Author: Jeremy Ware
TLP: WHITE
Overview
From 1 to 3 March, we observed a malspam campaign distributing the Warezov worm. Also known as Stration, Warezov is an email worm that was first seen in 2006 and is spread through EXE files sent via email.
This malware was most prevalent between 2006 and 2008, with little public reporting on it since then. It is known for frequently downloading new variants of its code from remote servers.1
Infoblox last reported on a major Warezov campaign in 2019.2 In this most recent campaign, both the body of the emails and the file names have changed but the subject line as well as the command and control (C&C) server remain the same as the campaign in 2019.
Customer Impact
Warezov infects a victim’s computer and incorporates it into a botnet. The malware then sends malicious emails to the victim’s contacts to spread the Warezov worm. From there, the threat actor can use the infected machines to carry out additional malicious acts such as distributed denial of service (DDoS) attacks.
Campaign Analysis
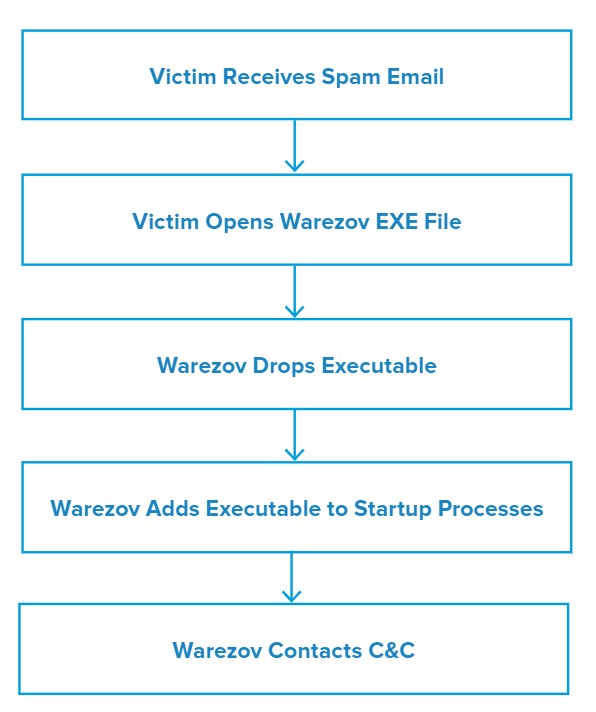
The campaign we observed delivered Warezov via email. The subject line and body of each message were identical (Mail server report). The emails carried a malicious EXE attachment with a file name mimicking Microsoft Windows updates, in this case, Update-KB2840-x86.exe.
Attack Chain
Warezov presents itself to the victim as a simple mail server report. The attached EXE is labelled as an update and presents a pop-up window that says “Update successfully installed” once executed.
The EXE drops an executable file named tserv.exe and updates the AutoRun Registry to include itself. It then attempts to contact a series of valid domains as well as a C&C server.
Vulnerabilities & Mitigation
Infoblox recommends the following precautions to reduce the possibility of infection by Warezov:
- Be cautious of emails from unfamiliar senders and inspect unexpected attachments before opening them.
- Always be suspicious of vague emails, especially if there is a prompt to open an attachment or click on a URL or clickable text.
- Filter attachments to reduce the likelihood of malicious content reaching a user’s workstation.
- Be aware of any attachment’s file type and never open files that could be a script (.vbs, .cmd, .bat) or another executable (.exe).
Endnotes
- https://www.pcworld.com/article/127711/article.html
- https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–30








