Executive Summary
One typically imagines the digital underworld—trojans, malware droppers, fake dating sites, investment scams, and more—as operating in the dark corners of the internet. But increasingly, these threats are hiding in plain sight, camouflaged by the glossy veneer of mainstream digital advertising. In some cases, the adtech platforms are abused, but we have uncovered an increasing number of adtech companies that are either complicit or actively engaged in the distribution of malicious content. Cybercriminals aren’t just exploiting adtech platforms, sometimes, they are the adtech platforms.

There’s a recipe for running malicious campaigns through adtech, and it starts with plausible deniability. Add in convoluted corporate structures, stir in opaque ownership, and you’ve got the perfect conditions for a profitable lack of accountability. These ingredients don’t just make abuse possible; they make it sustainable. The more tangled the web of shell companies, the less visibility there is into the operation, and the harder it becomes to assign blame or trace responsibility, which, of course, is by design.
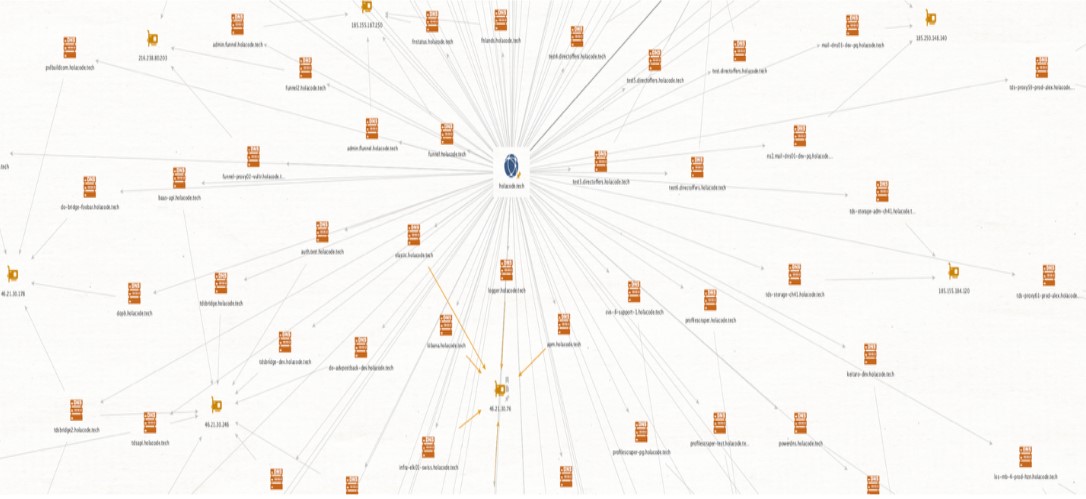
One such actor, Vane Viper, has appeared in approximately half of our customer networks and has accounted for about 1 trillion DNS queries over the past year, making it one of the most prevalent threat actors we observe. Vane Viper benefits from hundreds of thousands of compromised websites and ads inserted into blogs, gaming, and shopping sites worldwide.
Corporate filings and WHOIS data trace Vane Viper to AdTech Holding, a Cypriot holding company. Their flagship subsidiary, PropellerAds, acts as an advertising network and traffic broker, sourcing traffic from multiple channels, including compromised websites, and routing clicks through its traffic distribution system (TDS) to malicious pages. Although PropellerAds has been implicated in malvertising campaigns by others in the past, proving that they have crossed the line from abused service to complicit enabler has been challenging.1,2,3,4,5 We didn’t come to our conclusions lightly.
For months we debated internally and sought the perspective of other researchers in the security community like Guardio and Confiant, as well as advertising experts like Augustine Fou. Ultimately, we found compelling evidence that not only has PropellerAds turned a “blind eye” to criminal abuse of their platform, but indicators described below suggest—with moderate-to-high confidence—that several ad-fraud campaigns originated from infrastructure attributed to PropellerAds. We have not independently verified that PropellerAds personnel directed these campaigns. When security researchers have previously implicated PropellerAds in malvertising campaigns in the past, Propeller’s standard reply frames findings as “libel” while dismissing responsibility for downstream harm.
Peeling back the layers of ownership and sorting through the shell games AdTech Holding plays, reveal why deniability thrives. Vane Viper’s registrar of choice, URL Solutions/Pananames, belongs to CloudOne Digital, who acquired XBT Holdings and their subsidiaries Servers.com and Webzilla. PropellerAds owns multiple Webzilla subnets outright and Webzilla itself has a checkered past: its infrastructure was used for the Methbot click-fraud farm, Russia’s Doppelgänger disinformation sites, and piracy giant 4shared. Our investigation also uncovered a slew of executives with a history of providing services to fraudsters and financial ties to a Russian oligarch. In the end, the deeper we dug, the clearer it became that plausible deniability isn’t a flaw in the system, but a feature.
This paper provides an in-depth view of Vane Viper, their malicious operations, and their impact as seen via DNS traffic. Combining our research with that of Guardio, GoSecure, and others, we can show that:
- Shared infrastructure and personnel ties connect Vane Viper to Webzilla/XBT, convicted fraudsters, and Russian oligarchs, blending ostensibly legal adtech with infrastructure and people repeatedly cited for ad fraud, piracy, disinformation, pornography, and gambling traffic (See Figure 1).
- Vane Viper has provided core infrastructure in widespread malvertising, ad fraud, and cyberthreat proliferation for at least a decade.
- Vane Viper not only brokers traffic for malware droppers and phishers, but appears to run their own campaigns, consistent with previously documented ad-fraud techniques.
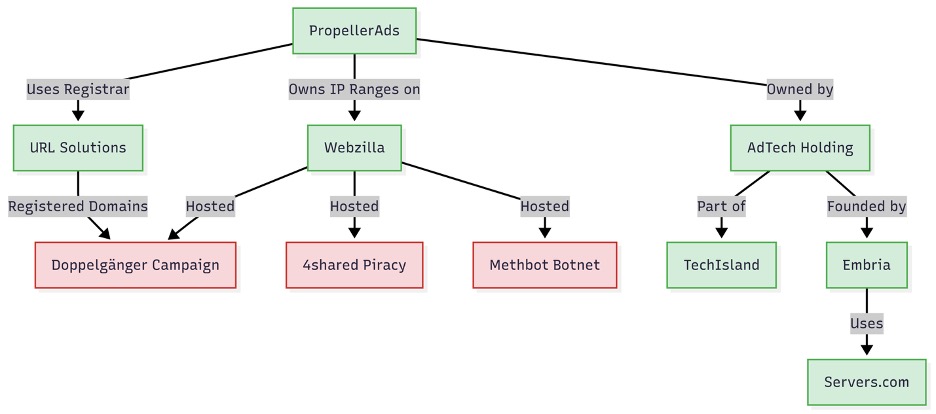
Figure 1. A diagram of key company relationships
The Tangled Web
The name “Vane Viper” denotes AdTech Holding, a Cyprus-based holding company of adtech and martech firms. PropellerAds, its most prominent subsidiary, gave us our first clear attribution point to Vane Viper infrastructure. What began as a single attribution soon unraveled into a far more intricate web of malicious adtech, gambling, piracy, pornography, disinformation, and more.
But first, some basics:
- PropellerAds enables publishers of content to monetize their websites with advertising and enables advertisers, who create and pay for ads, to promote their products or services. PropellerAds operates as both a supply-side and demand-side platform, giving them significant control over the supply chain
- Publishers are the owners or operators of websites, blogs, or apps that host advertisements. They provide the space where the ads are displayed, earning revenue based on the number of impressions, clicks, or conversions generated by the ads.
- Clicks are self-explanatory; however, impressions and conversions may not be. An impression is how often your ad is shown, whereas a conversion is an action resulting from an ad interaction and includes such things as answering questions or providing information.6,7
- Advertisers are businesses, individuals, or brands that want to promote their products, services, or content. They create ads and pay for them to be displayed to potential customers. Advertisers aim to reach a specific audience to drive traffic, generate leads, or increase sales. In the black hat world, however, advertisers engage in unethical or illegal practices to drop malware; steal credentials, personally identifiable information (PII), or payment information; or artificially inflate advertising revenue.
- Additionally, PropellerAds operates as a traffic broker, aggregating traffic from various sources (including third-party networks) and reselling it to advertisers. Traffic brokering allows advertisers access to a broad audience pool.

Figure 2. A diagram from PropellerAds displaying where they sit in the digital advertising ecosystem (Credit: PropellerAds)
PropellerAds ensures that ads are displayed to the right audience to maximize profit for advertisers. Think of them as a sort of advertising “post office” on the supply side, where they ensure that packages (advertisements) are delivered on time to the right recipients (publishers’ websites). Additionally, on the demand side, they offer services that act as “advertising ushers,” ensuring users are seamlessly redirected and routed to the most relevant advertisements upon clicking.
We currently assess that about 60,000 domains are part of Vane Viper’s infrastructure. These domains represent only a fraction of the broader ecosystem. TDSs can route users to a virtually unlimited number of downstream landing pages, most of which remain uncaptured. It is important to note that TDSs can also be used to serve legitimate advertising content to users—in fact, that industry is where the term “traffic distribution system” originated. Unfortunately, TDSs enable threat actors to deliver malicious content to the desired users, while intentionally diverting automated traffic, including tools used by security researchers, into dead ends. This is done in conjunction with cloaking kits, which are often tightly coupled to TDSs, but are separate. Vane Viper hides behind the plausible deniability of operating as an advertising network, while using their TDS to deliver multiple kinds of threats. Adtech’s fragmented structure and reliance on real-time bidding (RTB) makes plausible deniability inherent.8 Confiant’s Zirconium malvertising actor is another good example of how threat actors exploit the fragmentation across adtech’s demand and supply chains.9 With so many intermediaries across every step of the adtech supply chain, it’s easy for malicious actors to pose as legitimate players.
Corporate Structure and History
The “tangled web” we refer to is the network of intricate relationships between companies owned by AdTech Holding, and those they do business with, such as their webhost and domain registrar. AdTech Holding sits at the top of an investor portfolio that includes PropellerAds and at least four other companies:
- ProPushMe
- Zeydoo
- Notix
- Adex
Each of these companies play their own role in this adtech ecosystem, from managing push notifications to ostensibly identifying bot traffic. We have seen Notix, Adex, and ProPush domains alongside Vane Viper domains in many campaigns. Each of these companies can, and do, have their own subsidiaries. Monetag, another adtech company (but not a named part of AdTech Holdings), is a subsidiary of PropellerAds, as Figure 3 shows:
Figure 3. A screenshot of promo.monetag[.]com/page47501153.html, complete with PropellerAds branding and contact information
Propeller’s subsidiaries like Monetag attempt to obscure the link to their parent company. It was sheer luck to stumble across Figure 3; for a while we were operating under the assumption that Monetag was a separate, yet associated, firm. BeMob and RollerAds are good examples of what we mean by “separate but associated.” PropellerAds holds strategic partnerships with both companies. BeMob has advertised their partnership with PropellerAds since 2017. Guardio recently published research on the use of the BeMob TDS as a sort of proxy (wherein the campaign operator chained BeMob TDS after Vane Viper’s TDS, specifically Monetag) before delivering Lumma Stealer payloads.10 RollerAds was founded by a former manager at PropellerAds, and we currently believe it to be operating independently but would not be surprised if it is a subsidiary of PropellerAds.
If you are confused by the commercial relationships already, hang tight—it only gets more convoluted from here.
PropellerAds’ ownership history is complicated. It was founded as an independent company in London in 2011.11 One of the original directors of this first iteration of PropellerAds is Mardiros Haladjian. He appears in the Paradise Papers with a Cyprian address and as director of a Maltese company named Eldor Services.12 Malta is a known European gambling hub, which doesn’t seem to connect well to malicious adtech companies, until you dig a little deeper into Haladjian. In 2015, he was listed as the Respondent in a World Intellectual Property Organization (WIPO) domain dispute with EvoPlay LLP over Vulkan online casino domains.13 Strangely, Haladjian now seems to be the owner of EvoPlay, taking over after a series of ownership transitions between Belizean (likely shell) corporations.14 A few years later, in 2018, he was yet again named in another dispute related to Vulkan lookalike domains.15 This time, Haladjian was a co-respondent alongside Russian nationals who work at Global Domain Privacy Services Inc., also known as Pananames/URL Solutions (we’ll come back to them later). We know Haladjian is involved with online gambling in collaboration with Russian nationals, and he seems to favor the use of shell corporations in offshore tax havens (in the WIPO disputes, he is named as “Mardiros Haladjian, GGS Ltd. of Anguilla”); he also isn’t averse to serial cybersquatting. The decision in the 2018 WIPO suit found that the Vulkan lookalikes were registered in bad faith; the 2015 suit did not. Regardless of the potential violations of trademark law, these could very easily run afoul of gambling laws, especially in Russia, where gambling is almost entirely illegal.
But, like an old saloon owner, why stop at just gambling when there are more quick bucks to be made? Haladjian is also a director of Hammy Media Ltd., which is a Cyprus-based company that operates the major adult website xHamster.16 Hammy/xHamster have been in some hot water recently, with the state of Texas filing a lawsuit against them in 2024 for failure to properly enforce age verification.17 Additionally, Hammy was hit with a piracy lawsuit back in 2011, which they were able to get dismissed.18 Take note of the lawyer who represented Hammy in that case (and who represented Haladjian in his WIPO disputes): Valentin David Gurvits, of Boston Law Group PC. He’ll come up again later, as he appears to be the go-to lawyer for PropellerAds/AdTech Holding. Additionally, a Welt am Sonntag investigation in 2016 referenced that investigators have linked Haladjian to a German piracy ring; we were unable to verify that further.19
Whoever was bankrolling PropellerAds soon realized it probably wasn’t a good look to have a person with such a high-risk profile as Haladjian running the show, so they disbanded PropellerAds UK in July of 2014. They did, however, like shell games and tax havens, so PropellerAds popped up a few months later in the Isle of Man.20 Not much is known about this “branch” of PropellerAds because the Isle of Man masks corporate details and because a trust company handled the incorporation. The PropellerAds that we know best, PropellerAds Ltd. based in Cyprus, came about in March 2016 and now operates under AdTech Holding. The leadership at AdTech Holding and PropellerAds includes the following:
- Aleksandr Fedorov serves as PropellerAds’ CEO and sits on the AdTech Holding board.
- Alex Vasekin is the CEO of AdTech Holding.
- Igor Limbakh appears as a company director for both PropellerAds and AdTech Holding, and holds directorships at Samoukale Enterprises (Adex), Itpub, Finplat Technologies, Fourup, and others.
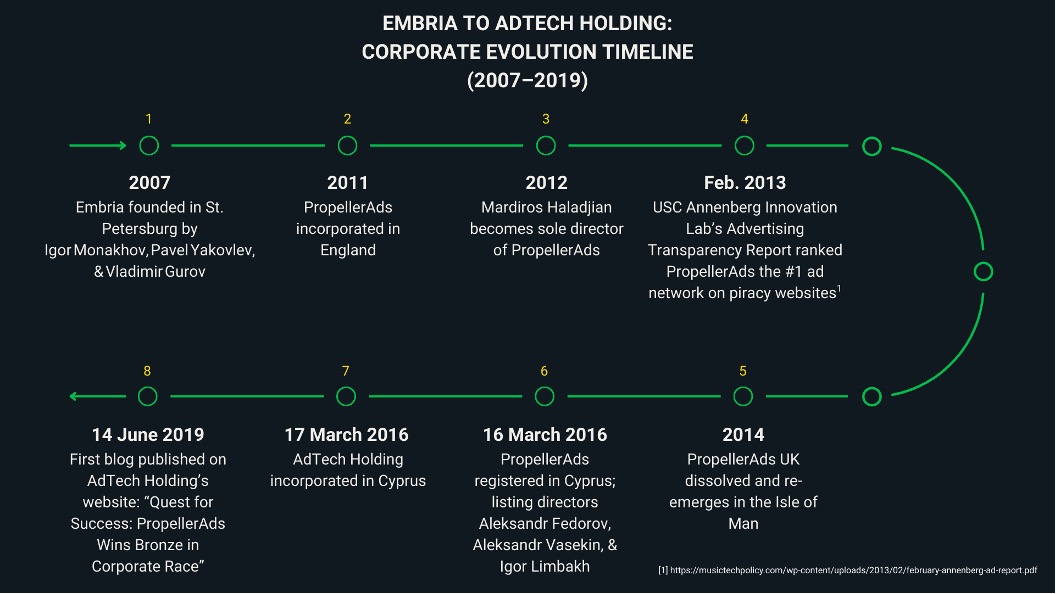
Figure 4. An overview of the timeline and evolution of Embria/PropellerAds/AdTech Holding
URL Solutions
AdTech Holding maintains suspicious ties to a web of related firms. Their preferred registrar is URL Solutions, also known as Pananames. These are the same folks named as a co-respondent with the original director of PropellerAds (Mardiros Haladjian), in one of the Vulkan cybersquatting domain disputes. As of April 1, 2025, URL Solutions ranked third-riskiest registrar via our reputation scoring algorithm (see Figure 4).21 URL Solutions moved up from eighth-riskiest registrar in February 2025 to third in March 2025 (cue Curtis Mayfield’s “Move On Up”—the extended version, please).
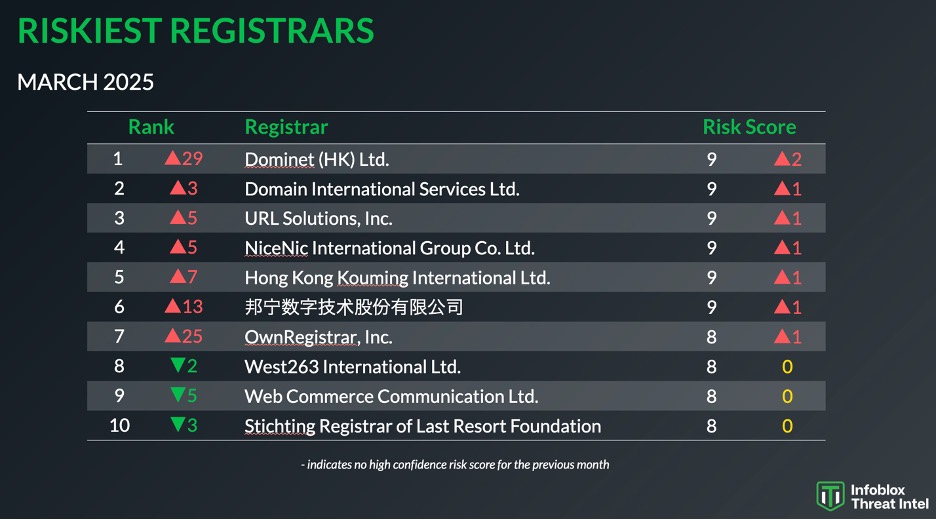
Figure 5. The ten riskiest registrars in March 2025 via our reputation algorithm
In their 2024 “Phishing Landscape” report, Interisle Consulting Group clocked URL Solutions as the third-highest registrar associated with bulk domain registration.22 Bulk domain registrations are often suspicious in nature. A high volume of domains registered in a brief period can indicate an intention to quickly use and dispose of them, which is behavior we commonly see in cybercrime. Per Interisle, the number of bulk registration sets and the number of domains in each set, are undercounted because their research was constrained to domains that had been specifically reported for phishing. Using their definition of bulk registration (at least ten domains through the same registrar with less than ten minutes between consecutive domain registrations), we specifically looked at URL Solutions’ bulk registration events since January 1, 2023. Vane Viper accounts for nearly half of all bulk registration events made through URL Solutions since January 2023.
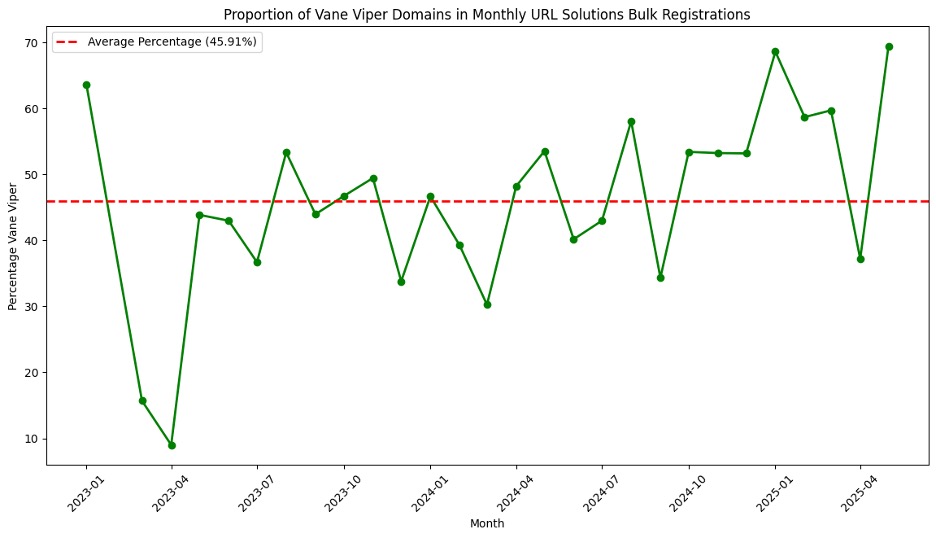
Figure 6. Monthly proportion of Vane Viper in URL Solutions bulk registration events
URL Solutions purports to be founded and operating in Panama. However, it is noteworthy that their privacy policy lists an address in Cyprus, just a seven-minute drive from PropellerAds’ office.
URL Solutions is owned by CloudOne Digital, which also owns Webzilla, Servers.com, and virtual private server (VPS) provider Fozzy. The CEO of both Fozzy and URL Solutions is Dmitry Filatov, whose LinkedIn lists him as “Head of B2C” at XBT Holdings until April 2023.23,24 CloudOne’s ASN, 35415, which is operated by Webzilla B.V., reports that multiple /24s are assigned to both PropellerAds and Fozzy, which further tightens the infrastructure overlap.25
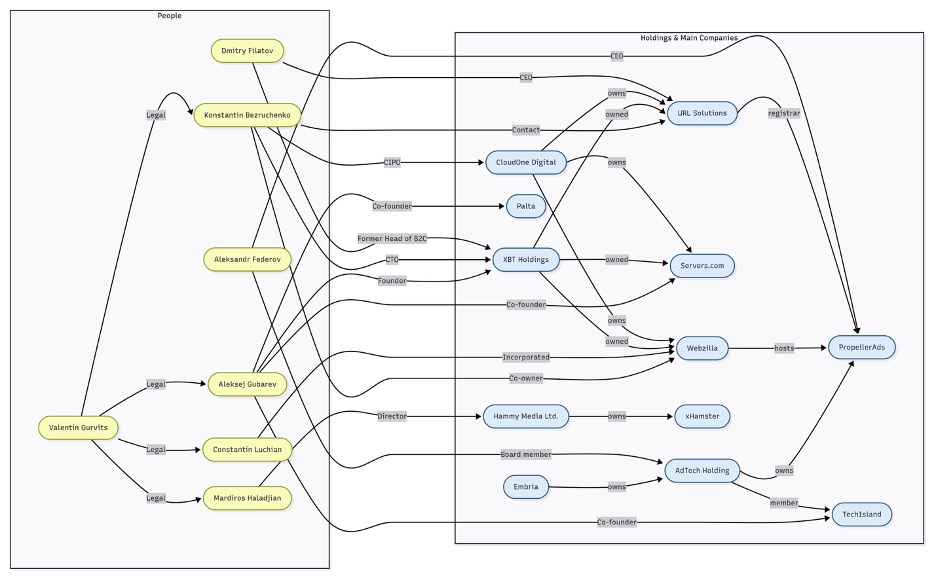
Figure 7. A diagram of relationships between notable people and companies in the Vane Viper ecosystem
XBT Holdings
This infrastructure overlap isn’t merely a technical convenience. At minimum, it provides ideal conditions for actors who benefit from ambiguity, such as malicious adtech, to operate without clear accountability. XBT Holdings, the former parent of Webzilla and the organization that acquired the domain name Servers.com in 2013, was founded by Aleksej/Aleksey/Alexey Gubarev.26,27
Gubarev (shown in Figure 7, and later in Figure 8) has been a staple on the Cyprus tech scene since 2002. Gubarev co-founded a health tech company named Palta in 2016. In 2019, according to a representative for Gubarev, Alex Frolov, the son of U.K.-sanctioned oligarch Aleksandr Frolov,28,29 joined Palta as another co-founder. Corporate filings and press releases name Gubarev and Alex Frolov as Palta co-founders. Target Global, the venture capital firm Frolov Jr. also founded, confirmed that Frolov Sr. and another sanctioned oligarch, Alexander Abramov, were early limited partners.30,31 Gubarev is on the board of directors and co-founded TechIsland, a tech incubator dedicated to accelerating Cyprus’ tech industry.32 TechIsland lists AdTech Holding (and Adsterra, another adtech company with ties to malvertising and malware propagation) as a member. AdTech Holding is owned by Embria, a holding company that has historically used Servers.com infrastructure (185.106.140.1/24) for the hosting of their websites embria[.]com and embria[.]one. AdTech Holding’s own blog from April 2024 credits “the vision of Alexey Gubarev” in helping to launch the Limassol skate park, a project AdTech Holdings also took part in.33 Some media outlets have alleged that Gubarev played a role in facilitating the presence of Russian information technology businessmen reportedly linked to sanctions evasion, claiming that Cyprus has become a base for extending Moscow’s influence in the European Union.34,35 At some point, these aren’t innocent business coincidences, or simply a measure of the goodwill emanating from TechIsland. Gubarev’s ties to sanctioned oligarchs, coupled with his incubator’s embrace of adtech companies linked to malware and fraud, demonstrate a blurring of ethical lines for commercial gain.
XBT Holdings is privately held, so ownership stakes are unavailable. What is apparent, however, is that this is another shell game. Since 2012, Cyprian corporate filings show that “XBT’s shareholders have included one entity that appears to have no internet presence at all, and four that are registered in Singapore or Cyprus.”36 Of those four, one lists Gubarev as its owner; the others provide little to no ownership information. The use of anonymous or offshore entities as shareholders is commonly considered a signal of an intention to evade accountability.37,38,39,40,41,42,43
PropellerAds utilizes XBT infrastructure, which has been cited as being used in major disinformation and fraud cases. The Russian propaganda network Doppelgänger used Webzilla as a hosting provider and URL Solutions as a domain registrar.44,45 Court filings in the Methbot ad fraud trial confirmed that a “sizable number” of Methbot servers resided on XBT networks.46 Methbot used a large botnet to artificially inflate the views of video ads, garnering millions of advertising dollars. Servers.com CTO, and Webzilla CTO from 2005 to 2014, Kostyantyn/Konstantin Bezruchenko testified that there were personal ties between the Methbot leader Aleksandr Zhukov and XBT founder Aleksej Gubarev.47
Gubarev first entered the geopolitical spotlight in 2017 when BuzzFeed posted the full, unverified Steele dossier. The dossier asserted that XBT/Webzilla servers helped to transmit malware and steal data from the Democratic National Committee via “botnets and porn traffic.”48 Gubarev sued BuzzFeed for defamation, and the case was dismissed; BuzzFeed later removed Gubarev’s name and apologized, so Gubarev’s appeal was withdrawn in 2021. During the proceedings, former FBI Cyber Chief Anthony Ferrante submitted a report that linked Webzilla address space to spear-phishing infrastructure. Ferrante’s report, “Exhibit 1,” reviews Bezruchenko’s deposition and details a striking lack of visibility into Webzilla’s network. Ferrante argued that “[XBT does] not actively prevent the use of their infrastructure to support malicious cyber activity.”49 Ferrante also cited Bezruchenko’s deposition when he opined that Webzilla had inadequate takedown procedures. Hypothetically, webhosts without robust abuse processes often become attractive to persistent malvertising actors. A rebuttal expert report filed by Dr. Eric B. Cole on XBT’s behalf challenges Ferrante’s findings, calling the analysis “misleading” and noting the investigation “has no information based on collection and analysis from XBT Holding systems.”50 Cole argues that traffic like the packets Ferrant flags “passes across IPs in every AS across the world” and that the record contains “no forensic evidence” tying XBT or Webzilla to deliberate wrongdoing; no court has found XBT or its affiliates liable.
Webzilla
Kostyantyn/Konstantin Bezruchenko owns the U.S. corporate shell of Webzilla (Figure 7, above). WHOIS filings also attach his name to the registration of xbt[.]com, and he’s listed as the contact person for URL Solutions.51,52 He incorporated Webzilla Inc. using Incorporate Now, a mailbox service run by long-time associate Constantin Luchian.53 Reporting by McClatchy found “that Nikita V. Kuzmin, the creator of the Gozi virus, which stole online banking data, incorporated at least three companies in South Florida, with the administrative assistance of Webzilla officer Constantin Luchian.”54 Additional reporting brought to light the fact that the International Intellectual Property Association entered a formal complaint that Webzilla “serviced and administered” a Cyprus company called 4shared[.]com. At the time, the complaint said that 4shared was the most-cited piracy website in the world. Webzilla denied liability but kept the customer.55
Webzilla’s decision to maintain business with an alleged piracy website, even after being implicated in a formal complaint, highlights how willing the company is to embrace high-risk clients. In addition to using Webzilla for hosting, 4shared[.]com uses URL Solutions as its registrar.56 Luchian and another Bezruchenko associate, Konstantin Bolotin, appear in multiple lawsuits. At one point, they were sued in federal court by Hydentra HLP over an adult-traffic affiliate scheme that used Webzilla infrastructure.57
One of the suit’s domains (sunsocialmedia[.]com), still resolves today to Webzilla’s AS 40824 block at 199[.]101[.]134[.]0/24.58 Further, the domain’s A record has a pointer (PTR) record of servicedomain[.]net. The WHOIS registrant email of that PTR record domain is info@lightsoft[.]co; the owner of Lightsoft is Konstantin Bolotin.59 Earlier German court filings on Freakshare (alleged to be a member of a global criminal enterprise run by two German citizens) list Luchian as the Digital Millennium Copyright Act agent via Scottish shell Vollend Plus LP, itself owned by two Seychelles entities.60 The involvement of the same small set of actors (Luchian, Bolotin, and Bezruchenko) in lawsuits that span adult content, piracy, and malware paints a picture of a close-knit, well-orchestrated team employing deliberate strategies.
Lawfare
Let’s return to Valentin Gurvits, the lawyer who represented Mardiros Haladjian (Figure 7), one of the initial directors of PropellerAds, in his various legal escapades. He is also counsel for Aleksei Gubarev/XBT. Gurvits commented to media outlets on the Methbot case and essentially played the plausible deniability card, admitting that bad actors had “misused” Webzilla infrastructure, and that Webzilla was not at fault for such misuse.61 Then, he led the 2017 defamation case against BuzzFeed over the Steele dossier. He has defended Constantin Luchian and Konstantin Bolotin in the Hydentra lawsuit and helped Luchian file the U.S. copyright paperwork for Vollend Plus. In nearly every civil case touching PropellerAds, XBT/Webzilla, or their various offshore fronts, Gurvits has acted as counsel to a web of malvertising, gambling, piracy, ad fraud, and adult content operations.
Corporate Connections
Let’s recap: PropellerAds’ lineage is one of shell-games: “founded” in London, moved to the Isle of Man, then reborn in Cyprus under AdTech Holding. Its original director, Mardiros Haladjian, shows up in the Paradise Papers, WIPO cybersquatting disputes, and in lawsuits against his adult content company Hammy Media. PropellerAds’ Cyprus office lies seven minutes from URL Solutions’ contact address and Vane Viper domains make up nearly 50 percent of bulk-registered domains via URL Solutions since 2023. Réseaux IP Européens (RIPE) maps multiple /24 blocks owned by PropellerAds on Webzilla/XBT address space. AdTech Holding is ensconced in Alexei Gubarev’s TechIsland incubator and AdTech Holding’s founders at Embria use Servers.com for hosting infrastructure. XBT’s networks have hosted the Methbot ad fraud botnet, the Kremlin’s Doppelgänger disinformation campaign, and piracy giants like 4shared. Valentin Gurvits, the go-to lawyer for Haladjian, Gubarev, Bezruchenko, Luchian, and Bolotin, represents them in court. None of these links proves coordinated wrongdoing. However, in aggregate, they paint a picture of opaque shareholding, offshore companies in tax havens, and networks repeatedly flagged for malvertising, disinformation, click-fraud, privacy, and ad traffic abuse. When those sketchy business practices intersect with the documented threats below, any claim of plausible deniability loses credibility.
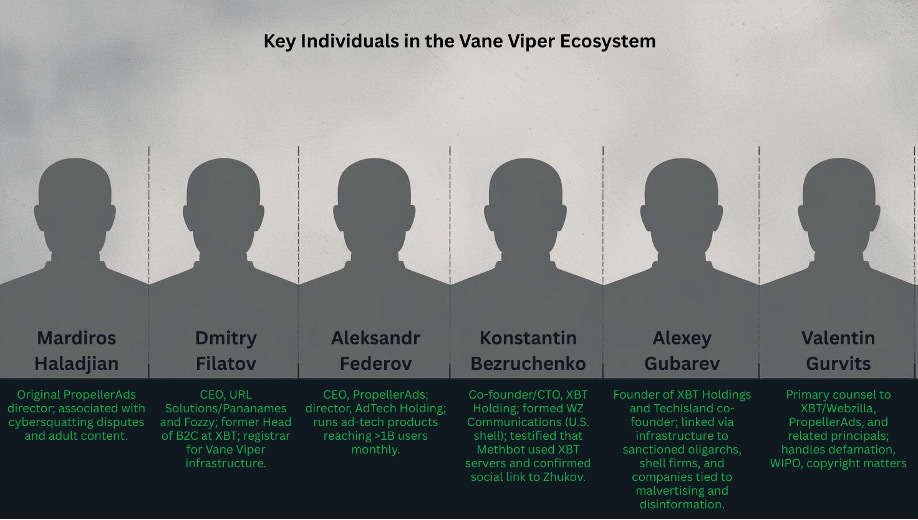
Figure 8. A brief recap of key players in the Vane Viper ecosystem and their role
With “plausible deniability” hanging by a thread, let’s now turn to the real-world tricks Vane Viper uses and the threats they deliver.
Push Comes to Shove
Under the Hood
Pushy salespeople are everyone’s “favorite,” right? Whether on the street, in a supermarket, or door to door, they just won’t take no for an answer. In-browser push notifications are similar. And there are legitimate use cases for them. They offer users an easy way to stay up to date with Facebook or Reddit posts, or with breaking news. But they also offer threat actors an opportunity to achieve persistence on an endpoint and in a network.
How do these notifications work under the hood? They rely on service workers: JavaScript files that act as a proxy service, intercepting network requests between the web app and the network. Vane Viper uses service workers and script chaining to abuse push notifications. In 2024, GoSecure published an in-depth analysis of a set of malicious service worker files but did not identify the operator at the time.62 Correlating the domains in that report with our own data shows that these service workers belong to Vane Viper. A service worker’s use of “eval()” to execute any content fetched from a remote URL is most alarming, as it lets any code retrieved from that URL run in the page’s context. The remote URL queried is given by one of the hardcoded domains within the service worker.
These push notifications, as mentioned, grant persistence on an endpoint if they’re accepted by the user. Once accepted, the user’s device turns into a merry-go-round of malvertising, enabling a constant stream of threats. In analyzing the lifespan of Vane Viper domains, most domains were active for less than a month; however, a certain set of domains have been active for 1,200 days or more. These include good old omnatuor[.]com, (which we published about in August 2022), propeller-tracking[.]com, and many domains that appear to be centered around push notification services: in-page-push[.]com, pushimg[.]com, inpagepush[.]com, propu[.]sh, and others.63 However, to keep the operation going, Vane Viper needs to register vast numbers of new domains each month. Figure 9 shows the increasing monthly registration count of domains since January 2023, up to the maximum monthly count of 3,500 domains in October of 2024.
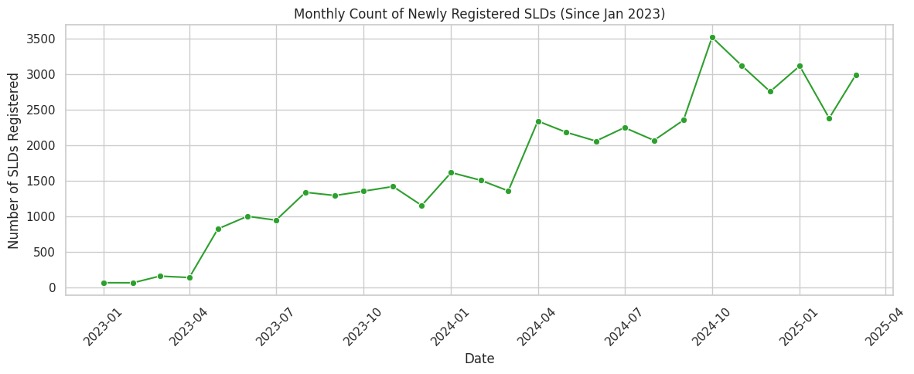
Figure 9. The number of Vane Viper domains registered per month since January 2023
By cycling through thousands of domains each month and keeping key push notification domains alive for years, Vane Viper demonstrates a strong resilience to takedowns and an increasing scale of operations.
The Funnel
Vane Viper uses their TDS to deliver threats in a variety of ways: from push notifications sent to an endpoint, to compromised or lookalike sites that victims can stumble across while web browsing. For example, in our research, we came across a malware trojan that was dropped onto a Pixel phone from a Vane Viper domain in the form of a malicious APK file (Figure 10).
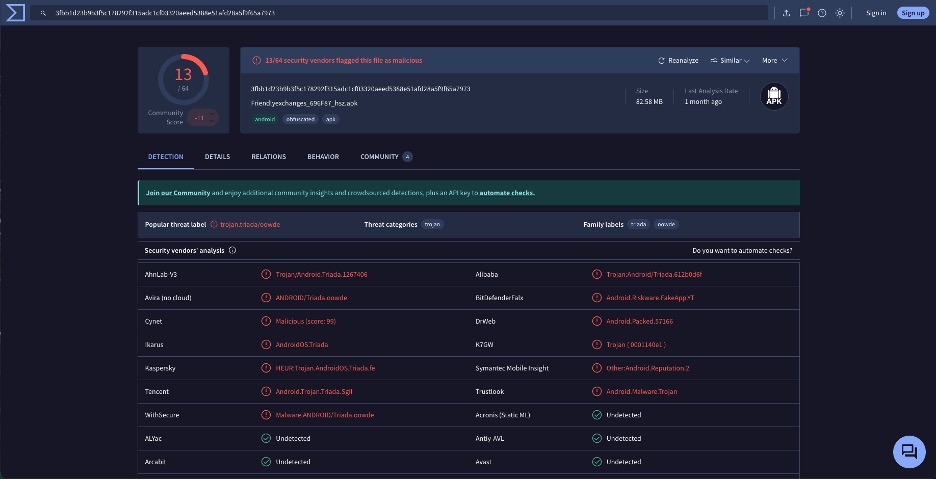
Figure 10. The VirusTotal entry for a malicious APK dropped onto a burner phone from a Vane Viper domain during our research (Credit: VirusTotal)
The trojan was Triada, and it was dropped from the domain visionedmisfocusedpanfry[.]com.64 But when we tried to visit the domain in URLScan, it showed up as a wrapper for a Google search, as shown in Figure 11. That’s part of the power of a TDS: if you don’t match the “desired victim” profile, it can be hard to tell anything is amiss about the domain.

Figure 11. A search bar, which queries Google, on visionedmisfocusedpanfry[.]com (Credit: URLScan65)
We’ve also seen Vane Viper distribute malicious browser extensions, fake shopping sites, adult content, survey scams, fake apps, and sketchy software downloads. One operation, which ends in a likely fake software download (we were unable to obtain a sample but are confident in our assessment due to analysis of the various domains along the redirection chain, explained further below), starts with a bit[.]ly link, forces a push subscription gate, then drops users onto a supposed Opera Browser download page. We suspect that Vane Viper themselves, and not an affiliate, ran this campaign for the purposes of ad fraud. Figure 12 provides a domain tree (read bottom-up) illustrating one variation of the traffic flow from this campaign.
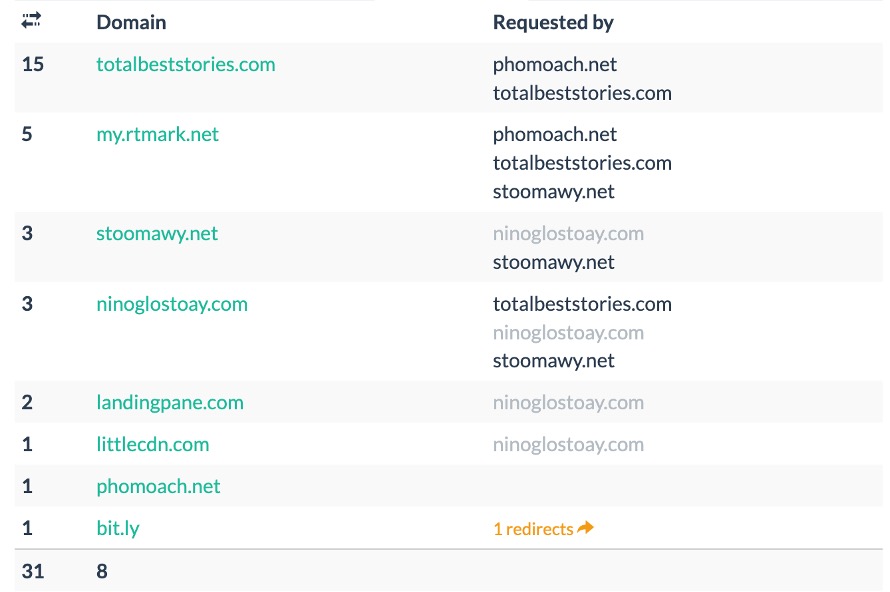
Figure 12. The domain tree for this campaign, read bottom-up (Credit: URLScan66)
Apart from the initial bit[.]ly link, we assess that Vane Viper registered and controls each domain in the tree. All observed traffic flows between these domains and there are no third-party publisher or affiliate domains involved. Moreover, the domain landingpane[.]com (used as a sort of static-content CDN) is hosted on the IP address 188[.]42[.]160[.]55. Webzilla is the sponsoring upstream holder for that network space, but the entire IPv4 /24 block 188[.]42[.]160[.]0–188[.]42[.]160[.]255 has been assigned to PropellerAds. An overview of selected fields from the most recent WHOIS lookup is provided in Table 2 below.
| WHOIS Field | Value |
|---|---|
| inetnum | 188[.]42[.]160[.]0 –to 188[.]42[.]160[.]255 |
| netname | NET-188-42-160-0-24 |
| descr | PROPELLER ADS LTD (Zinonos Rossidi 11, Limassol 3082, Cyprus) |
| country | NL |
| status | ASSIGNED PA |
| created | 2022-12-09T13:36:47Z |
| last-modified | 2024-04-22T06:39:19Z |
| sponsoring LIR/org-name | Webzilla B.V. (ORG-WL21-RIPE; Keienbergweg 22, Amsterdam, NL) |
| Table 2. RIPE WHOIS assignment record for 188[.]42[.]160[.]0/24 | |
This means that PropellerAds is the direct tenant of that address space and controls all routing, reverse‐DNS, and server deployments within it. landingpane[.]com has been linked to a VirusTotal file submission that has a “Browserknock” trojan label.67 We assess that this is a similar sample to the one that we found and analyzed because of the inclusion of a function called “knock.”
In this instance, the user is prompted to accept push notifications before ever reaching the landing page. The push notification page, shown in Figure 9, presents itself as a video prompt but is actually a malvertising funnel.
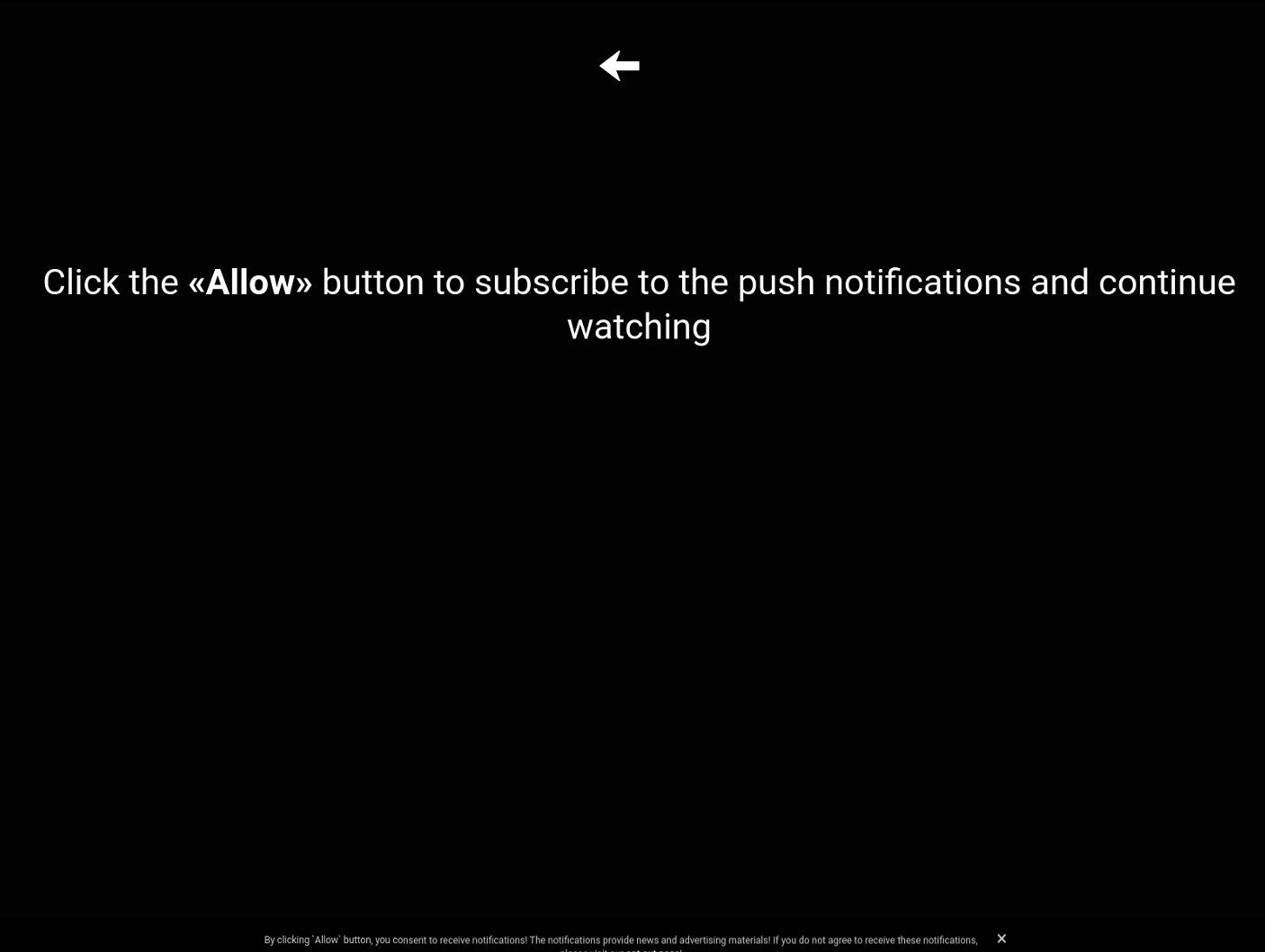
Figure 13. Page forcing the user to accept push notifications (Credit: URLScan68)
Upon page load, the following sequence unfolds asynchronously:
Token Generation and Tracking
- As soon as a user lands on the page, an “OAID” token is generated and sent off to my[.]rtmark[.]net to obtain a “GID” (likely a global identifier). This GID/OAID value is then stamped to the victim’s browser to enable fingerprinting.
Browser History Poisoning
- Next, the page poisons the browser history and hijacks the back button, preventing users from leaving the page, in addition to prompting them with a confirmation (“Are you sure you want to leave?”) if they attempt to exit the page completely.
Notification Abuse
- When the request for notification permission is denied, the script forces a random single-letter subdomain redirect to dodge permission refusals. In the background, an event listener is set up to listen on clicks, ensuring that even accidental clicks cause redirect activities.
Redirection
- Regardless of whether the user accepts, denies, or ignores the notification prompt, the script ultimately redirects them to a dynamically chosen target page.
After the push notification gate, the TDS command-and-control (C2) server returns a JSON file that guides further behavior of the redirects based on attributes including the primary URL for the next redirection, the user’s unique IDs (oaid, ruid), and session timeouts. The evidence demonstrating that Vane Viper themselves run this campaign increased when we discovered that they included “partner”:”pa” in this JSON (we believe PA = PropellerAds). Geofences and time zone offsets ensure the campaign hits the right users at the right time. Other attributes control pop-under, interstitial, and anti-adblock behavior, giving a glimpse into how the TDS dynamically reacts to ad blockers. There are feature toggles as well, including things like “smartOverlay,” “clickAnywhere,” and “iOSClickFix.” Figure 14 shows the landing page for this campaign. The iOSClickFix feature toggle is especially interesting given the rise of “Click Fix” attacks in the last year or so; however, our conversations with other researchers indicate that this feature is likely unrelated to the commonly seen attack, which typically targets Windows. It is worth noting though, that MediaTrust previously published Click Fix research that shows overlap with Vane Viper behavior.
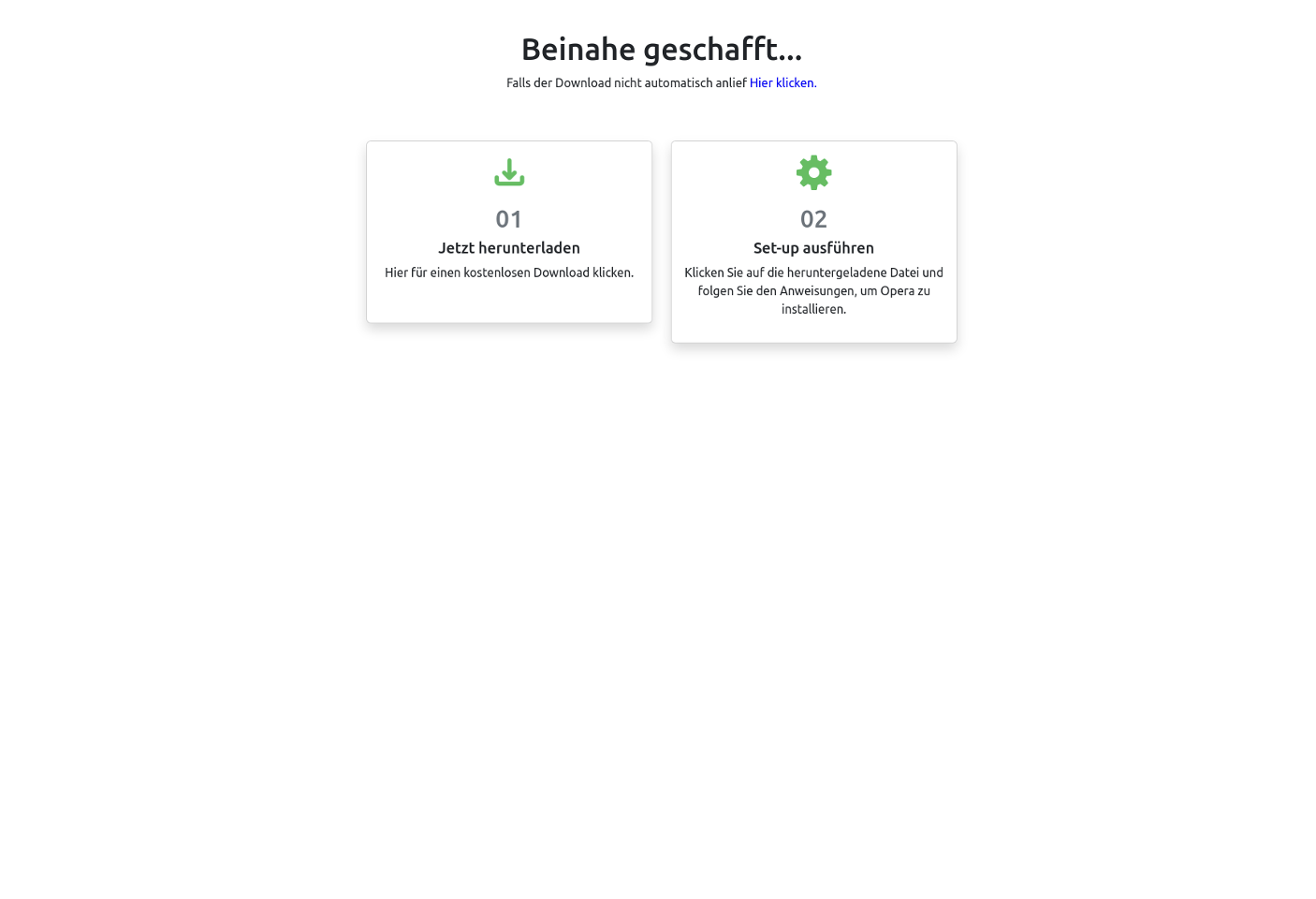
Figure 14. An Opera Browser “download page” used as a landing page for a Vane Viper campaign (Credit: URLScan69)
The landing page masquerades as a download step, presenting cues (in this case in German) that translate to “almost there.” Every call to action links to ninoglostoay[.]com and uses long, encoded query strings. Inline scripts inject “fake history states” (i.e., adding history entries by appending the string variable “fakepath” to the page URL along with a random number) upon page load, user interaction on the page, and use of the “back” button. That is, every time a user clicks “back” in their browser, the fake history entries only grow longer. This technique of generating fake history states effectively traps users on the malicious site, funneling them to further harmful content.70 A full-screen transparent <a> tag overlays the page, ensuring any user click redirects to a payload URL.
Other media have linked Vane Viper domains to PropellerAds and malicious activity. Alongside GoSecure’s research mentioned above, the Digital Citizens Alliance (DCA), a registered nonprofit in the United States focused on internet safety, has linked PropellerAds to malvertising on privacy websites. In their report titled “Unholy Triangle,” DCA claims that PropellerAds “and its related domains (in-page-push[.]com and inpagepush[.]com) accounted for an estimated $31 million—or one in four dollars—of the malvertising found on piracy websites.”71 PropellerAds was also implicated in the early stages (Spring 2017) of the Master134 malvertising campaign, wherein their domain onclkds[.]com was used to redirect traffic to malicious sites.72
Recent research by GoDaddy shows that the Master134 operation evolved into a campaign now called “DollyWay World Domination.”73 At the time, a PropellerAds representative wrote that “it is impossible to know whether traffic is hijacked and it is virtually impossible to ascertain whether the traffic is being redirected to malicious websites.”74 The same pattern reemerged in October 2018 when an affiliate marketer (“FMLTD”) opened a thread titled “PropellerAds Traffic Issue” on AffiliateFix.75 After the marketer documented that a hacked site was funneling visitors through PropellerAds’ network, Propeller’s support replied, “Nobody is hacking sites … Everything is legal,” then stopped answering emails until the dispute became public and the thread was escalated. PropellerAds has also been implicated in acting as a TDS for Tag Barnakle, a malvertising actor who compromises ad servers.76,77 In response, Propeller again shirked responsibility and went so far as to label Confiant’s research “libelous.”78 Ongoing complaints from marketers and security researchers alike about bot or illegal traffic from their domains seem to demonstrate a consistent reluctance by PropellerAds to accept responsibility.
Conclusion
Vane Viper’s operation is built for scale and evasion and provides a mechanism for them and other bad actors to run malicious ad campaigns. Through nearly 60,000 known unique domains, most active for only days or weeks, they leverage push notification persistence, dynamic cloaking, and script chaining to deliver cyberthreats at scale. URL Solutions, Webzilla, and AdTech Holding form a closely connected trio of firms: domains registered en masse via a registrar steeped in cybercrime, hosted on infrastructure operated by a company that’s hosted everything from Methbot to state-sponsored disinformation, and payloads delivered via an ad network long implicated in malvertising.
This core has built out infrastructure that overlaps with warez hubs, piracy platforms, adult traffic brokers, disinformation campaigns, phishing, malware, and more; not to mention indirect financial and organizational connections to figures with serious reputational and legal baggage. Some linkages are circumstantial. But the persistence of these connections suggests a pattern, not a coincidence. Each company or character in the Vane Viper extended universe maintains just enough distance to deny intent yet remains tightly coupled enough to keep the system functioning.
Vane Viper isn’t just a threat actor hiding behind an adtech platform. It’s a threat actor as an adtech platform. AdTech Holding claims to offer advertisers reach and monetization at scale, but what it actually delivers is risk. For enterprises, defenders, and internet users at large, that risk comes routed through CDN-grade infrastructure and delivered via click-to-accept. Vane Viper is a symptom of something deeper, however. The digital advertising ecosystem wasn’t designed to be accountable to users. It was designed to be fast, scalable, and profitable. Somewhere along the way, that design became a liability. Vane Viper shows how easy it is to weaponize that ecosystem. In that sense, Vane Viper isn’t just an example of the exploitability of the internet. Rather, they help reveal how much the internet has already been broken by an advertising model that prioritizes reach over responsibility and monetization over trust.
Vane Viper domains from this research can be found in our Github repository.
References
- https://blog.confiant.com/tag-barnakle-the-malvertiser-that-hacks-revive-ad-servers-redirects-victims-to-malware-50cdc57435b1
- https://blog.confiant.com/tag-barnakle-one-year-later-120-more-revive-adserver-hacks-f3e5b3bc8e70
- https://web.archive.org/web/20241108151006/https://www.techtarget.com/searchsecurity/news/252486702/Digital-ad-networks-tied-to-malvertising-threats-again
- https://web.archive.org/web/20250125182941/https://www.techtarget.com/searchsecurity/feature/Inside-Master134-Propeller-Ads-connected-to-malvertising-campaign
- https://www.digitalcitizensalliance.org/clientuploads/directory/Reports/Unholy-Triangle-Report.pdf
- https://support.google.com/google-ads/answer/6320?hl=en&ref_topic=24936&sjid=10049883789707446307-NA
- https://support.google.com/google-ads/answer/6365?hl=en
- https://advertising.amazon.com/library/guides/real-time-bidding
- https://blog.confiant.com/uncovering-2017s-largest-malvertising-operation-b84cd38d6b85
- https://labs.guard.io/deceptionads-fake-captcha-driving-infostealer-infections-and-a-glimpse-to-the-dark-side-of-0c516f4dc0b6
- https://opencorporates.com/companies/gb/07675984
- https://offshoreleaks.icij.org/nodes/56063574
- https://www.wipo.int/amc/en/domains/decisions/text/2015/d2015-0252.html
- https://opencorporates.com/companies/gb/OC394908
- https://www.wipo.int/amc/en/domains/decisions/text/2018/d2018-0104.html
- https://www.dnb.com/business-directory/company-profiles.hammy_media_ltd.9ae0492162b3071b852c5adc8671b9de.html
- https://www.texasattorneygeneral.gov/sites/default/files/images/press/Hammy%20Media%20Petition%20Filestamped.pdf
- https://www.pacermonitor.com/public/case/601776/Fraserside_IP_LLC_v_Hammy_Media_Ltd_et_al
- https://www.welt.de/print/wams/wirtschaft/article157880510/Geldmaschine-fuer-Fluechtende.html
- https://opencorporates.com/companies/im/011883V
- https://insights.infoblox.com/resources-research-report/infoblox-research-report-reliable-reputation
- https://web.archive.org/web/20250611125113/https://static1.squarespace.com/static/63dbf2b9075aa2535887e365/t/66cde404c8345e766972319c/1724769286084/PhishingLandscape2024.pdf
- https://web.archive.org/web/20250318004226/https://fozzy.com/us/about.shtml
- https://www.linkedin.com/in/dmitry-filatov-64867a46/?originalSubdomain=cy
- https://ipinfo.io/AS35415
- https://web.archive.org/web/20250730193755/https://www.prnewswire.com/news-releases/xbt-holding-ltd-continues-expansion-with-acquisitions-in-singapore-and-luxembourg-165397106.html
- https://web.archive.org/web/20250730194001/https://finance.yahoo.com/news/xbt-3-holdings-acquisitions-050000400.html?guccounter=1
- https://web.archive.org/web/20250730194339/https://siliconcanals.com/palta-raises-84-2m/
- https://archive.is/aYRY1#selection-445.157-445.166
- https://www.businessinsider.com/alexander-frolov-leaves-target-global-after-father-is-sanctioned-2022-12
- https://sifted.eu/articles/lawsuit-target-global-links-to-russia
- https://web.archive.org/web/20250609121901/https://thetechisland.org/board-directors/alexey-gubarev
- https://web.archive.org/web/20250325224620/https://adtechholding.com/blog/adtech-holding-limassol-city-skate-park/
- https://cynews.is/gubarev-s-importation-putin-s-it-guys-take-over-cyprus/
- https://pressway.org.uk/news/300098-rucsian_it_businessman_gubarev_in_cyprus_how_a_tech_eeemigrantee_turned_the_island_into_a_hub_for_sanctions_evasion
- https://www.mcclatchydc.com/news/nation-world/national/article184786328.html
- https://www.complif.com/us/blog/unmasking-shell-companies-the-hidden-tools-of-financial-crime
- https://www.fincen.gov/resources/statutes-regulations/guidance/potential-money-laundering-risks-related-shell-companies
- https://www.fraudconferencenews.com/home/2018/6/17/breaking-the-shell
- https://www.fbi.gov/news/speeches-and-testimony/combating-illicit-financing-by-anonymous-shell-companies
- https://www.sanctions.io/blog/sanctions-evasion-through-shell-companies-explained
- https://web.archive.org/web/20191214155442/https://www.mcclatchydc.com/news/investigations/article238024734.html
- https://www.occrp.org/en/project/the-troika-laundromat
- https://www.qurium.org/alerts/under-the-hood-of-a-doppelganger/
- https://www.disinfo.eu/wp-content/uploads/2022/09/Doppelganger-1.pdf
- https://cdn.cnn.com/cnn/2019/images/03/15/xbt.doc.248.2.pdf
- https://www.rferl.org/a/methbot-russia-internet-fraud-state-sponsored-hacking-zhukov/31241417.html
- https://archive.org/details/TrumpIntelligenceAllegations_201801
- https://dd80b675424c132b90b3-e48385e382d2e5d17821a5e1d8e4c86b.ssl.cf1.rackcdn.com/external/expertreportanthonyjferrante-1.pdf
- https://cdn.cnn.com/cnn/2019/images/03/15/show_temp_new.pdf
- https://www.bigdomaindata.com/whois-history/xbt.com
- https://domains.mjwebs.com/registrars/url-solutions-inc-1449#:~:text=Konstantin%20Bezruchenko
- https://search.sunbiz.org/Inquiry/CorporationSearch/SearchResultDetail?inquirytype=OfficerRegisteredAgentName&directionType=Initial&searchNameOrder=BEEBURTONZIII%20P090000643274&aggregateId=domp-p09000064327-d6e3dc9a-5813-4545-ad87-f81cd784017a&searchTerm=Beeble%20%20%20%20%20%20%20%20%20%20%20%20%20%20Kellie&listNameOrder=BEEBLEKELLIEA%20L240001151610
- https://www.mcclatchydc.com/latest-news/article218740565.html
- https://www.mcclatchydc.com/news/nation-world/national/article184786328.html
- https://urlscan.io/result/0196a84a-7a09-72cc-a787-801cddaf8f02/
- https://unicourt.com/case/rc-ap1-hydentra-hlp-int-limited-v-constantin-luchian-et-al-51105
- https://urlscan.io/result/e4ee74ff-25c2-485d-9c21-11ff630703c2/#summary
- https://opencorporates.com/companies/us_fl/P17000092716
- https://web.archive.org/web/20191214155442/https://www.mcclatchydc.com/news/investigations/article238024734.html
- https://web.archive.org/web/20250730205254/https://www.rferl.org/a/methbot-russia-internet-fraud-state-sponsored-hacking-zhukov/31241417.html
- https://gosecure.ai/wp-content/uploads/Anatomy-of-Service-Worker-Abuse-From-Visit-to-Network-Anomaly.pdf
- https://blogs.infoblox.com/cyber-threat-intelligence/cyber-threat-advisory/vast-malvertising-network-hijacks-browser-settings-to-spread-riskware/
- https://www.kaspersky.com/blog/triada-trojan/11481/
- https://urlscan.io/result/fb89ad59-72d7-4e05-9363-bcc6effe3f6b/
- https://urlscan.io/result/4ba9dd35-94d8-458e-864d-d2d97e92ef87/#summary
- https://www.virustotal.com/gui/file/38891a56d25f66218be2aab15a90773919e8d91f0ed6b6b38637fba2b184c129
- https://urlscan.io/result/3eef35a8-8029-4eb4-823f-f32e36e81c57/#summary
- https://urlscan.io/result/4ba9dd35-94d8-458e-864d-d2d97e92ef87/#summary
- https://blog.confiant.com/malvertiser-d-shortiez-abuses-webkit-back-button-hijack-in-forced-redirect-campaign-6b57f91ee737
- https://www.digitalcitizensalliance.org/clientuploads/directory/Reports/Unholy-Triangle-Report.pdf
- https://web.archive.org/web/20250125182941/https://www.techtarget.com/searchsecurity/feature/Inside-Master134-Propeller-Ads-connected-to-malvertising-campaign
- https://www.godaddy.com/resources/news/dollyway-malware-history
- Wright, Inside ‘Master 134’
- https://www.affiliatefix.com/threads/resolved-propellerads-traffic-issue.157288/
- https://web.archive.org/web/20241108151006/https://www.techtarget.com/searchsecurity/news/252486702/Digital-ad-networks-tied-to-malvertising-threats-again
- https://blog.confiant.com/tag-barnakle-one-year-later-120-more-revive-adserver-hacks-f3e5b3bc8e70
- https://propellerads.com/pr-general-response-to-articles-alleging-malware-on-the-propeller-ads-network/