Author: Christopher Kim
TLP: WHITE
Overview
On 9 June, Infoblox discovered a malspam campaign that impersonated a shipping logistics business and distributed the LokiBot infostealer. Over time, many LokiBot campaigns have used shipping-themed messages to lure users into opening weaponized documents that download the malware.1,2
Customer Impact
LokiBot is a commodity malware commonly sold on the dark web. This infostealer is a hybrid malware that can attack both Android and Windows operating systems. Threat actors typically distribute the malware via spam emails, private message applications, such as Skype, and malicious websites. LokiBot has built-in capabilities for tracking users’ activities by recording keystrokes with a keylogger, as well as stealing the following types of data:
- passwords and login credentials from web browsers,
- private keys from cryptocurrency wallets, and
- data from mobile banking applications and communication apps.
Campaign Analysis
Threat actors used InMotion Hosting email servers and the compromised email account xiaohui@euroswift[.]sg to send all the emails in this campaign. All emails had the subject VSL: MV Hyundai Integral, ORDER: TSA-A090621B and lured recipients into opening the attached document to bid for the container ship Hyundai Integral. The email message included a signature crafted to appear as if it came from an employee at Dolphin Logistics, a legitimate cargo agent based in Thailand.
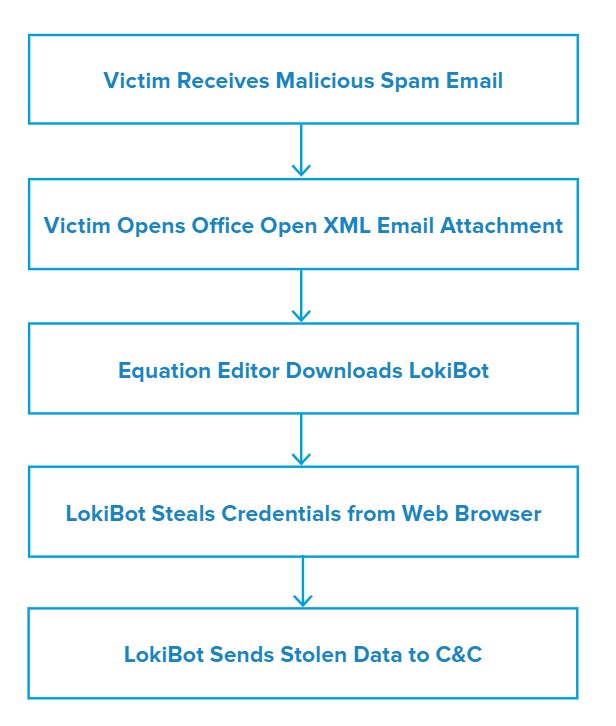
Attack Chain
When the victim opens the Microsoft Office Open XML email attachment named MV Hyundai Integral.docx, the file exploits the CVE-2017-118823 Stack Overflow vulnerability in Equation Editor (EQNEDT32.EXE) to download LokiBot malware. Equation Editor then writes the file to C:\Users\Public\vbc.exe and executes it.
LokiBot writes itself to C:\Users\admin\AppData\Roaming\F63AAA\A71D80.exe and then steals credentials from the victim’s web browser by reading from C:\Users\admin\AppData\Roaming\Mozilla\Firefox\profiles.ini. Finally, it sends stolen data to its command and control (C&C).
Vulnerabilities & Mitigation
Infoblox recommends the following actions to reduce the risk of this type of infection:
- Keep antivirus signatures and engines updated.
- Turn on automatic updates for the operating system to receive the latest security patches.
- Exercise caution when opening email attachments, especially if they come from an unknown sender.
- Subscribe to a comprehensive threat intelligence feed to strengthen firewalls.
- Enable two factor authentication on services (e.g. banking app) that show sensitive information.
Endnotes
- https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–62
- https://www.infoblox.com/wp-content/uploads/threat-intelligence-report-lokibot-campaign-uses-microsoft-office-exploit.pdf
- https://nvd.nist.gov/vuln/detail/CVE-2017-11882








