Bulletin
Who:
- Between October 2024 and early February 2025, multiple news sources and blogs reported on LummaStealer malware distributed via fake CAPTCHA.
- The information stealer is active across various sectors, primarily targeting users who store sensitive information in their browsers and cryptocurrency wallets.
- Identity-based threats pose a substantial risk to any organization as it allows actors to bypass controls using credentials from legit users. According to the January 25 “Global cost of ransomware study”, executed by Ponemon Institute, 48 percent of all respondents reported that actors target cached credentials as a key tactic to move lateral and escalate privileges.
What:
- LummaStealer, also known as LummaC2, is a type of malware that first appeared in 2022. It is designed to steal sensitive information from infected systems.
- LummaStealer is available through a Malware-as-a-Service (MaaS) model on various forums and collects sensitive data, such as passwords and cryptocurrency wallets. This data can be used to impersonate individuals, commit fraud or conduct further reconnaissance to gain unauthorized access to IT systems within an organization.
- Numerous commercial and open-source publications have extensively documented the use of counterfeit CAPTCHA pages to distribute LummaStealer. These CAPTCHA pages are designed to deceive users into executing commands that download uniquely crafted files capable of evading endpoint detection systems. The underlying source code for these deceptive pages has been made available from an open-source repository. By leveraging a well-known CAPTCHA service, the interaction appears legitimate to users, fostering trust and minimizing skepticism.
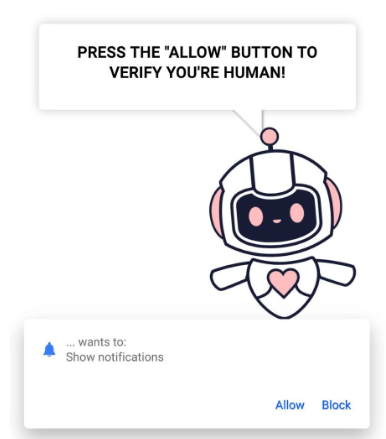
Picture 1: Sample fake CAPTCHA discovered by Infoblox
Threat actors use fake CAPTCHA to increase trust and establish initial foothold by initiation obfuscated command-level run scripts. Once the scripts are running, actors can drop secondary payloads and initiate lateral movements.
Infoblox Capability:
- Infoblox monitors threat actor infrastructure continuously by analyzing DNS traffic and changes made to domains. This results in threat intel discovering early indicators of attack before active payloads have been seen.
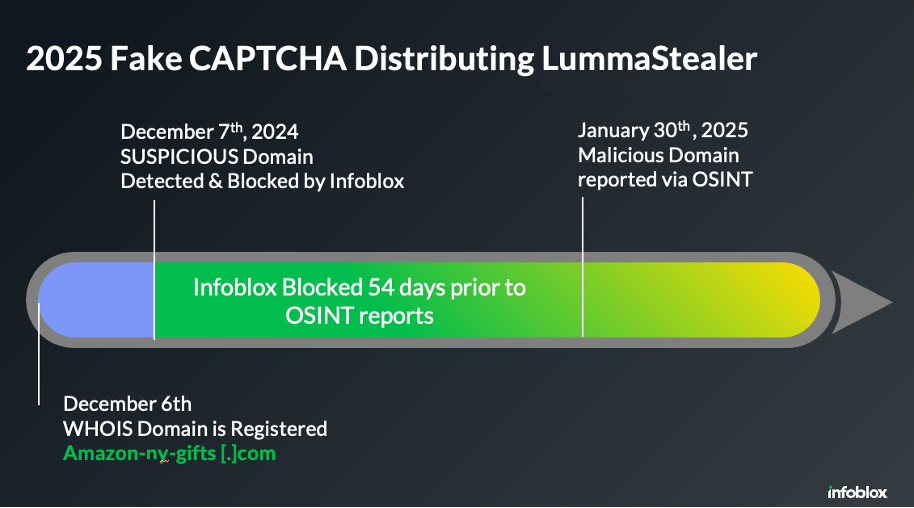
- The list below provides a summary of domains reported by various publicly made reports. These domains have been linked to fake CAPTCHA pages or used to distribute LummaStealer. The column in green provides the date when Infoblox detected these malicious domains and delta time before the public report was made available.
| Publicly Reported Domains | Publication Date | Infoblox Discovery | Early Protection Metric |
|---|---|---|---|
| googlsearchings[.]online | 1/30/25 | 1/12/25 | 18 |
| sharethewebs[.]click | 1/30/25 | 1/13/25 | 17 |
| googlsearchings[.]art | 1/23/25 | 1/11/25 | 12 |
| Kklipderiq[.]shop | 1/13/25 | 12/9/24 | 35 |
| amazon-ny-gifts[.]com | 1/30/25 | 12/5/24 | 56 |
| h3[.]errantrefrainundocked[.]shop | 1/23/25 | 1/20/25 | 3 |
| futureddospzmvq[.]shop | 10/22/24 | 9/6/24 | 46 |
| writerospzm[.]shop | 10/22/24 | 8/8/24 | 75 |
| mennyudosirso[.]shop | 10/22/24 | 8/8/24 | 75 |
| deallerospfosu[.]shop | 10/22/24 | 8/8/24 | 75 |
| quialitsuzoxm[.]shop | 10/22/24 | 8/8/24 | 75 |
| complaintsipzzx[.]shop | 10/22/24 | 8/8/24 | 75 |
| bassizcellskz[.]shop | 10/22/24 | 8/8/24 | 75 |
| languagedscie[.]shop | 10/22/24 | 8/8/24 | 75 |
| celebratioopz[.]shop | 10/22/24 | 8/8/24 | 75 |
- By using unique DNS telemetry and advanced data science, Infoblox Threat Intel provided an average early detection advantage of 46.8 days before other sources publicized. Infoblox flagged these domains as “high risk” so defenders can automatically block them weeks to months before active payloads are delivered.
Infoblox Impact and Recommendations
- Infoblox customers running in blocking mode using our high-risk feeds were protected from these dangerous domains.
- Given the easy access to malicious adtech services and public availability of fake CAPTCHA content, threat actors will continue and potentially increase their usage. Security organizations are urged to strengthen their defenses with DNS base intel and discover malicious infrastructure before payloads are delivered.
Additional Information on Combating Deception and Evasion Techniques
A recent research report published by Infoblox documented the extensive use of fake CAPTCHAs within malicious adtech. Similar to regular adtech, this scheme involves operators and malicious advertisers. Advertisers pay operators to target vulnerable victims with highly deceptive content, while remain hidden from threat researchers. This is done through large traffic distribution systems (TDS) that consist of complex meshes of domain redirections fully controlled by malicious adtech operators.
One of these actors, tracked by Infoblox, named VexTrio Viper, controls over 84,000 domains. Malicious adtech operators are often organized into individual, professional-looking entities to avoid legal scrutiny. However, combined their services provide adversaries with highly sophisticated digital tactics to carry out cybercrime, while avoiding threat research. The combination of highly deceptive content, like fake CAPTCHA and advanced evasion obtained through TDSs, impact individuals as well as the organizations they belong to.
Recommended Action: Click here to request a security workshop.
To learn more about Infoblox Threat Intel and DNS early detection:
https://www.infoblox.com/threat-intel/
To learn more about Infoblox Threat Defense:
https://www.infoblox.com/products/threat-defense/
(1) List of organizations warning on LummaStealer and Fake reCaptcha
https://blog.qualys.com/vulnerabilities-threat-research/2024/10/20/unmasking-lumma-stealer-analyzing-deceptive-tactics-with-fake-captcha
https://blog.reveng.ai/one-clickfix-and-lummastealer-recaptchas-our-attention-part-1/
https://www.netskope.com/blog/lumma-stealer-fake-captchas-new-techniques-to-evade-detection
https://www.eset.com/blog/business/lumma-stealer-a-fast-growing-infostealer-threat-1/
https://it.osu.edu/news/2025/01/13/beware-fake-captcha-initiates-malware










