Author: Yadu Nadh
TLP: WHITE
Overview
On 23 March, the Federal Bureau of Investigation reported on a variant of the disk-encrypting ransomware HDDCryptor, also known as Mamba. Specifically, it weaponizes DiskCryptor, a legitimate and open source full-disk encryption software.1
Threat actors previously used Mamba to infect victims in Brazil and Saudi Arabia, as well as attack the San Francisco Municipal Transportation Agency (SFMTA) in November 2016.2
Customer Impact
The cybersecurity community first discovered Mamba ransomware in 2016.3 It has been deployed against:
- local government,
- public transportation agencies,
- legal services,
- technology services,
- industrial,
- commercial,
- manufacturing, and
- construction businesses.
The threat actors behind Mamba encrypt the victim’s drive and operating system with a weaponized version of DiskCryptor. The ransomware’s capabilities include privilege escalation via exploit.
Campaign Analysis
Threat actors distribute Mamba via malspam and can compromise the victim’s network via Remote Desktop Protocol (RDP).
Once the malware encrypts the victim’s system, it displays a ransom note with the actor’s email address, ransomware file name, the host system name, and a place to enter the decryption key. The ransom note instructs the victim to contact the actor’s email address to pay the ransom in exchange for the decryption key. The threat actor adjusts the payment based on the scale of the infection and demands it to be made via Bitcoin.4
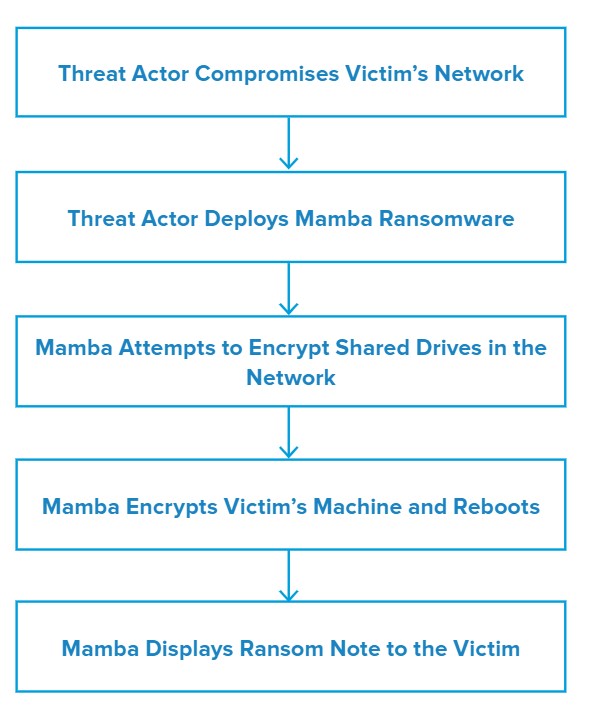
Attack Chain
Mamba uses a PsExec5 command to launch itself into remote systems running in the network and encrypt the compromised systems.
Along with DiskCryptor, Mamba uses a program that installs and starts disk encryption in the background using an encryption key chosen by the attacker. The attacker passes this key via the command-line parameter: [Ransomware Filename].exe
The ransomware works in two stages. The first stage, also known as the preparation stage:
- Creates the folder C:\Users\Public\,
- Drops DiskCryptor components into the folder,
- Installs the DiskCryptor driver,
- Registers a system service called myCryptographyService, and
- Reboots the victim machine.
The second stage, or encryption stage:
- Sets up a bootloader to the master boot record (MBR).
- Encrypts disk partitions using DiskCryptor oftware, and
- Reboots the victim machine.
The encryption key and the shutdown time variable are saved to the configuration file (myConf.txt). This file is readable until the second restart, which occurs approximately two hours later and concludes the encryption, as well as displays the ransom note.
If any of the DiskCryptor files are detected, attempts should be made to determine whether the myConf.txt is still accessible. If so, then the password can be recovered without paying the ransom. This opportunity, however, is limited to the point in which the system reboots for the second time.
Vulnerabilities & Mitigation
Organizations can reduce the risk and impact of Mamba ransomware6 with these practices:
- Implement network segmentation.
- Require administrator credentials to install software.
- If DiskCryptor is not used by the organization, add the key artifact files used by DiskCryptor to the organization’s execution blacklist. Any attempts to install or run this encryption program and its associated files should be prevented.
- Implement a recovery plan to maintain and retain multiple copies of sensitive or proprietary data and servers in a physically separate, segmented, secure location (i.e., hard drive, storage device, the cloud).
- Use multifactor authentication where possible.
- Disable unused remote access/RDP ports and monitor remote access/RDP logs.
- Audit user accounts with administrative privileges and configure access controls with least privilege in mind. Install and regularly update anti-virus and anti-malware software on all hosts.
- Disable hyperlinks in incoming emails
Endnotes
- https://www.ic3.gov/Media/News/2021/210323.pdf
- https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/disk-locking-hddcryptor-mamba-ransomware-makes-a-comeback
- https://securityaffairs.co/wordpress/51314/malware/mamba-ransomware.html
- https://thehackernews.com/2017/08/locky-mamba-ransomware.html
- https://www.mindpointgroup.com/blog/lateral-movement-with-psexec/
- https://securelist.com/the-return-of-mamba-ransomware/79403/









