Author: Victor Sandin
TLP: WHITE
Overview
On 12 April, Infoblox observed a malicious email campaign distributing Formbook malware via Microsoft Office documents containing malicious macros. Emails in this campaign lure victims into opening a spoofed purchase invoice from Hyundai, and into enabling macros to access the document’s content.
Infoblox has reported on Formbook campaigns several times in the past;1,2,3 they have had common patterns of financial-themed lures and other urgent topics such as the Coronavirus.
Customer Impact
Formbook is a well-known infostealer and form grabber malware that is sold as malware-as-a-service4 (MaaS) in underground forums. Its capabilities include evasion techniques such as process hollowing, webform hijacking, keylogging and clipboard monitoring, as well as communication with a command and control (C&C) server.
Campaign Analysis
In this campaign, victims received an email urging them to open the attached purchase invoice with the subject line PI Payment. The file attachment was a Microsoft Excel spreadsheet (XLS) containing a malicious macro that connects to threat actors C&C servers and downloads Formbook malware.
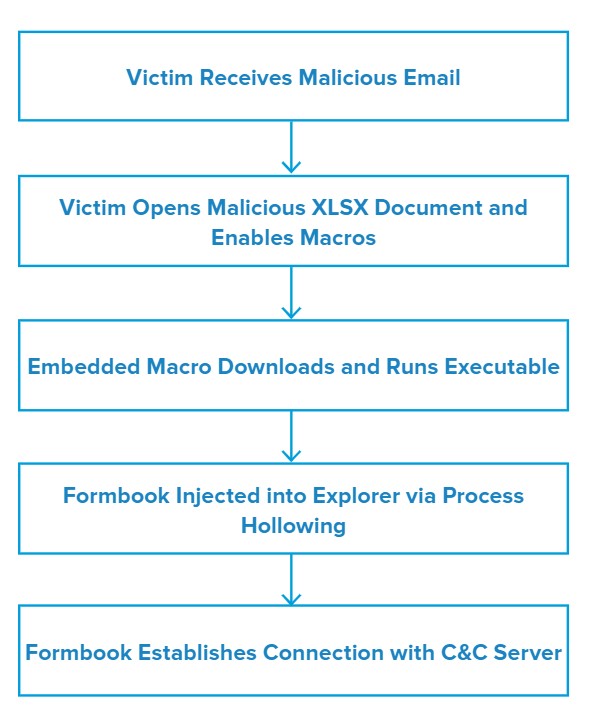
Attack Chain
When the victim opens the document and enables macros, the embedded code downloads a portable executable (PE) and writes it to C:\Users\Public\vbc.exe.
Next, the macro runs the executable, which spawns a new Explorer process and injects Formbook code into it using a technique known as process hollowing.
Finally, the malware connects to its C&C server to receive additional instructions.
Vulnerabilities & Mitigation
Infoblox recommends the following to reduce and mitigate the risk of this type of infections:
- Be cautious of emails from unfamiliar senders and verify important or legitimate attachments with sender via alternative means (e.g. by phone or in person) before opening them.
- Pay special attention to emails with financial or delivery themes which lure users into opening their attachment for full details.
- Configure Microsoft Office to disable macros by default and be cautious if the file’s only apparent contents are directions to enable macros.
- Apply security updates and keep software up-to-date with the latest patches to remove and mitigate vulnerabilities that can be abused.
- Increase security awareness in your organization by providing courses to train them on how to identify and notify about suspicious emails.
Endnotes
- https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–91
- https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–67
- https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–58
- https://www.blueliv.com/cyber-security-and-cyber-threat-intelligence-blog-blueliv/research/selling-formbook/





