Author: Yadu Nadh
TLP: WHITE
Overview
On June 21, Infoblox observed a malicious email campaign whose emails deliver NanoCore, a sophisticated remote access trojan (RAT). This malware was first discovered in 2013, when it was being sold in underground forums.1
Threat actor(s) mainly spread NanoCore via malspam campaigns, by using phishing emails that contain a variety of attachments, such as IMG, ISO, ZIP, and Microsoft Office files.2 Once executed, the malware allows the threat actor(s) to remotely access the victim’s machine, steal user information, and then send it to the command and control (C&C) servers operated by the actor.
NanoCore has been observed in attacks on high-value targets in Asia, Europe, and the Middle East.
Customer Impact
NanoCore’s features can be expanded via a plugin that enables a backdoor on the victim’s machine. Nanocore’s capabilities include:3
- Remote surveillance via Remote Desktop
- Access to the webcam
- Access to audio feeds
- Connection to the reverse proxy server
- Transfer and execution of files
- Mining for cryptocurrency
- Backdoor commands
- Information theft.
Campaign Analysis
The campaign we observed uses a shipment theme to lure a target with a weaponized Microsoft Excel attachment. The email has the following subject, and no body:
RE: FINAL HAWB/ DN NEW CHINA/HONG KONG SHIPMENT 21JUNE/ ETD 27 JUNE 1600kgs 2106015
Similar emails have been used in other campaigns that involve NanoCore. They have been distributed with a variety of phishing themes and have carried different attachments.
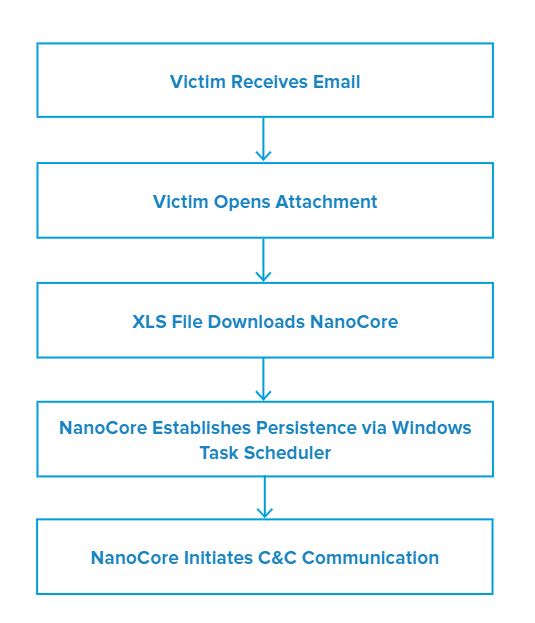
Attack Chain
Opening the malicious Excel attachment CI_PL_BL_AWB 988-33669786.xlsx triggers EQNEDT32.EXE, which exploits CVE-2017-11882, a vulnerability in Microsoft Equation Editor. It runs an embedded shellcode that downloads and executes a .NET binary from a remote server.
After the binary is executed, NanoCore proceeds to gain persistence by creating a Windows schedule task. Subsequently, the malware tries to establish a C&C (command and control) communication to a remote server
Vulnerabilities & Mitigation
Malspam email campaigns are a common distribution method for malware. Infoblox recommends the following precautions for reducing the possibility of an infection:
- Always be suspicious of unexpected emails that contain documents and links, especially emails regarding financial or delivery correspondences.
- Avoid opening emails with generic subject lines
- Do not enable macros in Microsoft Office attachments, especially if the file’s only apparent contents are directions for enabling macros.
- Never configure Microsoft Office to enable macros by default. Many malware families use macros as an infection vector.
- Before opening an attachment that seems to have come from a legitimate source, check (via phone or in person) with the sender the email appears to have come from.
Endnotes
- https://blog.morphisec.com/nanocore-under-the-microscope
- https://success.trendmicro.com/solution/1122912-nanocore-malware-information
- https://spanning.com/blog/nanocore-rat-malware-of-the-month/








