Author: Maël Le Touz
1. Executive summary
On March 19, Infoblox observed a new spam campaign distributing Formbook infostealer malware through email attachments. Formbook is installed through two different droppers, which are usually associated with Agent Tesla – in fact, much of the delivery involves known tactics and techniques for Agent Tesla, but ultimately the payload in this campaign was Formbook. The droppers use VM detection, steganography, process hollowing, mutexes, and many other evasion techniques, and they rely heavily on XOR encryption.
2. Analysis
2.1 Customer impact
At first glance, the characteristics of the campaign match those of campaigns known to distribute Agent Tesla and Formbook. Both are information stealers and capable of identifying and exfiltrating passwords from browsers, email clients, cryptocurrency wallets, and many other software applications. Both are sold as malware-as-a-service on specialized hacking forums, and both allow buyers to customize the malware with their own command and control (C&C) and obfuscation methods.
2.2 Campaign analysis
The spam lure is unsophisticated and has been used by threat actors consistently in recent years. All emails have the same subject line, “RE: Payment Transfer slip”, and a single attached file, Payment slip PDF.zip, which contains a PE32 executable called Payment Slip PDF.exe. Because the malware uses various anti-evasion and anti-detection techniques (described below), most antivirus solutions were unable to correctly identify the threat or to provide actionable intelligence.
2.3 Analysis of the first file
Payment slip PDF.exe is a heavily obfuscated .NET executable that targets Windows systems and is packed with ConfuserEX. The code is hardly readable, and the names of functions and variables in it are replaced with non-latin Unicode characters (the orange text in the screenshot below).
Figure 1: Obfuscated code from Payment Slip PDF.exe
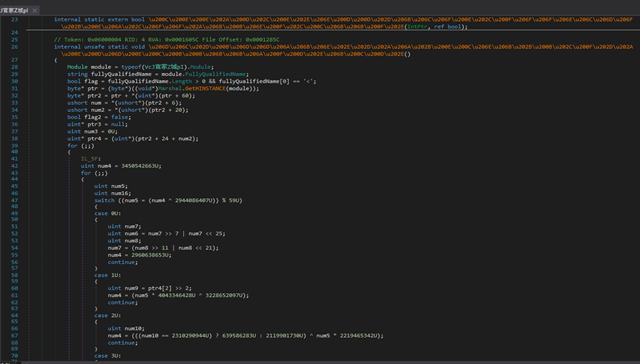
However, some functions are explicit. For example, to determine whether it is running in a sandbox, the program checks whether a remote debugger is present and tries to write to arbitrary memory locations. If the program detects a debugger, it fails silently.
The dropper also tries to prevent debugging. It does this by using flags [DebuggerHidden] and [EditorBrowsable(EditorBrowsableState.never)] to prevent an IDE from displaying code or functions and thus to hamper reverse engineering efforts. Most of the code is never executed but, instead, is taken from an open-source CPU-simulation program written in VB.NET.1
Hidden in the code is a large string and a bitmap image with high entropy:
Figure 2: Part of the bitmap image containing the payload binary

At runtime, the string is converted to a Base64 array and XOR decoded with another key. This creates a DLL, which is then reflectively loaded by Payment Slip PDF.exe.
2.4 DLL decryption routine
The DLL, named Bunifu.UI, is another .NET executable, and it is obfuscated with the help of ConfuserEX.
Figure 3: Semi-obfuscated code from the DLL
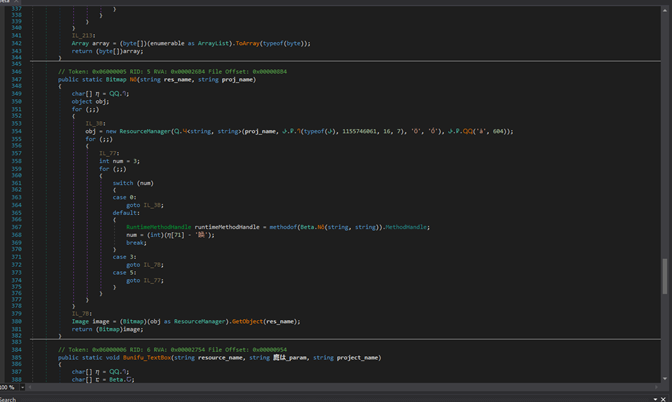
The sole purpose of Bunifu.UI is to decrypt an image by using a key passed as an argument. For each non-transparent pixel in an image, the function extracts the values of red, green, and blue and returns an array. This array is then XOR-decoded by using the parameter supplied when the DLL is invoked:
Figure 4: Deobfuscated decryption routine
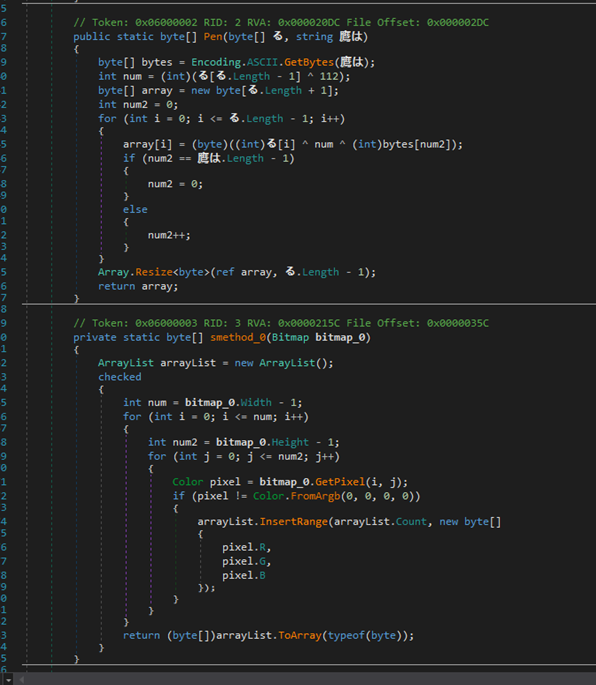
This method of obfuscation is consistent with that of Agent Tesla.2
2.5 Decrypted BMP
Hijacking the function calls enabled us to identify the decryption key of the bitmap: oRbU. Decrypting the bitmap revealed another file, MajorRevision. MajorRevision is a PE32 executable written in .NET and it, too, is obfuscated using ConfuserEX. MajorRevision contains a lot of unreachable code, which is probably copied from an open-source application that, in another attempt to prevent analysis, queries and runs SQLite databases in C#.
MajorRevision is another dropper used in this campaign. It collects information about the endpoint, verifies that the endpoint is running on a real machine, and then writes and executes the malware itself. To achieve this, MajorRevision verifies that the running system contains several strings related to virtualisation, sandboxing, and the name of the user, and that a real hard drive is present.
Figure 5: An example of checks for malware evasion
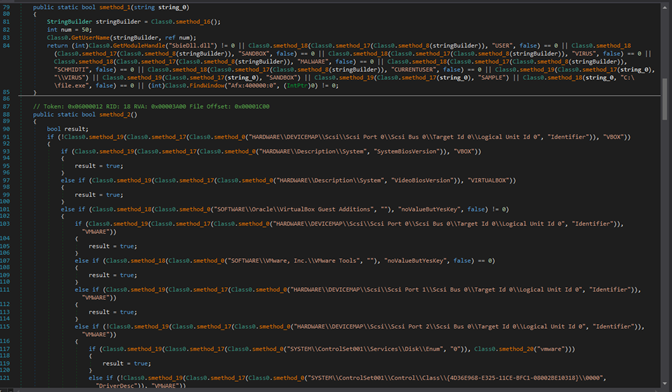
This behavior is consistent with that of common malware-as-a-service payloads, such as Agent Tesla.
If none of these checks succeeds, the program creates mutexes and copies of itself. To achieve persistence on the system, the program creates scheduled tasks. Although the code contains a mention of HTTP requests, the program does not make them. In fact, after achieving persistence on the target system, it runs several decryption routines to decrypt one of its embedded resources: an encrypted byte array called oj8UsD7H. After examining the code, we were able to extract the XOR key, PbmCIdBuCnEz. Decrypting the embedded byte array produced the final payload.
2.6 Final payload: Formbook
The final payload is not a .NET application but a MASM-compiled PE32 executable composed entirely of a .text section.
Figure 6: Identification of the payload; note the fake TimeDateStamp
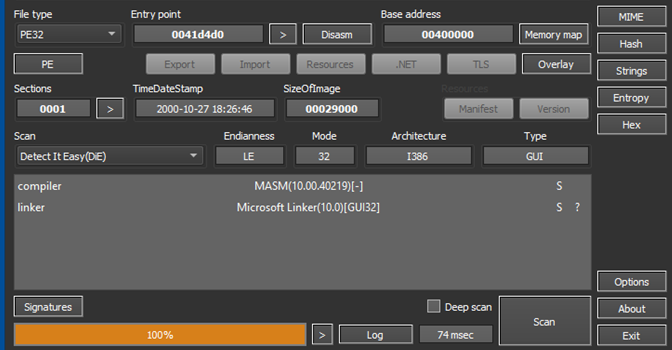
Although the rest of the delivery has been used by Agent Tesla payloads in the past, the final payload is Formbook. The executable is heavily obfuscated and contains large arrays of encrypted arrays decrypted only at runtime. The executable uses customer routines to evade debugging, and it runs most of its code on an internal virtual machine. As is typical of Formbook, the sample communicates with dozens of domains established as decoys, but only uses one true C&C.
3. Prevention and mitigation
- To prevent mobile machines from infecting others with a new variant, block known malicious URLs at the perimeter firewall and at the client firewall.
- Implement attachment filtering to reduce the likelihood of malicious content reaching a user’s workstation,
- Convert attachments to another format; for example, convert Microsoft Office documents to PDF documents. This can be an effective method for neutralizing malicious content.
- Block password-protected files and archives, because email filters cannot decrypt and inspect their contents. Block any protected archive or otherwise encrypted attachments until they can be deemed safe.
- Sanitize attachments to remove potentially harmful or active content, such as macros in Microsoft Office files, JavaScript, and links to executable downloads.
- Be aware of all attachments’ file types. Never open a file that could be a script (.vbs, .cmd, or .bat), an internet shortcut file, or a compression file. Threat actors use these techniques to evade detection methods that are based on file hashes and signatures. Threat actors also use these techniques to mask malicious files as a way of evading email service restrictions against file types used in attachments.
- Be familiar with appropriate Windows Startup entries, and check them regularly for unusual and potentially malicious applications that can start in Windows.
- Do not allow web browsers to save credentials or other sensitive information.
Endnotes
- https://github.com/Cheungo/LittleCheungComputer
- https://unit42.paloaltonetworks.com/unit42-analyzing-various-layers-agentteslas-packing/









