Infoblox’s DNS Early Detection Program utilizes proprietary techniques to identify potentially malicious domains at the earliest opportunity. The program shares our recent analysis of malicious domains disclosed through public OSINT, contrasting it with our preliminary identification of these domains as suspicious.

The need for speed is real. Threat actors have refined their techniques, causing most of the potential damage before malicious domains are identified and shared through open source intelligence (OSINT) and the majority of commercial threat intel feeds. Threat actors are capitalizing on the speed of execution, which necessitates an even faster response from defenders.
| Every second counts when identifying malicious campaigns and the DNS domains which support them. Infoblox’s early identification of these malicious domains as suspicious makes them available for blocking weeks, even months, ahead of the data provided in many industry-wide malicious threat intel feeds and OSINT sources. |
The Lazarus Group Releases KandyKorn
Lazarus Group is a state-sponsored cyber threat group that has been attributed to the North Korean Reconnaissance General Bureau1,2. The group started activity in approximately 2009 and over many years they have been involved in the theft of many millions of dollars of financial assets as well as the theft of intellectual property and other confidential data. Initially they attacked the South Korean government in Seoul, but have since moved broadly to steal from banks and attack commercial organizations such as Sony Pictures. Targets include the finance industry and potentially healthcare, supply chain management, government related industries, and more.
Malware used by Lazarus Group correlates to other reported campaigns, including Operation Flame, Operation 1Mission, Operation Troy, DarkSeoul, and Ten Days of Rain. North Korean group definitions are known to have significant overlap, and some security researchers report all North Korean state-sponsored cyber activity under the name Lazarus Group instead of tracking clusters or subgroups, such as Andariel, APT37, APT38, and Kimsuky. More information disambiguating Lazarus Group is available within MITRE ATT&CK.
KandyKorn is a highly sophisticated and dangerously formidable remote access trojan (RAT). Lazarus Group’s use of the KandyKorn malware tool highlights the group’s continued build-out of sophisticated tools and growing dangers of their cyberattacks. The KandyKorn campaign utilizes Python scripts to directly target blockchain software engineers using the MacOS. A very detailed analysis of this attack and the indicators of compromise (“observables”) were published in OSINT on October 31, 20233.
Anatomy of the Attack – Lazarus KandyKorn
| Stage 0: Social engineering blockchain engineers via conversations on Discord which loads Watcher.py |
Using Discord and leveraging social engineering, programmers and engineers are tricked into downloading a malicious Python application. As we see all of the time, users are manipulated by social engineering to participate in the early stages of the Cyber Kill Chain4. This Python application appears as a crypto arbitrage bot which enables users to profit from cryptocurrency rate differences between various platforms. This arbitrage bot was acquired by downloading Cross-Platform Bridges.zip. Malicious links are hosted on a google drive. The malicious app’s Main.py script imports Watcher.py.
| Stage 1: Watcher.py checks the Python version and then runs testSpeed.py and acquires FinderTools |
TestSpeed.pydownloads and executes FinderTools. Once execution is complete, testSpeed.py is removed. The FinderTools are saved as /Users/Shared/FinderTools.
| Stage 2: FinderTools now run SUGARLOADER |
After a series of complex activities the Cyber Kill Chain is well underway. SUGARLOADER is an executable that finds and identifies a config file required for KandyKorn execution. After successfully acquiring the config file, the FinderTool connects to the C2 malicious domain tp-globa[.]xyz.
| C2 Malicious DNS Domain: tp-globa[.]xyz identified and blocked by Infoblox within 3 days of the WHOIS date |
This malicious C2 domain tp-globa[.]xyz is a key component of the KandyKorn Cyber Kill Chain. This malicious domain, when researched in Infoblox Dossier, shows a WHOIS date of August 13, 2023 and being identified and blocked by Infoblox as a suspicious domain on August 15, 2023. The estimated release via OSINT is October 31, 2023.
| Stage 3: SUGARLOADER downloads HLOADER |
Assuming that the C2 malicious DNS domain tp-globa[.]xyz was not blocked the complex Kill Chain continues to unfold with the inclusion of a clever and stealthy persistence mechanism. Apple’s login item monitoring remains unaware of the techniques being used.
| Stage 4: KandyKorn Payload is delivered – Game Over! |
SUGARLOADER fetches and runs KandyKorn. KandyKorn is the final step in the Kill Chain and can now access and exfiltrate targeted data from the victim’s computer. GAME OVER! Your organization may suffer financial loss, the theft and exposure of valuable intellectual property, or worse.
KandyKorn has a wide variety of ways to monitor and avoid detection which make it even more dangerous. In one observed technique, KandyKorn uses reflective loading which is a direct-memory form of execution that may bypass detections. Reflective loading allows threat actors to deliver malicious payloads and malware on victim’s systems, without leaving behind critical forensic artifacts such as files on disk.
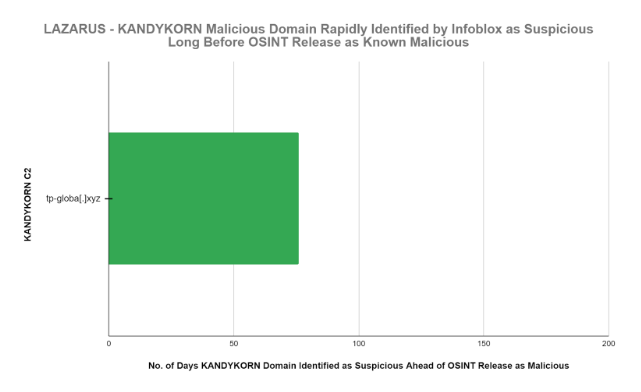
Note that Infoblox threat intelligence identified the critical malicious domain tp-globa[.]xyz, essential to execution of the Kill Chain, as suspicious 76 days or well over 2 months ahead of its identification and release as malicious in OSINT. This malicious domain is an essential component of the KandyKorn Kill Chain. The identification and subsequent blocking by the Infoblox ecosystem of this one (1) domain would stop the KandyKorn Kill Chain immediately.
| Infoblox identified the KandyKorn C2 tp-globa[.]xyz malicious domain as suspicious 76 days or well over 2 months ahead of the identification and release of this domain as malicious in OSINT. This enabled our customers to block it and stop execution of the KandyKorn Kill Chain. |
There have been many malicious domains attributed to Lazarus Group over time. The domains highlighted in this blog include most of those identified in recent OSINT analysis published approximately on October 31, 2023.
Supporting Analysis and Methodology
On October 31, 2023, data on newly identified KandyKorn kill chain and critical domains was published in OSINT. The Infoblox team analyzed them to determine if they were identified earlier by our suspicious domain feeds.
The critical domain in the KandyKorn Cyber Kill Chain, tp-globa[.]xyz, which was identified in OSINT was researched in the Infoblox Dossier portal by our team. We reviewed our timeline feature to extract the earliest dates associated with Infoblox suspicious designation. We also extracted the WHOIS information for additional context.
The conclusions of our analysis were definitive. The C2 domain which is a critical path component of the KandyKorn Kill Chain was identified as suspicious by Infoblox threat intelligence 76 days prior to the availability of the OSINT designation as malicious.
It is often the case that OSINT publication dates may sometimes be unclear or lack precision. The dates of published articles by reputable 3rd parties may not always accurately reflect the OSINT availability of each individual domain as identified by their threat researchers.
To provide context on the performance of our suspicious threat intel feeds we extracted the WHOIS date and found that the same KandyKorn domain was blocked as suspicious within 3 days after the WHOIS domain registration date. The WHOIS dates are almost always precise and provide another perspective on the high value of suspicious threat intel feed content.
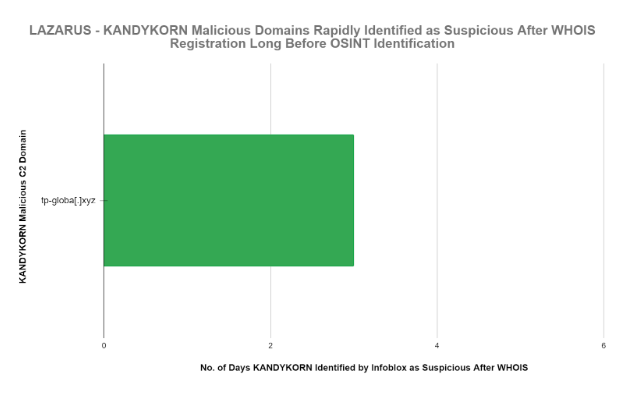
| Infoblox finds potentially malicious DNS domains faster. Infoblox identified the KandyKorn C2 tp-globa[.]xyz malicious domain as suspicious within 3 days of the domain’s registration date in WHOIS. |
Per the U.S. National Security Agency (NSA), Protective DNS, such as that offered by Infoblox, would reduce the ability for 92% of malware attacks both from command and control perspective, deploying malware on a given network.
So, if you rapidly identify and block access to the C2 domain tp-globa[.]xyz then the KandyKorn Kill Chain is shut down. This can happen days, weeks, or even months before information on KandyKorn is publicly available in OSINT sources.
There were quite a few related domains and campaign intersections identified within OSINT. This may be based upon data on the TLS certificate which is then used as a pivot point to learn more about these related, and often malicious domains. For example, we found this as used in a related Lazarus campaign:
| Related C2 Malicious DNS Domain: pro-tokyo[.]top identified and blocked by Infoblox on July 23, 2023. |
The WHOIS date for the malicious pro-tokyo[.]top domain was July 18, 2023 and it showed up in Twitter posting in OSINT on July 30, 20235. This source on Twitter might have been announced, but still unobserved, by many threat researchers and defenders.
Recognize that attack groups like Lazarus are continually creating and changing the domains they use to camouflage their attacks. All of the key domains used in delivering the KandyKorn RAT may be shut down in just a few days and replaced with something new. You can see the tangible advantages Infoblox early DNS Detection threat intelligence can bring to your organization.
Risk Reduction and Return on Investment
| Infoblox’s suspicious domain data can help our customers avoid a potentially devastating data breach by the Lazarus Group leveraging tools such as KandyKorn. Suspicious domain data can reduce risk and increase the return on investment for your threat intelligence program. |
The use of our proprietary technology to identify suspicious domains is a major “Shift Left” to normal processes used across the industry to develop and leverage DNS threat intelligence information. Infoblox suspicious domain data helps security operations teams gain the timely information they need to better address and defeat the barrage of new threats before they can cause harm.
For Additional Information
The Infoblox Threat Intelligence Group provides fast access to accurate, contextual threat alerts and reports sourced from our own real-time research teams. Suspicious Domains feeds were introduced as an Infoblox proprietary product on November 10, 2022 and, since then, have successfully provided many thousands of customers with the advanced information to block domains which ultimately become malicious long before most other threat intelligence sources identify them as malicious. Infoblox allows your team to leverage the high value of suspicious domain threat intelligence while ensuring unified security policy across your entire security infrastructure. Infoblox threat data minimizes false positives, so you can be confident in what you are blocking.
To learn more about suspicious domains and DNS early detection:
https://www.infoblox.com/threat-intel/
To learn more about BloxOne Threat Defense:
https://www.infoblox.com/products/bloxone-threat-defense/
To learn more about Advanced DNS Protection:
https://www.infoblox.com/products/advanced-dns-protection/
To learn more about the National Security Agency (NSA) and Cybersecurity & Infrastructure Security Agency (CISA) guidance on Protective DNS:
https://media.defense.gov/2021/Mar/03/2002593055/-1/-1/0/CSI_PROTECTIVE%20DNS_UOO117652-21.PDF
Footnotes
- https://www.cisa.gov/news-events/alerts/2017/06/13/hidden-cobra-north-koreas-ddos-botnet-infrastructure
- https://home.treasury.gov/news/press-releases/sm774
- https://www.elastic.co/security-labs/elastic-catches-dprk-passing-out-kandykorn
- https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html
- https://twitter.com/TLP_R3D/status/1685581711139102720