DNS Early Detection – Proof of Value Study
In this blog, we present a proof of value study demonstrating the value of detecting attempted DNS exfiltration and Command and Control (C2) communications. Our focus is on two anonymized customers: a large e-commerce/retail company (Customer #1) and an educational institution (Customer #2). This study shows how the use of both our Suspicious Domain feeds and our Threat Insight capability that inspects customer network DNS traffic can work to protect the enterprise.
The intriguing aspect of this proof of value study lies in the diverse decisions made by each customer, influenced by their unique security policies, and their utilization of various security capabilities provided by Infoblox.
Infoblox’s early identification of Suspicious Domains is a unique method for identifying potentially harmful domains. By employing our proprietary techniques, we can detect and flag Suspicious Domains early, offering cyber defenders a significant advantage over threat actors. These Suspicious Domain feeds are regularly updated based upon the information from Infoblox Threat Intel. This proactive approach enables defenders to block attacks days, weeks, or even months before they appear in Open Source Intelligence (OSINT) or threat intelligence feeds.
Another crucial capability offered by Infoblox is Threat Insight. This technology identifies potentially harmful domains involved in data exfiltration by inspecting customer DNS traffic using machine learning (AI). It helps identify risks and stop them within a customer specific context.. These algorithms, developed through extensive study and analysis of sample DNS statistics, can identify DNS tunneling data that normal rules and signatures cannot detect.
Sidewinder (aka Rattlesnake) Uses Custom Cobalt Strike Loader
The SideWinder threat actors have been causing problems for many years now. It appears that the SideWinder are likely culprits behind the activity we observed in both customer accounts. Our threat hunters have noted that the SideWinder threat group has not been previously reported as using DNS command and control. If you refer to, for example, https://attack.mitre.org/groups/G0121/ you will see that no DNS techniques are referenced and it is unclear when their use of DNS for command and control began.
MITRE ATT&CK identifies the SideWinder APT as being known under other identities such as Rattlesnake, Hardcore Nationalist (HN2), and T-APT4. SideWinder APT, believed to originate from India, has been observed targeting government, military, and business entities throughout Asia with emphasis on Afghanistan, China, Nepal, and Pakistan.1
In late 2022, the SideWinder APT group began backdoor malware in campaigns primarily targeting Pakistan. This malware includes several malicious modules that deliver a Cobalt Strike loader.
Cobalt Strike is a legitimate software tool. It was designed to simulate advanced cyberattacks and helps penetration testers and cybersecurity teams test the capabilities and resilience of their infrastructure. Cobalt Strike enables cyber defenders to simulate real threats in live attack which helps organizations identify vulnerabilities and improve defenses. Threat actors misuse Cobalt Strike to launch cyberattacks and breach networks.
Cobalt Strike can create beacons (remote agents), which enable remote code execution on the target system after initial access. Cobalt Strike beacons, which can be deployed as staged or stageless payloads can be configured. Cobalt Strike can deliver C2 commands and ready data for exfiltration if an unidentified malicious domain is involved in communications. Its adaptability allows threat actors to alter its components to resemble legitimate network traffic, thus avoiding detection. This enables various malicious activities such as malware distribution, unauthorized network access, privilege escalation, and more. Keep in mind, malicious traffic is encrypted, making it challenging to discern if it contains C2 command streams, data, or both.
Analysis
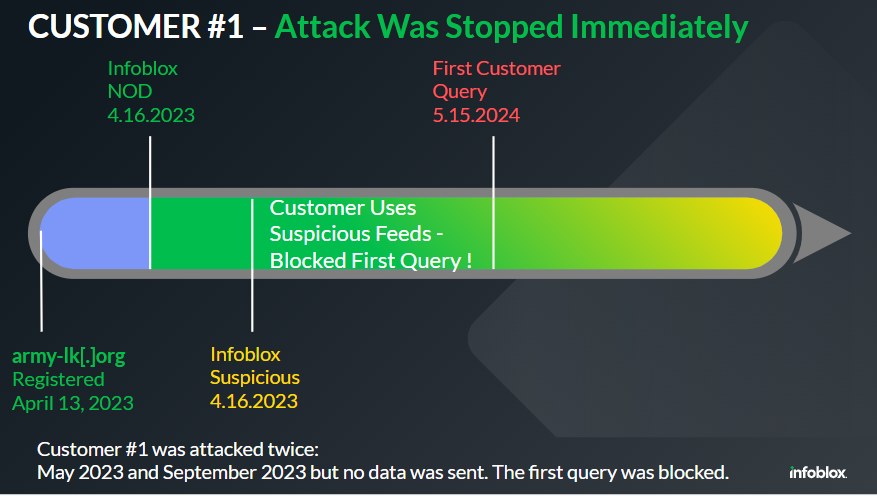
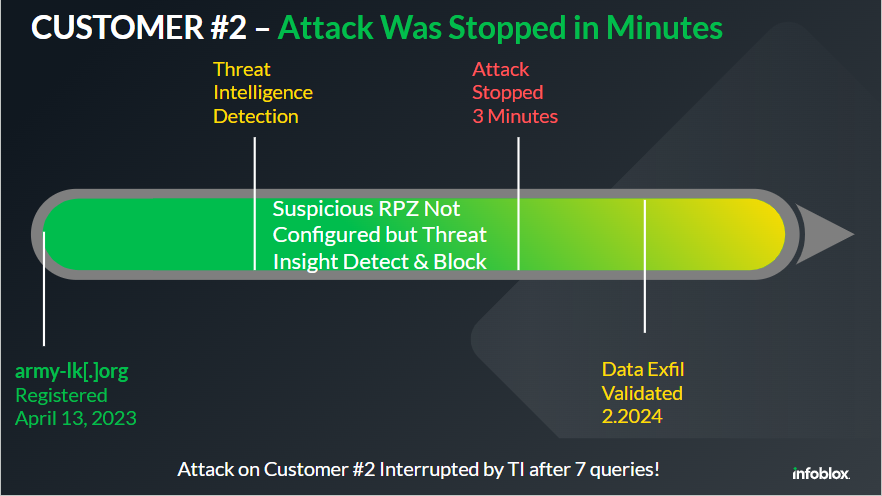
| Army-lk[.]org has been identified as a key indicator of compromise (IoC) for the SideWinder APT group. The domain army-lk[.]org is one of many domains now identified as malicious that have been associated with the Sidewinder APT by other threat researchers. Infoblox identified army-lk[.]org domain as Suspicious 3 days after the domain’s WHOIS registration. The domain was created on 4.13.2023 and then noted as Suspicious by Infoblox on 4.16.2023. |
Let’s take a look at how this data was used by the two customers. The customers were set up using different policy configurations.
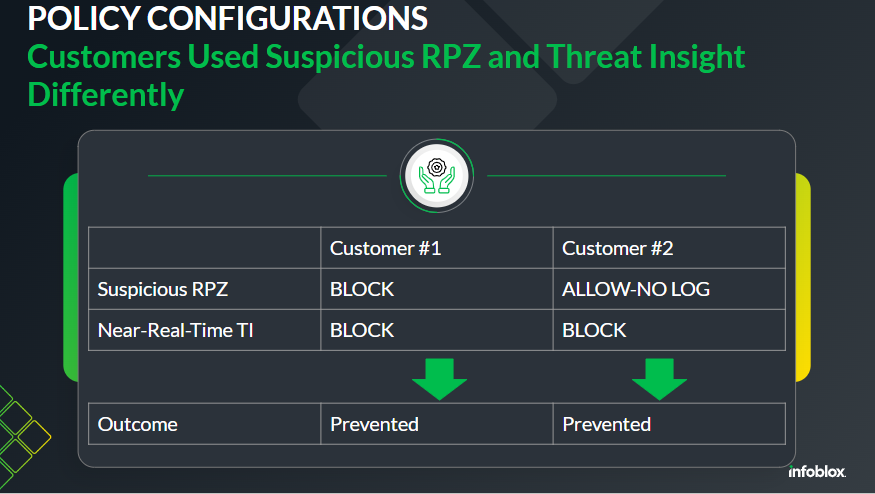
Customer #1 allowed for the use of Suspicious Domain feed data and blocked upon encountering traffic to a Suspicious Domain. Customer #1 also allowed for near real time blocking by Threat Insight. With this set of policies in place, the attack using army-lk[.]org was blocked immediately by use of the Suspicious RPZ feed.
Customer #2 allowed for the use of Threat Insight, but was not using Suspicious Domain data for blocking. In the case of Customer #2, the attack using the malicious domain army-lk[.]org was interrupted by Threat Insight after 7 queries. In context, this was just 7 packets of data.
Conclusions
To extract maximum value, this study suggests that a full implementation of both Suspicious Domain feeds and Threat Insight will help to optimize the DNS protection provided by Infoblox. Infoblox DNS Detection and Response (DNSDR) works with other security controls and your XDR Architecture as part of an overall modernized Defense-in-Depth strategy to help reduce risk.
Suspicious Domain feeds are an important part of this strategy. Suspicious Domain feeds can identify potentially malicious domains very early. This enables our customers to stop execution of the intended Cyber Kill Chain2 by automatically blocking access to these dangerous domains.
Threat Insight is deployed with BloxOne™ Threat Defense. Threat Insight detects and automatically blocks data exfiltration via DNS. It uses real-time streaming inspection of live customer DNS queries to accurately detect the presence of potential data exfiltration activity within data queries. Threat Insight also provides protection against DNSMessenger, DGA and fast flux.
By using both Infoblox’s Suspicious Domain data feed and Threat Insight, our customers can help protect themselves from a potentially disastrous data breach. Both of these tools can potentially lower risk and boost the ROI of your threat intelligence program.
For Additional Information
Infoblox Threat Intel provides fast access to accurate, contextual threat alerts and reports sourced from our own real-time research teams. Suspicious Domains feeds were introduced as an Infoblox proprietary product on November 10, 2022 and, since then, have successfully provided many thousands of customers with the advanced information to block domains which ultimately become malicious long before most other threat intelligence sources identify them as malicious. Infoblox allows your team to leverage the high value of suspicious domain threat intelligence while ensuring unified security policy across your entire security infrastructure. Infoblox threat data minimizes false positives, so you can be confident in what you are blocking.
To learn more about suspicious domains and DNS early detection:
https://www.infoblox.com/threat-intel/
To learn more about BloxOne Threat Defense:
https://www.infoblox.com/products/bloxone-threat-defense/
To learn more about Threat Insight:
https://insights.infoblox.com/resources-datasheets/infoblox-datasheet-threat-insight
To learn more about Advanced DNS Protection:
https://www.infoblox.com/products/advanced-dns-protection/
To learn more about the National Security Agency (NSA) and Cybersecurity & Infrastructure Security Agency (CISA) guidance on Protective DNS:
https://media.defense.gov/2021/Mar/03/2002593055/-1/-1/0/CSI_PROTECTIVE%20DNS_UOO117652-21.PDF
Footnotes
- https://attack.mitre.org/groups/G0121/
- https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html