasualClub Crownstone LLC Digibility SRL Digitarium SRL Enerdigity SRL Falkenzer SRL Fidelity Mail GL Holding SA GoalMobile SRI Gitronis SRO Havran Investments SRL Havran Media HolaCode DOO Hostinec |
Idea Partners GmbH Intelligent Supply sro Iridio SA Ironads srl IronDeal FKT Kaya Brands Klover Group LocoMind LoggaTI LosPollos Malthael GmbH Marten Ivestment SRL Media Alliance sro Mobappo SAGL Nascor sro New Breeze OOD Pay Salsa Primerox sro Raven Media SionDev AG Skib SA SkyForge AG SkyForge Digital AG TacoLoco Take OFF GmbH Techtribe AG Tekka Teknology SA Tekka Date Tekka Next SAGL Tekka Limited Teknology Corp Yapple K Sro YotaByte SA |
Table 1. A sample of the entity names associated with the key historical figures of VexTrio: Guilio Lingua, Matteo Costa, Marco Rufa, Igor Voronin, Andrew Kunitsa, Dzmitry Laptsevich, and Kroum Vassilev.
Smartlinks and the VexTrio TDS
There are three companies in the VexTrio enterprise that are affiliate advertising networks: Los Pollos, Taco Loco, and Adtrafico. Each of these could be the subject of a paper in itself, but we will just do a short introduction of each and their connection to cybercrime.
VexTrio is notorious because large numbers of compromised websites redirect users into their TDS; in 2024, nearly 40 percent of the compromises observed by GoDaddy led to VexTrio. This redirection is caused by links called smartlinks (or direct offers): a single URL that will always deliver content, regardless of the visitor’s location or device. Adtech companies promise publishing affiliates, meaning the people who distribute the URLs, that these are an easy way to ensure they maximize their profits. Figure 20 shows how the company Adsbridge explains smartlinks, which they began offering in 2020. The diagram is taken from a more recent version of their website.
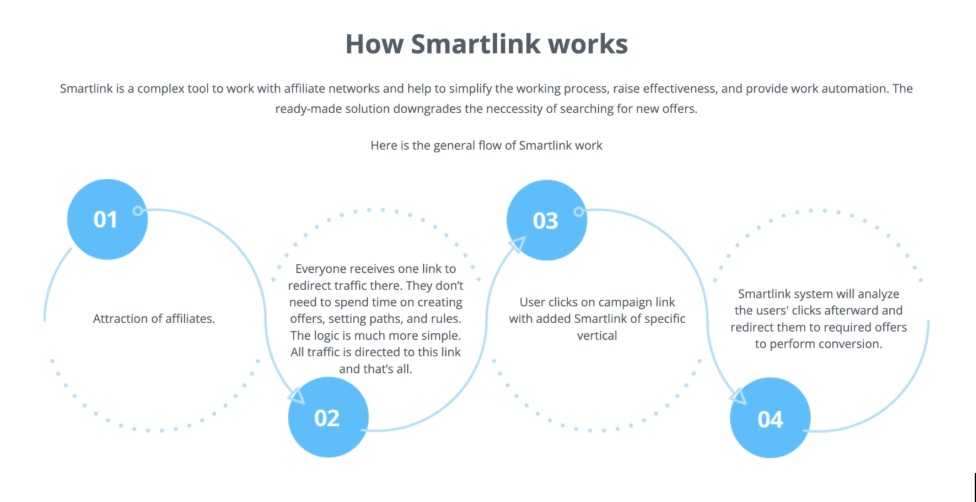
Figure 20. How smartlinks work according to the website of Adsbridge, which is part of iMonetizeIT. Captured July 2025.
Los Pollos is a cost per action (CPA) network. In a CPA network, the publishing affiliate—which in the case of compromised websites is a malware actor—receives a commission if the site visitor performs an “action” at the landing page. An action in this context may be accepting website push notifications, providing their name and email, or purchasing a product with a credit card, for example. Los Pollos boasts that their advertisers are of high quality with a high conversion rate, meaning that users are likely to take the action. In return, the publishing affiliate only receives payment when the action specified by the advertiser is taken. We show a simplified example of this process in Figure 21.
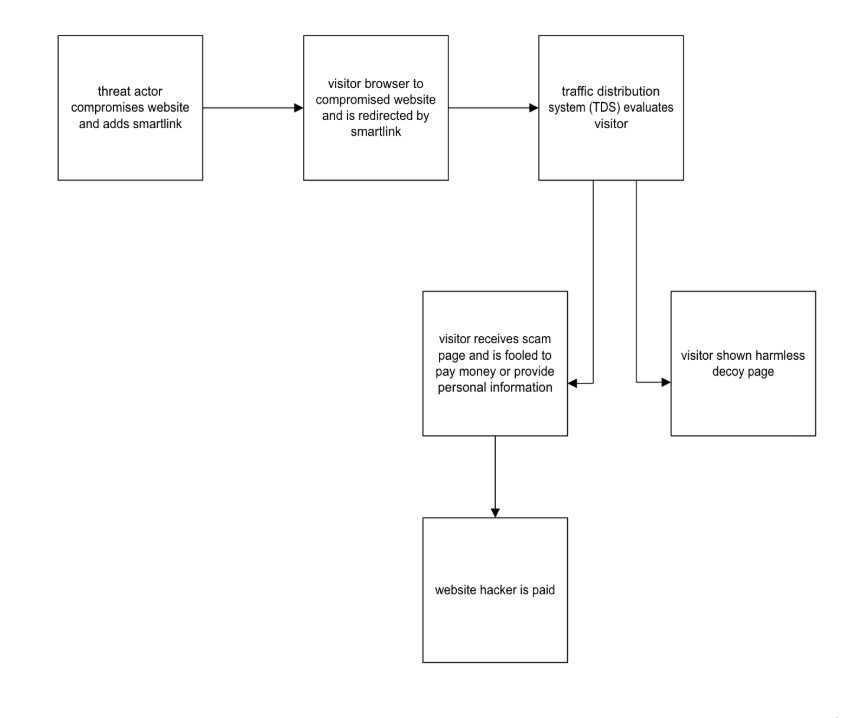
Figure 21. How threat actors leverage compromised sites and smartlinks to earn money.
Los Pollos smartlinks emerged on the security industries radar in 2017 but it was not clear that they were linked to the adtech firm until fall 2024. In October 2019, Los Pollos introduced “push” smartlinks (Figure 22), which led to fake CAPTCHAs that tricked users into accepting push notifications from the site, creating a form of persistence. Until users turned off browser notifications, a task that is tricky for the average user, they would be inundated with notifications that their computer was hacked, they had won a gift card, or other clickbait. Opening a notification put them back into the TDS and a whole new cycle of exploitation would begin. This was the push monetization option that Los Pollos closed in late November 2024.
Figure 22. Los Pollos announces their push monetization offering on their paid Black Hat World thread in October 2019. Captured June 2025.
In 2020, Los Pollos announced their sister company, TacoLoco, which offered a new way for publishing affiliates to monetize their traffic. Los Pollos publishing affiliates who incorporated TacoLoco push monetization into their sites were promised a 90 percent revenue share for the life of the user’s subscription. Los Pollos also encourages their affiliates to register as TacoLoco advertisers and use their smartlink as their ad. See Figure 23. We don’t know how many people have followed this advice, but it creates a clever cycle in which these publishing affiliates are paying VexTrio for the potential of receiving a payment in return: what a deal!
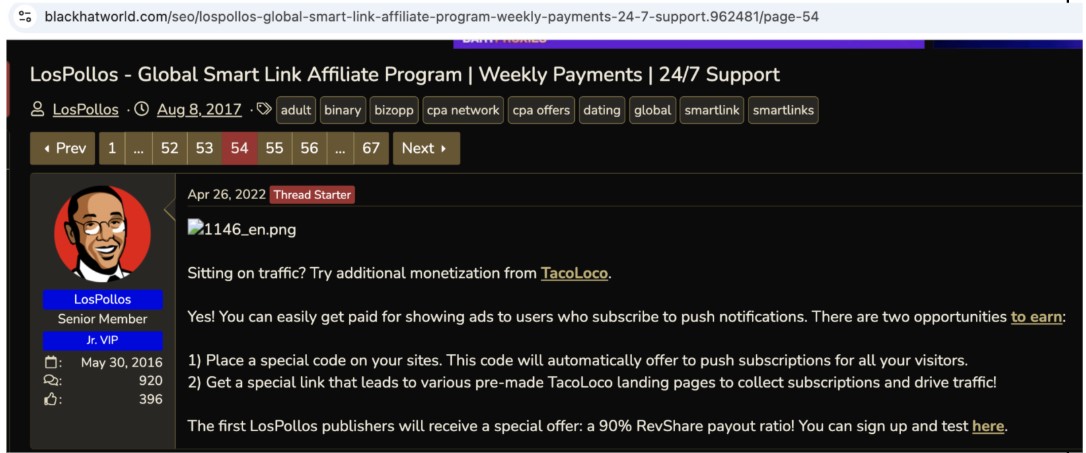
Figure 23. Advertisement for and explanation of, TacoLoco, the VexTrio push monetization company. By combining LosPollos smartlinks with TacoLoco, they promised a 90 percent revenue share to affiliates.
TacoLoco offers affiliates two ways to monetize: place special code on a website that automatically offers push notifications to all visitors or get a special link and drive traffic to it. Figure 24 shows the script that is inserted into a website to ask users to accept notifications. The domain listed, nxt-psh[.]com, is a top 100,000 domain in global popularity by multiple sources as of July 2025. Some VexTrio domains have risen to the top 10,000 within a month, demonstrating their ability to reach large audiences worldwide.
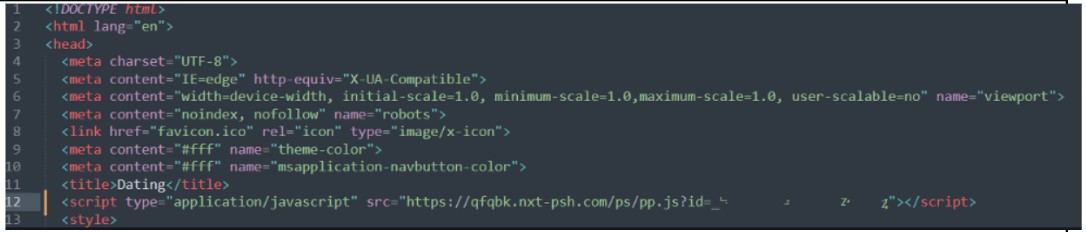
Figure 24. The push notification script that is inserted in a website header to lead visitors to a request to allow browser notifications, according to TacoLoco documentation. The domain nxt-psh[.]com is one of several domains used for push notifications.
In their (now-deleted) “complete guide” blog, TacoLoco showed several pre-made landing pages that were available to affiliates. These landing pages are fake CAPTCHAs and considered within the security industry to be signature VexTrio images; see Figure 25. The blog also explains to affiliates how to set the “aggression” parameter, which controls how many times a user will be asked to subscribe to notifications. The article states: “Simply put, if a user opens a page, sees a push notification, but does not subscribe, then auto-update is triggered, and on another page, a pop-up window will offer to subscribe again.”
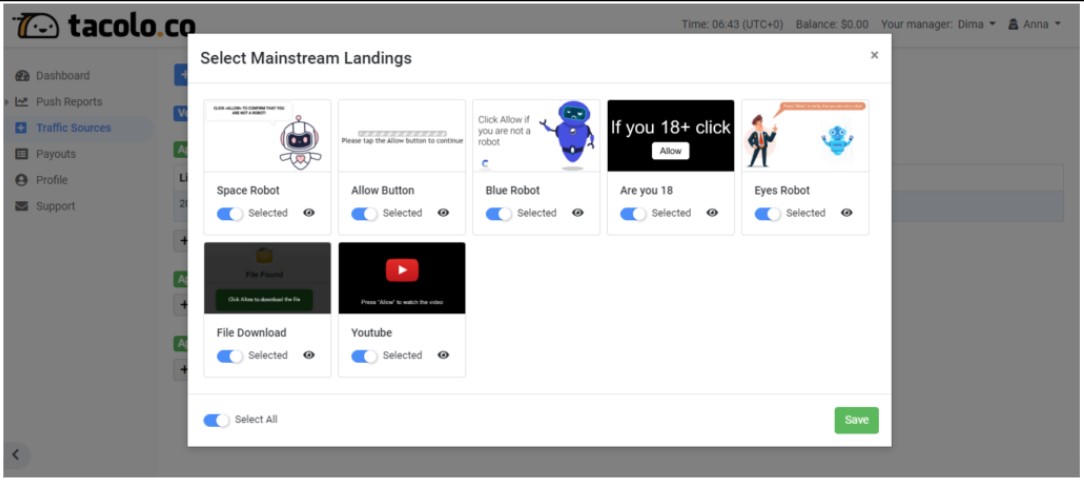
Figure 25. Premade landing pages offered by TacoLoco in August 2022 according to their blog “How to Monetize Traffic with TacoLoco: A Complete Guide.” Captured June 2025.
The available evidence strongly suggests that VexTrio is complicit in cybercrime. They boast about the quality of their advertising affiliates. Unlike Facebook and other major advertising platforms, Los Pollos does not allow just anyone to advertise: they vet their advertisers. We, and many others, have followed hundreds of smartlinks and been willingly scammed time and time again. The million-dollar question is: Are they complicit in the scourge of WordPress malware that plagues sites globally? According to a message from their official account on Black Hat World in 2017, their platform is a little black, a little white. See Figure 26.
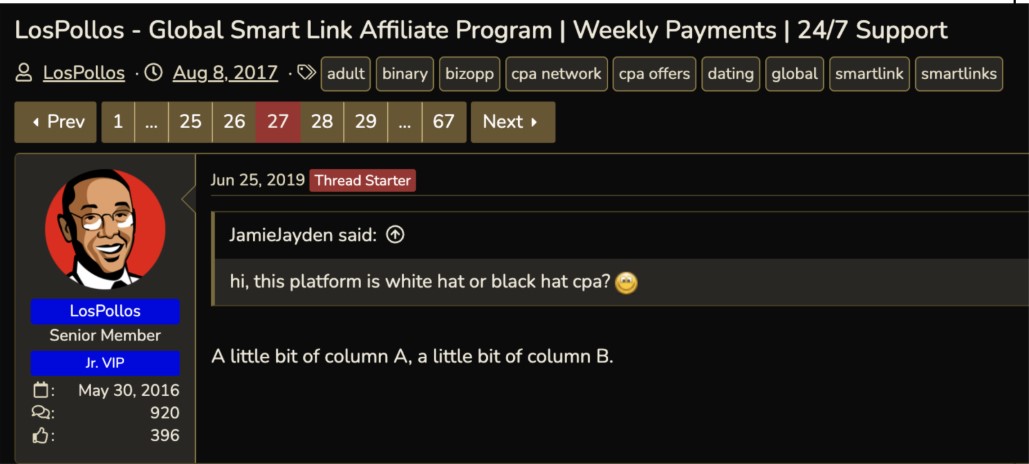
Figure 26. Los Pollos official account reply to a question on Black Hat World forum. Captured June 2025.
In the advertising world, black traffic refers to illegal sources. Senior AdsPro employees attended invite-only black hat SEO parties, according to photographs uncovered by Qurium researchers. So, what exactly do they know about the website hacking publishing affiliates? Minimally, they know enough to connect the compromises to the crypto wallets that they pay out every Tuesday. In other forum messages, the LosPollos official account suggests that affiliates who want to use their smartlinks on Facebook will need to learn black hat methods; see Figure 27.
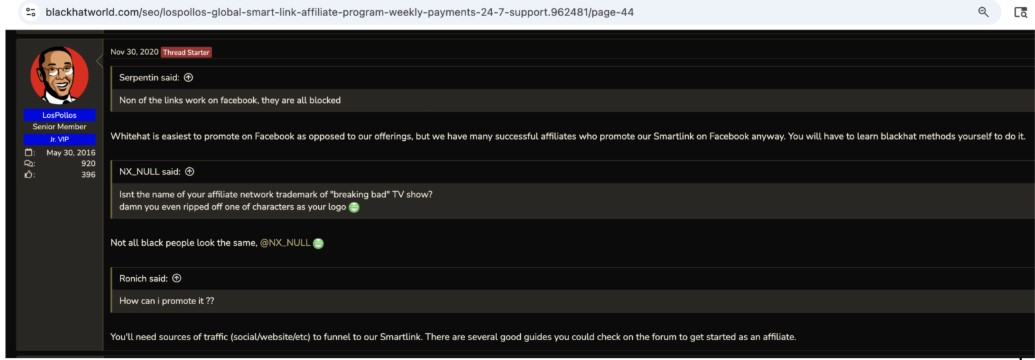
Figure 27. LosPollos official account suggesting the affiliate needed to learn black hat methods to advertise on Facebook and that their offers were not white hat. Captured June 2025.
Not only has Los Pollos acknowledged they receive black hat traffic, but some black hat hackers have claimed direct ties to Los Pollos. Marius Gjura, who appears to be Albanian in origin, stated on LinkedIn (Figures 28 and 29) that he developed affiliate marketing cloaking software and further indicated he was connected to Los Pollos and iMonetizeIT (yes, the same iMonetizeIT that owns AdsBridge, whose smartlinks are described in Figure 20).
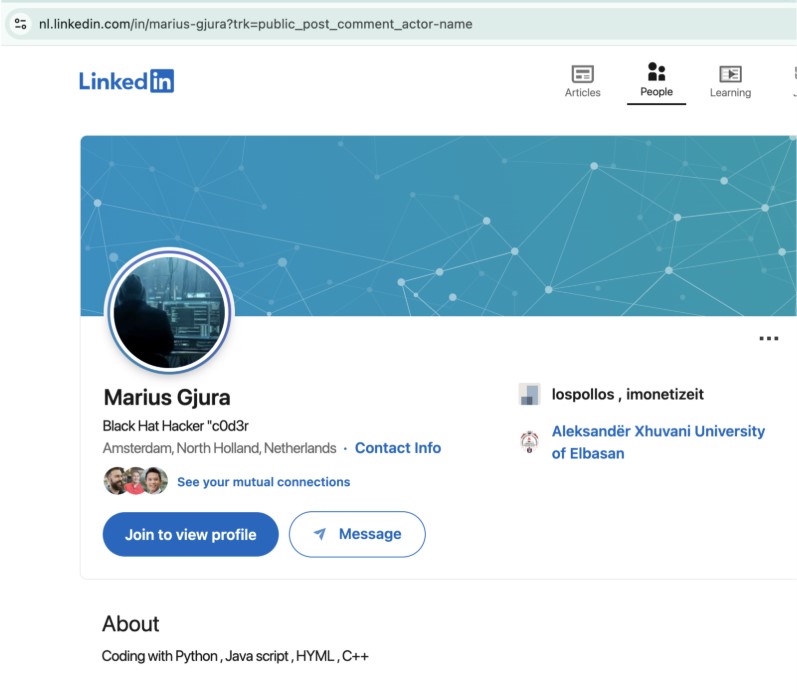
Figure 28. LinkedIn profile for self-described black hat hacker claims relationships with Los Pollos and iMonetizeIT. This same individual is linked to a different Albanian LinkedIn profile.
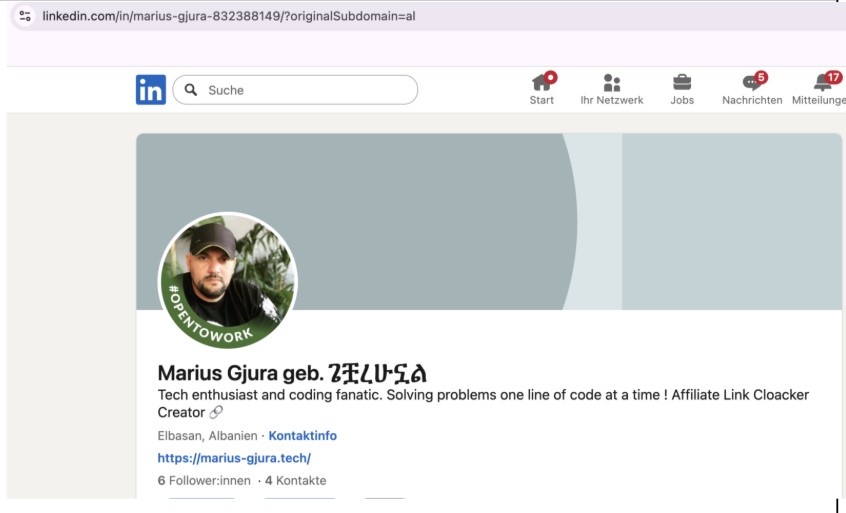
Figure 29. Albanian LinkedIn profile describes role in developing affiliate link cloaking software. This same individual is linked to a Dutch profile that lists Los Pollos and describes themselves as a black hat hacker.
Los Pollos not only vets their advertisers, but they also vet their publishing affiliates. In doing so, VexTrio may cause their own demise. User posts on forums such as Black Hat World indicate that the rejection level of publishing affiliate applicants is high, and there are no clear requirements for acceptance. On November 12, 2019, in response to an inquiry about what is needed, the official Los Pollos account replied “We don’t have a list of requirements, we review each application.” They do not accept applicants with no history as a publishing affiliate (Figure 30) and they frequently reject applicants without a specific reason (Figure 31). Los Pollos asks applicants to provide them with marketing forum profiles, the names of other Los Pollos affiliates who could vouch for them, as well as traffic source information. According to forum posts, they routinely respond with “Unfortunately, I am unable to accept your application at this time.” And yet, they accepted the applications of prolific website hackers.
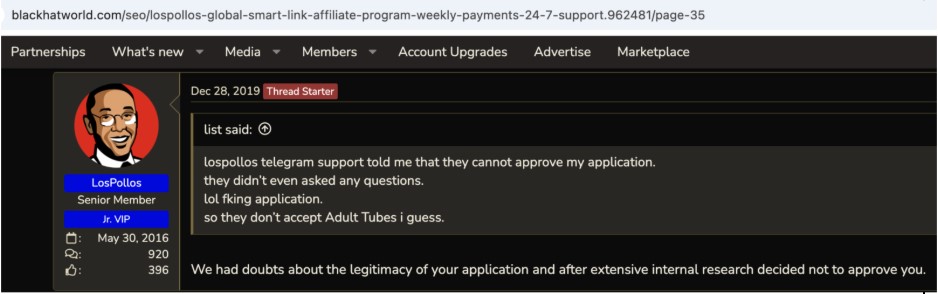
Figure 30. Los Pollos official account commentary on the rejection of a publishing affiliate application indicating they analyze their applicants. Captured June 2025.
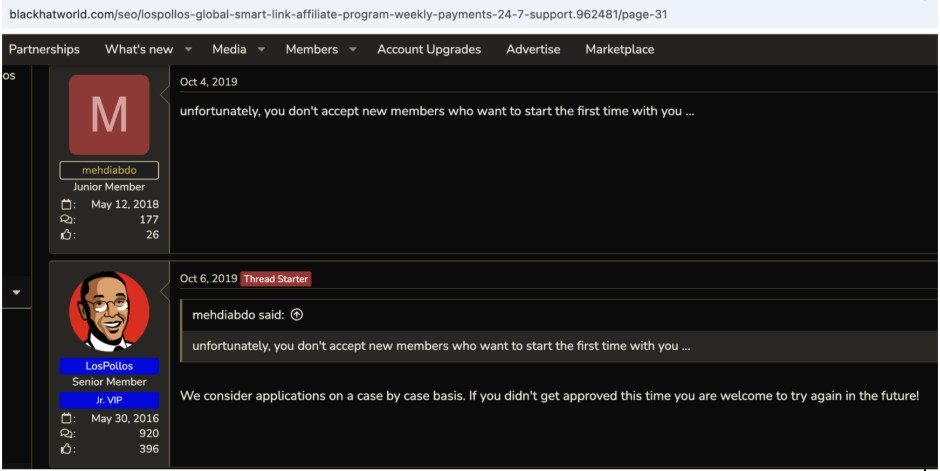
Figure 31. Los Pollos vets their publishing affiliates before providing access to live smartlinks and does not accept first-timers. Captured June 2025.
The third affiliate advertising company in their portfolio is Adtrafico. Instead of smartlinks, Adtrafico sells affiliates direct cost-per-action offers, meaning they know exactly what the end advertisement is and the action required for payment. Adtrafico emerged around the same time as Los Pollos, with a home page appearing around September 2016; see Figure 32. Early Adtrafico messaging promised “the freshest offers. Illegaly-high payouts” for publishers. In April 2025, Adtrafico announced it was merging with its parent company LosPollos, and as of July 2025 the domain adtrafico[.]com redirects to lospollos[.]com. According to their announcement, the merger doesn’t change the Adtrafico business model, so for this discussion, we are keeping the present tense.
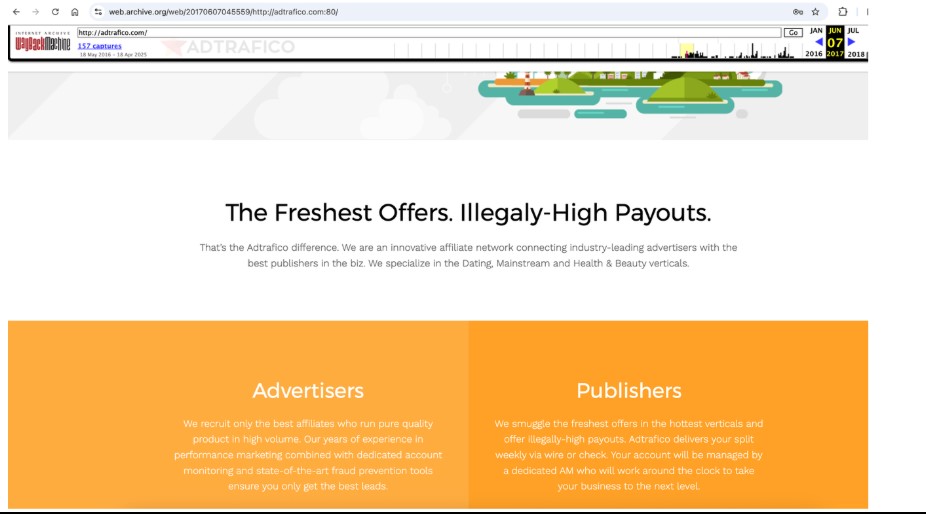
Figure 32. The Adtrafico website as of June 7, 2016, as well as the timeline of Wayback Machine archives for the domain adtrafico[.]com. Captured June 2025.
As Adtrafico explained in their marketplace thread on Black Hat World, the publisher is paid for every successful lead, which is defined by some specific action. For example, on April 20, 2021, they detailed a “sweepstakes” offer for an iPhone 12 Pro, targeting people in Czechia. The Adtrafico affiliate would somehow lead the user through to a link that gave an opportunity to win the new phone. To qualify, the targeted victim is led through a series of three quiz questions, and finally to a simple call button. Once the user makes the phone call, the affiliate is paid out €2.80. Not bad! This is called an interactive voice response (IVR) offer. In our experience, the quiz questions aren’t real quizzes; they appear to buy time for the TDS to profile the potential victim.
Most of the Adtrafico offers pay affiliates a few dollars for obtaining a user’s email address, date of birth, physical address, and name. But some pay much more. These are typically what are called “CC submit” offers, meaning the fraud victim will need to submit a credit card number for the affiliate to be paid. As the Adtrafico official account announced on February 4, 2022, these offers have good payouts. In that example, a landing page offering the victim the ability to buy an iPad Air for US$3 would lead to a US$33.60 payment to the publishing affiliate if completed.
How is that possible? Fraud. This type of ad steals the victim’s money by charging them more than is shown on the screen. For example, they may be billed US$9.99 for that iPad Air that they will never receive. But they also get enrolled into automatically renewing subscriptions. The victim will need to realize the crime and then fight it through the credit card company as “chargebacks.”
We’ve had several people argue with us as to whether this is an effective scam mechanism; but if it weren’t, they wouldn’t do it. Threat actors like VexTrio can distribute massive numbers of such offers around the globe. They typically claim conversion rates for CC submit offers around 1.5 to 2 percent. At scale, that’s a lot of money. We’ve seen nutra industry vertical and anti-virus offers from Adtrafico that paid well over US$100 per lead.
In 2024, Adtrafico was one of few advertising networks that openly sold “blank CC submit” ads (Figure 33). In a typical CC submit offer like the iPad Air example, the advertiser provides the so-called creative. But with a blank offer, the publisher is given a template which they can adorn with the logo of their choice, like Amazon or Walmart, as well as the wording. According to advertising affiliate blog Partnerkin, blank CC offers were among the hottest in 2024. Partnerkin states that some affiliates have “six-figure days” running blank CC offers, often getting 300+ percent return on investment (ROI). Another company, CheckItOut, created slide decks for prospects to explain the scheme.
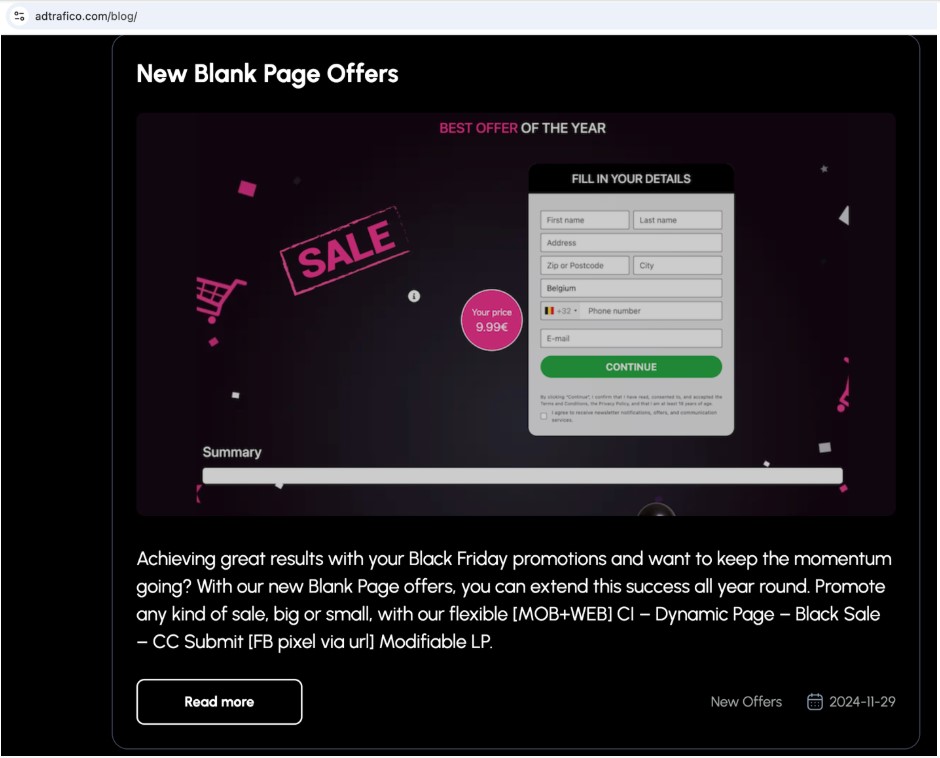
Figure 33. Adtrafico blank credit card offer as of November 29, 2024. Adtrafico deleted these pages in mid-December 2024.
In an effort to expose this type of activity, we outed Adtrafico in late December 2024 on LinkedIn after they began removing content from their website. Adtrafico reacted within a few hours of the post, not by contacting us, but by scrubbing more material from the internet. They had the original Partnerkin article modified to remove references to them and deleted numerous online posts. Before we release material, however, we make many copies. One copy of the original Partnerkin blog is kept in the Internet Archive. Further archives of Adtrafico’s website show that their top offer in October 2024, was a blank CC offer targeting Slovenian residents and paying approximately US$38. The VexTrio team is always innovating: in August 2024, they announced “SmartRotation” of blank CC offers, which allowed for more variety in landing pages to fool a broader audience.
Plausible deniability is built into the paradigm of advertising networks. The adtech companies claim to act only as an intermediary between a publisher and an advertiser, with no way to control abuse of their platform. Indeed, this is what Guilio Cerutti claimed to Brian Krebs in December 2024 following a post we made on LinkedIn. But in the case of VexTrio, they are not just the conduit, they are the connective tissue between two types of crime. They are not at arm’s length from either the website hackers or the scam advertisers. Moreover, the evidence presented shows they likely run a large portion of the scams themselves.
The Ecosystem
VexTrio and their partners are successful in part because their businesses are obfuscated. But a larger part of their success is likely because they stick to fraud, where they know there is less risk of consequences.
Michael Schwalbach, the CEO of Advidi, a VexTrio advertiser, said in an online interview:
“… some of the products can be aggressive —
but we’ll never push products that cross the line.
For example, we’ll never push a cryptolocker or malware.”
VexTrio steals money by conning people. And as a result, they live a lavish lifestyle that most people only dream of; see Figure 33. If only Lex Tutor could have his wish come true.
Since our last publication, VexTrio has registered thousands of domains and has changed their infrastructure, however we are still tracking them and the affiliated malware actors. Domains and references from this research can be found in our GitHub repository.
One of the many social media posts by key VexTrio figures showing off expensive cars and a lavish lifestyle. Captured July 2025.
References
- https://groups.google.com/g/it.news.net-abuse/c/Jyd5cZy2Nnc/m/0bmio7YJMSsJ
- https://blogs.infoblox.com/threat-intelligence/cybercrime-central-vextrio-operates-massive-criminal-affiliate-program/
- https://groups.google.com/g/it.news.net-abuse/search?q=lex%20tutor
- https://www.ana.net/miccontent/show/id/ii-2025-02-ai-ad-fraud
- https://www.ic3.gov/AnnualReport/Reports/2024_IC3Report.pdf
- https://blog.sucuri.net/2024/06/socgholish-malware.html
- https://blogs.infoblox.com/threat-intelligence/cyber-threat-advisory/vextrio-ddga-domains-spread-adware-spyware-and-scam-web-forms/
- https://www.godaddy.com/resources/news/godaddy-annual-cybersecurity-report
- https://blogs.infoblox.com/threat-intelligence/vexing-and-vicious-the-eerie-relationship-between-wordpress-hackers-and-an-adtech-cabal/
- https://web.archive.org/web/20150313013854/http:/tekka.it/
- https://web.archive.org/web/20121014150606/http:/www.tekkagroup.com/
- https://www.linkedin.com/company/tekka-group
- https://www.linkedin.com/in/giulio-cerutti-1472611/?originalSubdomain=ch
- https://web.archive.org/web/20170830003222/http:/www.tekka.it/
- https://www.qurium.org/forensics/when-kehr-meets-vextrio/
- https://www.youtube.com/watch?v=8rLIx_wKrto
- https://platform.inflect.com/building/12-via-soldini-chiasso/c41-ch/datacenter/chiasso
- https://blogs.infoblox.com/threat-intelligence/cyber-threat-advisory/vextrio-deploys-dns-based-tds-server/
- https://blog.sucuri.net/2024/03/sign1-malware-analysis-campaign-history-indicators-of-compromise.html
- https://blog.sucuri.net/2023/08/from-google-dns-to-tech-support-scam-sites-unmasking-the-malware-trail.html
- https://blog.sucuri.net/2024/11/php-reinfector-and-backdoor-malware-target-wordpress-sites.html
- https://insights.infoblox.com/resources-whitepaper/infoblox-whitepaper-cybercrime-central-vextrio-operates-massive-criminal-affiliate-program/
- https://web.archive.org/web/20100429075420/http:/crownstone.net/
- https://bibliotecadelconsumidor.profeco.gob.mx/media/revistas/RC-385 Marzo 2009.pdf
- https://www.adweek.com/performance-marketing/zoosk-badoo-topface-onedate-and-more-on-the-top-20-facebook-dating-apps-by-mau/
- https://www.adweek.com/performance-marketing/this-weeks-most-explosive-facebook-applications-23/
- https://datingspot24.com/reviews/onedate.com-experience/
- https://www.aepd.es/documento/e-00900-2011.pdf
- https://trademarks.justia.com/772/30/onedate-77230697.html
- https://assignments.uspto.gov/assignments/assignment-tm-4810-0406.pdf
- https://rocketreach.co/matteo-costa-email_48103689
- https://web.archive.org/web/20111105025930/http:/www.tekkaweb.com:80/customers.html
- https://web.archive.org/web/20111005171901/http:/www.tekkaweb.com/
- https://www.linkedin.com/company/teknology-sa/about/
- https://annuaire-entreprises.data.gouv.fr/entreprise/tekka-next-812083806
- https://business-monitor.ch/en/companies/1024817-bidok-sagl
- https://www.moneyhouse.ch/en/company/gl-holding-sa-14023417831
- https://www.shab.ch/shabforms/servlet/Search?EID=7&DOCID=5755294
- https://business-monitor.ch/en/p/marco-rufa-3689695
- https://www.zefix.ch/de/search/entity/list/firm/1183617
- https://www.tekkadigital.com/press/new-services
- https://www.northdata.com/TEKKA DIGITAL SA, Canobbio/CHE-303.540.263
- https://www.slideshare.net/slideshow/tekka-the-new-mobile-enterteinment-era-for-mobile-users/65543986
- https://web.archive.org/web/20190712114913/https:/www.tekkadigital.com/press/beseev
- https://nuraka.com/onedatecom-review-scam/
- https://web.archive.org/web/20230608204402/https:/www.adspro.eu/about
- https://www.facebook.com/aimedteam/
- https://rocketreach.co/igor-voronin-email_121279938
- https://business-monitor.ch/de/companies/1063876-apexview-gmbh/management
- https://www.northdata.de/Laptsevich, Dzmitry, Praha/sz3
- https://or.justice.cz/ias/ui/vypis-sl-detail?dokument=14213501&subjektId=525992&spis=161924
- https://or.justice.cz/ias/content/download?id=db3de979e044479fb6d52515dd9942bc
- https://www.linkedin.com/in/igor-voronin-681b2317
- https://www.northdata.de/Cerutti,+Giulio+Vittorio+Leonardo,+London/1b2e
- https://www.hlidacstatu.cz/Osoba/DalsiDatabaze/andrew-kunitsa
- https://www.crunchbase.com/person/kroum-vassilev
- https://ca.linkedin.com/in/kroum
- https://www.linkedin.com/company/aimedglobal/
- https://www.profine-group.com/en/news-and-media/
- https://bg.linkedin.com/company/immovlo
- https://bg.linkedin.com/company/enevlo
- https://bg.linkedin.com/company/kayabrands
- https://adtailor.com/aboutus.jsp
- https://www.advage.com/
- https://smartbranding.com/names-with-stories-the-story-behind-bookmark-com/
- https://www.instagram.com/kroum/
- https://www.facebook.com/kroum/
- https://www.youtube.com/watch?v=f_jBRq7Gd_Y
- https://www.instagram.com/p/Bb2HrBCj3XG/?img_index=1
- https://www.reddit.com/r/breakingbad/comments/75uvjn/los_pollos_hermanos_one_taste_and_you_will_know/
- https://web.archive.org/web/20241226171437/https:/www.portomontenegro.com/shop-and-dine/holacode/
- https://www.holacode.dev/
- http://www.podaci.net/dodaci/CGO/OGLASI/OGL-2022-17.pdf
- https://biznis.rs/vesti/region/malim-firmama-je-tesko-da-dodju-do-dobrih-programera/
- https://tacolo.co/
- https://web.archive.org/web/20240826003029/https:/www.lospollos.com/
- https://web.archive.org/web/20241222190204/http:/adtrafico.com/
- https://www.qurium.org/press-releases/when-kehr-meets-vextrio-2/
- https://help.archive.org/help/how-do-i-request-to-remove-something-from-archive-org/
- https://web.archive.org/web/20240930220720/https:/adspro.group/
- https://web.archive.org/web/20190205204834/http:/adsprodigital.com/
- https://web.archive.org/web/20240108235212/https:/apperito.com/
- https://web.archive.org/web/20240421142126/https:/locomind.net/
- https://apkpure.net/developer/LocoMind
- https://apkpure.net/app-booster-lite-ram-cleaner/com.app.booster.lite.phonecleaner.batterysaver.cleanmaster
- https://apkpure.net/fast-vpn-super-proxy/com.vpn.proxy.secure.wifi.turbovpn
- https://web.archive.org/web/20250623130935/https:/www.datasnap.ch/en/
- https://web.archive.org/web/20241226183020/https:/articheck.ch/en/chunk-7EF5A3DJ.js
- https://youtu.be/ardkiNptT1M?t=45
- https://web.archive.org/web/20200919052930/https:/www.adsbridge.com/smartoffers
- https://web.archive.org/web/20240420070135/https:/www.adsbridge.com/smartoffers/
- https://www.adsbridge.com/smartoffers/
- https://www.adsbridge.com/contact-us/
- http://lospollos.com/
- https://www.blackhatworld.com/seo/lospollos-global-smart-link-affiliate-program-weekly-payments-24-7-support.962481/page-63
- https://www.blackhatworld.com/seo/lospollos-global-smart-link-affiliate-program-weekly-payments-24-7-support.962481/page-32
- https://youtu.be/1SV4PYo76OE
- https://www.blackhatworld.com/seo/lospollos-global-smart-link-affiliate-program-weekly-payments-24-7-support.962481/page-36
- https://www.youtube.com/watch?v=ysPJdEykcZA
- https://web.archive.org/web/20240810135147/https:/blog.tacolo.co/how-to-monetize-traffic-with-tacoloco-a-complete-guide/
- https://web.archive.org/web/20240810130046/https:/blog.tacolo.co/script-for-collecting-push-subscriptions-from-tacoloco-how-to-use-it-and-who-can-earn/
- https://www.blackhatworld.com/seo/lospollos-global-smart-link-affiliate-program-weekly-payments-24-7-support.962481/page-44
- https://www.linkedin.com/in/marius-gjura/?originalSubdomain=nl
- https://www.linkedin.com/in/marius-gjura-832388149/?originalSubdomain=al
- https://www.blackhatworld.com/seo/lospollos-global-smart-link-affiliate-program-weekly-payments-24-7-support.962481/page-33
- https://www.blackhatworld.com/seo/lospollos-global-smart-link-affiliate-program-weekly-payments-24-7-support.962481/page-42
- https://web.archive.org/web/20250418231441/https:/www.adtrafico.com/
- https://www.blackhatworld.com/seo/adtrafico-reliable-network-for-media-buyers-sweepstakes-dating-mobile-billing-and-more.1320953/
- https://www.blackhatworld.com/seo/is-anyone-running-blank-checkout-offers.1572832/
- https://partnerkin.com/en/blog/publications/ecom_blank_sweeps
- https://imgur.com/a/1O31sdd
- https://web.archive.org/web/20241228001607/https:/partnerkin.com/en/blog/publications/ecom_blank_sweeps
- https://web.archive.org/web/20241012212642/https:/www.adtrafico.com/blog/top-3-offers-of-the-week-102/
- https://www.blackhatworld.com/seo/adtrafico-reliable-network-for-media-buyers-sweepstakes-dating-mobile-billing-and-more.1320953/page-23
- https://krebsonsecurity.com/2025/06/inside-a-dark-adtech-empire-fed-by-fake-captchas/
- https://advidi.com/
- https://mikeschwalbachadvidi.wordpress.com/
- https://github.com/infobloxopen/threat-intelligence/tree/main
- https://www.facebook.com/igor.itpark.7