Author: Jeremy Ware
TLP: WHITE
Overview
During the week of 4 January, we observed a malspam campaign distributing the Valyria trojan. The emails in this campaign contain malicious Microsoft Office Word documents (DOCs) that display an error message when opened and execute a PowerShell script via Windows Management Instrumentation (WMI).
Customer Impact
Threat actor(s) have distributed Valyria via weaponized email attachments, social media, fake Windows updates, third-party programs and pirated content from torrent sites.1
In this campaign, Valyria uses malicious DOC files to distribute additional malware payloads. In other recent campaigns the malware has distributed Emotet,2 although it has also been reported to deliver Agent Tesla, Lokibot, and Kriptik, among others.3
Campaign Analysis
The campaign we observed used a number of seemingly unrelated subject lines and sender data. These subject lines include R:, Re: Francisco Sanchez, Hola, SALES ORDER CONFIRMATION, etc. The sender information also varied; with displayed emails such as Comercial@binarysoul[.]net, jgarratt@spectrumfloor[.]com, info@studiogabaldo[.]it, <Empty>, etc. However, the emails in the campaign all carried an attachment with a single filename of KISL06788466.doc, and the body of the message was always empty.
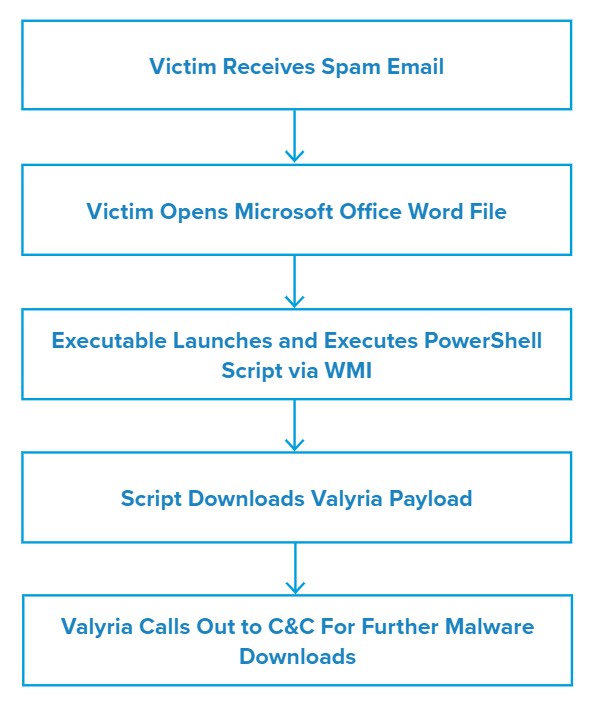
Attack Chain
When the user opens the attached document, they will see the error message: Word experienced an error while trying to open the file. While this displays an executable (cmd.exe) runs to execute a PowerShell script via WMI and creates a file at C:\Users\admin\AppData\Local\Temp\.
The script then executes the Valyria payload (rundll32.exe) and makes an AutoRun change to the registry, reaches out to the command and control (C&C) server and downloads an additional malware payload, which was Emotet in this campaign.
Vulnerabilities & Mitigation
The Valyria trojan is spread via spam email and abuses Microsoft Word Docs to execute PowerShell scripts via WMI. Infoblox recommends the following actions to reduce the risk of infection:
- Keep Microsoft Office security patches up-to-date.
- Implement attachment filtering to reduce the likelihood of malicious content reaching a user’s workstation.
- Do not open attachments from unfamiliar or unknown senders.
- Always be suspicious of unexpected emails, especially financial or delivery correspondence, documents or links.
- Regularly train users to be aware of potential phishing efforts and how to handle them appropriately.
- Convert attachments to another format, for example, converting Microsoft Office documents to PDF documents can be an effective method of neutralizing malicious content.
- Never enable macros, and do not configure Microsoft Office to enable macros by default.
Endnotes
- https://lmntrix.com/lab/valyrian-trojan-a-cut-above-the-rest/
- https://blog.talosintelligence.com/2020/02/threat-roundup-0221-0228.html
- https://lmntrix.com/lab/valyrian-trojan-a-cut-above-the-rest/











