The stereotypical picture of a hooded figure hacking from a basement is a misguided one when it comes to the threat actors behind many cybercrimes. Malicious adtech is a prime example. This type of cyberthreat is carried out not by lone individuals, but by professional organizations with many affiliates. On the surface, these entities may appear legitimate, which is how they snare their victims. In this post, we provide a brief overview of what this dishonest variant of adtech is, why it is dangerous and how DNS-based threat intelligence is uniquely suited to protect against it.
What Is Adtech and When Does It Become Malicious?
Advertising technology, aka adtech, is the collection of technologies and tactics marketeers use to increase the effectiveness of their efforts by engaging online audiences in a highly targeted fashion. Google AdSense is a well-known example of adtech you may be familiar with. If you’ve ever noticed that websites you visit are suddenly showing ads from products you’ve recently researched elsewhere, you’ve seen adtech in action.
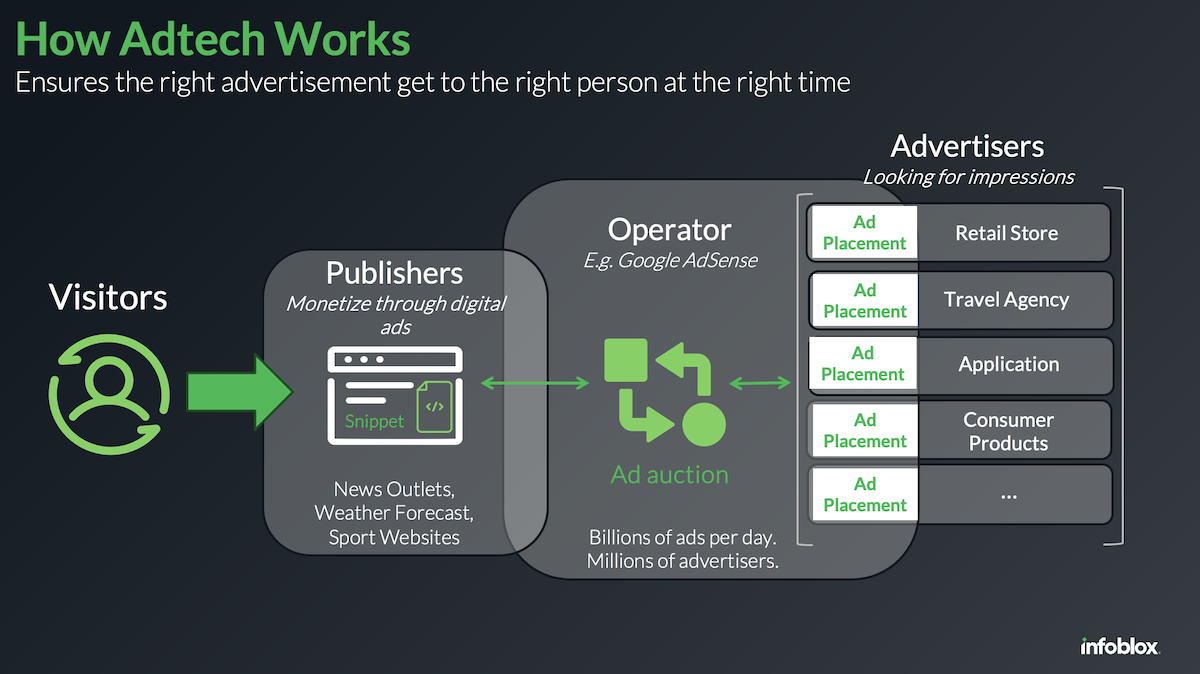
Figure 1: The three main participants in adtech.
Adtech involves three groups of key players: publishers, advertisers and operators.
- Publishers typically own a website containing content of interest to a specific audience. They look to monetize their online platform. Examples of publishers include news outlets, weather forecasting, specific interest groups, etc.
- Advertisers look to grab attention from potential buyers by sending promotional content, like banners ads, videos, sponsored articles and more. Advertisers always look to reach the right audience for their promoted services or products.
- Operators, like Google, act as the exchange between advertisers and publishers. They allow publishers to register their website with them and enable advertisers to place digital ads directly onto the publisher’s online presence. Operators take payments from the advertisers and pay publishers. Operators also provide advertisers the tools to find the right publishing sites that match audiences of interest.
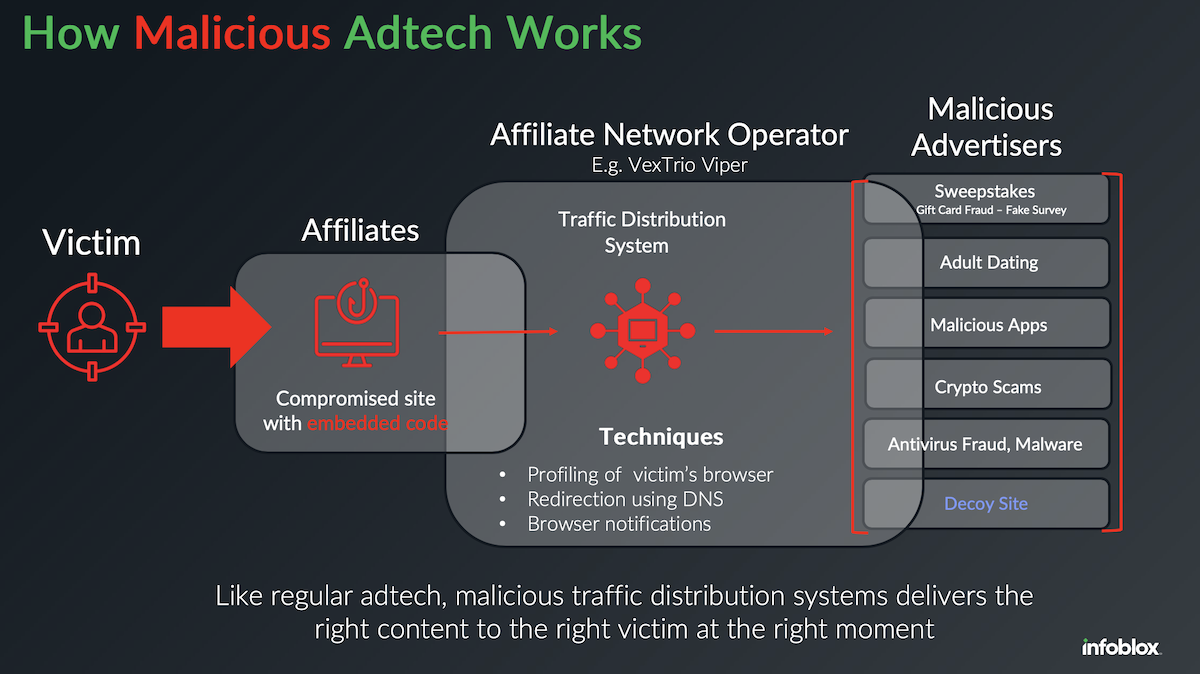
Figure 2: As with legitimate adtech, the malicious variation uses a traffic distribution system to deliver the right content to the right person at the right moment.
Malicious adtech follows the same processes. Publishers, sometimes also called affiliates, offer their compromised websites to an operator, and let the operator redirect victims to a malicious advertiser. Sometimes the operator will compromise websites themselves. At the center of this process is a traffic distribution system (TDS) created by the operator with advanced capabilities, like browser profiling, decoy sites to mislead scanning tools and cloaking services to protect the malicious domains.
Criminal organizations use malicious adtech to bring victims into their illegal schemes. It is a key enabler of fake applications, malware delivery, credential theft and the selling of fraudulent digital products and services, among many other cyberthreats.
Why Is Malicious Adtech So Dangerous?
There are many reasons why malicious adtech is harmful. Here is a brief look at some of the most critical.
Operators Are Hard to Disrupt
The organizations that operate malicious adtech have access to or are capable of creating infrastructure of considerable scale. That infrastructure can include thousands of compromised sites to trick users, a maze of thousands of domains used to redirect victims and high-volume usage of browser push-notification services. In addition, these adtech operations are often organized into multiple entities to keep activities separate to hide their intent —from advertisement creation to fake CAPTCHAs, surveys, scam pages and even malicious downloads. These services combine into a formidable adversary that leverages sophisticated digital tactics to carry out cybercrime while avoiding legal scrutiny. As a result, some of these operators, like VexTrio Viper, have existed for years, have become highly profitable, and their activities may well continue for a long time.
Deception Impacts Organizational Security
Malicious adtech tricks victims into engaging with content they are eager to access, often cleverly mimicking popular brands, so that victims lower their guards and initiate a high-risk action. For instance, once a victim engages by visiting a compromised site, the operator may send a fake CAPTCHA that lures the victim into accepting browser push notifications from a malicious advertiser. These notifications, in turn, may now contain even more fraudulent content, pushing users down a dangerous rabbit hole.
Receiving unwanted push notifications can have substantial implications for users and the organizations they belong to. For example, when a victim interacts with browser notifications mimicking legit applications, they may get tricked into downloading unverified software, sharing personal information or entering their organizational credentials. The tendency for so many of us to spend time on our smartphones during and after work hours makes malicious adtech a serious cybercrime enabler. Personal smart phone push notifications in combination with reconnaissance information allow actors to phish for business credentials or execute multi-factor authentication (MFA) bombing, where victims are flooded with MFA prompts by advertisers or operators. By combining earlier captured credentials with MFA bombing, cybercriminals can gain unauthorized access to enterprise assets resulting in costly data leakages, ransomware attacks and brand damage.
Some Impacts of Malicious Adtech Persist
Malicious adtech is also vexing because once a victim has been drawn in, the distorted information stream created from fake advertisements remains, even after the victim has cleared browser caches or performed other hygiene measures.
Security Controls Become Ineffective
Evasion from security research tools is one of the primary reasons that criminal adtech remains so widespread. By profiling visitors’ browsers, TDSs can cloak advertiser sites from commonly used security scanners and threat research tools. Even more, when the TDS senses that a browser’s settings are more secure, it will route the incoming connection to a benign decoy site to throw threat investigators off the trail.
Cybercriminals, such as VexTrio Viper, use these counterintelligence tactics to reduce their risk of discovery by threat intel teams. By redirecting intelligence-gathering crawling tools to decoy sites, operators interrupt the production of tactical threat intelligence on which automated detection and blocking mechanisms rely. Bottomline, malicious adtech reduces the effectiveness of existing security controls largely because the used TDSs ensure that security vendors do not encounter the pages that ultimately host malicious content or payloads.
Targeting Victims with Custom Content
Instead of executing broad “spray and pray” attacks, TDSs allow adversaries to deliver custom content to the right victim. By executing advanced reconnaissance via social media or other available victim data, actors can craft uniquely created packages in hyper-personalized fashion trusted by the victim. These packages can deliver actor-controlled versions of common IT-admin tools like remote management solutions (RMMs) already used in the environment. This strategy of weaponizing existing IT tools allows actors to carry out malicious activities without being discovered.
The Value of DNS in Detecting Malicious Adtech
Harmful adtech thrives because it deceives victims and evades detection by most security tools. Traditional tools are only effective once a protected device has been exposed to a malicious payload and patient zero’s information is collected. In contrast, data from Domain Name System (DNS) records reveals when and how new malicious infrastructure is configured. Researchers who leverage real-time and historical DNS data combined with innovative data science can identify suspicious or malicious domains before any payload gets delivered, including those used in malicious adtech.
DNS-derived intelligence illuminates the infrastructure behind the threat, including how TDSs work and how they redirect traffic. Unlike any other security methodology, DNS-based security implementations can proactively uncover malicious adtech and block internet-connected endpoints from engaging with it. DNS also does not live within a single IT area. It acts holistically across any internet-connected device whether it is mobile, desktop or cloud instance, enabling security teams to achieve a true proactive security posture. In simple terms, by focusing on the operator infrastructure, DNS-based security tools break the supply chain between malicious advertisers and victims, providing long-term protection instead of focusing on the latest payloads.
Protecting Against Malicious Adtech with DNS Security and Threat Intelligence
Threat actors keep evolving. The rising use of deceptive adtech together with its entrenched infrastructure and evasion techniques pose substantial risks in our increasingly connected digital age. The organizations that operate malicious adtech profit from it and are adept at avoiding legal repercussions, so their activities are likely to continue.
The tactics used in their deceptions are sophisticated enough that even the most security-conscious among us can be tricked into entering a malicious adtech network—and with no easy way out.
Through the enhanced visibility they provide, DNS-based security and threat intelligence are the best measures available today to expose criminal adtech operations and prevent users from connecting to its corrupt domains.
To learn more about Infoblox Threat Intelligence Research visit https://www.infoblox.com/threat-intel/.
Request DNS Security Workshop
https://info.infoblox.com/sec-ensecurityworkshop-20240901-registration.html