Author: Shashank Jain
TLP: WHITE
Overview
Between 3 and 5 April, Infoblox observed a malicious spam campaign distributing weaponized Microsoft Excel spreadsheets (XLS) containing malicious macros intended to infect victims’ machines with the Agent Tesla keylogger. The threat actor(s) used a spoofed email sender address to gain the victim’s trust by impersonating Petroham Oil & Gas, a legitimate chemical and petrochemical company based in Abu Dhabi.
Customer Impact
Agent Tesla malware is known for its keylogging and credential stealing capabilities, as well as its distribution method as a form of “malware-as-a-service.”
Infoblox has previously reported on Agent Tesla campaigns in Dec 20201 and April 2021.2 Both used the same initial attack vector (malspam) and delivery technique (weaponized XLS files containing malicious macros) as this recent campaign.
Campaign Analysis
In this campaign, the threat actor(s) used the sender email address sales@oryx-ad[.]ae to impersonate the Abu Dhabi-based oil and gas company with the subject line Labour Day holiday RFQ 191938. The email bodies are empty but the messages carry an attachment with the filename RFQ 191938.xls, as referenced by the subject line. All of the XLS files contained malicious macros.
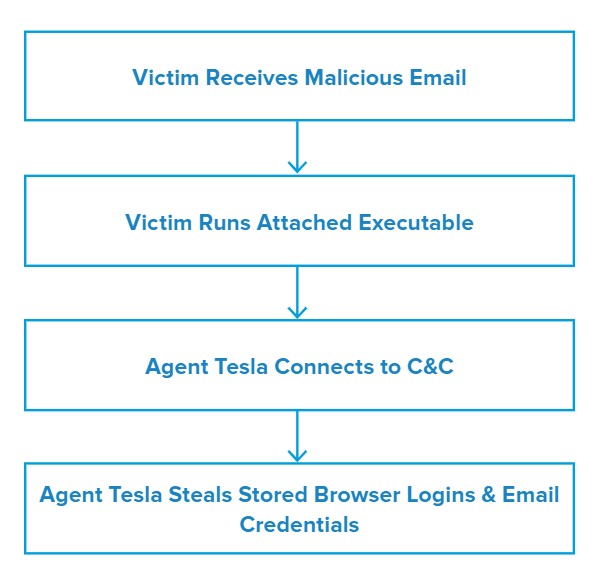
Attack Chain
When the user opens the attachment, they will see the error message “Word experienced an error while trying to open the file.” In the background, cmd.exe (windows legitimate utility) begins to run and executes a PowerShell script via Windows Management Instrumentation (WMI).
The malicious program then creates a scheduled task to achieve persistence and uses the Windows native application aspnet_compiler to compile and connect to the command and control (C&C) server to download the Agent Tesla payload.3 After successful execution of the payload, it starts capturing the victim’s login credentials that have been stored in browsers and registries, while also capturing screenshots using its keylogger abilities.
Vulnerabilities & Mitigation
Malspam attachments containing malicious macros are the primary infection vectors for Agent Tesla. Infoblox recommends the following actions to reduce the risk of this type of infection:
- Keep computers and all endpoints up-to-date with the latest security patches to block known vulnerabilities that threat actors could target.
- Be cautious of emails from unfamiliar senders and inspect unexpected attachments before opening them.
- Always be suspicious of vague or empty emails, especially if there is a prompt to open an attachment or click on a link.
- Implement attachment filtering to reduce the likelihood of malicious content reaching a user’s workstation.
Endnotes
- https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–100
- https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–116
- https://app.any.run/tasks/53454313-851f-4203-95ea-ebcbabc8e745/








