Author: Christopher Kim
1. Overview
On 20 October, Infoblox observed a malicious email campaign distributing the infostealer Vidar and using a SWIFT payment theme in the messages. The features of the Vidar file used in this campaign closely resembled those of the Vidar file we observed last year.1
2. Customer impact
Vidar was first discovered in October 2018.2 It is written in C++ and is a variant of the Arkei infostealer. The developers of Vidar sell it as a malware-as-a-service (MaaS), and cyber criminals can customize and control it through a web control panel.
After compromising a victim’s machine, Vidar exfiltrates data from web browsers, cryptocurrency wallets, messenger software, and two-factor authentication software.
3. Campaign analysis
All emails in this campaign had the subject line Pro-Forma Invoice- 8552616 Oil_Field_Meterials EXW 19/10/2021, the From name Crayonsglobal. Passive DNS (pDNS) indicates that the IP address used to send the emails is mapped to nearly 50 other domains that host Vidar and other malicious payloads. Many of these domains use a Dynamic DNS and the web-hosting provider that appears to be widely abused by phishing and malware campaigns, including those conducted by advanced persistent threat (APT) groups.3
4. Attack chain
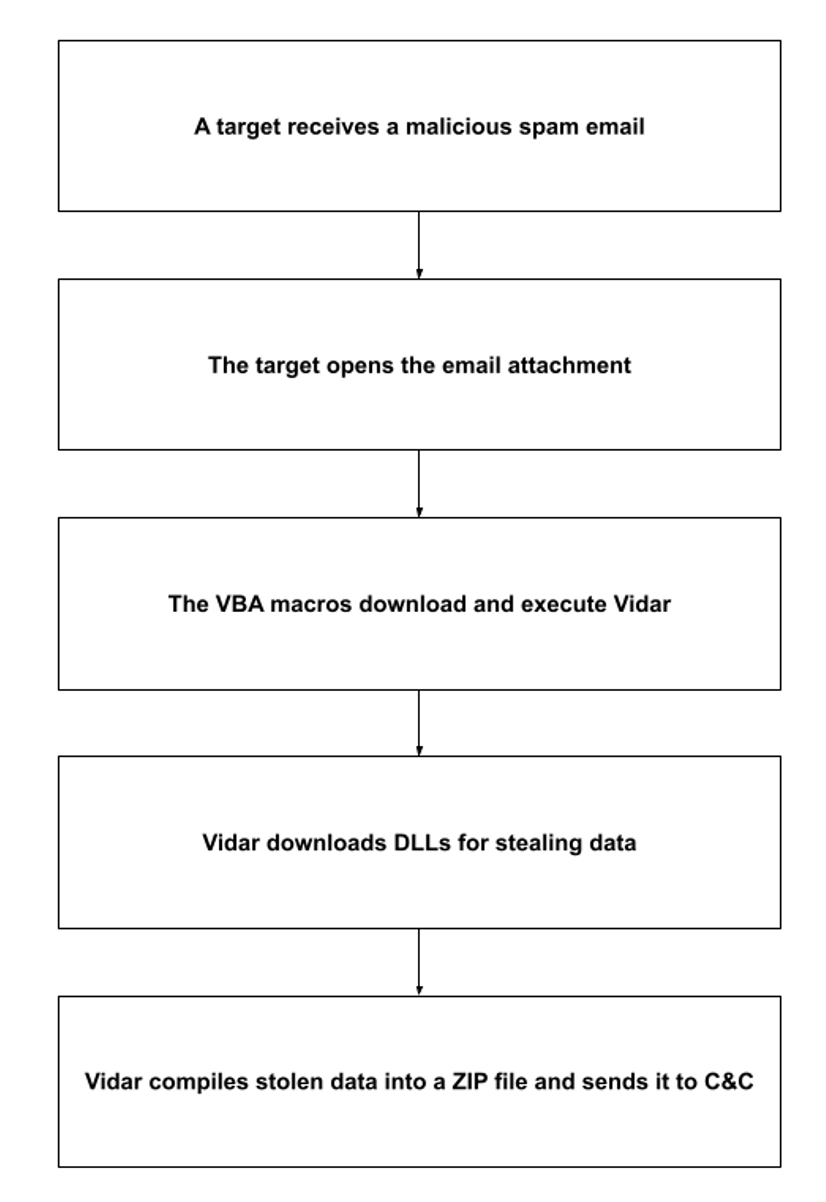
The infection chain begins when a recipient opens the email attachment, Invoice- 245678909 Oil_Field_Swift_remmitance.doc. The Visual Basic for Applications (VBA) macros embedded in the document execute a script, leastenter.cmd, which launches PowerShell to download the Vidar executable, write it to \Documents\littlelittle.exe, and then execute it.
Next, Vidar downloads several dynamic-link library (DLL) files that allow access to data of various applications. Vidar uses these dependencies to steal data, compiles it into a ZIP file, and sends it back to the C&C. Finally, Vidar deletes itself and all the libraries it downloaded.
5. Vulnerabilities and mitigation
Vidar can severely damage an organization’s financial well-being and reputation. Organizations should reduce their attack surface by strengthening security in two areas: (1) handling of emails, which are Vidar’s primary attack vector, and (2) DNS, which Vidar uses to find locations for downloading payloads. We recommend the following actions for reducing the possibility of succumbing to an attack by Vidar:
- Be cautious of emails from unfamiliar senders, and inspect unexpected attachments before opening them.
- Always be suspicious of unexpected emails, especially those that appear to be financial or delivery correspondences and contain documents or links.
- Never enable macros. They are a very common infection vector used by many families of malware.
- When monitoring HTTP traffic, filter for requests missing a User-Agent string. Such requests might be indicative of non-human activity and malicious programs.
Endnotes
- https://blogs.infoblox.com/cyber-threat-intelligence/vidar-infostealer/
- https://fumik0.com/2018/12/24/lets-dig-into-vidar-an-arkei-copycat-forked-stealer-in-depth-analysis/
- https://www.ptsecurity.com/ww-en/analytics/pt-esc-threat-intelligence/shadowpad-new-activity-from-the-winnti-group/