Bulletin
Who:
- Cybersecurity threat researchers at TALOS discovered a new malicious cyber campaign operated by the threat group CoralRaider. Per the TALOS blog published in late April, the recent CoralRaider campaign operations appeared to have started in February 2024. This campaign was used to deliver a variety of malware that used DNS for command and control (C2).
What:
- CoralRaider appears to be distributing several types of infostealer malware, including Rhadamanthys, Lumma C2, and Cryptbot. The LUMMA C2 domains (see our previous blog on Lumma C2) we identified with our SUSPICIOUS domain algorithms in late 2023 seem to have been augmented by new and dangerous malicious C2 domains.
- Threat researchers believe that CoralRaider uses the Content Delivery Network (CDN) to host malicious files and payloads. CDNs generally include a network of proxy servers and data centers that deliver content from media and e-commerce companies to users with improved performance and availability. These CDN servers are hosted in ISP data centers.
- Unfortunately, the CDN-hosted malicious content and the malicious domains employed are critical parts of a cleverly camouflaged Kill Chain. Using a CDN to store and download malicious files obfuscates the malicious intent from potential victims.
Infoblox Capability:
- Infoblox DNS Early Detection identified both key CoralRaider C&C domains as SUSPICIOUS days to months ahead of availability in OSINT as MALICIOUS.
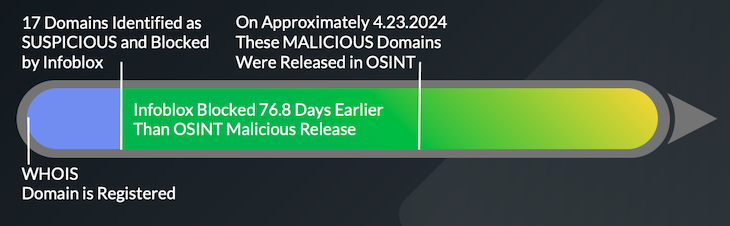
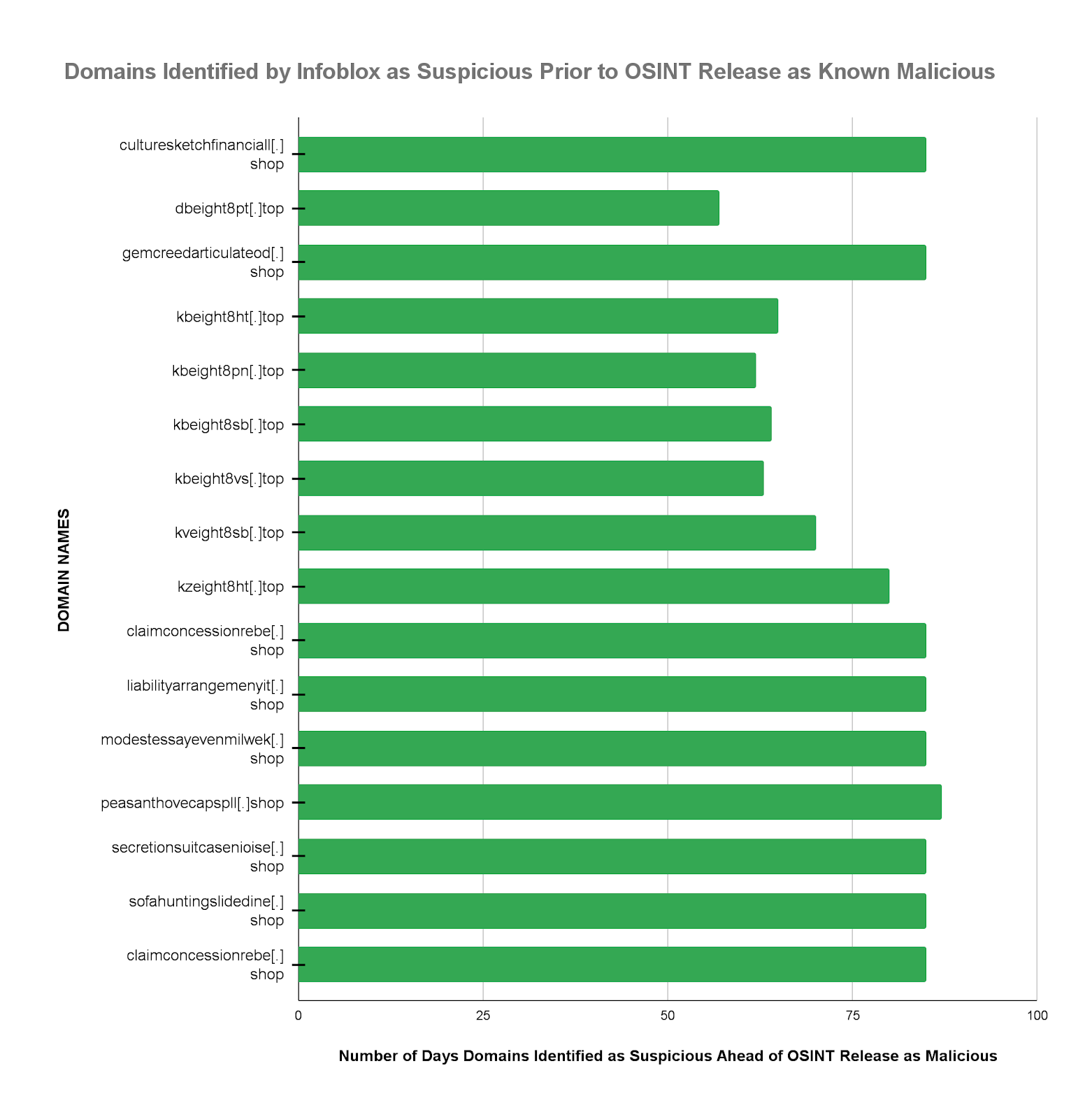
- Infoblox identified and blocked 94.12% of the CoralRaider MALICIOUS domains shortly after registration and an average of 76.8 days earlier than OSINT availability.
- MALICIOUS CoralRaider C2 domains identified as SUSPICIOUS include:
| culturesketchfinanciall[.]shop |
| dbeight8pt[.]top |
| gemcreedarticulateod[.]shop |
| kbeight8ht[.]top |
| kbeight8pn[.]top |
| kbeight8sb[.]top |
| kbeight8vs[.]top |
| kveight8sb[.]top |
| kzeight8ht[.]top |
| claimconcessionrebe[.]shop |
| liabilityarrangemenyit[.]shop |
| modestessayevenmilwek[.]shop |
| peasanthovecapspll[.]shop |
| riangleseasonbenchwj[.]shop |
| secretionsuitcasenioise[.]shop |
| sofahuntingslidedine[.]shop |
| claimconcessionrebe[.]shop |
Infoblox Impact:
- Infoblox customers running in blocking mode using our SUSPICIOUS feed were protected from CoralRaider Kill Chains using these malicious domains.
- Infoblox identified that several of its customers had these domains in their traffic and were protected. These customers were saved from the theft of confidential information, fines, and other legal impacts.
- Our suspicious domain feeds could be used to automatically block these malicious domains, which resulted in breaking multiple attack Kill Chains across our worldwide customer base.
- Infoblox SUSPICIOUS domain data is HIGH VALUE, can be used with relatively LOW EFFORT, and can SHRINK THE TIME TO VALUE and INCREASE THE RETURN ON INVESTMENT for your threat intelligence program.
Recommended Action:
Click here to connect with Infoblox and assess your security posture.
Detailed Analysis And Methodology:
This blog section delves into our detailed data analysis process and methodology. OSINT publication sources released disclosures on CoralRaider in February 2024, providing a comprehensive list of malicious domains.
Infoblox then extracted malicious domains identified within these OSINT sources. The Infoblox team then analyzed the identified malicious domains to determine whether they had been identified earlier by our suspicious domain feeds.
| Infoblox identified 94.12% of the CoralRaider MALICIOUS domains as SUSPICIOUS, an average of 76.8 days earlier than OSINT availability. Similarly, Infoblox identified many malicious domains within 2 to 3 days of their WHOIS registration. This enabled our customers to stop the execution of the intended Cyber Kill Chain1 by automatically blocking access to these dangerous domains. |
Our team researched each malicious domain identified in OSINT in the Infoblox Dossier portal. We reviewed our timeline feature to extract the earliest dates associated with Infoblox’s suspicious designation. We also extracted the WHOIS information for additional context.
The CoralRaider threat was active before the OSINT data was released. Our early identification of these domains has provided compelling timeline data. Our team found that, in many cases, the threat actors were already ramping up activity shortly after our suspicious designations and long before visibility to the public at large via OSINT availability.
| Several dangerous domains in our data cloud were queried and blocked within a few days to a few weeks after our initial SUSPICIOUS designation. So, the threat actors were active and likely successful many months before the availability of OSINT information unless you were using Infoblox Threat Intel SUSPICIOUS domain feeds. |
The conclusions of our analysis illustrate the potential benefits of suspicious domain feeds:
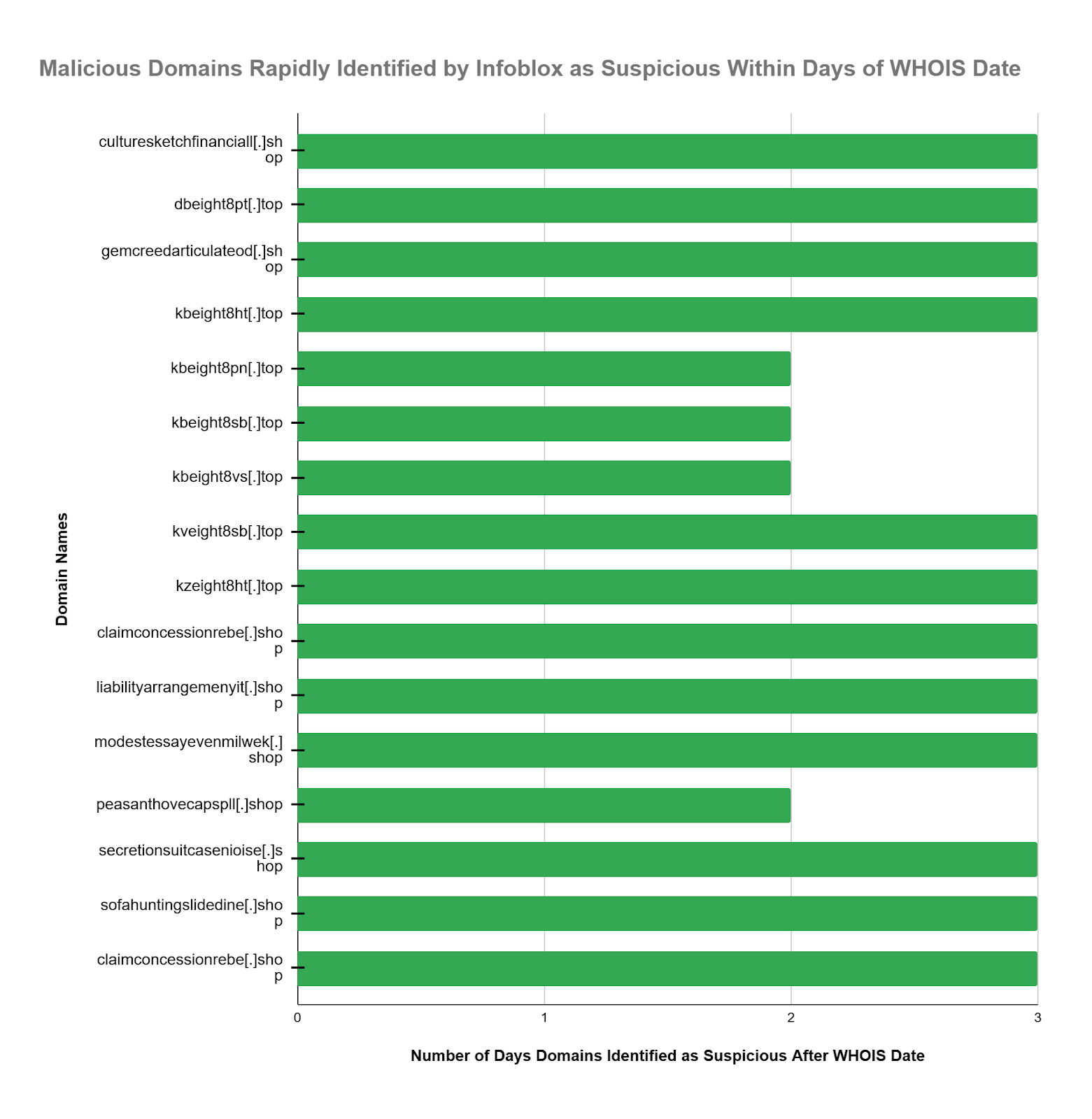
- 94.12% of the CoralRaider domains were identified as suspicious by Infoblox an average of 76.8 days (2.52 months) before the OSINT designation as malicious became available. This same domain group was identified within 2 to 3 days after the WHOIS domain registration date.
- Our DNS early detection program identifies suspicious domains weeks to months, as in this case, ahead of OSINT identification as malicious.
- There is often an extended period of time from availability via OSINT to utilization by your cybersecurity ecosystem and defense-in-depth strategy. Infoblox Threat Intel designation of suspicious domains can link to automation to block them immediately.
OSINT publication dates may sometimes be unclear or lack precision. The dates of published articles by reputable 3rd parties may not always accurately reflect the OSINT availability of each domain. The critical point is that even if you have the OSINT data, it must propagate through the threat feeds you use and your cybersecurity ecosystem to support actionable policies. All of that is automated with Infoblox DNS Detection and Response (DNSDR) and our suspicious domain data.
Comparison To Whois Data
WHOIS data draws a line in the sand and gets you as close as possible to hard data. A comparison with WHOIS data tells you how your threat intelligence systems work. To provide context on the performance of our suspicious threat intel feeds, we extracted WHOIS dates and found that all of the CoralRaider domains were blocked as suspicious within 2 to 3 days after the WHOIS domain registration date. The WHOIS dates are relatively precise and provide another perspective on the high value and relative performance of suspicious DNS threat intel feed content.
The threat actors behind most campaigns have learned to continually create and change the domains they use to camouflage their malicious activities. New domains are issued every day. Any of the key domains used in perpetuating the CoralRaider campaigns may be shut down at any time and replaced with new infrastructure. Infoblox DNS Early Threat Detection gives your cyber defenders an important advantage.
Infoblox Threat Intel’s DNS Early Detection Program
Infoblox Threat Intel’s DNS Early Detection Program uses proprietary techniques to identify potentially MALICIOUS domains much faster than other technologies. Infoblox flags these domains as SUSPICIOUS so your defenders can automatically block them, often weeks to months before OSINT designates them as malicious.
Infoblox Threat Intel can detect these malicious domains early, long before they are available in Open Source Intelligence (OSINT) or commercial feeds as malicious. We flag these domains as SUSPICIOUS at the earliest stage and make them available for immediate blocking. By taking this proactive approach, defenders can stop attacks days, weeks, or even months before they appear in OSINT or threat intelligence feeds.
Threat actors continually adjust their techniques and often use malicious domains to launch damaging and dangerous attacks quickly. Once that link to a malicious domain is clicked, the Kill Chain can rapidly unfold to the detriment of the defenders. These malicious domains are often detected and shared too late by OSINT and threat intel feeds.
Go Faster With Infoblox
Infoblox DNS Early Detection using our suspicious feeds can help your SOC quickly identify and block potentially dangerous threats such as CoralRaider. Infoblox Threat Intel proprietary technology can detect suspicious domains faster than the industry’s current methods.
| Infoblox SUSPICIOUS domain data helps your SOC team make better and faster decisions and can help protect your organization from a disastrous data breach. |
Suspicious domain feeds provide a significant advantage in developing and using DNS threat intelligence information. With Infoblox’s suspicious domain data, security operations teams can get the timely information they need to prevent and counter new threats before they do any damage.
For Additional Information
The Infoblox Threat Intel Group provides fast access to accurate, contextual threat alerts and reports from our real-time research teams. Suspicious Domains feeds were introduced as an Infoblox proprietary product on November 10, 2022, and, since then, have successfully provided many thousands of customers with the advanced information to block domains that ultimately become malicious long before most other threat intelligence sources identify them as malicious. Infoblox allows your team to leverage the high value of suspicious domain threat intelligence while ensuring a unified security policy across your entire security infrastructure. Infoblox threat data minimizes false positives, so you can be confident in what you are blocking.
| Infoblox SUSPICIOUS domain data is HIGH VALUE, can be used with relatively LOW EFFORT, and can SHRINK THE TIME TO VALUE and INCREASE THE RETURN ON INVESTMENT for your threat intelligence program. |
To learn more about suspicious domains and DNS early detection:
https://www.infoblox.com/threat-intel/
To learn more about BloxOne Threat Defense:
https://www.infoblox.com/products/bloxone-threat-defense/
To learn more about Advanced DNS Protection:
https://www.infoblox.com/products/advanced-dns-protection/
To learn more about the National Security Agency (NSA) and Cybersecurity & Infrastructure Security Agency (CISA) guidance on Protective DNS:
https://media.defense.gov/2021/Mar/03/2002593055/-1/-1/0/CSI_PROTECTIVE%20DNS_UOO117652-21.PDF
OSINT sources on CORALRAIDER included, but were not limited to:
https://www.bleepingcomputer.com/news/security/coralraider-attacks-use-cdn-cache-to-push-info-stealer-malware/ published on 4.23.2024.
Footnotes
- https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html Cyber Kill Chain is a registered trademark of Lockheed Martin.