Malicious traffic distribution systems (TDSs) have flown under the radar of most cybersecurity organizations for years: they have been largely ignored and thought of as simply advertising networks or “adware”, a term associated with nuisances and not threats. Cybercriminals have used this to their advantage and have built massive networks of domains that direct victims to scams, phishing, and malware. The size and complexity of these TDSs are hidden behind a constantly changing labyrinth of domains and defense measures that frustrate even the most experienced security researchers. A TDS can be difficult to recognize because many domains are just redirects and because it does not deliver malicious content to every user. Fortunately, information found in DNS can be used to pull back the curtain and shine a light on these networks. Moreover, DNS offers the most powerful control point to prevent compromise that occurs from malicious content delivered via a TDS.

What are Traffic Distribution Systems (TDSs)?
If you have clicked on a link in an email or on an ad in social, you have probably encountered a traffic distribution system, also known as a traffic delivery system. You may not realize it, but that link didn’t take you directly to the web page you wanted to visit. Somewhere along the path to your desired destination, a server gathered information about you and the link you originally clicked, before the server sent you on your way. It collected this data to provide to your favorite store, whose marketing department wants to know which of their marketing campaigns works best. Should they continue to send emails to potential customers or just focus on those social media ads?
TDSs were first developed to help marketers manage incoming traffic from various sources. They needed a systematic way of tracking how visitors were getting to their site and TDSs provide that capability. TDSs can even use information they gather about their visitors to direct them to different content. Are people that click on email links about sales or discounts more cost conscious? If so, marketers will direct them to a page that emphasizes affordability, while other visitors are sent to a page that emphasizes ease of use…and so on.
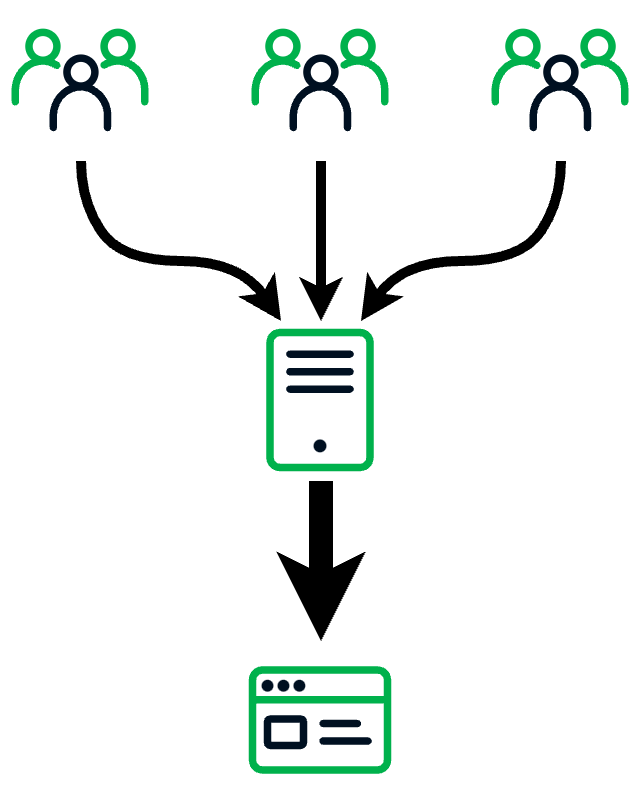
One of the main purposes for which marketers use TDSs is to ascertain and keep track of who, or what, was behind each “click.” A TDS can track which options for directing traffic to their site (social media ads, emails, third-party affiliates that refer their audiences, etc.) are most effective (Figure 1). This tracking data is used both to inform future decisions and determine how much these affiliates should be compensated. Since affiliates are known to sometimes use bots to artificially increase their referrals, TDSs can also be used to determine who, or what, is behind the click.
|
| Figure 1 – Traffic distribution systems (TDSs) are often used to track the source of incoming traffic |
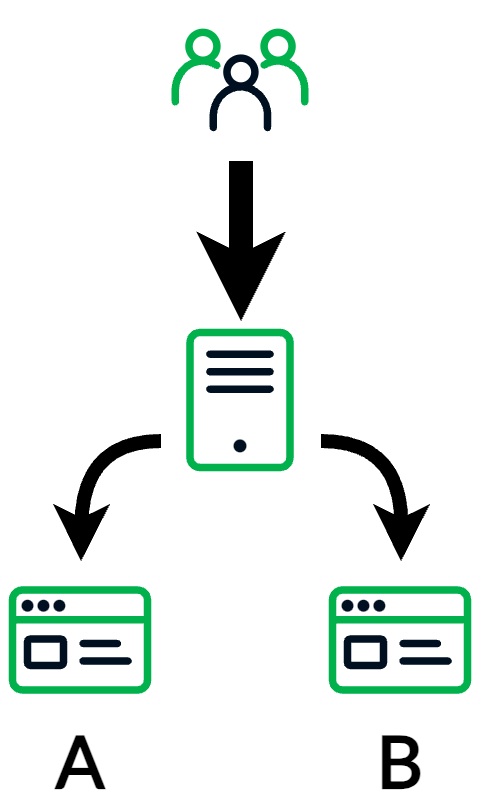
Marketers also frequently use TDSs when they perform A/B testing (Figure 2). For example, when a marketer wants to test a new web design, they could use a TDS to send half their visitors to the new version of the site and the other half to the current version. Marketers can then analyze how visitor behavior is different between the two versions, thereby evaluating the new design. If it works well, they can then use the TDS to just send all the traffic to the new version.
|
| Figure 2 – TDSs can be used to evaluate the performance of different content on a website, known as A/B testing |
While these features have made TDSs an essential tool for marketers, they have proven to be equally effective for cybercriminals.
Malicious TDSs
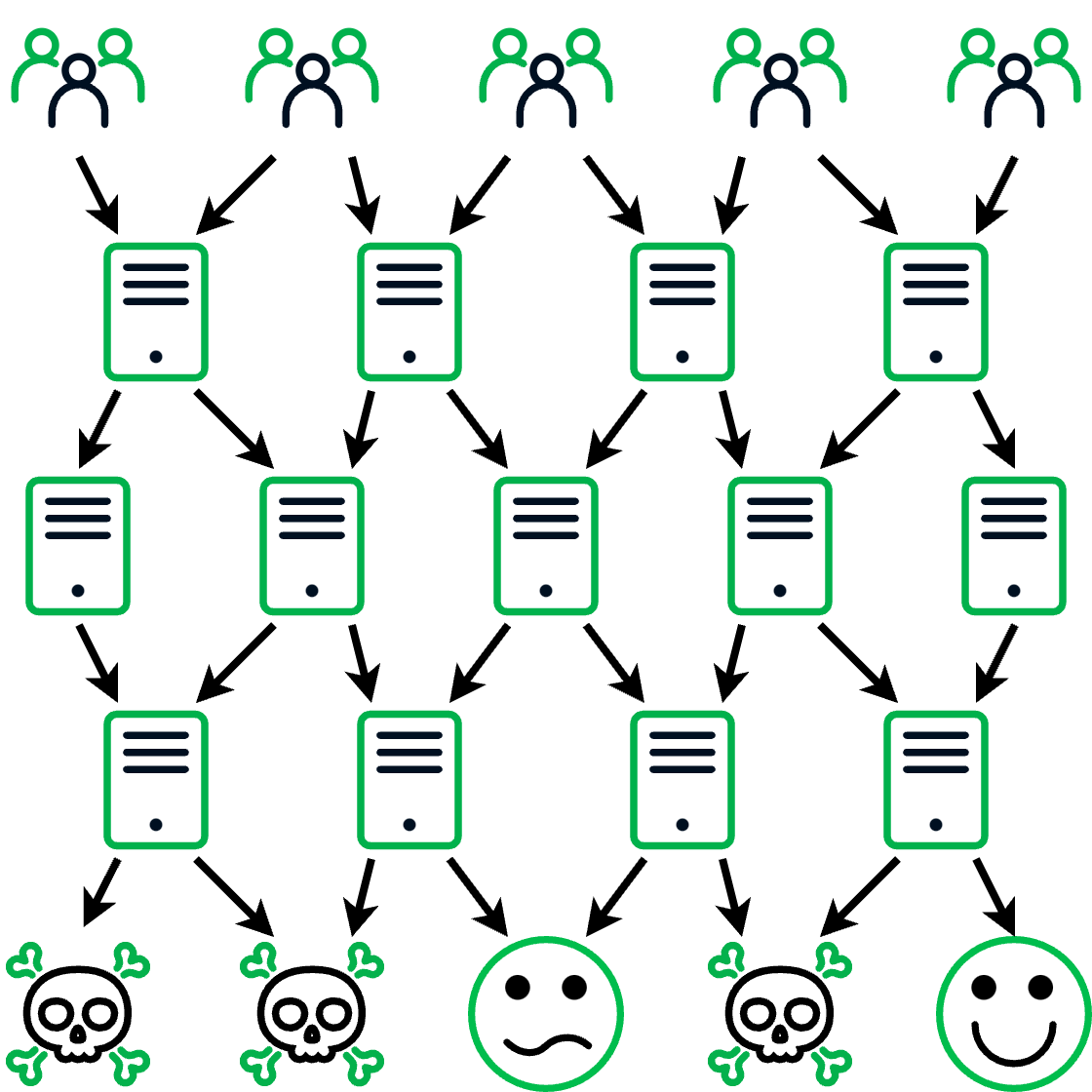
A TDS offers an infrastructure that is highly resistant and adaptive, and can withstand standard security defense approaches. Victims get pulled into a TDS in a variety of ways: from clicking on a fake search result to being hijacked by a malicious ad. Regardless of how they got there, once they are in, they are merely along for the ride. They have as much control as a pinball in a pinball machine. Most of the time, victims are sent to a malicious site that specifically targets visitors meeting certain criteria. Other times, they are simply sent to a site that generates ad revenue. In some cases, potential victims are kicked out of the TDS entirely and sent to legitimate sites like Google. Not only does this variety of destinations reduce the perceived risk of these “advertising networks,” but it also hinders security researchers investigating the TDS (see Figure 3).
|
| Figure 3 – Threat actors have built massive TDSs that direct victims through a maze of domains delivering content that is malicious, that provides ad revenue, or that sometimes is legitimate and set to throw off researchers |
Cybercriminals that operate TDSs don’t always use them just for their own campaigns. They frequently act as a service provider and provide access to the network, and its victims, to affiliates that are operating their own campaigns. All for a fee, of course. In marketing, TDSs are specifically designed to gather as much information about the visitor as possible. In the world of cybercrime, threat actors that operate large TDS networks offer their affiliates the ability to target a very specific set of victims. For example, an affiliate could use a TDS to target victims using a specific Safari browser version on an iPhone with a phishing campaign that looks just like native system notifications. Another affiliate could target Windows users that are using an outdated browser version with a malware exploit tailored to a specific vulnerability found on that version. One of the most important benefits for threat actors, however, is the ability to identify bots or security researchers and direct them out of the network, making traditional methods for mapping the infrastructure a challenge.
Varieties of TDSs
Although TDSs often use HTTP redirects, there are other ways to direct traffic, enabling cybercriminals to hide what they are doing from victims and researchers alike. To date, we have observed three different types of TDS implementations.
HTTP-based
In HTTP-based systems, the web server receives the request, analyzes the client making the request, and then redirects the client to the next destination using an HTTP redirect code such as 301 or 302. This traditional version may not be as stealthy as the other versions of TDSs, but it does give the owner the opportunity to get as much information from the client as possible. It has full access to data in the HTTP request itself and can even use JavaScript to get information about the client machine. This information is necessary for cybercriminals who want to direct victims to specific destinations. For example, a website hosting Microsoft Windows malware won’t be effective if the visitor is using the Safari browser on their iPhone. At Infoblox, we use the designation Viper for certain threat actors that use this type of TDS. Vigorish Viper and Vextrio Viper are two recent examples.
Link Shortener
While link shorteners have legitimate uses, cybercriminals use them to hide the intended destinations of links. Some cybercriminals abuse well-known link shortening services to give their links the appearance of legitimacy. We have also observed that some cybercriminals operate custom systems that create shortened links for large TDSs. Since the links are short, less victim information can be embedded in the link than with HTTP-based TDSs. However, the benefit for cybercriminals is that internet users are accustomed to seeing shortened links and may be more likely to click on them. At Infoblox, we use the designation Puma for threat actors that use this type of TDS. Prolific Puma is a recent example.
DNS CNAME-based
The last type of TDS we will discuss here directs traffic using DNS CNAME records. Since this redirection happens at the DNS level, it does a far better job of hiding from victims and researchers than the previous types of TDSs, which operate at the level of HTTP requests. The downside of this approach, however, is that it doesn’t provide access to as much information about the victim. The threat actor only has access to the victim’s IP address from the DNS request. Granted, things like the victim’s location can be inferred from the IP address, but it isn’t close to the information that can be obtained from JavaScript running on the victim’s machine. At Infoblox, we use the designation Seahorse to identify threat actors that use this type of TDS. Savvy Seahorse is a recent example.
Stopping a Malicious TDS
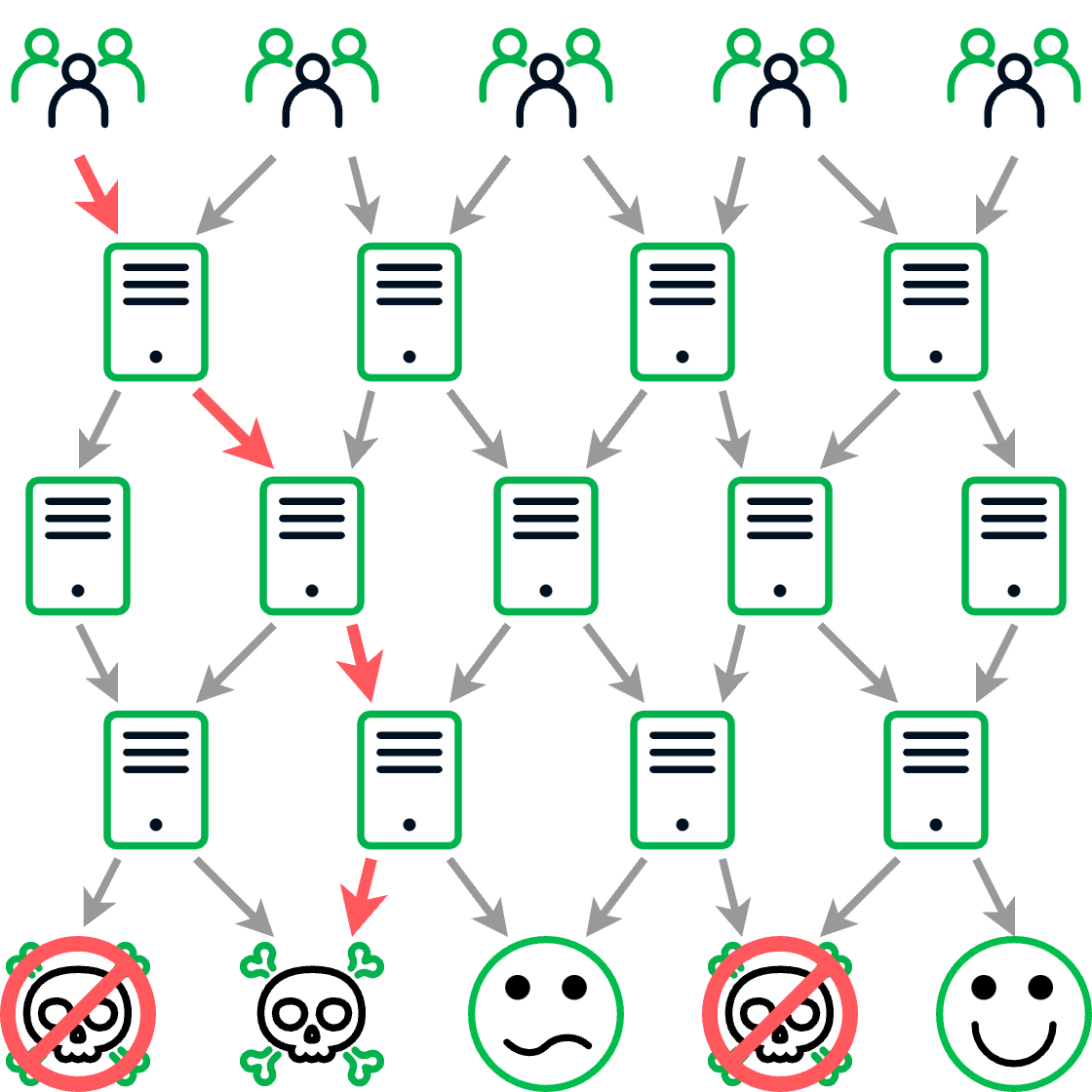
Given the obfuscation and apparent randomness inherent to malicious TDSs, the traditional approach of simply blocking a domain with crypto scam content or a malware download isn’t broadly effective. Threat actors can easily update their TDS to direct traffic to one of the other hundred domains with the same content or change the content to evade scanning solutions (see Figure 4). Furthermore, since the designers of malicious TDSs aggressively work to prevent researchers and analysts from interacting with them, the techniques normally used to map such networks are often unsuccessful.
|
| Figure 4 – Blocking individual destination domains with malicious content isn’t that effective in protecting against a TDS since the operator can simply direct the victim along a different path to a different destination domain |
Fortunately, DNS offers researchers the ability to sidestep many of these attempts to hinder the discovery and tracking of large TDS networks. DNS traffic can be used to identify the sequence of requests made as a victim is directed through the TDS and to find common configurations that aren’t visible in normal web traffic. All of this can be combined to create a picture of the TDS infrastructure as a whole. Given that many of these TDSs use tens of thousands of domains (some more than 100,000), most researchers are bound to miss portions of the infrastructure. However, if enough of the infrastructure is blocked, then the TDS will cease to be effective (see Figure 5). Furthermore, with an understanding of a TDS’s infrastructure, a researcher can see the threat actor’s attempts to rebuild and block new domains before they pose a threat.
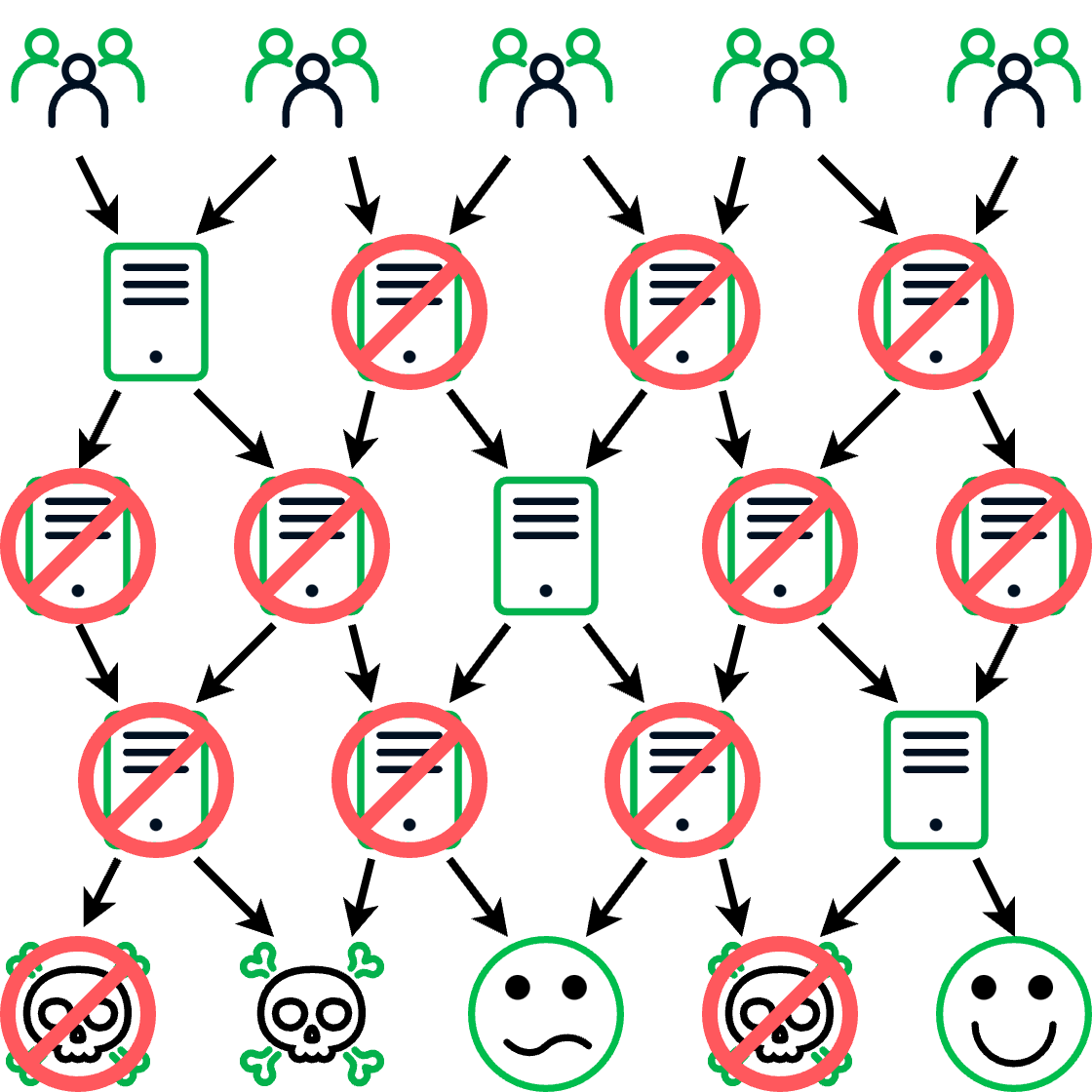
|
| Figure 5 – If enough of a TDS’s infrastructure is blocked, there aren’t enough domains left to direct traffic to the desired destinations |
Wrap-up
By collectively overlooking malicious TDSs over the years, the cybersecurity community has allowed them to flourish. With more visibility on the risks that malicious TDSs pose, the community has started to look for effective ways to protect against them. Infoblox Threat Intel’s expertise in DNS has proven to be essential in making sense of the massive networks of domains and redirects that threat actors have built. These TDSs comprise some of the largest sets of cybercrime infrastructure yet observed.









