Author: Eric Patterson
TLP: WHITE
Overview
On 12 March, Infoblox observed a malspam email campaign distributing the Dridex banking trojan via emails spoofing updated/adjusted invoice notifications from the shipping company Freight Quote.
Previous Infoblox reporting has highlighted Dridex campaigns distributing malspam masquerading as legitimate emails from organizations such as Intuit and Automatic Data Processing, Inc. (ADP).1,2
Customer Impact
Dridex was first discovered in 2011 and has been a prolific banking trojan available on darknet markets.3 Threat actors historically favor this malware for larger scale, financially-motivated malspam campaigns.
Once a victim is infected, Dridex employs its core features of form grabbing and website injections to siphon online banking credentials and pilfer funds from the victims.
Campaign Analysis
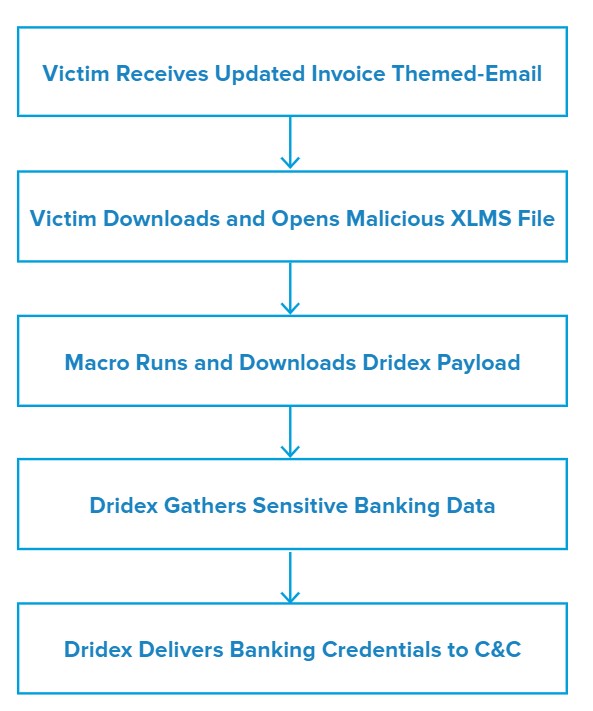
Emails in this campaign imitate financial invoices with subject lines similar to: Updated Invoice(s) with Adjustment. The fake invoice attachment is a Microsoft Office Excel (XLSM) macro-enabled file following the naming convention: Inv<9-11 digit number>.xlsm.
Attack Chain
Downloading and opening the attached XLSM presents the user with a spoofed invoice statement portraying itself to be from Freight Quote. Once the victim enables macros, the Excel document appears to stop responding and prompts the user to close the document.
During this time, the macro code attempts to beacon to several domains in order to download a stage two payload that would install Dridex on the victim machine. We were not able to download this second stage payload. However, had we been successful, the malware would presumably follow a conventional Dridex execution flow and attempt to hook into legitimate Windows processes to evade detection.
Once installed, Dridex will attempt to uncover and steal sensitive banking information belonging to the victim and transmit that to one of its active command and control (C&C) channels via secure socket layer (SSL).
Vulnerabilities & Mitigation
Dridex is a banking trojan with credential stealing functions. Infoblox recommends the following methods for detecting, preventing and mitigating Dridex attacks:
- Install and run advanced antivirus software that can detect, quarantine and remove malware.
- Be cautious of emails from unfamiliar senders and inspectunexpected attachments before opening them.
- Develop traffic rules that can block outbound access topotentially malicious endpoints based on domains orunique URI parameters.
- Install strong email security solutions to detect emails withsuspicious content.
- If clicking on a link immediately initiates an attempt todownload a file, that file is suspicious. Inspect it carefully.
- Never enable macros, and do not configure Microsoft Office to enable macros by default.
Endnotes
- https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–72
- https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–51
- https://www.globenewswire.com/news-release/2020/04/09/2014156/0/en/March-2020-s-Most-Wanted-Malware-Dridex-Banking-Trojan-Ranks-On-Top-Malware-List-For-First-Time.html





