We recently received a tip from a customer that their institution was under recurring attacks that targeted their student single sign-on (SSO) portal. The threat actor leveraged Evilginx (likely version 3.0), an open source, advanced phishing adversary-in-the-middle (AITM, aka MITM) framework designed to steal login credentials and session cookies. Evilginx is widely used by cybercriminals to undermine multi-factor authentication (MFA) security, and this actor has used it to target at least 18 universities and educational institutions across the United States since April 2025. The campaigns were delivered through email and the phishing domains used subdomains that mimicked the legitimate SSO sites. Figure 1 shows a timeline of attack volumes, based on DNS, against the schools.
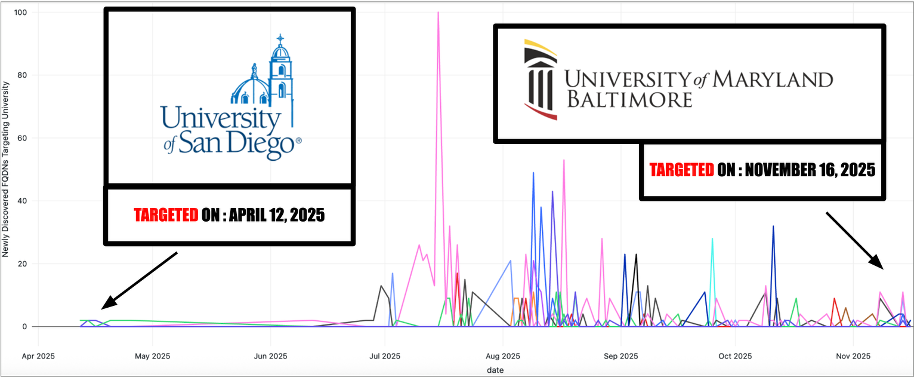
Figure 1. A timeline of SSO phishing attacks against higher educational institutions by the actor between April 12-Nov 16, 2025. Each color represents a different university.
Evilginx employs multiple evasion techniques, making it difficult to detect and analyze using common methods. For example, the software resists security scanners. Additionally, the actor running the university campaigns configured their toolkit to use short-lived phishing URLs and hide its servers behind Cloudflare proxies. Combined with Evilginx’s reverse-proxy characteristics, these tactics challenge traditional detection methods such as URL analysis and front-end code inspection (HTML, CSS, JavaScript). Nevertheless, the campaigns had consistent DNS patterns that allowed us to craft a signature for effective, continuous tracking using initial web server fingerprinting and extensive DNS-based analysis.
We uncovered nearly 70 domains related to these attacks and created tracking mechanisms to identify future activity. This work demonstrates that DNS can uncover malicious infrastructure that is otherwise very hard to detect, and the results can be used to pre-emptively protect organizations from compromise, including data breaches. It also highlights the benefit of collaboration: by sharing their story, our customer has helped protect many others.
Campaigns
In the campaigns we analyzed, students were targeted via personalized emails that contained TinyURL links. These short links redirected to phishing URLs dynamically generated from Evilginx phishlets—configuration files that define how the proxy interacts between the victim’s device and the legitimate site. Each phishing URL used a subdomain that impersonated the target brand and a URI with eight random alphabetic characters (case-insensitive).
The URLs expired within 24 hours, a tactic to limit exposure and evade detection. When victims accessed the phishing URL, Evilginx proxied the legitimate login flows in real time, making traffic appear normal and bypassing MFA. Figure 2 shows a simplified view of the actor’s campaign that targeted students enrolled at the University of San Diego, one of many universities that received these emails.
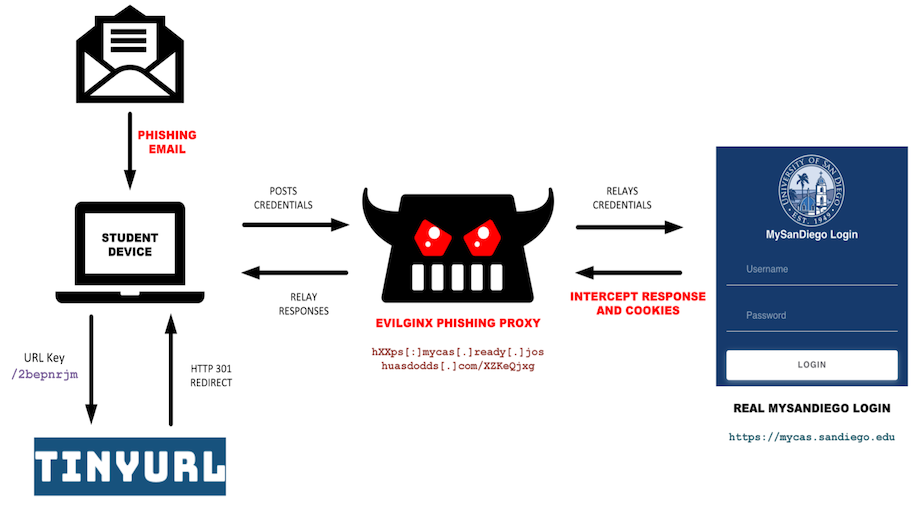
Figure 2. The threat actor used Evilginx to target University of San Diego students.
DNS Unveils Targets
Although the Evilginx proxy phishing URLs expired quickly, traces of their activities remain in passive DNS. When cybercriminals configure subdomains for phishlets, they typically use names that closely mimic legitimate login pages to appear authentic. This particular actor uses subdomain labels that match the legitimate service domain. For example, in one attack the phishing subdomain shibbolethmainrit[.]fiuy[.]weddingsarahetemmanuel[.]com impersonated a Rochester Institute of Technology SSO login page, which is hosted at shibboleth.main.ad.rit.edu. Both domains share the prefix “shibboleth,” which refers to an open-source identity management and authentication service.
By analyzing these labels, we determined that the actor has targeted at least 18 different U.S. universities. Figure 3 highlights the most targeted institutions based on the volume of DNS queries to their phishing sites. The top five targeted institutions are the University of California Santa Cruz, University of California Santa Barbara, University of San Diego, Virginia Commonwealth University, and the University of Michigan.
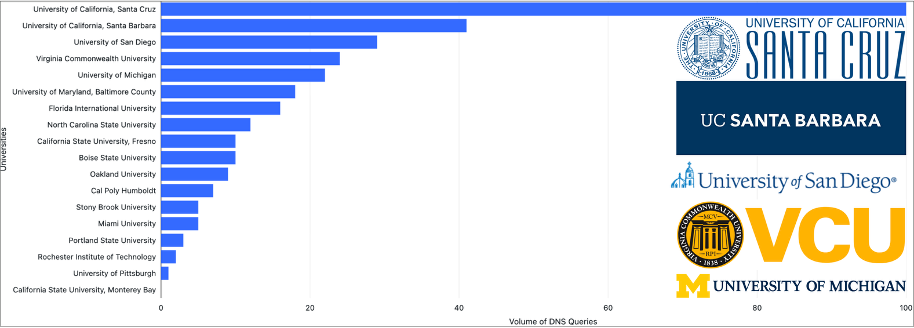
Figure 3. Universities targeted by the Evilginx actor
While the actor is currently using Cloudflare to hide their hosting location, they previously used dedicated servers in GoDaddy and NameCheap. In their infrastructure conversion, they reused some domains, allowing us to unravel a much larger set of campaigns and analyze the attack timeline. In total, we found 67 domains owned by the actor. The first domain observed was catering-amato[.]com.
The first known phishing attack using this infrastructure occurred on April 12, 2025, against the University of San Diego. Attack volumes remained relatively low until mid-2025, when activity increased significantly. Additional targets were added over time; the University of Maryland, Baltimore County on November 16, 2025. See Figure 1.
DNS as a Detection Weapon
The low detection rates across the cybersecurity community highlight how effective Evilginx’s evasion techniques have become. Recent versions, such as Evilginx Pro, add features that make detection even harder. These include default use of wildcard TLS certificates, bot filtering through advanced fingerprinting like JA4, decoy web pages, improved integration with DNS providers (e.g., Cloudflare, DigitalOcean), multi-domain support for phishlets, and JavaScript obfuscation. As Evilginx continues to mature, identifying its phishing URLs will only become more challenging. Traditional detection methods and manual hunting can’t keep pace at scale. Fortunately, threat actors who leverage tools like Evilginx usually still utilize domain names for their operations and often leave fingerprints, allowing us a means to be a little devilish and foil their plans.
IoAs
The table below provides IoAs (indicators of activity) used by this Evilginx threat actor. We strongly recommend that organizations block the domains in this list for better protection over DNS. For more indicators, visit the Infoblox Threat Intel Github repo: https://github.com/infobloxopen/threat-intelligence/tree/main.
| Indicator | Type | Note |
|---|---|---|
| 132[.]148[.]73[.]92 | IPv4 | Dedicated IP address hosting Evilginx phishing proxy domains |
| 132[.]148[.]74[.]178 | IPv4 | Dedicated IP address hosting Evilginx phishing proxy domains |
| 160[.]153[.]176[.]197 | IPv4 | Dedicated IP address hosting Evilginx phishing proxy domains |
| 160[.]153[.]178[.]199 | IPv4 | Dedicated IP address hosting Evilginx phishing proxy domains |
| 162[.]0[.]214[.]254 | IPv4 | Dedicated IP address hosting Evilginx phishing proxy domains |
| 162[.]0[.]228[.]151 | IPv4 | Dedicated IP address hosting Evilginx phishing proxy domains |
| 192[.]169[.]177[.]165 | IPv4 | Dedicated IP address hosting Evilginx phishing proxy domains |
| 199[.]192[.]23[.]40 | IPv4 | Dedicated IP address hosting Evilginx phishing proxy domains |
| 203[.]161[.]60[.]59 | IPv4 | Dedicated IP address hosting Evilginx phishing proxy domains |
| 208[.]109[.]244[.]86 | IPv4 | Dedicated IP address hosting Evilginx phishing proxy domains |
| 208[.]109[.]39[.]196 | IPv4 | Dedicated IP address hosting Evilginx phishing proxy domains |
| 64[.]202[.]186[.]223 | IPv4 | Dedicated IP address hosting Evilginx phishing proxy domains |
| 66[.]29[.]133[.]135 | IPv4 | Dedicated IP address hosting Evilginx phishing proxy domains |
| 72[.]167[.]224[.]193 | IPv4 | Dedicated IP address hosting Evilginx phishing proxy domains |
| 72[.]167[.]52[.]130 | IPv4 | Dedicated IP address hosting Evilginx phishing proxy domains |
| acmsquared[.]com | domain | Domain used by Evilginx phishing proxy URL |
| ads2ads[.]com | domain | Domain used by Evilginx phishing proxy URL |
| aghomesandproperties[.]com | domain | Domain used by Evilginx phishing proxy URL |
| allwebdirectories[.]com | domain | Domain used by Evilginx phishing proxy URL |
| amj-international[.]com | domain | Domain used by Evilginx phishing proxy URL |
| apartamentosmalaga[.]com | domain | Domain used by Evilginx phishing proxy URL |
| armingaud[.]com | domain | Domain used by Evilginx phishing proxy URL |
| bazmepaigham[.]com | domain | Domain used by Evilginx phishing proxy URL |
| bedrijvenregister[.]com | domain | Domain used by Evilginx phishing proxy URL |
| bestshayari[.]com | domain | Domain used by Evilginx phishing proxy URL |
| brillianceboundielts[.]com | domain | Domain used by Evilginx phishing proxy URL |
| brownak[.]com | domain | Domain used by Evilginx phishing proxy URL |
| buildonhope[.]com | domain | Domain used by Evilginx phishing proxy URL |
| cappadociavisittours[.]com | domain | Domain used by Evilginx phishing proxy URL |
| catering-amato[.]com | domain | Domain used by Evilginx phishing proxy URL |
| cccsok[.]com | domain | Domain used by Evilginx phishing proxy URL |
| citywideprayer[.]com | domain | Domain used by Evilginx phishing proxy URL |
| controlunlimited[.]com | domain | Domain used by Evilginx phishing proxy URL |
| coralridgehour[.]com | domain | Domain used by Evilginx phishing proxy URL |
| dartsinireland[.]com | domain | Domain used by Evilginx phishing proxy URL |
| data-logistics[.]com | domain | Domain used by Evilginx phishing proxy URL |
| dhoughton[.]com | domain | Domain used by Evilginx phishing proxy URL |
| dogcuty[.]com | domain | Domain used by Evilginx phishing proxy URL |
| e-briefe[.]com | domain | Domain used by Evilginx phishing proxy URL |
| eggcoo[.]com | domain | Domain used by Evilginx phishing proxy URL |
| eheringe-trauringe[.]com | domain | Domain used by Evilginx phishing proxy URL |
| ehsantrust[.]com | domain | Domain used by Evilginx phishing proxy URL |
| esdetodo[.]com | domain | Domain used by Evilginx phishing proxy URL |
| fluffybascha[.]com | domain | Domain used by Evilginx phishing proxy URL |
| forty-something[.]com | domain | Domain used by Evilginx phishing proxy URL |
| freaksandfriends[.]com | domain | Domain used by Evilginx phishing proxy URL |
| geegletee[.]com | domain | Domain used by Evilginx phishing proxy URL |
| georgiayr[.]com | domain | Domain used by Evilginx phishing proxy URL |
| goraba[.]com | domain | Domain used by Evilginx phishing proxy URL |
| hafikoman[.]com | domain | Domain used by Evilginx phishing proxy URL |
| heisseliebe[.]com | domain | Domain used by Evilginx phishing proxy URL |
| hurenkontakte[.]com | domain | Domain used by Evilginx phishing proxy URL |
| ideallivingsolutions[.]com | domain | Domain used by Evilginx phishing proxy URL |
| igreensoft[.]com | domain | Domain used by Evilginx phishing proxy URL |
| ilchirone[.]com | domain | Domain used by Evilginx phishing proxy URL |
| impexinc[.]com | domain | Domain used by Evilginx phishing proxy URL |
| inkdchronicles[.]com | domain | Domain used by Evilginx phishing proxy URL |
| intellipex[.]com | domain | Domain used by Evilginx phishing proxy URL |
| intercuba[.]com | domain | Domain used by Evilginx phishing proxy URL |
| ispamembers[.]com | domain | Domain used by Evilginx phishing proxy URL |
| jimmylange[.]com | domain | Domain used by Evilginx phishing proxy URL |
| joshuasdodds[.]com | domain | Domain used by Evilginx phishing proxy URL |
| kbdav[.]com | domain | Domain used by Evilginx phishing proxy URL |
| l2storm[.]com | domain | Domain used by Evilginx phishing proxy URL |
| littlenuggetsco[.]com | domain | Domain used by Evilginx phishing proxy URL |
| lost-signal[.]com | domain | Domain used by Evilginx phishing proxy URL |
| lpdeco[.]com | domain | Domain used by Evilginx phishing proxy URL |
| monnalissaboutique[.]com | domain | Domain used by Evilginx phishing proxy URL |
| mpoterbaru2024[.]com | domain | Domain used by Evilginx phishing proxy URL |
| mykidsfashion[.]com | domain | Domain used by Evilginx phishing proxy URL |
| northstarcouncil[.]com | domain | Domain used by Evilginx phishing proxy URL |
| qrcodespoweredbygs1[.]com | domain | Domain used by Evilginx phishing proxy URL |
| schnaitsee[.]com | domain | Domain used by Evilginx phishing proxy URL |
| sercanaydin[.]com | domain | Domain used by Evilginx phishing proxy URL |
| srpskazemlja[.]com | domain | Domain used by Evilginx phishing proxy URL |
| thelovecity[.]com | domain | Domain used by Evilginx phishing proxy URL |
| thermalresistivity[.]com | domain | Domain used by Evilginx phishing proxy URL |
| transusasia[.]com | domain | Domain used by Evilginx phishing proxy URL |
| tubeunderwater[.]com | domain | Domain used by Evilginx phishing proxy URL |
| weddingsarahetemmanuel[.]com | domain | Domain used by Evilginx phishing proxy URL |
| winbet299mas[.]com | domain | Domain used by Evilginx phishing proxy URL |
| yoopuipui[.]com | domain | Domain used by Evilginx phishing proxy URL |








