Infoblox’s DNS Early Detection Program utilizes proprietary techniques to identify potentially malicious domains at the earliest opportunity. The program shares our recent analysis of malicious domains disclosed through public OSINT, contrasting it with our preliminary identification of these domains as suspicious.
Threat actors have refined their techniques, causing most of the potential damage before malicious domains are identified and shared through open source intelligence (OSINT) and the majority of commercial threat intel feeds. They are capitalizing on the speed of execution, which necessitates a swift response from defenders.
| Infoblox finds potentially dangerous DNS domains faster. Infoblox identification of these suspicious domains makes them available for blocking weeks, even months, earlier than the domains published in many industry-wide malicious threat intel feeds. |
Void Rabisu ROMCOM
Void Rabisu, an evolving and sophisticated threat actor group, also known as Storm-0978, Tropical Scorpius, and UNC2596 has been identified as using a new variation of their malware ROMCOM1. The ROMCOM backdoor was first discovered in 2022 and has undergone several iterations, with the latest variant known as the slimmed down version of ROMCOM also called ROMCOM 4.0, ROMCOMLITE, and PEAPOD.
The ROMCOM malware tool is used to enable both espionage and financially motivated attacks2. Void Rabisu initially concentrated on ransomware attacks with financial motives. However, they have since shown an increasing interest in cyberespionage.
In the most recent attacks Void Rabisu has primarily targeted organizations in Ukraine and various NATO countries including military personnel, government agencies and political leaders. They have recently been observed targeting female political leaders within these countries using the new ROMCOMLITE variant.
The ROMCOM backdoor’s capabilities extend beyond espionage, as it can steal sensitive information and deploy other malware. Void Rabisu’s use of this malware tool highlights the group’s adaptability and growing sophistication of their cyberattacks. Void Rabisu remains an active and dangerous threat actor, and organizations should be vigilant in protecting themselves against their attacks.
Understanding Void Rabisu and the ROMCOM Cyber Kill Chain3
In approximately early August 2023 Void Rabisu set up a fake version of the official website of the Women Political Leaders (WPL) Summit held in Brussels earlier in June. This malicious website utilized social engineering techniques to entice victims into downloading malicious attachments containing the backdoor4.
Specifically, the correct domain name for the official website is wplsummit.org. This domain was spoofed using a lookalike domain and presented instead as the fake website:
| Malicious Domain #1: wplsummit[.]com |
When various photos were selected and clicked for download, this fake and malicious website ultimately delivered the ROMCOM payload. Once downloaded and active, the malware sends a request for to a URL /favicon.ico in the malicious domain:
| Malicious Domain #2: https://mctelemetryzone[.]com |
This, in turn, initiates the download of an encrypted file which works to set up the payload. After several activities another outreach to a malicious domain is made to download the 3rd stage component:
| Malicious Domain #3: redditanalytics[.]pm |
This redditanalytics[.]pm component, in turn, communicates with the C2 server:
| Malicious Domain #4: netstaticsinformation[.]com |
These various components continue to execute the Kill Chain which ultimately supports the threat actor’s espionage and/or financial objectives. Other ROMCOM identified or suspected C2 servers identified in OSINT5 include but are not limited to:
| Malicious Domain #5: wirelessvezion[.]com |
| Malicious Domain #6: budgetnews[.]org |
Malicious domain #5 appears to be using typosquatting techniques to mimic perhaps a legitimate Verizon wireless domain or branding. Malicious domain #6 is using a “.org” top level domain which seems to carry trusted branding for many internet users. This trust is no longer deserved as anyone can buy these domains today and use them for malicious purposes.
The attack likely started in early August, on or around the 8th when the lookalike domain #1 was set up. Some of the components like the C2 we can see had domain names set up even earlier.
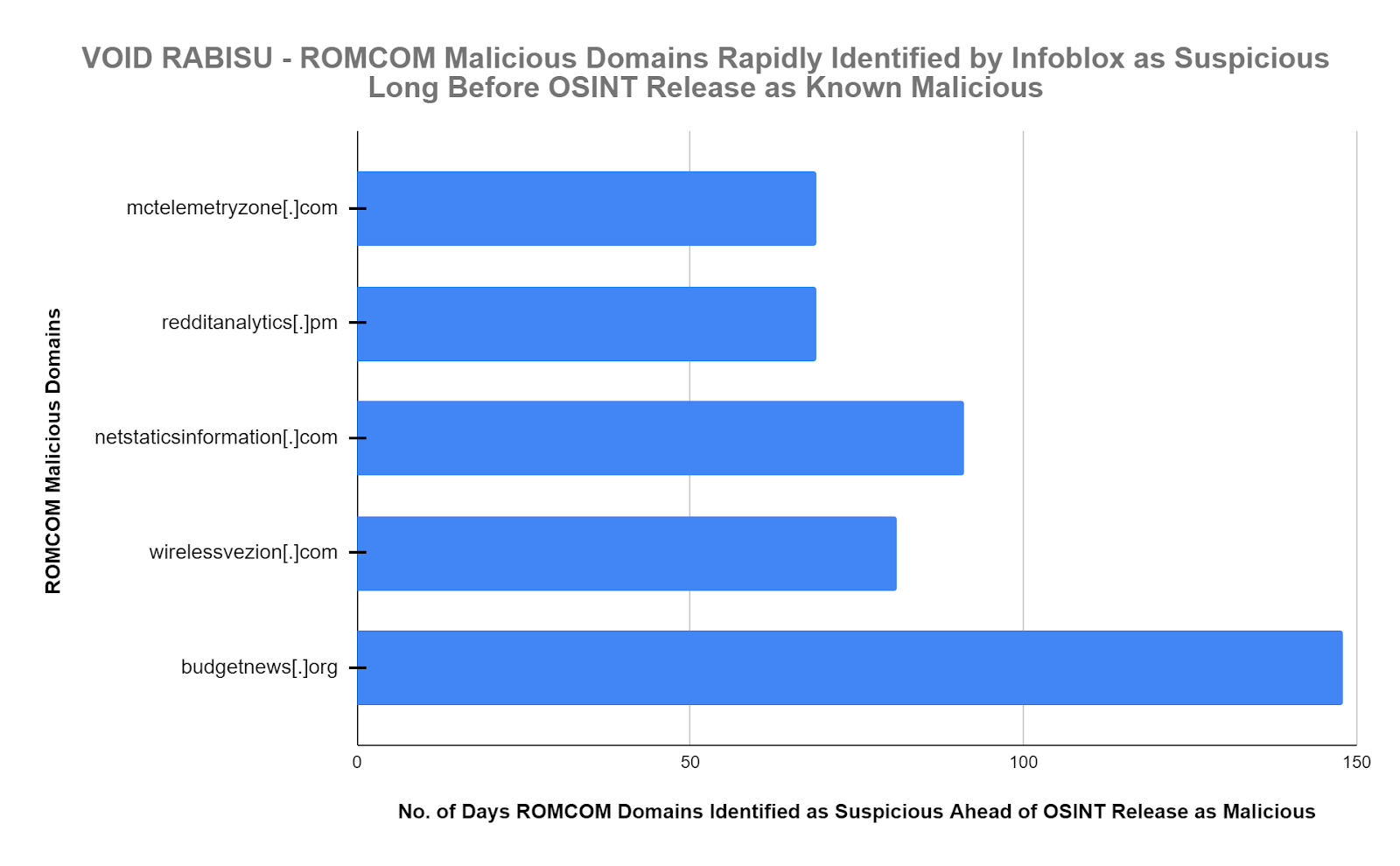
Infoblox threat intelligence identified domains #2, #3, and #4, #5, and #6 as suspicious an average of 91.6 days or over 3 months ahead of their identification and release as malicious in OSINT. Domains #2, #3, and #4 are key and essential components of the ROMCOM Kill Chain.
The identification and subsequent blocking by the Infoblox ecosystem of any one (1) of these domains would have stopped the ROMCOM Kill Chain immediately.
| Infoblox identified multiple ROMCOM malicious domains as suspicious an average of 91.6 days or over 3 months ahead of their identification and release as malicious in OSINT. This enabled our customers to block them and prevent execution of the ROMCOM Kill Chain. |
There have been many malicious domains attributed to VOID RABISU and ROMCOM over time. The domains highlighted in this blog include most of those identified in recent OSINT analysis published approximately on October 13, 2023.
Supporting Analysis and Methodology
On October 13, 2023, data on newly identified ROMCOM domains was published in OSINT. Analysis of these malicious domains was done by the Infoblox team to determine if they were identified earlier by our suspicious domain feeds.
Each malicious ROMCOM domain identified in OSINT was researched in the Infoblox Dossier portal by our team. We reviewed our timeline feature to extract the earliest dates associated with Infoblox suspicious designation. We also extracted the WHOIS information for additional context.
The conclusions of our analysis were definitive. Key ROMCOM domains which are critical path components of the ROMCOM Kill Chain were identified as suspicious by Infoblox threat intelligence an average of 91.6 days prior to the availability of the OSINT designation as malicious.
It is often the case that OSINT publication dates may sometimes be unclear or lack precision. The dates of published articles by reputable 3rd parties may not always accurately reflect the OSINT availability of each individual domain as identified by their threat researchers.
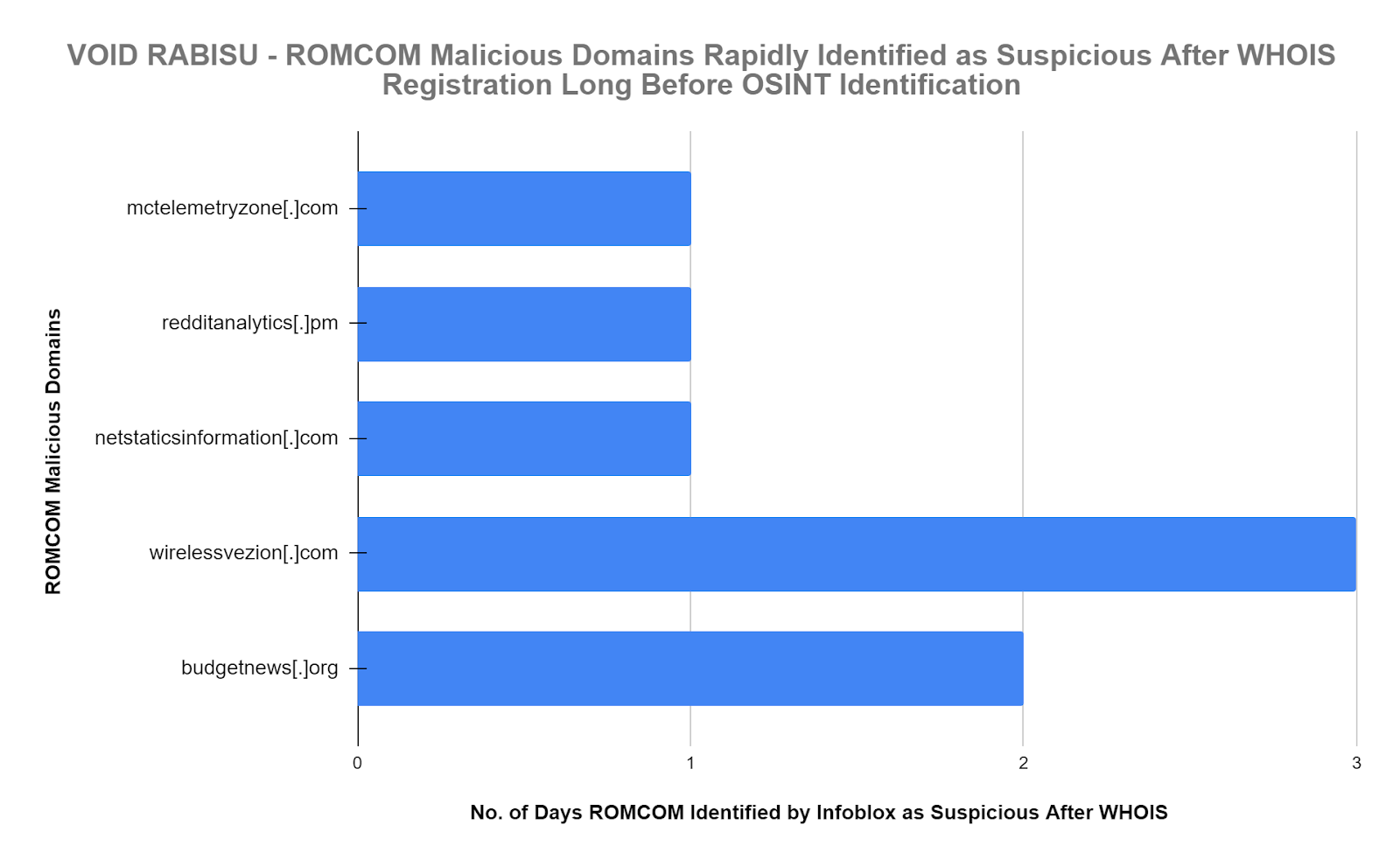
To provide context on the performance of our suspicious threat intel feeds we extracted WHOIS dates and found that the same ROMCOM domains were blocked as suspicious within an average of 1.6 days after the WHOIS domain registration date. The WHOIS dates are almost always precise and provide another perspective on the high value of suspicious threat intel feed content.
Risk Reduction and Return on Investment
| Infoblox’s suspicious domain data can help our customers avoid a potentially devastating data breach. Suspicious domain data can reduce risk and increase the return on investment for your threat intelligence program. |
The use of our proprietary technology to identify suspicious domains is a major “Shift Left” to normal processes used across the industry to develop and leverage threat intelligence information. Infoblox suspicious domain data helps security operations teams gain the timely information they need to better address and defeat the barrage of new threats before they can cause harm.
For Additional Information
The Infoblox Threat Intelligence Group provides fast access to accurate, contextual threat alerts and reports sourced from our own real-time research teams. Suspicious Domains feeds were introduced as an Infoblox proprietary product on November 10, 2022 and, since then, have successfully provided many thousands of customers with the advanced information to block domains which ultimately become malicious long before most other threat intelligence sources identify them as malicious. Infoblox allows your team to leverage the high value of suspicious domain threat intelligence while ensuring unified security policy across your entire security infrastructure. Infoblox threat data minimizes false positives, so you can be confident in what you are blocking.
To learn more about suspicious domains and DNS early detection:
https://www.infoblox.com/threat-intel/
To learn more about lookalike domains:
https://blogs.infoblox.com/cyber-threat-intelligence/lookalike-domain-attacks-are-on-the-rise-be-on-the-lookout-for-these-four-types/
https://insights.infoblox.com/resources-whitepaper/infoblox-report-deep3r-look-at-lookal1ke-attacks
To learn more about BloxOne Threat Defense:
https://www.infoblox.com/products/bloxone-threat-defense/
To learn more about Advanced DNS Protection:
https://www.infoblox.com/products/advanced-dns-protection/
To learn more about the National Security Agency (NSA) and Cybersecurity & Infrastructure Security Agency (CISA) guidance on Protective DNS:
https://media.defense.gov/2021/Mar/03/2002593055/-1/-1/0/CSI_PROTECTIVE%20DNS_UOO117652-21.PDF
To learn how using NSA analysis concluded that, “DNS would reduce the ability for 92 percent of malware attacks both from command and control perspective, deploying malware on a given network.” based on NSA analysis.”
https://executivegov.com/2020/06/anne-neuberger-on-nsas-secure-dns-pilot-program/
Footnotes
- https://thehackernews.com/2023/10/new-peapod-cyberattack-campaign.html
- Void Ramisu: “A Sophisticated Threat Actor Group Using the ROMCOM Backdoor for Espionage and Financially Motivated Attacks” Mandiant Security Response 2022. https://www.trendmicro.com/en_us/research/23/e/void-rabisu-s-use-of-romcom-backdoor-shows-a-growing-shift-in-th.html
- Cyber Kill Chain is a registered trademark of Lockheed Martin https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html
- https://www.trendmicro.com/en_us/research/23/j/void-rabisu-targets-female-leaders-with-new-romcom-variant.html
- https://www.trendmicro.com/content/dam/trendmicro/global/en/research/23/j/void-rabisu-targets-female-political-leaders/ioc-void-rabisu-targets-female-political-leaders-with-new-slimmed-down-ROMCOM-variant.txt