Author: Laksh Sethi
1. Overview
From 22 to 27 October, Infoblox observed multiple related malspam campaigns distributing the remote access trojan (RAT) Adwind via weaponized Java and JavaScript files. Emails in these campaigns present themselves as coming from a logistics bureau, Al Bahr Al Arabi, and The United Bank of Egypt.
Adwind RAT is a cross-platform, multi-functional malware. It is openly distributed as a paid malware-as-a-service (MaaS), which cyber criminals can customize and control.
2. Customer impact
Adwind originated in Mexico and was discovered in 2012, when it was known as Frutas RAT. Adwind can control the infected machine’s webcam, capture screenshots and sensitive data, install and run applications, run commands remotely, collect data, and perform other tasks.
3. Campaign analysis
Emails in these campaigns have no body and portray themselves as coming from email addresses associated with an unidentified logistics bureau; Al Bahr Al Arabi, which is the name of a marine engineering services company based in the United Arab Emirates; and the United Bank of Egypt. Each email contains an attachment: a JavaScript file named ORDER_21108899.js or a Java file named Payments_Copy.jar, mt103_usd78654_pdf.jar, or ORDER_211099A_pdf.jar. The subject line is Fw: Payment Copy, PO 04399021, Fw: Order, or ORDER #211099A.
4. Attack chain
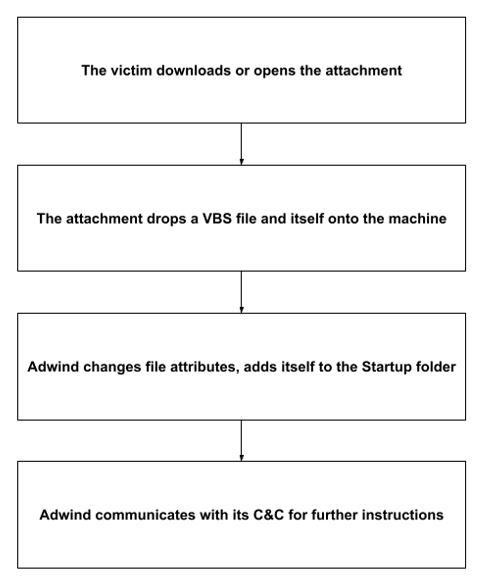
Adwind obtains supported languages, the computer name, and other data from a victim’s system. It then uses (1) icacls.exe to change Java Usage Tracker’s access permissions to everyone, (2) javaw.exe to prevent any console or window from opening while it performs its tasks, and (3) java.exe to read encrypted Java code from plain-text and class files that contain further instructions.
To achieve persistence, Adwind drops itself into the Startup folder. To hide itself, it changes its file attributes by using attrib.exe. Finally, it attempts to connect to its command and control (C&C) IP and, if it succeeds, serves as a remote-controlled backdoor to the victim’s machine.
5. Vulnerabilities and mitigation
Infoblox recommends the following actions for reducing the risk of infection by Adwind RAT:
- Keep antivirus signatures and engines up to date.
- Turn on automatic updates, to keep the operating system up to date with the latest security patches.
- Do not expose email addresses to the internet.
- Do not open email attachments with extensions that look unfamiliar.
- Exercise caution when opening all email attachments, especially those that come from unfamiliar senders.
- Avoid opening emails with generic subject lines.
- Prevent JAR files from running in %AppData%/[random folder name], and prohibit the creation of JAR files in the same folder.