This is the second in a three-part, in-depth report covering nearly a year of research into VexTrio. To learn more about the people and entities involved, see the first part here. To learn about VexTrio’s infrastructure and technology stack, see here. VexTrio domains and references from this research can be found in our GitHub repository.
VexTrio is a cybercriminal organization with tendrils that are far-reaching. But at the core of their operations are scams and spam. As we described in the first part of this research, key figures in VexTrio have been involved in fraudulent activity since at least 2004. Images of VexTrio’s fake CAPTCHA robots have been included in a multitude of reports about fraudulent activities for years. Their affiliate networks offer so-called smartlinks in many verticals, including dating, crypto, and sweepstakes. These links hide (“cloak”) the landing page and hinder analysis by security teams. They are embedded into compromised websites, Instagram messages, Facebook, and even email security tools. Regardless of the starting point, the final landing pages are all scams, both in our experience and as widely reported by others in the industry.
The infamous VexTrio robot
While the fact that the VexTrio traffic distribution systems (TDS) deliver scams is wellknown, it is not widely known that most of the time VexTrio is delivering their own scam content, rather than that of independent advertisers. As a result, they benefit in multiple ways from embedding their smartlinks in compromised websites and social media. Fraudulent sites include a wide range of marketing verticals, most prevalently dating and cryptocurrency. Many affiliate networks will cite abuse when advertisers deliver malicious content to users, but VexTrio will have difficulty making this claim. There is substantial evidence that demonstrates that they control the landing pages.
VexTrio also offers fake VPNs, ad blockers, and other apps. Available in Google Play and the App Store, as well as via direct download sites, the apps have been downloaded over a million times in aggregate over several years. They show incessant ads to users, bind them into subscription contracts that are difficult to cancel, and convince them to reveal personal information like email addresses.
But this software also reveals the murky line between VexTrio and their business partners. Apps created by VexTrio appear to be identical to those offered by two of their advertisers based in Prague, and they share hosting with VexTrio’s development group, HolaCode. These overlaps raise questions about the relationship between VexTrio and VexTrio advertisers. Just how distinct are they? Beyond the shared code, there is a personal link: a founder of one of the companies, Techintrade, was also previously a managing director at VexTrio’s AdsPro Group. If the software and hosting of Technitrade apps are identical to those of AdsPro and the second firm, Oilimpex, how does this company relate to VexTrio? We aren’t sure, but it does hint at the potential that the full extent of the VexTrio enterprise is even larger than we know.
Another pillar of their enterprise is spam, which they use in a vicious cycle with their scam operations. They blatantly copy major direct email marketing (DEM) companies, like SendGrid, and use generic terms, like Fidelity Mail to avoid detection. Try searching sendgrid[.]rest in a search engine and see for yourself. Fidelity Mail claims to give their customers access to over 220 million verified email addresses. Where do they get those email addresses? Based on our personal experience, they come from their fraudulent sites and apps. A victim’s journey includes numerous requests for email addresses to win a free gift card, join a dating app, or recover some lost cryptocurrency. Entering an email is often an action in their cost-per-action affiliate marketing model.
In spite of the number of email marketing companies they own, VexTrio’s domain name system (DNS) records lack diversity, tying email distribution domains to their very own TacoLoco. We used DNS records and our own spam collection to analyze how their spam and scam operations tie together. Of note, we found that in addition to their own mail servers, VexTrio is contracting with third parties like YNOT Mail for spam distribution. We will show how the domain datingcell[.]com was used in dating-themed spam. Buttons that are included in the email allow YNOT Mail to track clicks, which when pressed will lead users to VexTrio fake dating sites. VexTrio’s scams feed their spam, and their spam feeds their scams.
Besides classic spam and scam operations, the key figures are involved in dozens of other businesses, primarily micro-companies. Many of these have little connection to the advertising industry. Some of them are quite puzzling to us, and we’ll provide some examples in this blog. For example, one of the firms is connected to a promised €1 billion investment in Bulgaria to provide solar energy by a German manufacturing group. How does a businessman from the adult industry become the head of such a large national endeavor? We don’t know, but it certainly shows that it pays being in the malicious adtech industry.
We have included numerous links to supporting evidence throughout this paper. All these hyperlinks were active in early July 2025. Names, domains, and companies may appear in this report only because of technical or business link to VexTrio; their mention alone does not mean they knew of or took part in any wrongdoing. Specific illegal activity claims are explicit and backed by cited evidence.
Scam Sites
The scams promoted through VexTrio smartlinks have been covered numerous times over the years (like here and here and here and here), but what isn’t widely known is that they also create the majority of the content they deliver. Thus VexTrio benefits twice when publishing affiliates distribute their smartlinks. The affiliate networks (Los Pollos, Adtrafico, TacoLoco) offer several verticals, including dating, adult-only, sweepstakes, nutra industry vertical, and crypto-related advertisements—and they offer scams for each of these verticals. See Figure 1 for a sample of the many landing pages that we have confirmed are controlled by VexTrio.
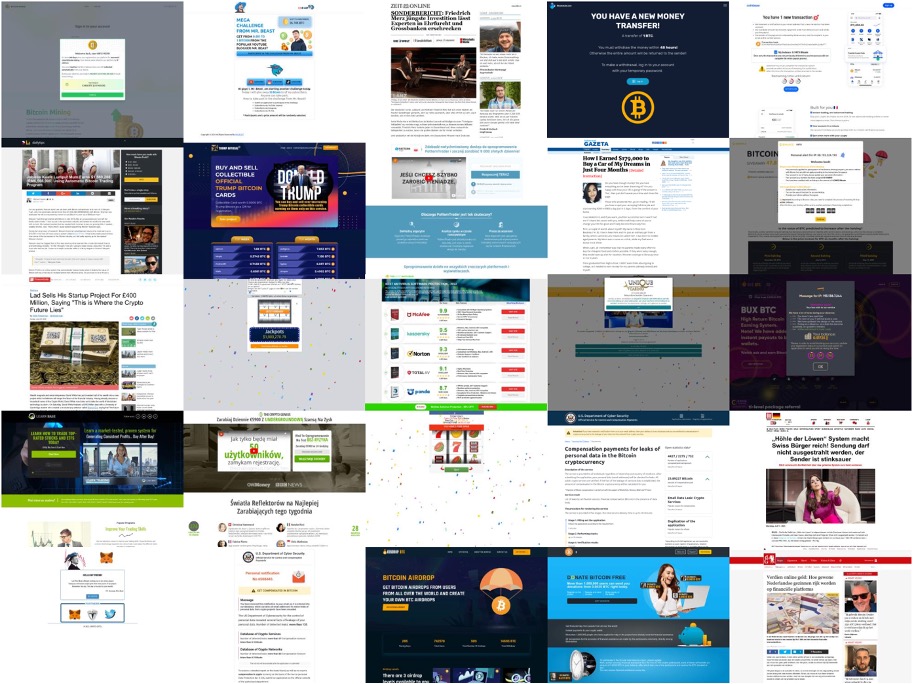
Figure 1. A collage of scam landing pages related to VexTrio’s cryptocurrency, investment, sweepstake, and antivirus scam verticals
The dating verticals are the most popular. VexTrio’s firm Teknology owns trademarks for some of their dating sites, including OneDate. While their dating and hookup sites claim to connect customers to real people, they are widely reported as scams. Reviews of many VexTrio sites state that they require subscriptions that are difficult to cancel, the profiles are not real people, and the central part of the service is a fake chat scam. In these fake chats, users are charged excessive amounts to send messages, but without the possibility of meeting someone in real life. We have interacted with their sites and created accounts dozens of times. Even when their sites put up control questions, such as “Are you 18?”, you will be allowed into the content and a constant stream of connection requests from fake profiles will begin. Besides their trademarked brands, several other brands have long been associated with Tekka/Teknology, including OnlyOne, which can be seen hosted in their dedicated Swiss IP range, as well as hidden in Cloudflare.
Trademark ownership is one way to connect VexTrio directly to the scam sites, but there is other evidence as well. Based on the volume of DNS queries and observed redirection chains, the VexTrio TDS delivers content more often from their own hosting, for example, AS5368, than external partners, such as PropellerAds and Traffic Partners, which are listed on their website. Through the use of smartlinks, VexTrio determines what gets shown to end users and the DNS query volumes indicate that favor themselves.
The evidence that the landing pages belong to VexTrio includes unique web artifacts employed by no other entity. More decisively, TDS servers we have linked to VexTrio are hosting the scam toolkits directly. When delivering these scams to victims, those TDS servers use the following URL patterns:
| URL | Vertical |
|---|---|
| hXXps[:]//fastminingpro[.]com/payouts/ | Cryptocurrency Scam |
| hXXps[:]//bit-wagifouzolu[.]top/transfers/ | Cryptocurrency Scam |
| hXXps[:]//base-fastbitco[.]top/threads/transfers?u=d4w264 | Cryptocurrency Scam |
| hXXps[:]//cryptoprofit[.]life/?u=fmkpte4&o=m45kwzr&t=html | Investment Scam |
| hXXps[:]//www[.]pattern-trader[.]net/lp?k=acf93&i=25e7&utm=941d7b3f-1ca7-470b-8ccd-641a056c15d4 | Investment Scam |
| hXXps[:]//place-more-prizes[.]life/?u=m5uwwwl&o=frcpbz7&t={affiliate_id}&cid={transaction_id} | Dating Scam |
| hXXps[:]//defendyourpc[.]com/shield/norton_global_2_new/?lpkey=17de31083311094c36 | Antivirus Scam |
| hXXps[:]//multipleprofit-now[.]life/?u=30wweky&o=pvkptz3&t=CryptoSingnetSG | Sweepstakes Scam |
VexTrio landing pages infringe on high-profile brands, such as Tinder and PornHub, and use images from high-profile public figures. Previous cryptocurrency and investment campaigns have appropriated the brands of famous YouTube celebrity MrBeast, President Donald Trump, billionaire Elon Musk, and even the Cybersecurity and Infrastructure Security Agency (CISA). Figure 2 shows how VexTrio blatantly pirates celebrity trademarks to deceive users into participating in its cryptocurrency scams.

Figure 2. VexTrio blatantly infringes on the trademarks of MrBeast, President Trump, and Elon Musk to deceive users into participating in its cryptocurrency scams.
Scam Apps
In addition to their direct scams and push notifications, VexTrio has developed malicious apps over the last several years, including VPNs, device “monitoring” apps, spam blocker apps, and dating apps. They released apps under several developer names, including HolaCode, LocoMind, Hugmi, Klover Group, and AlphaScale Media. Available in Google Play and the App Store, these have been downloaded millions of times in aggregate. High ratings for the apps hide the true nature of the software, and it is only in the one- and two-star reviews that it becomes clear that they are scams.
Dating apps like Hugmi and Cheri have been downloaded over a million times each on the Google Play store, despite reviews that reveal their scam nature. Like many scam chat apps, these require users to buy coins to send text messages, while also forcing users to watch ads. These apps were originally released by LocoMind but the developer information was changed to MateyX sometime in 2024. WinkChat, an app released by VexTrio group AlphaScale Media GmbH is ranked 158th in the Apple Store’s social networking category. Reviews for all of these include comments about bot accounts and incessant advertising. A TikTok review of dating app similar to those offered by VexTrio describes the full scam.
These apps can be tied to the VexTrio enterprise in multiple ways, such as through developer information, which often lists one of the shell companies, and through DNS records. Figure 3 shows that the IP address 136[.]243[.]216[.]249 was used simultaneously to host HolaCode, AdsPro Digital, Los Pollos, and multiple scam apps. Late into our investigation, we discovered in-depth research by Cyjax that also demonstrated the link between HolaCode and several scam apps.
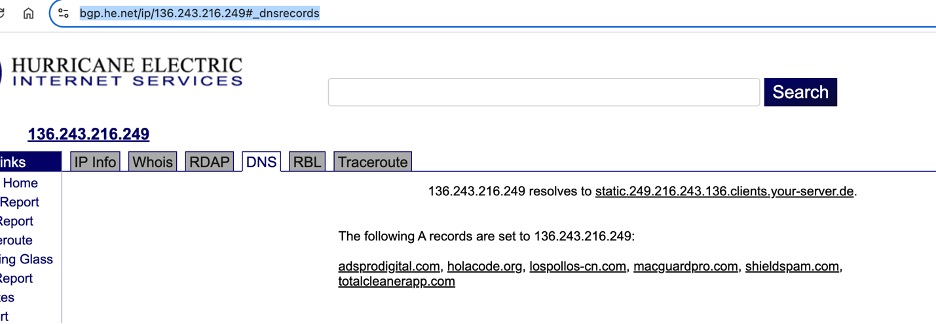
Figure 3. DNS records show that VexTrio domains are resolving at the same dedicated IP address as scam apps. Captured June 2025.
Let’s take a look at one of VexTrio’s adblock scam apps: Spam Shield. It’s been available on Google Play since 2021, and claims to be a spam blocker for push notifications. In July 2025, the app’s Google Play page urged “Just give us permission and you won’t see any spam or unwanted notifications. Trust us – we only want to protect you, your data is safe!” The variant shown in Figure 4 had garnered over 100,000 downloads in December 2024. The real deal? While it claims to eliminate threats, this app simply turns off browser notifications. Spam Shield displays a fake monitor showing notifications and spam email that it has blocked. After 24 hours, the user is forced to pay for a subscription ($6.99 per month in December 2024) to continue service.
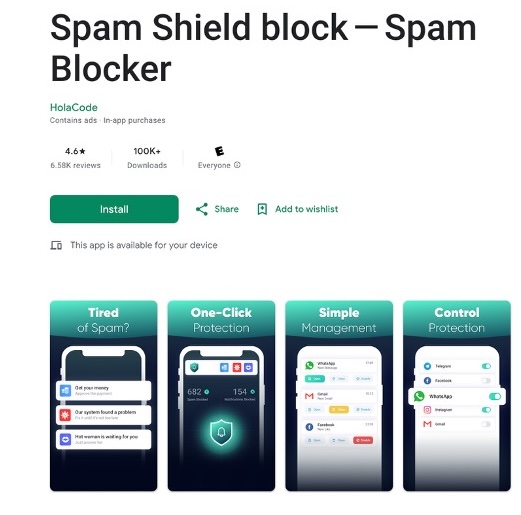
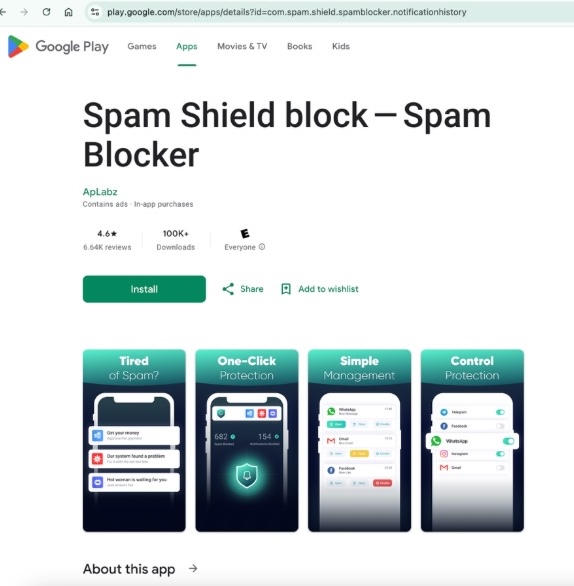
Figure 4. Google Play page for the Spam Shield app listed as developed by HolaCode in December 2024 and ApLabz in early 2025. This app is uniquely identified as com.spam.shield.spamblocker.notificationhistory. The Spam Shield privacy policy as of June 2025 still says HolaCode.
The scam apps often have an accompanying website; we show Spam Shield’s in Figure 5. This page links the domain to Media Alliance s.r.o., another VexTrio company.
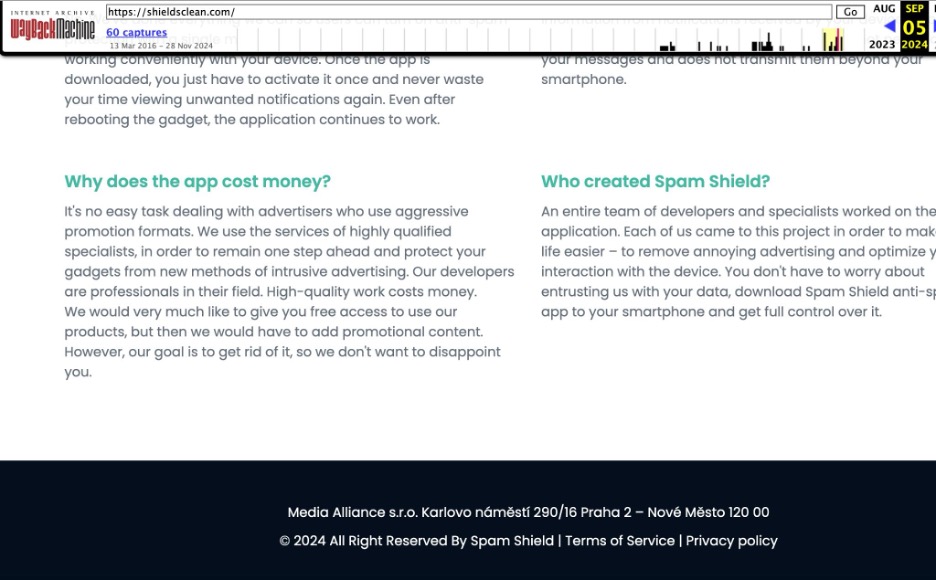
Figure 5. Spam Shield website links the app to the company Media Alliance s.r.o. Captured September 2024.
The VexTrio VPN apps are residential proxies. Everyone in the security community will cringe and sigh at that news. Not surprisingly, these “VPNs” have been reported for questionable privacy. Figure 6 shows one example, Fast VPN, which was released in 2021 by LocoMind to Google Play. An app with the same name was also released on the App Store under the developer name Alpha Scale Media and with the site eugene-ios-mvp[.]apperito[.]dev; see Figure 7. Both Alpha Scale Media and Apperito are known VexTrio companies. VexTrio is frequently changing their developer information while forgetting to clean up the details. The terms and conditions of Fast VPN as of July 2025 refers to Ads Guardian rather than the VPN.
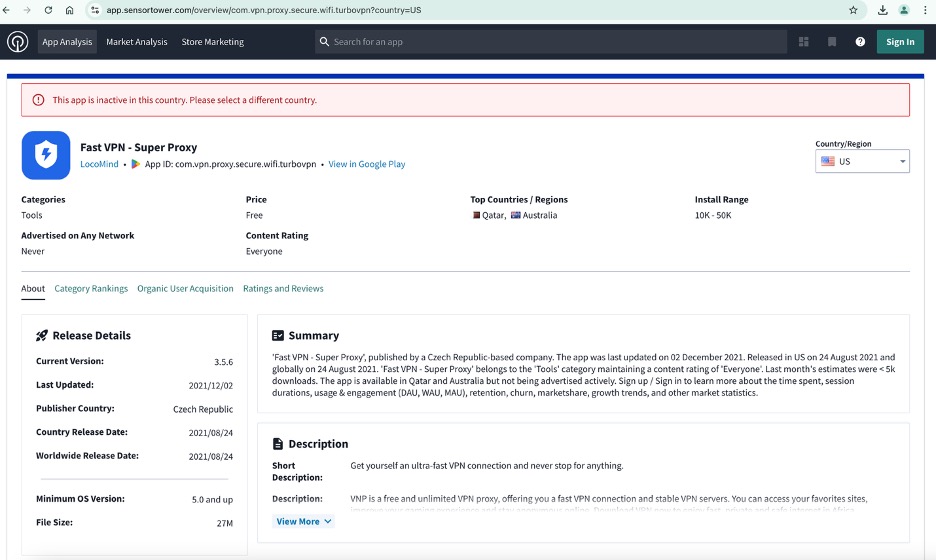
Figure 6. Information about Fast VPN shows that it was developed by LocoMind, a VexTrio entity. In the App Store, the developer is listed as Alpha Scale Media.
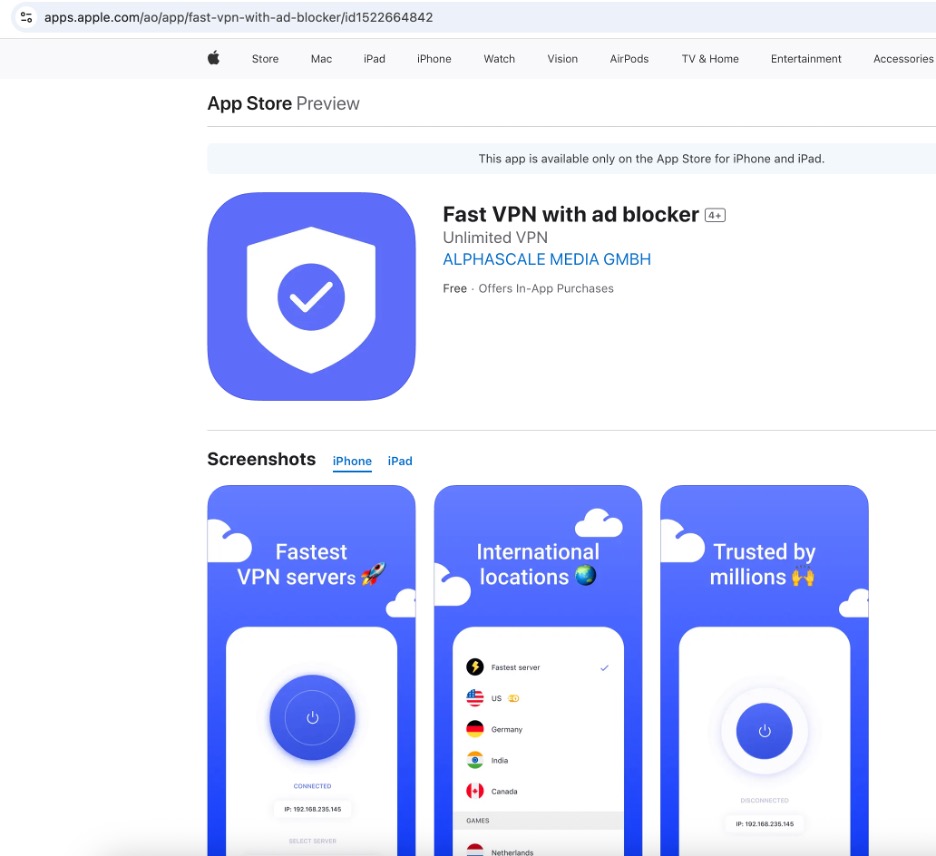
Figure 7. Fast VPN advertised on the App Store by Alphascale Media GmbH as of July 2025.
The app ID name for Fast VPN includes the phrase “turbovpn”, a well-known commercial VPN. Wouldn’t you think that an app with the ID com.vpn.proxy.secure.wifi.turbovpn would be related to the extremely popular Turbo VPN? Presumably, confusion is the goal. And as far as we know, there is no relationship between the Turbo VPN and any of the fake VPNs offered by VexTrio. This is consistent with VexTrio’s tactic of choosing product and company names that overlap with legitimate ones.
VexTrio and their advertising partners sometimes appear to have a shared codebase. For example, VexTrio’s Spam Shield is almost identical to several other “spam blockers” available on Google Play. Figure 8 shows a comparison of the Spam Shield interface with that of Spam Lock. The screenshot from Spam Shield is taken from one of our personal devices in January 2025, while the screenshot of Spam Lock was taken from Google Play. But Spam Lock is not the only twin app to Spam Shield; there are many others, purportedly by different developers. For example, we’ve seen nearly identical apps cited in Japanese reporting on scareware apps.
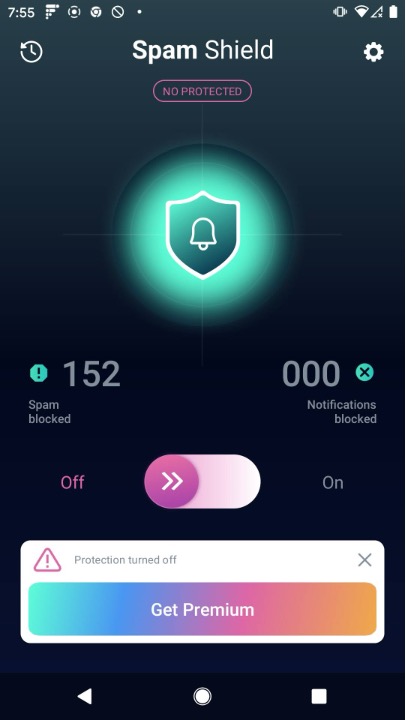
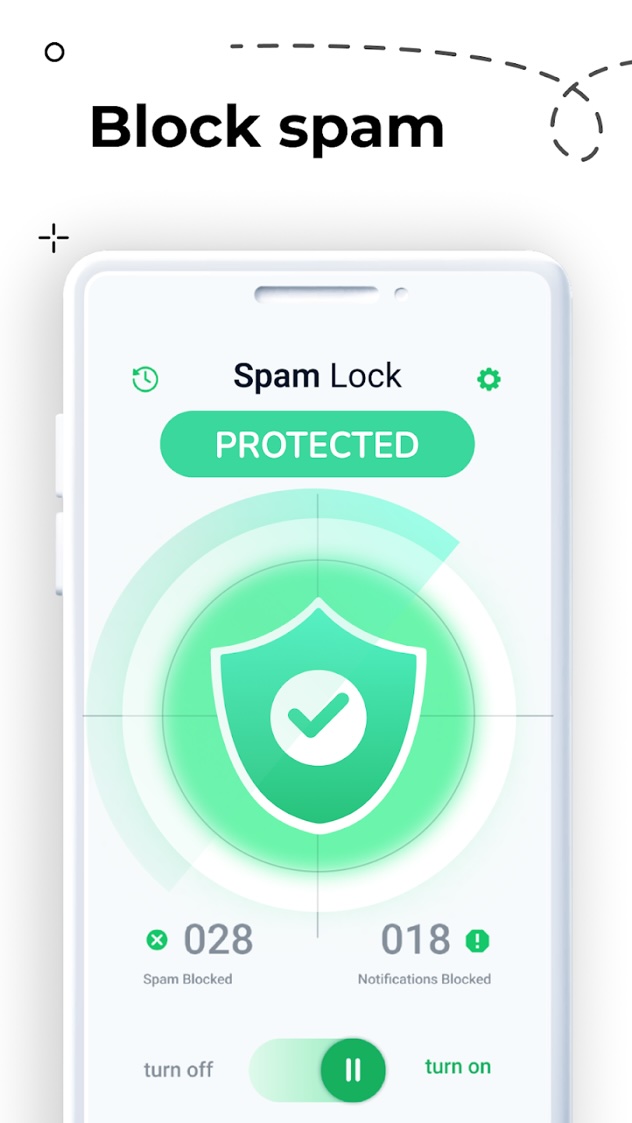
Figure 8. The main screen of the VexTrio scam app Spam Shield in comparison to the Spam Lock scam app by VexTrio advertising partner, Techintrade. The screenshot on the left came from a personal device in January 2025. On the right, is the Google Play image captured June 2025.
Spam Lock is supposedly developed by DevTapX, who is also listed as the developers of another nearly identical app, True Blocker. But wait, there’s more! The terms and conditions for True Blocker are nearly identical to those of another app, Spam Guard; see Figure 9. In early January 2025, these pages included the addresses of the responsible parties, and linked the apps to Techintrade s.r.o. and OILIMPEX s.r.o., two entities with Prague addresses and connections in Cypress. Searching in Google Play and the App Store will reveal many more almost identical scam apps.
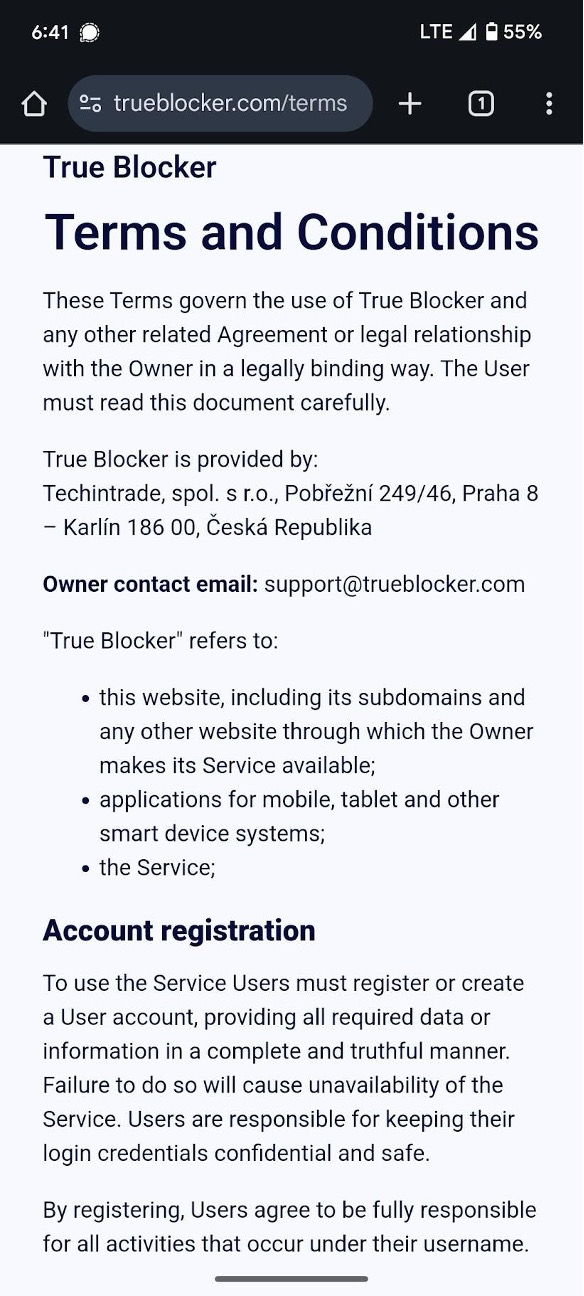
Figure 9. VexTrio advertising partners Techintrade and OILIMPEX offer scam apps that have identical terms of service structure. The apps True Blocker and Spam Guard are remarkably similar to VexTrio’s own Spam Shield. Captured January 2025. As of July 2025, both websites have been altered to remove company references.
Techintrade, spol s.r.o. and VexTrio appear to have a relationship that goes well beyond one of customer and provider. Aside from the shared software, in the registration documents for Techintrade filed in 2000, the Belarussian Katsiaryna Torapava (b. 1971) is listed as one of the founders. In 2019, Igor Voronin and Andrew Kunitsa assigned Katerina Toropova as a director for AdsPro Group; see Figure 10. While the spellings are different, the birth dates are the same. In 2024, Techintrade appears to have claimed no income in online marketing.

Figure 10. An extract of a 2019 record in which Andrew Kunitsa and Igor Vornin name Katerinu Toropovou (nominative Katerina Toropovo), as managing director of AdsPro Group. This is the same birthdate and near-identical name to one of the founders of Techintrade s.r.o.
OILIMPEX was founded in 2002 by Dmitri Pachenko (b. 1962), also from Belarus. He later registered Overdrive Systems in 1999. But, beyond seemingly sharing software with OILIMPEX and VexTrio, we don’t know much about Pachenko or the company. The financial records are available on the Czechia government website.
Finally, these two companies are included as hostnames in DNS records of holacode[.]tech. The domains vm-oilimpex.holacode[.]tech and vm-technitrade.holacode[.]tech resolve to 185[.]155 [.]186 [.]134, a dedicated VexTrio IP address as of mid-July 2025. While the exact nature of their relationship isn’t known, it appears close in nature!
Spam
Los Pollos insists that it does not work with affiliates who drive web traffic through spam emails, and its website prominently states a zero-tolerance policy. Yet behind the scenes, VexTrio is a major spam distributor that reaches out to millions of potential victims. DNS records reveal that VexTrio uses lookalike domains of globally renowned mail services. Most notably SendGrid, with sendgrid[.]rest, and MailGun, with mailgun[.]fun. We don’t know if these companies have any financial relationship with VexTrio entities or whether they are aware of the infringement. These two domains have mail-related DNS TXT records providing the domains’ sender policy framework (SPF) policy
v=spf1 a mx ip4:78[.]47.103.187 ~all
which authorizes 78 [.] 47 [.] 103 [.] 187 to be the sole email distributor for the domain.
The DNS PTR record for this IP address is mail[.]holaco[.]de as of July 2025. Hola Code is the VexTrio entity responsible for the software development behind their many commercial services. In addition, numerous other VexTrio domains are also connected to the mail server at this IP address.
While we focus on DNS, we also collect and analyze spam. Our database contains many emails featuring links to TDS domains operated by VexTrio. Distributed from a variety of mail servers, these messages originate from both VexTrio entities and their affiliates. Among them are several domains that were used both in the links as well as the email address that sent the email. Those domains were configured with the DNS TXT record
v=spf1 include:_spf.smtp.com include:_spf.ynotmail.com ~all
This SPF record is recursive and might be tricky to understand. It tells receiving mail servers that any IP address matching the mechanisms defined in the SPF records at _spf.smtp.com or _spf.ynotmail.com is authorized to send emails on behalf of the domain. So, the receiving server has to then check the SPF records for those delegated domains. The TXT record for _spf.ynotmail.com was recently set to include several large IP ranges, but that’s not particularly important for this story. The important point is that domains that are definitively owned by VexTrio, for example, datingcell[.]com, have used a service to deliver mail on their behalf.
YNOT Mail is a commercial, subscription-based paid email marketing platform, and we suspect that VexTrio contracts (or contracted) with YNOT Mail for additional mail delivery beyond their own mail servers. To our knowledge, YNOT Mail is not part of VexTrio but merely a conduit to further their spam campaigns.
The domains with the YNOT Mail SPF record include:
- cuddlydating[.]com
- datingcell[.]com
- empowermanpower[.]com
- hedonism[.]global
- hpc[.]marketing
- hpc[.]world
This implies that YNOT Mail is distributing email on behalf of these domains. But at the same time, these domains are advertising themselves as email marketing firms. The domains datingcell[.]com, cuddlydating[.]com, and hpc[.]marketing previously displayed homepages that promised customers access to “over 220 million addresses.” What struck us was that these sites used virtually the same web template as fidelityemail[.]com, a domain that belongs to VexTrio’s email marketing company Fidelity Mail.
Figure 11 presents a side-by-side comparison of the homepages for fidelityemail[.]com and datingcell[.]com. Because nothing is simple with VexTrio, of course Fidelity Mail does not use the YNOT Mail SPF record. Instead, it is tied to 78[.]47[.]103[.]187, the IP address for mail.holaco[.]de. The websites are not only using the same template, but datingcell[.]com resolves in VexTrio’s Swiss data center IP range. This combination of factors implies that the group relies on third-party servers to conduct some of their email campaigns.
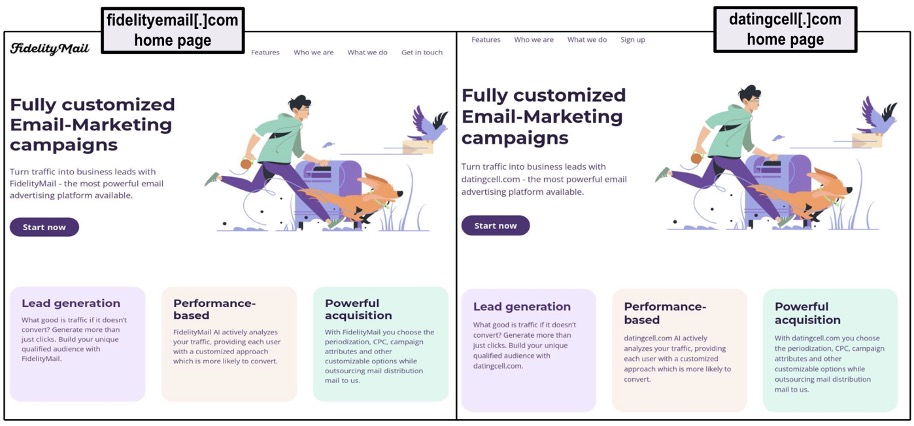
Figure 11. Snapshot of the fidelitymail[.]com and datingcell[.]com websites, captured on November 16, 2024
The domain datingcell[.]com was used to deliver dating scams. We found dating-spam emails in our own spam collection. For example:
- Emails were sent from postmaster[@]datingcell[.]com via the SMTP host at 99[.]192[.]179[.]143.
- That IP belongs to smtp[.]trafficiq[.]com, a mail-server domain operated by YNOT Mail.
- To grab recipients’ attention, VexTrio personalizes the subject lines with second-person phrasing, for example:
- “Fakeemaiy01, Eva just sent you a new message & wants to meet 💌”
- “Maili88, do you want to meet? I’m from Bingen am Rhein too”
- “Diana from Kingston is viewing your Fakeemaiy01 profile NOW 💋”
Each email contains an HTML message that masquerades as a chat or text exchange from a prospective dating partner; see Figure 12.
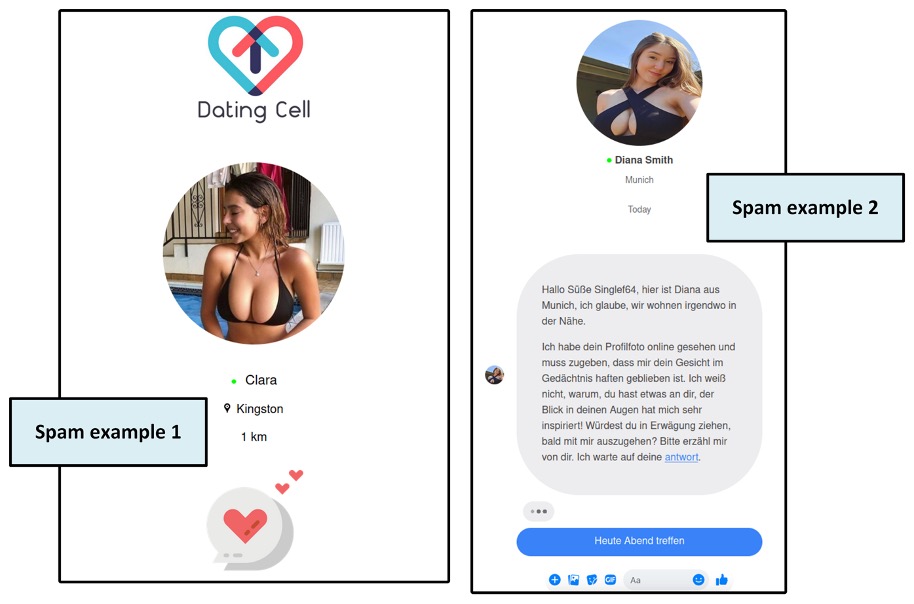
Figure 12. Examples of spam emails sent by VexTrio seen in Infoblox data. This shows the email’s HTML body content, which is embedded with a link that redirects to datingcell[.]com.
The buttons in the HTML messages are embedded with a trafficiq[.]com PHP link that belongs to YNOT Mail and tracks user clicks. Afterward, the tracker redirects the victim to VexTrio’s dating scam (see Figure 13).
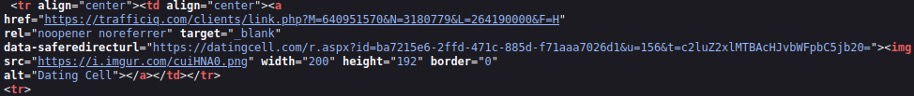
Figure 13. Spam HTML message contains embedded trafficiq link that redirects to the datingcell[.]com scam page.
Once the victim lands on the dating-themed scam, VexTrio masquerades as a fictional dating site called “BIGO LOVE.” This fake site is served by IPs in AS5398—part of VexTrio’s data center located in Lugano, Switzerland. The spoofed site walks the visitor through a short questionnaire designed to profile their online behavior (Figure 14). After harvesting this information, VexTrio silently forwards the user to one of its adult content advertisers and collects a referral commission.
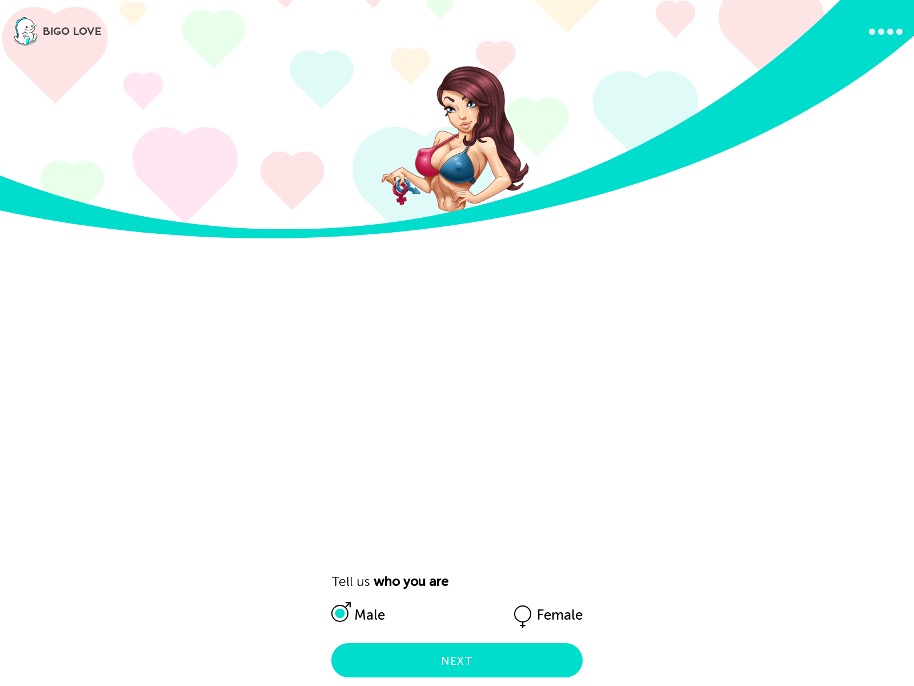
Figure 14. Dating scam on landing page that uses the datingcell[.]com domain
We reviewed datingcell[.]com domain registration records and web archives predating 2023 and found several suspicious indicators. While we cannot definitively confirm that VexTrio owned the domain before 2023, we did uncover artifacts consistent with the group’s known activities, as well as other forms of fraud operation. Figure 15 displays web content that datingcell[.]com used in late 2017; its purpose was to share contact information of dating candidates.
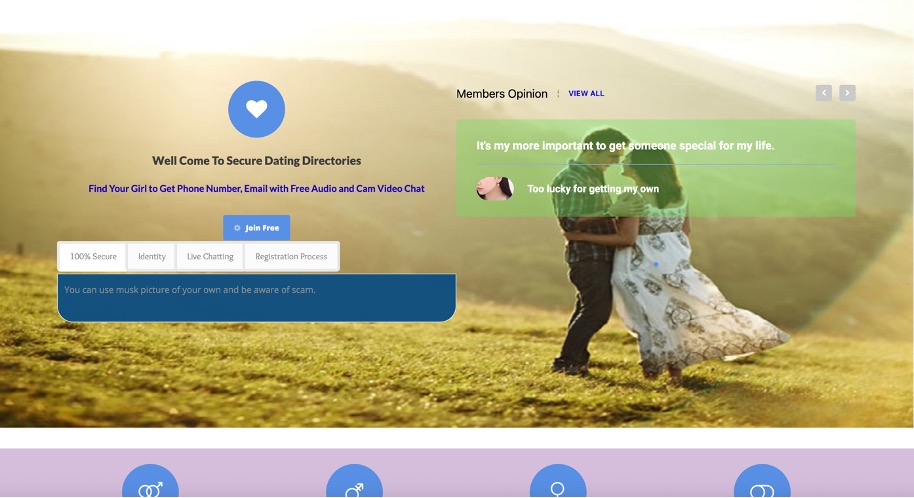
Figure 15. Screenshot of datingcell[.]com used by a dating portal site in December 2017
In mid-2017, the domain was abused by threat actors for phishing attacks and it targeted various brands including Google products, Dropbox, and the Christian Mingle dating site. Figure 16 shows a phishing page hosted on datingcell[.]com that impersonated Dropbox while presenting a fake Gmail sign-in form.
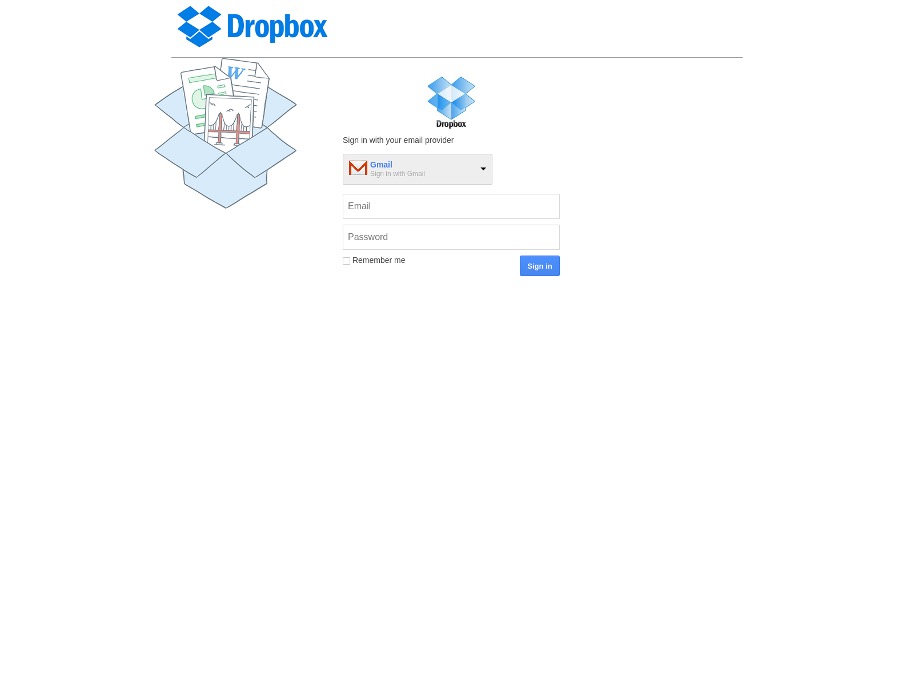
Figure 16. Screenshot of datingcell[.]com, which was used in a phishing operation targeting Dropbox in 2017
Early registration records for datingcell[.]com point to a figure whose background mirrors that of VexTrio’s leadership. In 2011, Yevgen Telychko registered the domain using the email address yevgen[@]telychko[.]com (Figure 17). According to his LinkedIn page, Yevgen grew up in Ukraine and has extensive experience in affiliate marketing, including the dating industry.
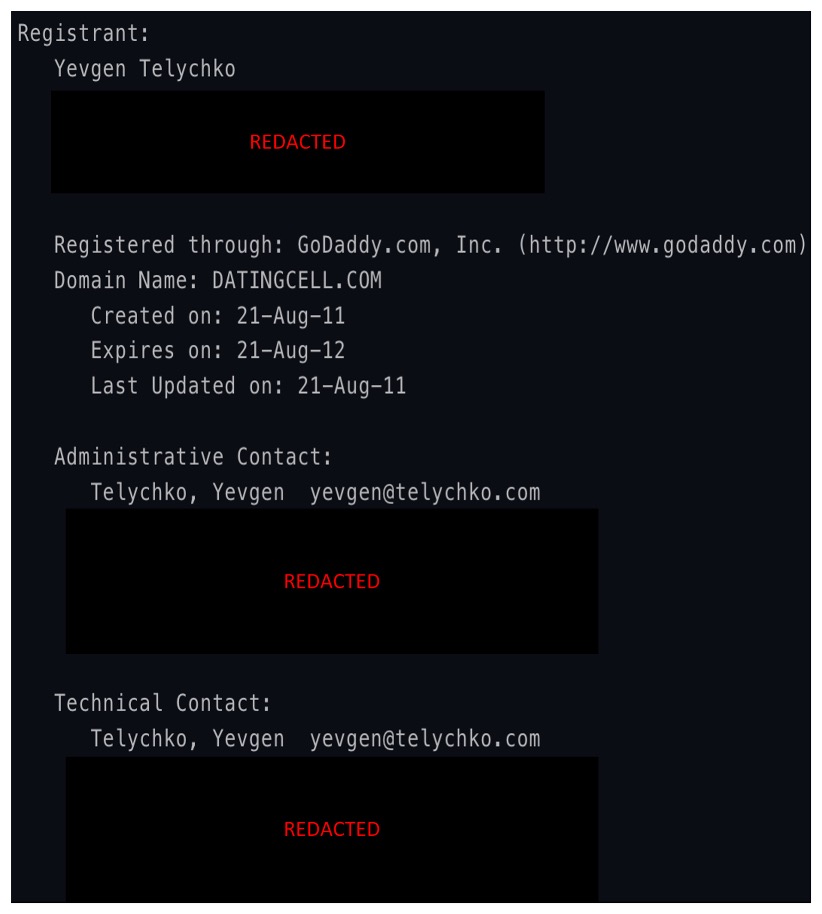
Figure 17. 2011 domain registration details of datingcell[.]com showing contact details for Yevgen Telychko, a Ukrainian with extensive dating affiliate marketing experience
At the time of writing, the base pages for datingcell[.]com, cuddlydating[.]com, and hpc[.]marketing all display a simple maintenance notice: “The website is undergoing maintenance. Please come back later.” One of VexTrio’s other email marketing platforms, articheck[.]ch also appears offline. Homepages of VexTrio’s email marketing platforms fidelityemail[.]com (Fidelity Mail) and datasnap[.]ch (Datasnap) are still currently available. Articheck has at times redirected to DataSnap. See Figure 18.
Figure 18. Webpages for articheck[.]ch and datasnap[.]ch as captured in 2024
And More?
VexTrio-related DNS records confounded us for years. How was it possible that IP address space almost entirely dedicated to malicious operations also hosted ski resorts, gift shops, and restaurants? The discovery of VexTrio’s true identity as a global enterprise made us realize these were not outliers, they were all part of the extended commercial enterprise. But how? We are not sure. Besides those hosted in VexTrio data centers, the key figures in VexTrio are connected to dozens of companies, many seemingly unrelated to their core spam and scam business model. Many of these businesses are involved in very large-scale financial transactions.
For example, it is a puzzle to us how a German company, Profine Energy GmbH ended up in a deal with Kroum Vassilev (through Enevlo EEOD) to create Profine Energy Bulgaria. Kroum is not only the self-described cofounder of AdsPro and Los Pollos but has a long history in industries that are, shall we say, not in the energy sector. This type of business relationship highlights the complex nature of analyzing the VexTrio extended enterprise; it is very hard to separate the good from the bad. According to the articles of registration, the initial capital of Profine Energy Bulgaria is 1,000 shares at 10 BGN each, worth about US$6,000 in July 2025. The company would develop “Bulgaria’s first floating PV plant in the northwestern part of the country, by the Ogosta reservoir” and that the project would “cost an estimated 600-800M Euro” to complete. Profine Energy reportedly signed a letter of intent to invest €1 billion into Bulgaria. Profine Energy is a subsidiary of the Profine Group, a plastics manufacturing company founded in 2003. According to reporting from September 2024, the solar plant is under development and expected to be commercial in 2026. Perhaps more than anything, the case of Profine Energy Bulgaria shows that the shady adtech and the adult industry are within arm’s reach of mega investment companies. Figure 19 shows companies that have indirect relationships with VexTrio or its leadership team.
Figure 19. Business entities with notable relationships to VexTrio key figures include marketing firms, a software development organization, payment processing, physical access systems, and ski resorts
To Conceal Fraud is Itself a Fraud
A scam is a deliberate scheme designed to defraud or deceive someone, usually for financial gain. It typically involves false promises, misrepresentation, or manipulation that persuade the target to hand over money, sensitive information, or some other valuable resource. With that definition in mind, we are astonished that VexTrio has operated—and thrived—for 15 years without facing legal consequences. Its activities fit every hallmark of a scam: using deception to corruptly steer unsuspecting internet users. Whether through bogus push-notification lures, “too-good-to-be-true” investment success stories that funnel traffic into cryptocurrency fraud, or blatant trademark abuse on platforms like TikTok and Tinder to inflate affiliate referrals to adult sites, VexTrio epitomizes the very practices the security community condemns.
The quote “There is nothing more deceptive than an obvious fact” by Arthur Conan Doyle (through Sherlock Holmes) reminds us that even highly educated security professionals are easily fooled by conditions that are simple to interpret. Too often, internet authorities dismiss anything that looks like adtech as low-severity nuisance. Cybercriminals can exploit this tendency, presenting selective facts that appear self-evident while concealing the larger and malicious reality. And so this begs the question, how long, do we as a community, keep turning a blind eye to stories like VexTrio’s? Our takedown efforts have caused temporary disruption, but they fall far short of ending the scheme.
We close with Publilius Syrus’s famous line: “Fraus est celare fraudem”—to conceal fraud is itself a fraud.
Now that we covered VexTrio’s fraudulent activities, we will move on to how their infrastructure is configured and the technology stack they rely on to run global operations. Find the next installment here.