Bulletin
Who:
- The FBI, CISA, HHS, and MS-ISAC have jointly issued a cybersecurity alert about Black Basta ransomware. This ransomware variant has affected at least 12 of the 16 critical infrastructure sectors, including a high impact on the Healthcare and Public Health Sectors. Per the CISA report on the surge in ransomware attacks, BlackBasta is one of the top 5 most prevalent ransomware variants observed in healthcare attacks in 2023
- Identified first in April 2022, Black Basta is a dangerous ransomware-as-a-service variant. It has significantly impacted businesses and critical infrastructure across North America, Europe, and Australia. As of May 2024, 500+ global organizations have been affected by Black Basta affiliates.
- Infoblox published an earlier blog entitled Black Basta Anatomy of the Attack which was published in May, 2023. We have been aware of the activities of Black Basta for some time.
What:
- Black Basta affiliates typically gain initial access through phishing and exploiting known vulnerabilities, then use a double-extortion model to encrypt systems and exfiltrate data. Rather than including ransom demand or payment instructions, ransom notes provide victims with a unique code and direct them to contact the group via a .onion URL accessible through the Tor browser. Victims usually have 10 to 12 days to pay the ransom before their data is published on the Black Basta TOR site, Basta News.
- Due to their size, reliance on technology, access to personal health data, and the significant impact of disruptions to patient care, healthcare organizations are prime targets for the Black Basta cybercriminals. The issuing organizations strongly recommend that the Healthcare and Public Health sectors and all critical infrastructure entities implement the mitigation strategies outlined in this Cybersecurity Alert to decrease the risk of compromise from Black Basta and similar ransomware attacks.
Infoblox Capability:
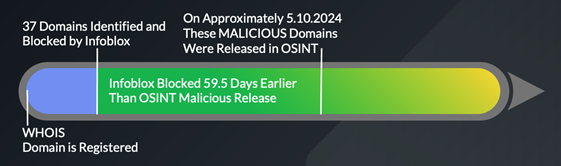
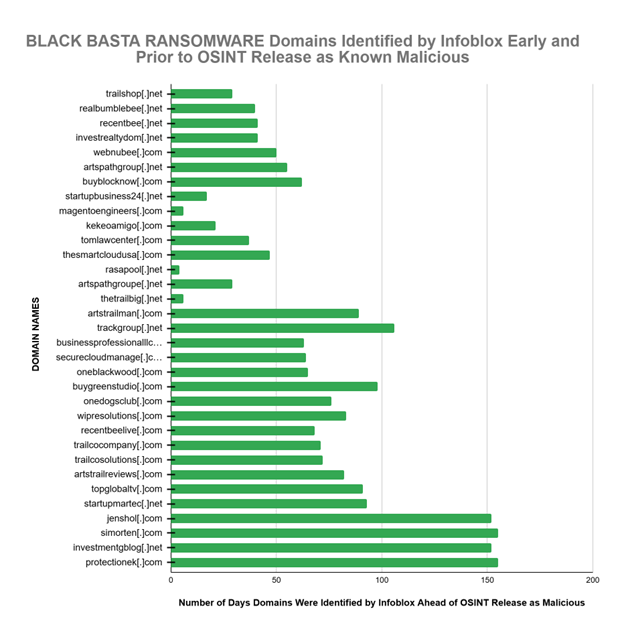
- Infoblox DNS Early Detection identified key Black Basta ransomware domains shortly after registration and days to months ahead of availability in OSINT as MALICIOUS.
- Infoblox identified and blocked 37 domains—78 % of the Black Basta ransomware MALICIOUS domains—an average of 59.5 days earlier than OSINT availability.
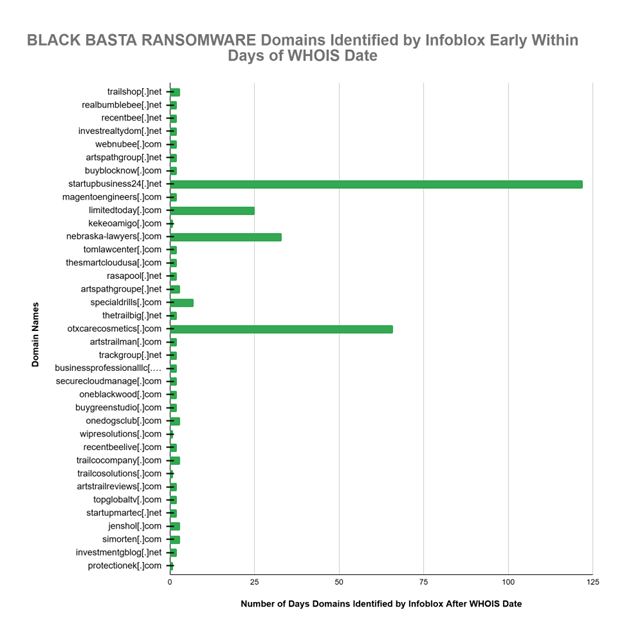
- Similarly, Infoblox identified and blocked many Black Basta ransomware MALICIOUS domains within 2 to 3 days of their WHOIS registration.
- Here are the Black Basta malicious domains identified early, including two LOOKALIKE domains:
| trailshop[.]net | artstrailman[.]com |
| realbumblebee[.]net | trackgroup[.]net |
| recentbee[.]net | businessprofessionalllc[.]com |
| investrealtydom[.]net | securecloudmanage[.]com |
| webnubee[.]com | oneblackwood[.]com |
| artspathgroup[.]net | buygreenstudio[.]com |
| buyblocknow[.]com | onedogsclub[.]com |
| startupbusiness24[.]net | wipresolutions[.]com |
| magentoengineers[.]com | recentbeelive[.]com |
| limitedtoday[.]com | trailcocompany[.]com |
| kekeoamigo[.]com | trailcosolutions[.]com |
| nebraska-lawyers[.]com | artstrailreviews[.]com |
| tomlawcenter[.]com | topglobaltv[.]com |
| thesmartcloudusa[.]com | startupmartec[.]net |
| rasapool[.]net | jenshol[.]com |
| artspathgroupe[.]net | simorten[.]com |
| specialdrills[.]com | investmentgblog[.]net |
| thetrailbig[.]net | protectionek[.]com |
| otxcarecosmetics[.]com |
Infoblox Impact:
- Infoblox customers running in blocking mode using our high-risk feeds were protected from the Black Basta ransomware campaign.
- Infoblox identified that multiple customers had these domains in their traffic and were automatically protected. These customers were saved from the theft of confidential information, fines, and other legal impacts.
- Our feeds could be used to automatically block these malicious domains, which resulted in breaking multiple attack Kill Chains across our worldwide customer base.
- Infoblox Threat Intel is HIGH VALUE, can be used with relatively LOW EFFORT and can SHRINK THE TIME TO VALUE and INCREASE THE RETURN ON INVESTMENT for your threat intelligence program.
Recommended Action:
Click here to be connected with Infoblox to assess your security posture.
Analysis And Methodology:
The CISA alert released disclosures on Black Basta ransomware in May 2024 with detailed malicious domain listings. Infoblox then extracted malicious domains identified within the CISA alert and other sources. The Infoblox team then analyzed the malicious domains that had been identified earlier by our feeds to determine whether they had been identified earlier.
We used our lookalike domain technology to identify domains earlier than OSINT availability in two instances. An lookalike domain is designed to resemble a legitimate domain, often used in cyber attacks. Cybercriminals create these malicious domains to deceive users into thinking they are interacting with a trusted entity. This can lead to phishing, malvertising, and other similar attacks.
| Infoblox identified 78.72% of the Black Basta ransomware MALICIOUS domains an average of 59.5 days earlier than OSINT availability. This enabled our customers to stop the execution of the intended Cyber Kill Chain1 by automatically blocking access to these dangerous domains. |
Our team researched each malicious domain identified in OSINT in the Infoblox Dossier portal. We reviewed our timeline feature to extract the earliest dates associated with Infoblox’s high-risk designation. We also extracted the WHOIS information for additional context.
The Black Basta ransomware threat was active before the CISA alert OSINT data was released. Our early identification of these domains has provided compelling timeline data. Our team found that, in many cases, the threat actors were already ramping up activity shortly after we included them in our feeds and long before visibility to the public at large via OSINT availability.
| Several dangerous domains in our data cloud were queried and blocked within days to a few weeks after we included them in our feeds. So, the threat actors were active and likely successful many months before the availability of OSINT information unless you were using Infoblox Threat Intel feeds. |
The conclusions of our analysis illustrate the potential benefits of Infoblox Threat Intel feeds:
- 78.72% of the Black Basta ransomware domains were identified as high risk by Infoblox an average of 59.5 days (1.96 months) before the OSINT designation as malicious became available. Except for only four (4) domains, this same group of domains was identified within 2 to 3 days after the WHOIS domain registration date.
- Our DNS early detection program identifies high-risk domains weeks to months ahead of OSINT’s identification as malicious.
OSINT publication dates may sometimes be unclear or lack precision. The dates of published articles by reputable 3rd parties may not always accurately reflect the OSINT availability of each domain. The critical point is that even if you have the OSINT data, it must propagate through the threat feeds you use and your cybersecurity ecosystem to support actionable policies. This is all automated with Infoblox DNS Detection and Response (DNSDR) and our threat intel data.
Comparison To Whois Data
WHOIS data draws a line in the sand and gets you as close as possible to hard data. A comparison with WHOIS data tells you how your threat intelligence systems work. To provide context on the performance of our threat intel feeds, we extracted WHOIS dates and found that almost all of the Black Basta ransomware domains were blocked within 2 to 3 days after the WHOIS domain registration date. The WHOIS dates are relatively precise and provide another perspective on the high value and relative performance of DNS threat intel feed content.
The threat actors behind most campaigns have learned to continually create and change the domains they use to camouflage their malicious activities. New domains are issued every day. Any key domains used in perpetuating the Black Basta ransomware campaigns may be shut down at any time and replaced with new infrastructure. Infoblox DNS Early Threat Detection gives your cyber defenders an important advantage.
MITRE ATT&CK TACTICS AND TECHNIQUES USED BY BLACK BASTA
| BLACK BASTA MITRE ATT&CK Tactics and Techniques |
||
| Initial Access | ||
| Phishing | T1566 | Black Basta affiliates have used spear phishing emails to obtain initial access. |
| Exploit Public-Facing Application | T1190 | Black Basta affiliates have exploited ConnectWise vulnerability CVE-2024-1700 to obtain initial access. |
| Privilege Escalation | ||
| Exploitation for Privilege Escalation | T1068 | Black Basta affiliates have used credential scraping tools like Mimi Katz, ZeroLogon, NoPac and printNightmare for privilege escalation. |
| Defense Evasion | ||
| Masquerading | T1036 | Black Basta affiliates have conducted reconnaissance using utilities with innocuous file names, such as Intel or Dell, to evade detection. |
| Impair Defenses: Disable or Modify Tools | T1562.001 | Black Basta affiliates have deployed a tool called Backstab to disable endpoint detection and response (EDR) tooling. Black Basta affiliates have used PowerShell to disable antivirus products. |
| Execution | ||
| Command and Scripting Interpreter: PowerShell | T1059.001 | Black Basta affiliates have used PowerShell to disable antivirus products. |
| Impact | ||
| Inhibit System Recovery | T1490 | Black Basta affiliates have used the vssadmin.exe program to delete shadow copies. |
| Data Encrypted for Impact | T1486 | Black Basta affiliates have used a public key to encrypt files fully. |
Infoblox Threat Intel for Early Threat Detection
Infoblox Threat Intel uses proprietary techniques to identify potentially malicious domains much earlier than other technologies. Infoblox flags these domains as high risk so your defenders can automatically block them, often weeks to months before OSINT designates them malicious.
By taking this proactive approach, defenders can stop attacks days, weeks, or even months before they appear in OSINT or threat intelligence feeds.
Threat actors continually adjust their techniques and often use malicious domains to quickly launch damaging and dangerous attacks. Once that link to a malicious domain is clicked, the Kill Chain can rapidly unfold to the detriment of the defenders. These malicious domains are often detected and shared too late by OSINT and threat intel feeds
For Additional Information
Infoblox Threat Intel provides fast access to accurate, contextual threat alerts and reports from our real-time research teams. High-Risk Domains feeds were introduced as an Infoblox proprietary capability on November 10, 2022, and, since then, have successfully provided many thousands of customers with the advanced information to block domains that ultimately become malicious long before most other threat intelligence sources identify them as malicious. Infoblox allows your team to leverage the high value of DNS-based threat intelligence while ensuring a unified security policy across your entire security infrastructure. Infoblox threat data minimizes false positives, so you can be confident in what you are blocking.
| Infoblox Threat Intel data is HIGH VALUE, can be used with relatively LOW EFFORT, and can SHRINK THE TIME TO VALUE and INCREASE THE RETURN ON INVESTMENT for your threat intelligence program. |
To learn more about Infoblox Threat Intel and DNS early detection:
https://www.infoblox.com/threat-intel/
To learn more about BloxOne Threat Defense:
https://www.infoblox.com/products/bloxone-threat-defense/
To learn more about the National Security Agency (NSA) and Cybersecurity & Infrastructure Security Agency (CISA) guidance on Protective DNS:
https://media.defense.gov/2021/Mar/03/2002593055/-1/-1/0/CSI_PROTECTIVE%20DNS_UOO117652-21.PDF
OSINT sources on Black Basta ransomware included, but were not limited to:
https://www.cisa.gov/news-events/cybersecurity-advisories/aa24-131a
To reference our earlier blog on Black Basta published in May 2023:
https://blogs.infoblox.com/threat-intelligence/black-basta-anatomy-of-the-attack/