Author: James Barnett
TLP: WHITE
Overview
On 2 June, security researcher Brad Duncan reported on a malspam campaign from the threat actor known as Shathak (a.k.a. TA551) distributing the IcedID banking trojan.1
We previously reported on an IcedID campaign in November 2020 in which Shathak distributed the malware via Japanese language malspam.2 We also published on a campaign in July 2020 wherein threat actors used a Valak downloader to deliver IcedID.3
Customer Impact
IcedID is a banking trojan that uses web injection and redirection attacks to steal banking credentials, credit cards, and other financial information from victims who believe they are entering their information into a secure website.
Campaign Analysis
The emails in this campaign followed Shathak’s standard operating procedure of distributing malicious Microsoft Word documents within password-protected ZIP file attachments. The report did not provide examples of the emails themselves, but based on previous campaigns, Shathak likely used falsified replies as subject lines and included a short lure in the body text that prompted the recipient to open the attached ZIP file using a numerical password included in the email.
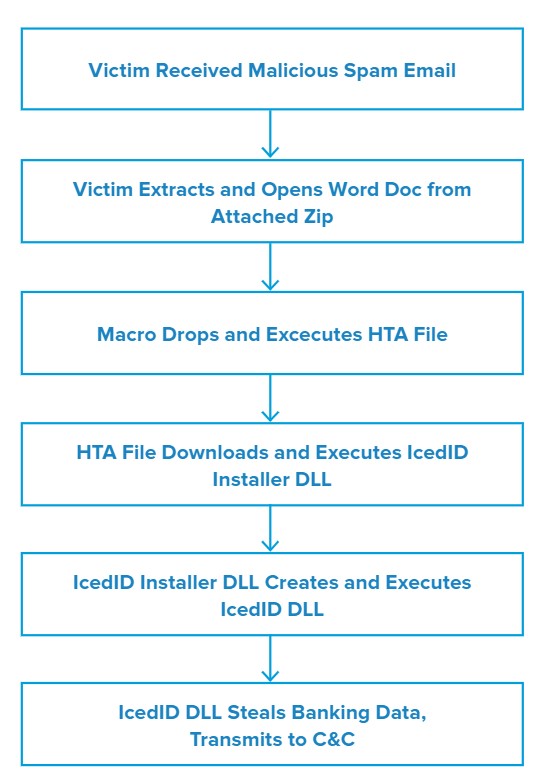
Attack Chain
When the victim extracts the ZIP archive using the included password and opens the Word document inside, the document displays the following message:
This document created in a previous version of Microsoft Office Word. To view or edit this document, please click “Enable editing” button on the top bar, and then click “Enable content.”
Once the victim does so, a malicious macro drops a malicious Microsoft HTML Application (HTA) and executes it via Windows Management Instruction (WMI). The HTA file then attempts to download and execute the IcedID installer dynamic-link library (DLL) from one of several domains controlled by the attacker. Inthis campaign, the malware saved the installer DLLs with a .JPG file extension to obfuscate their intended purpose.
When the IcedID installer DLL executes, it downloads an additional file from a remote server and uses it to build and execute a persistent version of the IcedID DLL at C:\Users\[username]\AppData\Local\[username]\Tetoomdu64.dll. The persistent IcedID DLL then monitors the victim’s system and uses web injection techniques to redirect the victim to one of IcedID’s proxy servers whenever they try to visit a website that may contain credentials valuable to the attacker (e.g. financial institutions).
When the victim is redirected to the IcedID proxy server, it will show them a page that appears identical to the legitimate login page of the website they were attempting to visit. However, if the victim enters their login details on this page, the proxy server will send their credentials to the attacker for later abuse before forwarding them to the actual website the victim intended to visit. The victim will then be logged into the legitimate version of the website, leaving them with no obvious indication that their credentials have just been stolen.
Vulnerabilities & Mitigation
Infoblox recommends the following actions to reduce the risk of this type of infection:
- Always be suspicious of vague emails, especially if there is a prompt to open an attachment or click on a link.
- If clicking on a link immediately initiates an attempt to download a file, that file is suspicious. Inspect it carefully.
- Never enable macros, and do not configure Microsoft Office to enable macros by default.
Endnotes
- https://www.malware-traffic-analysis.net/2021/06/02/index.html
- https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–95
- https://blogs.infoblox.com/cyber-threat-intelligence/valak-downloader-infostealer-delivers-icedid-banking/








