Author: Maël Le Touz
1. Overview
Since late August, Infoblox has been tracking an actor sending a large number of SMS phishing (smishing) messages targeting phone numbers in France. This attack is ongoing and so widespread that it is regularly mentioned in national news.1 The text requests that the addressee fill out a form to receive a new Social Security Card and to keep the addressee’s healthcare plan. Threat actors then charge victims’ bank accounts and later make fraudulent tax claims.
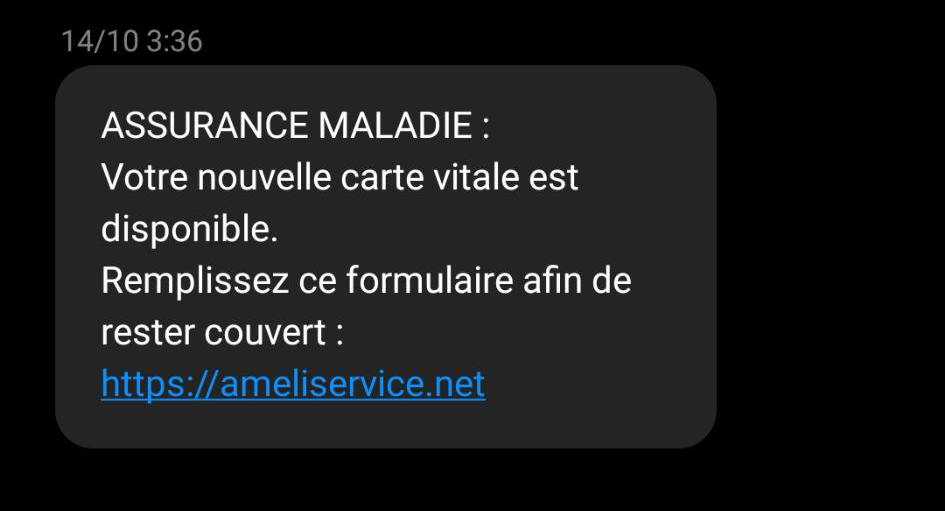
Figure 1: An example of an inbound smishing message, received on 14 October.
2. Customer Impact
This campaign was first discovered in relation to Ameli: the French government’s portal for social security, and one of the single sign-on (SSO) points for other websites of government services. The campaign is focused on French speakers and French nationals who use government services and banks. However, some related domains used also include lookalikes that target British nationals, Spanish and Portuguese speakers, as well as Belgian telco and Dutch energy companies. See Figures 2 and 3 below.
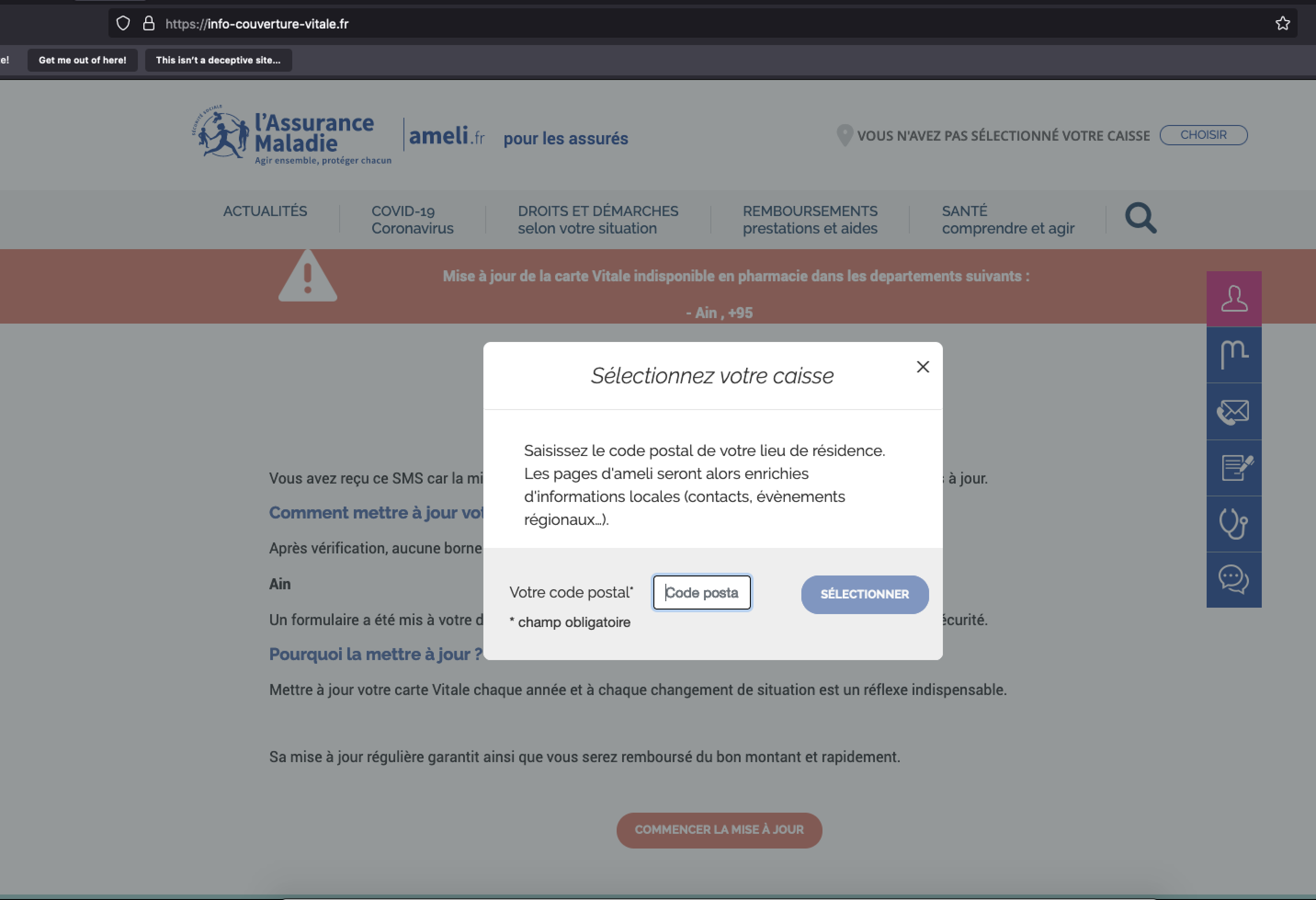
Figure 2: An example of a phishing page masquerading as the portal for the website for Sécurité Sociale
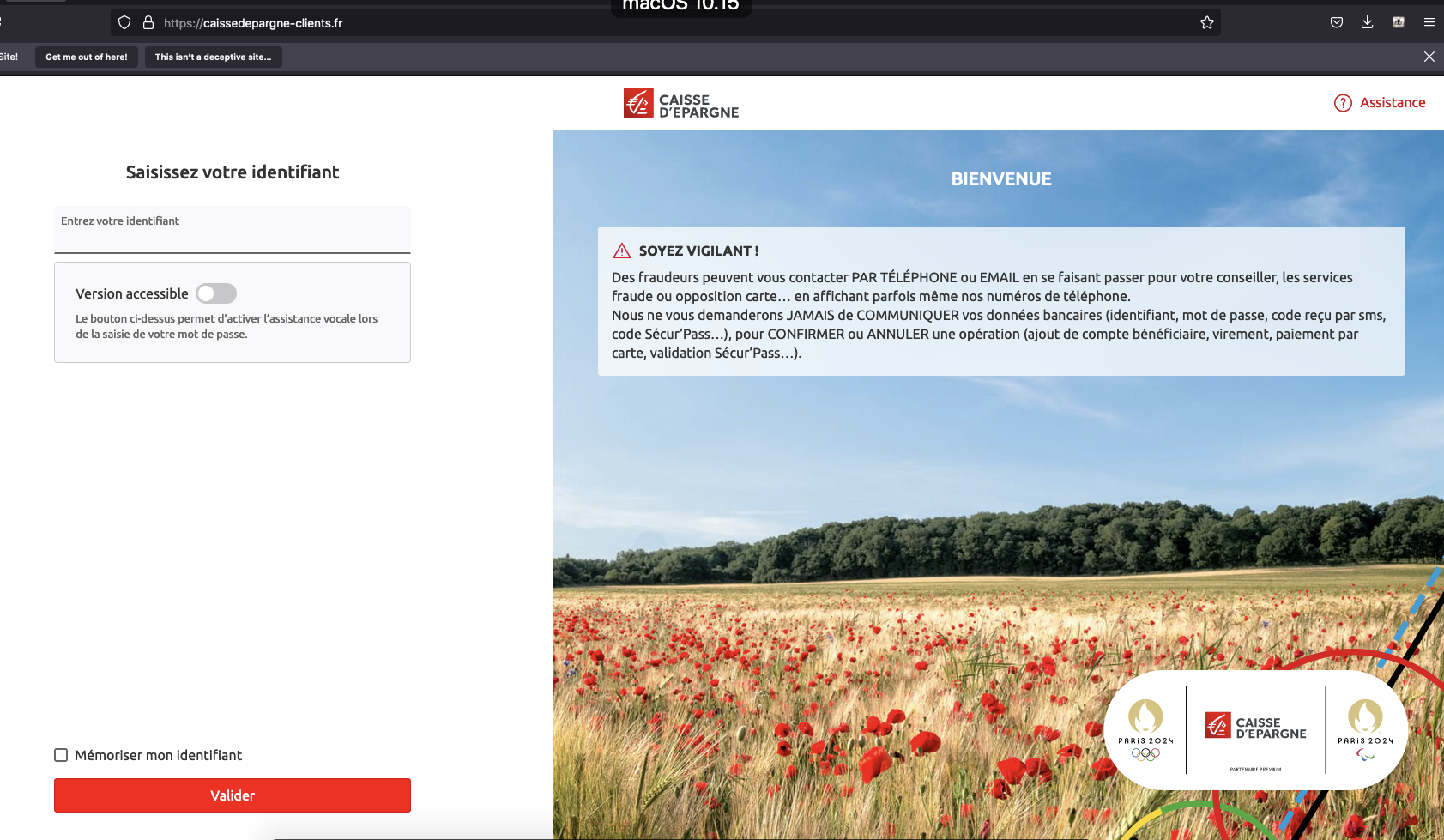
Figure 3: Example of a phishing page targeting customers of the Caisse d’Epargne bank
Once the landing page is accessed, the victim is served with a form asking for personal information, such as email addresses and passwords. The fraudulent websites also ask for financial information, purportedly to allow for the payment of taxes or late fees. If the victim fills out those forms, their bank accounts will be immediately charged. Some time later, when tax season comes, the victims’s Ameli login will be used to make fraudulent tax claims and receive tax rebates on an attacker-controlled bank account.
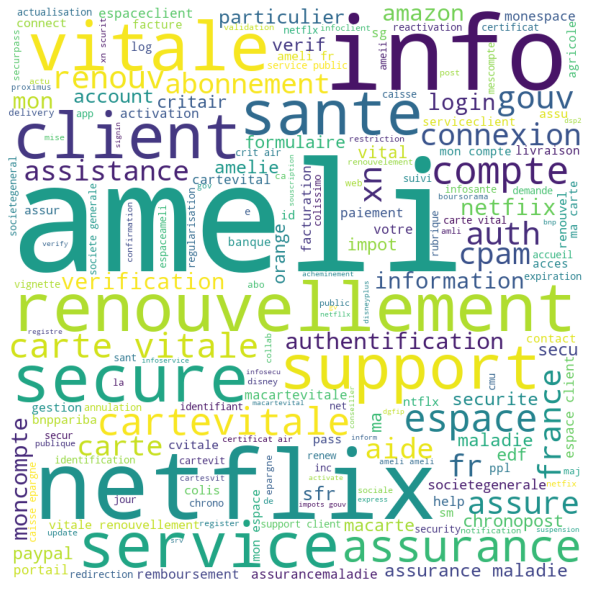
Figure 4: Most commonly used words in the domain names
4. Infrastructure analysis
Attackers used an extensive network of burner emails, phone numbers, and fake identities to cover their tracks, as well as used multiple hosts to avoid automatic takedowns. After several days, the attackers took the phishing pages offline to avoid detection by automated tools and browser safety lists. Infoblox was able to detect and identify approximately 200 IP addresses serving over 7,000 unique phishing domains, illustrated in the map in Figure 5 below. Although the attackers have used Amazon, Google, and other providers of cloud services, they also rely heavily on dedicated servers.
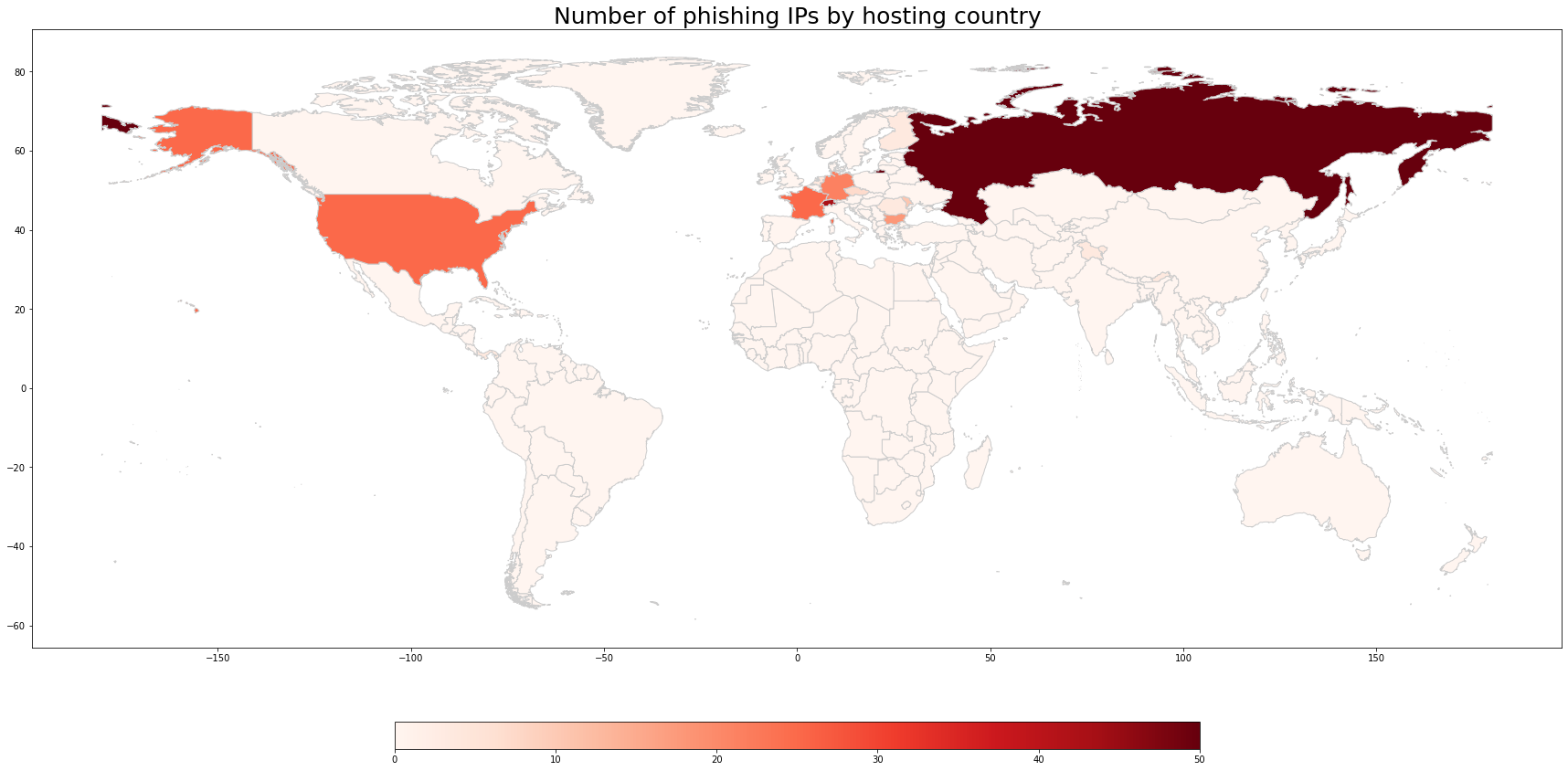
Figure 5: The number of dedicated hosting IPs used by the actors, per country
The landing pages are of good quality and, to the unsuspecting eye, visually indistinguishable from the legitimate login pages. Some phishing pages ask for credit card information, purportedly to pay taxes or resolve an unsuccessful payment to a legitimate service. Using Ameli, one can log in to a variety of government portals, including the tax office and the portal for government subsidies. This has led the government of France to temporarily cut off access from it.2 Nevertheless, we consider this attack as more likely to be financially motivated rather than political, because it has targeted multiple sectors – government, financial, energy and communication – in several countries.
5. Vulnerabilities and Mitigation
Infoblox strongly recommends that businesses consider the following security measures:
- Never click URLs in emails or texts from unknown sources.
- Be wary of links in incoming emails and texts. A link in a message from a legitimate company will usually point to the company’s domain; for example, a link in a message from FedEx will point to http://fedex[.]com. Pause the cursor over the link to verify its true destination.
- If in doubt, do not click links in messages. Instead, navigate to the websites by typing their URLs in the web address bar of your browser.
Appendix
The table below provides a list of the indicators or compromise (IOCs) relevant to our recent findings. For the complete list of IoCs, see our GitHub repository.3
| Representative Indicators of Compromise | Description |
| remboursement-impot-fiscal[.]com
connexion-ligne[.]com cartevitale-info-ameli[.]com cartevitale-actualisation[.]com authentification-carte-vitale-secure[.]com auth-secure-carte-vitale[.]com assurevitale[.]com assurance-cartes[.]com netflix-secu[.]com ameli-monrenouvellement[.]com votre-envoi-colis[.]com authentification-ameli-secure[.]com authameli[.]com auth-carte-vitale-connexion[.]com assurvital[.]com vitale-carte-actualisation[.]com secur-amelie[.]com ma-vitale-sante[.]com ma-cledigitale-support[.]com gouv-reduction-impot[.]com digitale-support[.]com auth-connexion-service-public[.]com ameli-frais[.]com |
Sample of phishing domains |
Endnotes
- https://www.bfmtv.com/tech/cybersecurite/carte-vitale-les-arnaques-a-l-assurance-maladie-par-sms-se-multiplient_AN-202210240473.html
- https://www.impots.gouv.fr/actualite/suspension-de-la-connexion-nos-services-pour-les-usagers-utilisant-leur-compte-ameli-sur
- https://github.com/infobloxopen/threat-intelligence/tree/main/cta_indicators