DNS for Early Threat Detection – Lumma C2
Only a few years ago, threat intelligence data on malicious domains provided a window of protection during which malware was still actively being spread. Protection could be afforded to many organizations by blocking the malicious domains that were published. Over time, threat actor techniques have evolved to the point where much of the potential damage and compromise is done long before any of the malicious domains are identified and propagated through open source intelligence (OSINT) (and most commercially available threat intel feeds). Threat actors are leveraging speed of execution to gain advantage and defenders need to respond accordingly.
Our DNS Early Detection Program highlights and showcases the findings of Infoblox proprietary techniques that provide the earliest possible identification of potentially malicious domains. The program publishes our recent analysis of public OSINT disclosures of malicious domains compared against our early identification of these domains as suspicious.
The NEED FOR SPEED is real. Infoblox identification of these suspicious domains makes them available for blocking weeks, even months, earlier than the domains published in many industry-wide malicious threat intel feeds.
| The data shows that Infoblox suspicious domain threat intel feeds identified 37 Lumma malicious domains, on average, 62.1 days sooner than availability in OSINT. Infoblox’s suspicious domain data can help our customers avoid a potentially devastating data breach. |
Lumma C2 Stealer (Lumma)
Lumma is an information stealer that has been attributed to the threat actor “Shamel” operating under the alias of Lumma. Lumma is available for purchase on Russian speaking Dark web forums as malware-as-a-service (MaaS). MaaS access to Lumma provides even the most inexperienced threat actors with an inexpensive way to gain access to relatively sophisticated and dangerous tools.
The nature of how Lumma is packaged and presented as almost any standard commercial product might be at times appears surreal. Lumma is sold in various “plans” that include log upload and log analysis. Then optionally, depending on the plan selected, the user may also license the use of special log and traffic analysis tools, and, in the high end “Corporate” version, a feature which includes the ability to bypass many types of proactive defensive protections. The pricing for these plans runs between $250 to $1,000 U.S.
The Lumma payload is typically distributed via spear phishing campaigns with malicious attachments, and malvertising campaigns with embedded malicious links. Lumma steals system data and sensitive information from infected machines, including browser data,1 stored credentials and cryptocurrency data,2 as well as two-factor authentication browser extensions.3
Analysis and Methodology
In late September, 2023, data on 85 Lumma domains was published in OSINT. Analysis of these malicious domains was done by the Infoblox team to determine if they were identified earlier by our suspicious domain feeds.
Each malicious domain identified in OSINT was researched in the Infoblox Dossier portal by our team. We reviewed our timeline feature to extract the earliest dates associated with Infoblox suspicious designation. We also extracted the WHOIS information for additional context.
The conclusions of our analysis were definitive:
- 37 Lumma domains were identified as suspicious by Infoblox an average of 62.1 days prior to the availability of the OSINT designation as malicious.
- 43% of these suspicious domains were blocked between 72 and 90 days earlier than the OSINT designation as malicious.
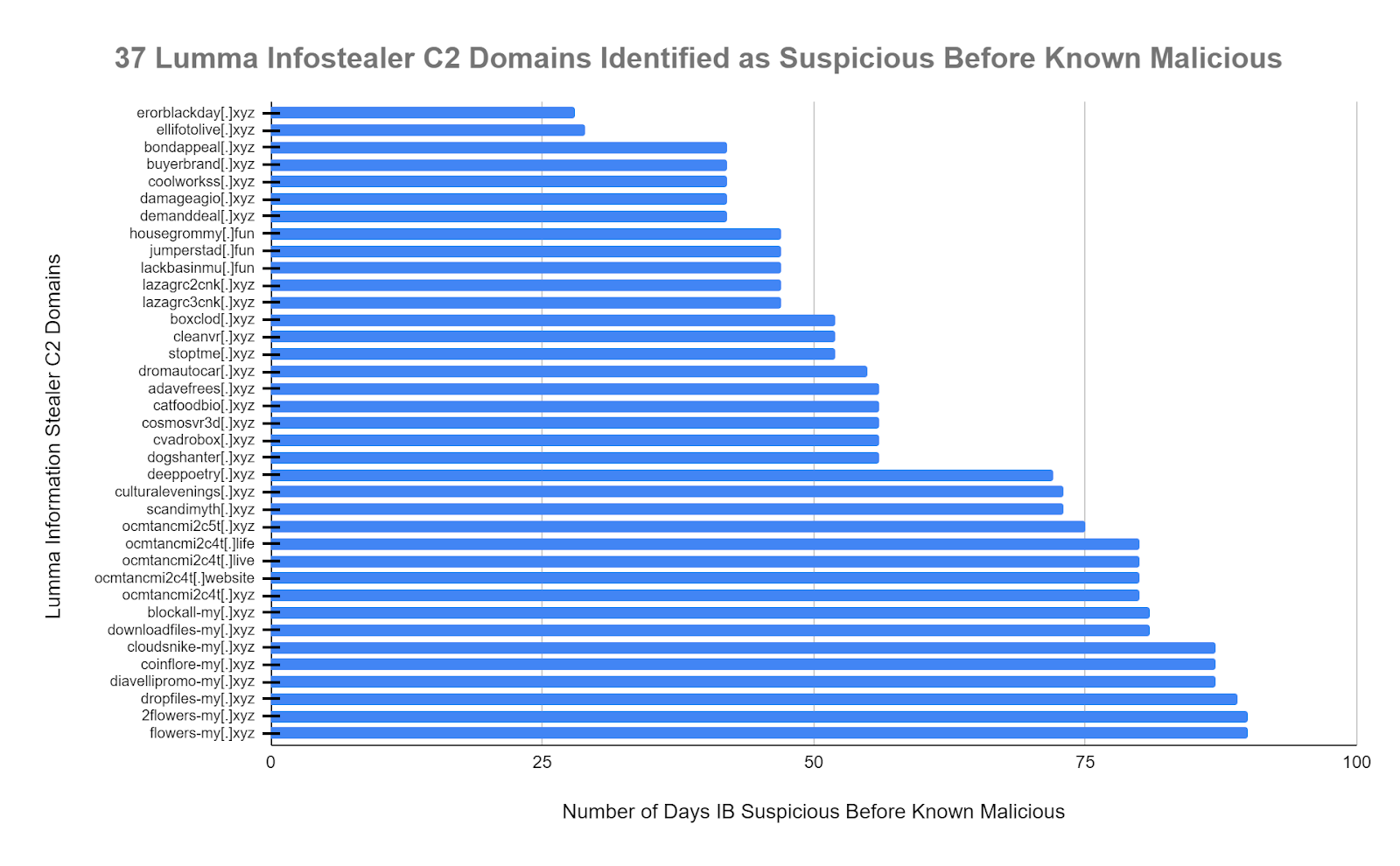
It is often the case that OSINT publication dates may sometimes be unclear or lack precision. The dates of published articles by reputable 3rd parties may not always accurately reflect the OSINT availability of each individual domain.
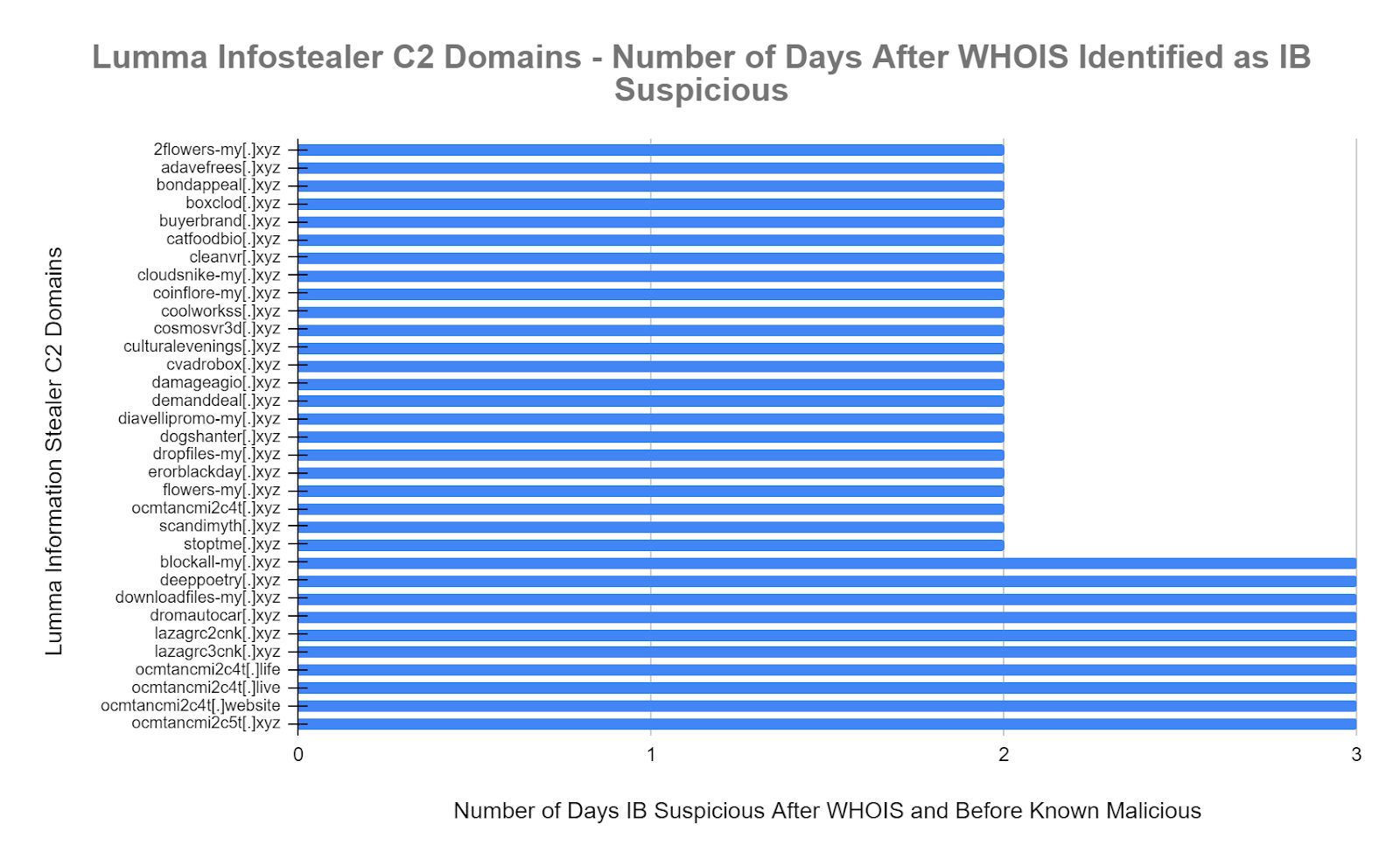
To provide context on the performance of our suspicious threat intel feeds we extracted WHOIS dates and found that 33 of the Lumma C2 infostealer domains were blocked as suspicious within an average of 2.5 days (60 hours) after the WHOIS domain registration date. The WHOIS dates are always precise and provide another perspective on the high value of suspicious threat intel feed content.
Risk Reduction and Return on Investment
| Infoblox finds potentially dangerous DNS domains faster. Infoblox suspicious domain data can reduce risk and increase the return on investment for your threat intelligence program. |
The use of our proprietary technology to identify suspicious domains is a major “Shift Left” to normal processes used across the industry to develop and leverage threat intelligence information. Infoblox suspicious domain data helps security operations teams gain the timely information they need to better address and defeat the barrage of new threats before they can cause harm.
For Additional Information
The Infoblox Threat Intelligence Group provides fast access to accurate, contextual threat alerts and reports sourced from our own real-time research teams. Infoblox allows your team to leverage the high value of suspicious domain threat intelligence while ensuring unified security policy across your entire security infrastructure. Infoblox threat data minimizes false positives, so you can be confident in what you are blocking.
To learn more about suspicious domains and DNS early detection: https://www.infoblox.com/threat-intel/
To learn more about BloxOne Threat Defense:
https://www.infoblox.com/products/bloxone-threat-defense/
To learn more about Advanced DNS Protection:
https://www.infoblox.com/products/advanced-dns-protection/
To learn more about the National Security Agency (NSA) and Cybersecurity & Infrastructure Security Agency (CISA) guidance on Protective DNS:
https://media.defense.gov/2021/Mar/03/2002593055/-1/-1/0/CSI_PROTECTIVE%20DNS_UOO117652-21.PDF
Endnotes
- Targeted browsers include: Chrome, Chromium, Edge, Kometa, Vivaldi, Brave-Browser, Opera Stable, Opera GX Stable, Opera Neon, and Mozilla Firefox.
- Targeted crypto wallet extensions include: Metamask, BitApp, Sollet, Nash Extension, TronLink, iWit, Auro, Hycon Lite Client, Ronnin Wallet, Wombat, Polymesh, ZilPay, Binance Chain Wallet, MEW CX, ICONex, Coin98, Yoroi, Guild, Nabox, Cyano, Nifty, Saturn, KHC, Byone, Math, NeoLine, Temple, OneKey, Coinbase, Clove, TezBox, Leaf, Guarda, Liquality, DAppPlay, EQUAL, Terra Station, BitClip, Jaxx Liberty, Kepin, and Steem Keychain.
- Targeted two-factor authentication (WFA) extensions include: Authenticator, Authy, EOS Authenticator, GAuth Authenticator, and Trezor Password Manager.











