Author: Eric Patterson
TLP: WHITE
Overview
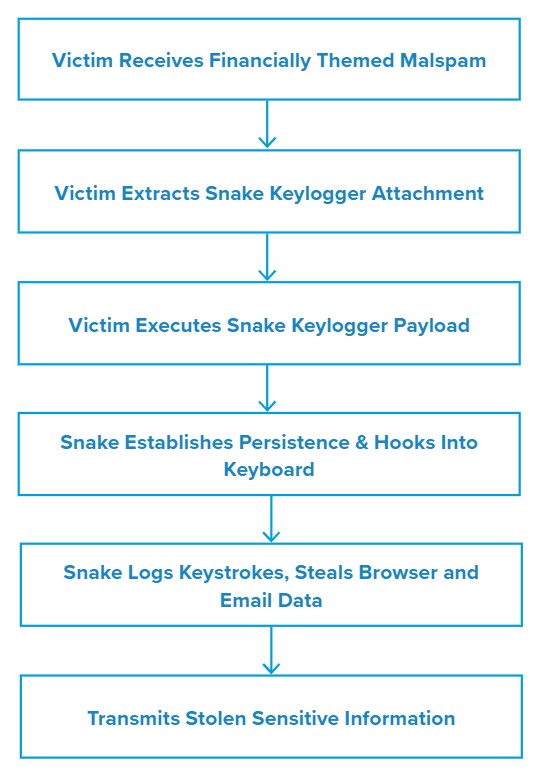
During the week of 14 January, we observed a malspam campaign distributing the Snake Keylogger. The emails in the campaign contain a malicious 7-ZIP archive that opens an SCR file and downloads the malware to the victim host.1,2
Customer Impact
Snake Keylogger (a.k.a. 404 Keylogger)3 is an infostealer that can steal a victim’s sensitive information, log keyboard strokes, take screenshots and extract information from the system clipboard.4 Those infected with Snake can potentially face anything from identity theft to fraudulent financial transactions depending on the type of information siphoned by the keylogger.
Campaign Analysis
As in previous 404 Keylogger campaigns we have observed,5 this malspam campaign was financially themed and contained subject lures such as STATEMENT OF ACCOUNT NOVEMBER DECEMBER 2020. The mails also carried a compressed ZIP archive attachment with an R03 file extension. The observed sender was Qtech Admin and used the email address ungkwangmedtech[@]gmail[.]com.
Attack Chain
When the victim extracts and executes the 7-ZIP archive, an executable (EXE) file of the same name will drop onto the user’s Desktop (C:\Users\
The malware then attempts to discover and steal mail credentials by accessing any saved profiles present on the machine (e.g., Outlook), as well as steal sensitive browser information from the local cookie and login data files found under the AppData directory (i.e. for Google Chrome).
If it is successful in gathering information, Snake will use a known-good IP lookup service (checkip.dyndns.org) to get the victim IP address. It will also query the system to gather other information such as the Windows version.
While we did not observe exfiltration for this campaign, Snake is able to transmit information via email, FTP, SMTP, Pastebin or the messaging app Telegram.
Vulnerabilities & Mitigation
Infoblox recommends the following to reduce the risk of this type of infection:
- Be cautious of emails from unfamiliar senders and inspect unexpected attachments before opening them. Especially if they use commonly used themes such as shipping or financial documents or advice.
- Configure firewall rules properly to block unusual traffic.
- Verify important or potentially legitimate attachments with the sender via alternative means (e.g., by phone or in person) before opening them.
Endnotes
- https://www.virustotal.com/gui/file/7eb2de2bfd05ee1e83980aa914486789d2e8f3fb3cc6e166f140302fdaf40cd9/details
- https://www.virustotal.com/gui/file/4b08d69d6bdb81f338710851e3631513f0360187e68ef07bf71665ef33783364/community
- https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–89
- https://www.enigmasoftware.com/snakekeylogger-removal/
- https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–89
- https://www.joesandbox.com/analysis/338942/0/html#6904E7E6EE6EF97FF797562C91E0FF401AC4










