Executive Summary
The United States Postal Service (USPS) has taken center stage as this season’s phishing craze. Since July, there has been a remarkable increase in SMS phishing attacks, often called smishing, fueled by the availability of a toolkit on the dark market. The attacks have impacted all forms of text messaging, from iMessage to Android, and all major carriers. The vast majority of these USPS smishing messages come from Chinese threat actors, but not all. One phishing kit gained attention from Krebs On Security, while other reporting from Rescurity focused on the connection between Chinese actors and sophisticated iMessage attacks. In early reporting on this topic, Resecurity detailed a campaign they dubbed Smishing Triad, which leveraged compromised Apple iMessage accounts to spam users with warnings of undeliverable packages. More recently, Domain Tools reported on a campaign they associate with Iranian individuals. In many cases, the actor didn’t even bother to utilize U.S. phone numbers for the sender. None of this reporting has deterred USPS smishers, like the beloved USPS unofficial motto states, “neither snow nor rain nor heat nor gloom of night” seems likely to stop these cybercriminals.

Although widely discussed and reported on in the security industry, discussion of the topic thus far has focused on a particular campaign, threat actor, or the toolkit itself. In our analysis, we looked comprehensively at the over 7,000 USPS-related domains we have detected. This approach lets us understand the landscape of this activity and how different actors’ techniques, tactics, and procedures (TTPs) are observable in DNS. Regardless of the tools threat actors use in the backend, malicious activity of this type requires the creation of infrastructure in the Domain Name System (DNS). The choices they make create fingerprints that can be observed in registration data and DNS queries.
The larger the campaigns, the more infrastructure threat actors need to build, and USPS smishers have gone big. We observe 40-160 new domains registered daily for this purpose; some built with registered domain generation algorithms (RDGAs) and others using lookalike techniques. In the Krebs reporting, for example, a lookalike domain usps[.]informedtrck[.]com is used, while in the Resecurity reporting, the domains follow an RDGA in the .topTLD, e.g., ususuua[.]top and usplve[.]top. Combined with choices the threat actor makes in hosting, registrars, and name servers we can create a DNS fingerprint to isolate and track actors as they create new domains. Our analysis shows at least 16 actors are currently active.
In this article we share some of the major TTPs that separate these actors and include a primer on how DNS can be used to support threat landscape analysis.
Infrastructure and DNS Fingerprints
Like many industry investigations into these campaigns, ours started with analysts receiving SMS messages on their personal phones. When we began researching, we discovered that our existing algorithms and processes had already identified as suspicious many of the domains being used, primarily because they were recently registered and many shared uncommon naming patterns or were lookalikes. Using them as starting points, we searched in our passive DNS (pDNS) data and began finding more domains linked to various USPS phishing campaigns. We can track these participating domains all the way back to June 2022, with a significant increase in activity starting June 2023 (see Figure 1). The majority of the additional domains had also been classified as suspicious by our automated detection algorithms. As we employed human-in-the-loop approaches in our DNS threat hunts, we found that those suspicious domains were, in fact, being used in USPS phishing scams.
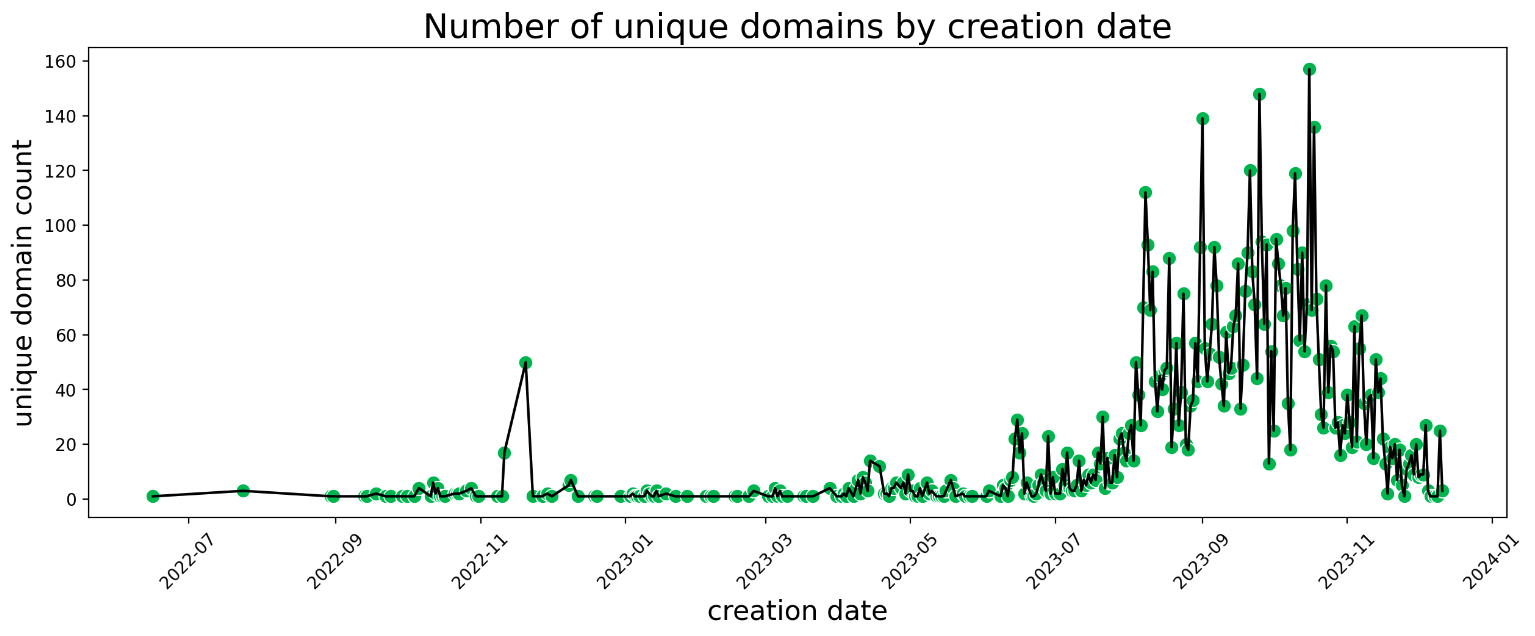
Figure 1: Registrations for domains used in the USPS phishing campaign have increased in the latter half of 2023.
The dramatic increase in USPS phishing domain registration shown in Figure 1 is most likely a result of a phishing toolkit advertised on Telegram. As reported by Resecurity and DomainTools, the toolkit allows anyone to build their own USPS-themed phishing sites, and its relatively low cost and ease of use has very likely contributed to the proliferation of campaigns. The threat actors behind them share a toolkit, but have their own sets of TTPs and infrastructure.
Given the potential variety in infrastructure between the different threat actors, a starting point for DNS hunting can be to create a simple graph linking domains to the IP address(es) to which they resolve (see Figure 2). In this case, it is evident that there is no single pattern in the way domains are hosted. Some actors operate an infrastructure where multiple domains (shown in green) resolve to the same IP address (shown in red). This construction simplifies administration of the domains, but also makes them more vulnerable to blocking. In contrast, other actors design their infrastructure to be more stealthy and resilient, with IP addresses only hosting a single domain, and some domains resolving to multiple, unique IP addresses.
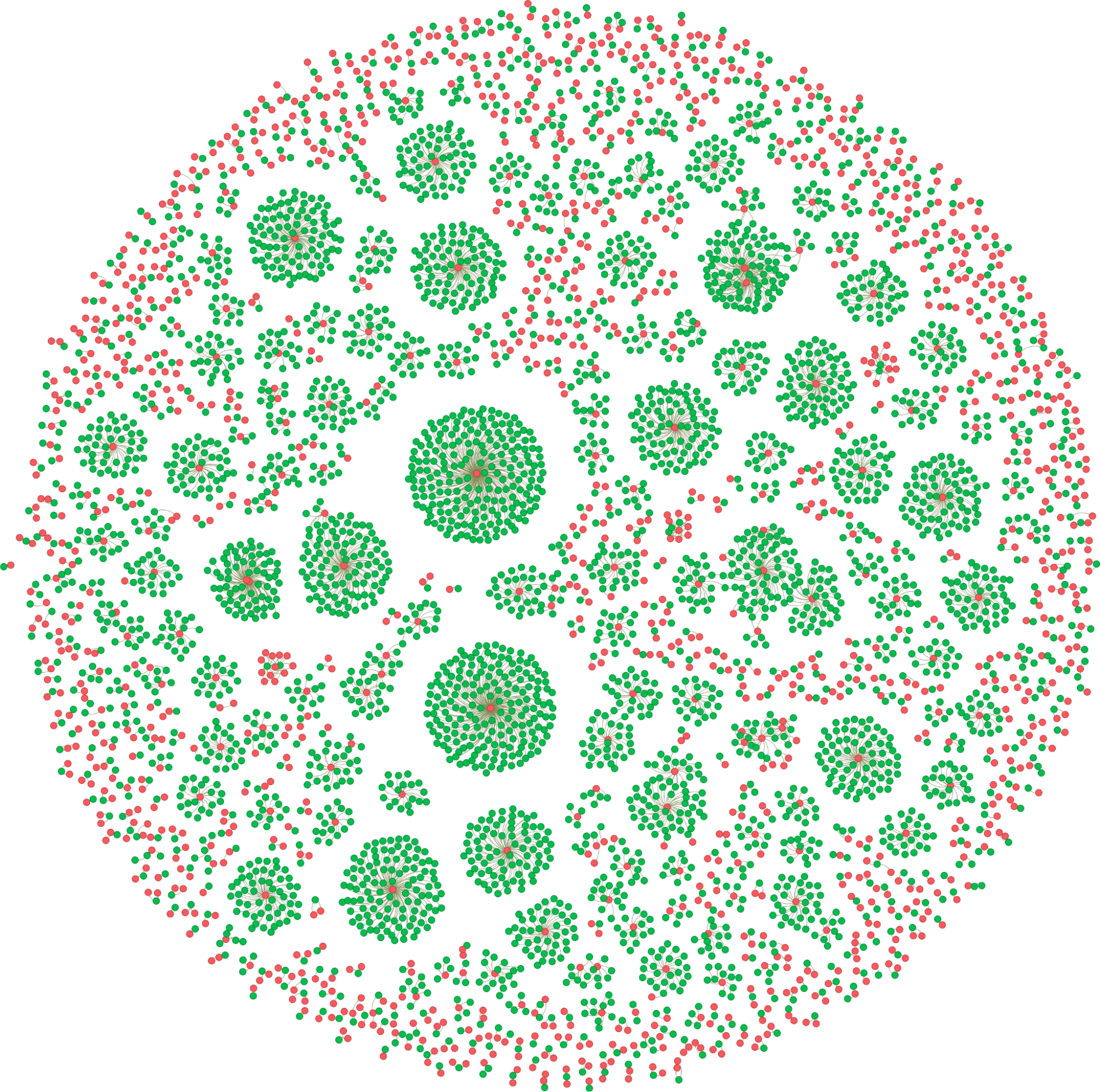
Figure 2: Linking domains (shown in green) to their IP addresses (shown in red) shows multiple large clusters where infrastructure is shared, as well as more distributed infrastructure with IPs resolving only single domains.
Other DNS information, such as the Autonomous System Numbers (ASNs) of the IP addresses, can similarly be used to create a graph that now depicts domains that resolve to adjacent IP addresses within a single ASN. In this case, seemingly independent actor infrastructures appear to merge into a single infrastructure (see Figure 3). Not only do we see links between domains hosted at the same ASN, but there are even instances where domains are observed to resolve to IP addresses hosted by providers in completely different ASNs.
a)
b)
Figures 3a and 3b: Linking domains (shown in green) with the ASN (shown in red) containing their resolved IP address/es shows that infrastructure can span multiple hosting providers over time. Domains that resolved to IPs in different ASNs may have done so at the same time or were moved from one ASN to another at some point. Figure 3a depicts the full set of domains, while Figure 3b depicts a small set of domains that resolved to IPs in different ASNs, effectively acting as a link between two separate clusters of domains.
Shared IP addresses or ASNs aren’t definitive evidence of an actor’s infrastructure, however. As we will later illustrate with a few examples, threat actors often leave fingerprints in DNS with additional data points that provide that evidence. This can be anything from bulk registering domains at the same time with the same registrar, to using the same (fake) registrant information, to leveraging registered domain generation algorithms (RDGAs).
Finding Infrastructure – A Case Study
Since many security professionals are not familiar with DNS threat hunting, we thought it would be instructive to describe how we used various hunting techniques to uncover the infrastructure of a particular actor participating in a USPS phishing campaign. Figure 4 below depicts how our knowledge of this actor’s infrastructure evolved over time and how we were able to track it across multiple IP addresses and ASNs, which frequently correspond to hosting providers.
At the end of September 2023, our automated detection algorithms discovered the lookalike domain uspops[.]top resolving to the IP address 91[.]195[.]240[.]123 and determined that it was being used in a USPS phishing campaign. Up to this point, we hadn’t observed this IP address used by any USPS phishing domains. A few weeks later, we identified another lookalike domain, uspkas[.]top, which resolved to two IP addresses. The first was the same one observed a few weeks earlier and the second was a new IP address, 204[.]44[.]75[.]194, which we hadn’t yet observed in USPS phishing campaigns and was hosted in a completely different ASN (denoted by the blue vertical bar on the left).
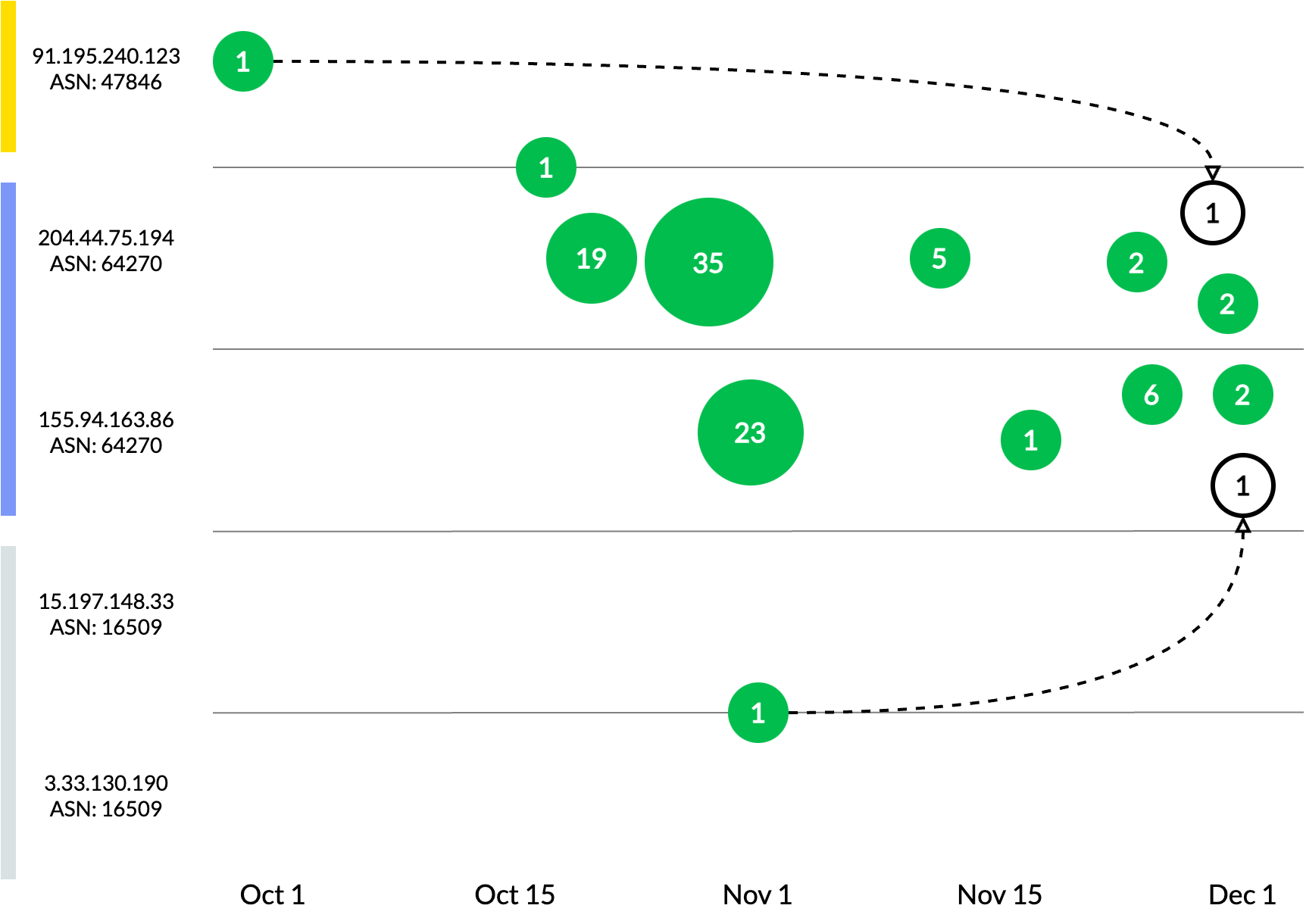
Figure 4: Our understanding of a particular DNS threat actor’s infrastructure changes over time as we observe more data. Nodes in green represent counts of new domains that are known to be used in a USPS phishing campaign. Unfilled nodes represent domains that have been moved to a different host and resolved to a new IP address.
As October progressed, our detection algorithms observed many more domains resolving to the second IP address. Interestingly, these domains were generated using two completely different RDGAs. One used the pattern uspXXX[.]top, like the previous domain observed resolving to that IP address and the other used the pattern uspslose-XXXXXX[.]com, both of which are lookalikes to the official USPS domain usps.com. While the registrar used for both naming patterns was GoDaddy, the actual name of the registrar as reported in WHOIS records differed slightly (i.e., GoDaddy.com vs. GoDaddy.com, LLC), indicating that the domains for each pattern were registered in different ways, such as using a web interface, an API, or using a domain reseller associated with GoDaddy.
Around the end of October, we observed a cluster of domains resolving to a third IP address, 155[.]94[.]163[.]86. Up to this point, we hadn’t seen any USPS phishing domains on this IP, but it did share the same ASN as the second IP address we had observed: 204[.]44[.]75[.]194. At the same time, we identified another new USPS phishing domain that resolved to two new IP addresses on a completely different ASN (denoted by the light gray bar). Again, at this point it appeared to be just another phishing domain and unrelated to the current actor(s).
In November 2023, we detected more domains resolving to the second and third IP addresses that reside on the same ASN. Most importantly though, we saw two previously observed domains resolve to new IP addresses (denoted by the unfilled nodes in Figure 4). One simply reinforced the conclusion that the first two IP addresses were used by the same threat actor, even though they reside on different ASNs. The second, however, suggested that the last two IP addresses that were used by a single domain may be used by the threat actor also using the third IP address observed, 155[.]94[.]163[.]86. At this point, using only IP addresses and ASNs from the domains, we had evidence that these 97 domains were used by one or two different threat actors involved in USPS phishing campaigns. This infrastructure primarily used two IP addresses in a single ASN, but included three more IP addresses across two additional ASNs.
On its own, this evidence can appear to be inconclusive. Those IP addresses could be used to host thousands of unrelated domains and larger ASNs can administer tens of thousands of IP addresses. In this situation, pDNS can be used to provide additional insights. Using historical pDNS data, we determined that the two IP addresses used by all the domains, 204[.]44[.]75[.]194 and 155[.]94[.]163[.]86, hosted 64 and 33 domains, respectively, during this time period. These account for the 97 domains we observed participating in USPS phishing campaigns, providing strong evidence that these IP addresses were in fact related.
Based on just this evidence, we still don’t know if it is a single DNS threat actor, or two different actors on adjacent IP addresses. Given that this level of attribution would be sufficient for tracking the infrastructure and blocking new domains, we could stop at this point and not investigate any further the possibility that it is a single DNS threat actor. However, while analyzing the domains for further insights, our researchers realized that many domains from both IP addresses shared the same custom SSL certificate. This final piece of information gave us the confidence to group the infrastructure under a single DNS threat actor.
This isn’t the end of the story, though. We continue to use new information to pivot and find additional domains and links identifying infrastructure. As we were preparing the data for this article, researchers noticed that the registrant organization for two of the domains in this cluster wasn’t anonymized and used the name “Sean M Hemming.” Using this small bit of information, they were able to find 194 new domains, which is a DNS hunting story for another time.
Infrastructure Variations
Although the registrant information for the majority of the domains is private, like the ones in the example above, we were able to find a number of domains that had visible information. Table 1 lists the number of domains associated with the more common registrant organizations that we found. It is evident that none of these are legitimate, but they can still provide valuable insights and are often the source for further pivots. A common pattern was the repeated use of two or three letters.
| Registrant Organization | Count |
|---|---|
| PrivacyGuardian.org llc | 2095 |
| REDACTED FOR PRIVACY | 720 |
| adadasdadasdad | 529 |
| xcxcx | 41 |
| xczx | 29 |
| gjhjhjhj | 12 |
| lucky | 92 |
| luckyleo | 34 |
| Table 1: Commonly observed registrant organizations in USPS phishing campaigns. | |
In addition to the choice of what contact information to use during registration, a threat actor’s choice of domain naming or, as is the case of many of the observed domains, the choice of pattern for an RDGA can be used to identify domains that were previously thought to be unrelated. Once our autonomous detection algorithms detected suspicious domains, we analyzed them to determine if there was a discernable pattern. If there was, we then used that pattern to augment both our automated and human-in-the-loop hunting process to find related domains. We listed some of the observed patterns and sample domains below in Table 2.
| Pattern | Example Domains |
|---|---|
| us[a-z]+.top | ususzzo[.]top ususuua[.]top usqxsz[.]top |
| usps?[a-z]+.<tld> | uspsmg[.]com uspszm[.]com uspsall[.]top |
| usps.com.usp[a-z]+.shop | usps[.]com[.]usprc[.]shop usps[.]com[.]usprl[.]shop |
| usp[a-z]{2,3}-delivery.com | uspisp-delivery[.]com uspos-delivery[.]com usposp-delivery[.]com usposz-delivery[.]com |
| uspslose-[a-z]{6}.com | uspslose-gsybya[.]com uspslose-jxcskk[.]com uspslose-usausps[.]com |
| arrive[a-z]+.top | arrivew[.]top arrivewe[.]top arrivewt[.]top |
| Table 2: Most of the domains observed in USPS phishing campaigns were created using RDGAs. Some of the more common patterns are listed, along with some of the observed domains they created. | |
The choice of a domain’s TLD can also provide insights into a DNS threat actor and aid in tracking their infrastructure. Table 3 below lists the top five TLDs used by the domains involved in USPS phishing campaigns, with a few known to have very risky reputations. Unsurprisingly, and with a hint of irony, the TLD .top was at the top of the list and is used by 60% of the domains. It is a highly abused TLD and we have calculated that it has a very risky reputation. The .com TLD is the next most frequently used, with a sharp drop in frequency after that.
| TLD | Count | Percentage | TLD Risk |
|---|---|---|---|
| .top | 4,369 | 60% | High |
| .com | 1,436 | 20% | Moderate |
| .shop | 397 | 5% | High |
| .us | 212 | 3% | Moderate |
| .xyz | 86 | 1% | Moderate |
| Table 3: The top five TLDs of domains observed participating in USPS phishing campaigns. | |||
Attack Variations
Since there are a variety of DNS threat actors participating in these USPS phishing campaigns, we see variation in the lure messages and in the domains used to phish personal information. The messages are usually some version of the one shown in Figure 5 below. The majority of domains used in these messages are lookalikes to the official USPS site, frequently making use of the acronym. We have also observed that many threat actors have chosen to not use USPS in the domain name itself, and instead use it in a subdomain (e.g., usps[.]amtion[.]top), which may be an attempt to evade detection from algorithms that simply look at the second-level domain name in a WHOIS record.
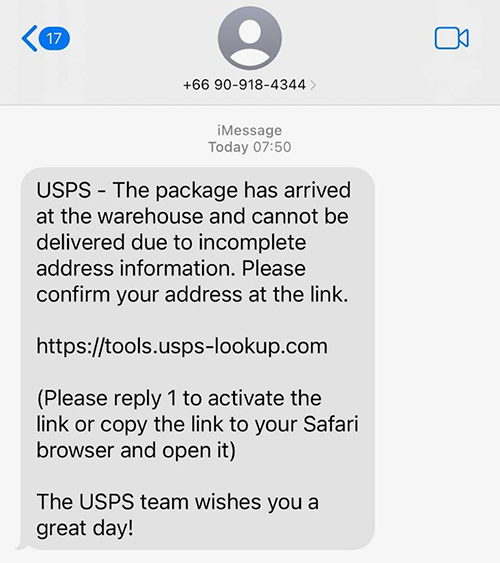
Figure 5. The website used in these phishing campaigns is frequently a lookalike for a legitimate USPS domain such as the one shown here.
When a victim clicks on the link, they are generally taken to a site like the one shown here in Figure 6 below.
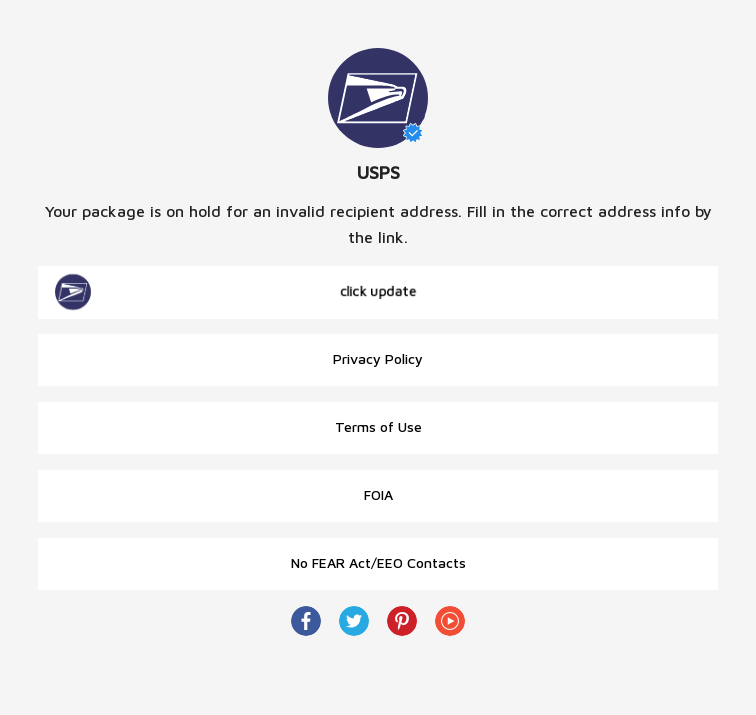
Figure 6. The majority of sites we have observed appear to use the landing page shown. Most of the links are to the legitimate USPS website, except for the “click update” link, which takes the victim to the website with the phishing content.
Nearly all of the links are to the official USPS website; the exception being the “check update” button at the top of the list, which takes victims to the phishing page. We have noticed that there are some differences in the sites, depending on the choices of the particular threat actor operating the domains. In many cases, the domain checks the user’s browser UserAgent. If the UserAgent does not correspond to a mobile browser, the browser is redirected to the official USPS website (Figure 7). This is most likely done in an attempt to avoid detection by researchers or search engines. Redirection is done using an HTTP 302 code, indicating that the redirection is temporary and search engines should not update their links, thus enabling other victims to still reach the phishing site.
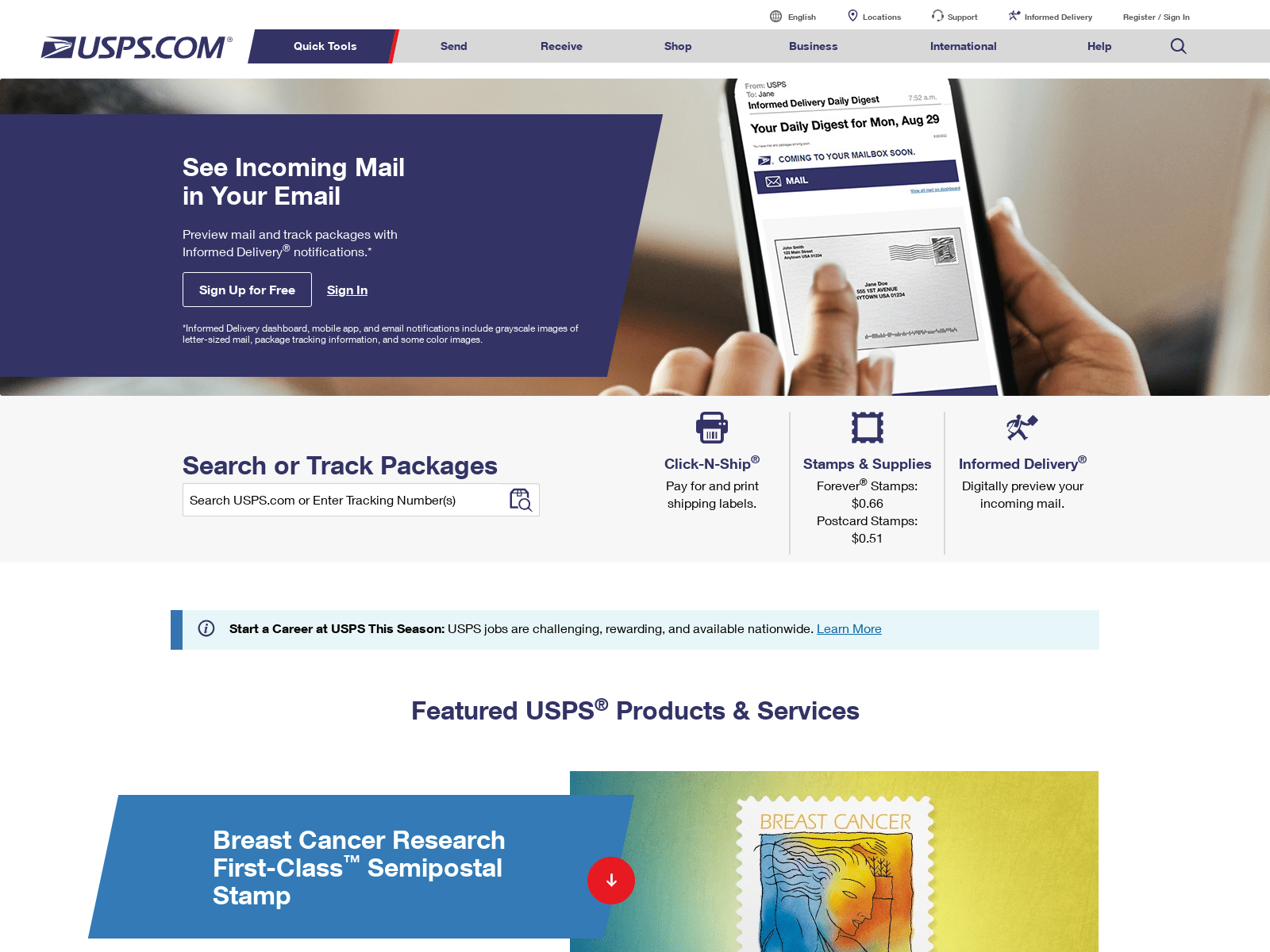
Figure 7. Some domains selectively redirect requests to the official USPS website, shown here, based on the UserAgent of the user’s browser.
In rare cases, the domains in the phishing messages take the victim directly to a page with a more informative lure like the one shown in Figure 8 below. We have even found instances wherein the page uses the physical location of the victim’s IP address to customize the delivery area in an added attempt to appear legitimate. Eventually, the victim is taken to a series of pages that request credit card and other personal information.
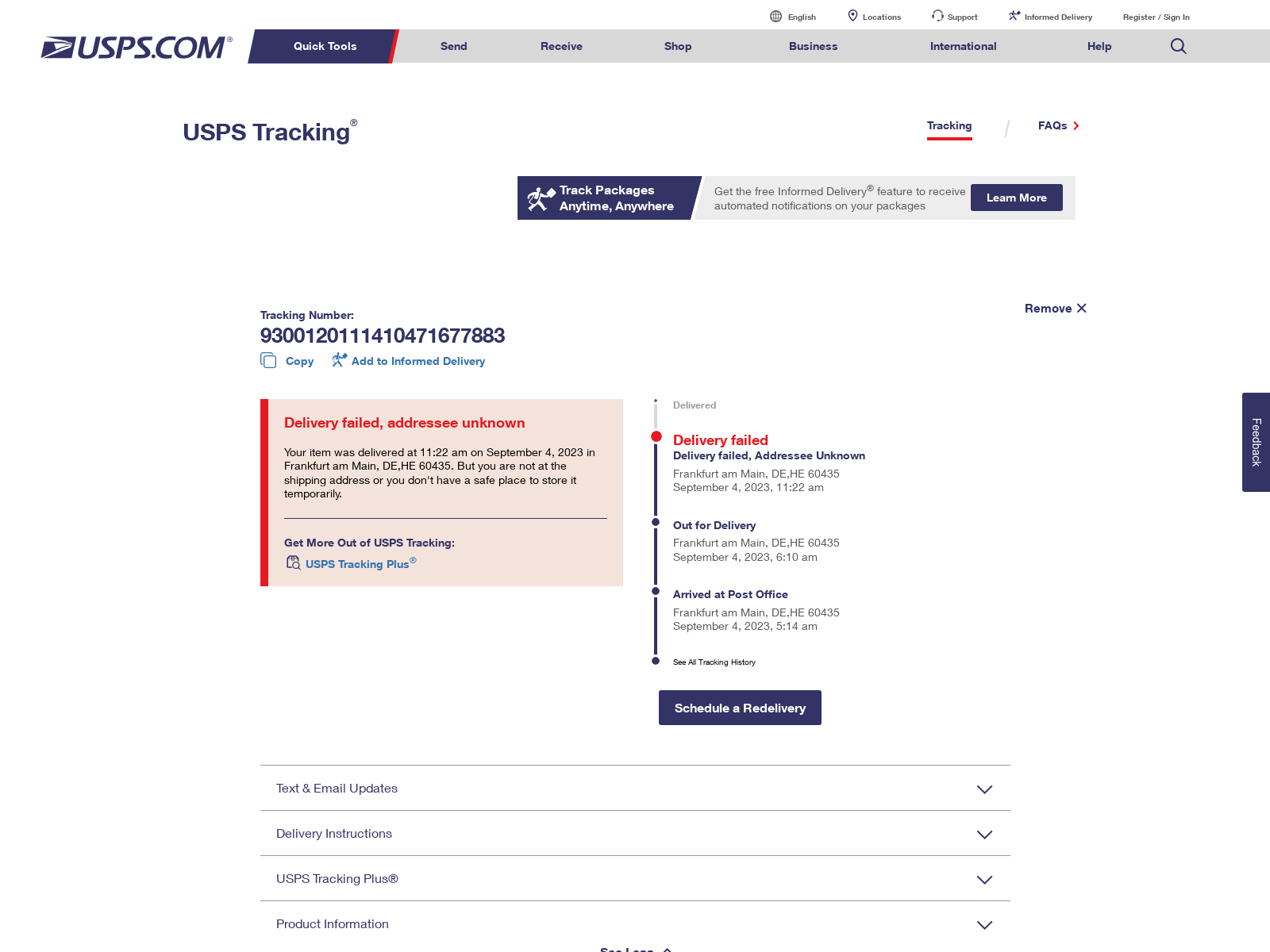
Figure 8. A fake USPS error page is displayed to victims to add legitimacy to the phishing website. In some cases, the physical location of the victim’s IP address is used to customize the locations shown on the page.
Conclusions
Although phishing actors are utilizing a variety of TTPs, we are able to detect, track, and block the actors through DNS. We have found over 7,000 of their domains, all of which are either generated by an RDGA or are a lookalike. Through the use of DNS threat actor-centric algorithms, we saw a more comprehensive picture of the threat landscape. For comparison, the Resecurity article identified 26 domains and specified a single hosting and registrar; however, at the time of their publication, we had already correlated nearly 900 domains controlled by a single DNS threat actor and leveraging multiple registrars and hosting providers.
Infoblox customers who have BloxOne Threat Defense are protected against all of the known USPS phishing domains, including new domains as they are detected. The table below provides a selection of the indicators of activity used by the DNS threat actor in the case study discussed above. Our GitHub repository contains these indicators and all the others we are currently tracking as participating in a USPS campaign.
| Indicator | Type of Indicator |
|---|---|
| uspjfs[.]top uspjts[.]top uspkgds[.]top uspklas[.]top uspkubs[.]top uspkyhs[.]top uspslose-sdew[.]com |
Domains resolving to 155[.]94[.]163[.]86 |
| uspkxs[.]top uspkzs[.]top usplsd[.]top uspors[.]top uspsloe-jutf[.]com uspslose-gschtsy[.]com uspslose-gsxujsy[.]com |
Domains resolving to 204[.]44[.]75[.]194 |
| 204[.]44[.]75[.]194 155[.]94[.]163[.]86 |
IP addresses operated by QuadraNet Enterprises, LLC (ASN 64270) |








