Author: Christopher Kim
TLP: WHITE
Overview
On 30 March, Infoblox observed a malspam campaign using an economic support-themed message to lure Italian-speaking victims into opening a malicious attachment that delivers Ursnif, a widely distributed banking trojan. The tactics, techniques, and procedures (TTPs) we observed in this campaign are consistent with recent Ursnif reports.1
Customer Impact
Ursnif is a variant of the Gozi banking trojan (first discovered in 2007)2 and is typically spread via phishing emails. Threat actors primarily use this malware for data theft. Its capabilities include:
- stealing computer system information, including operating system (OS) versions and running processes,
- stealing user credentials related to financial and banking services,
- communicating with command and control (C&C) for data exfiltration and to download additional malware components, and
- executing backdoor commands from remote attackers.
The majority of Ursnif campaigns within the last few months appear to have targeted Italian-speaking users.3,4 Notably, in early March, Avast identified an Ursnif infection that led to over 1,700 stolen credentials from a single payment processor.5
Campaign Analysis
The campaign we observed continuously sent spam emails to potential victims for several hours. All emails contained the same message and spoofed the Instituto Nazionale Previdenza Sociale (INPS), Italy’s social security administration. Email subject lines consisted of one generic Italian word followed by a string of random digits (4-10 characters long), such as Aggiornamento {digits}, PROPOSTA {digits}, and Licenza {digits}.
The email message was also written in Italian and informed recipients that they were qualified for economic support under legislative decree number 148 as a response to the ongoing pandemic. All messages included the same password – allegato21 – and instructed recipients to use it to unlock the password- protected attachment and fill out the embedded application.
This campaign also used compromised email accounts, as well as generic from names (e.g. help, contact, members) to send the messages.
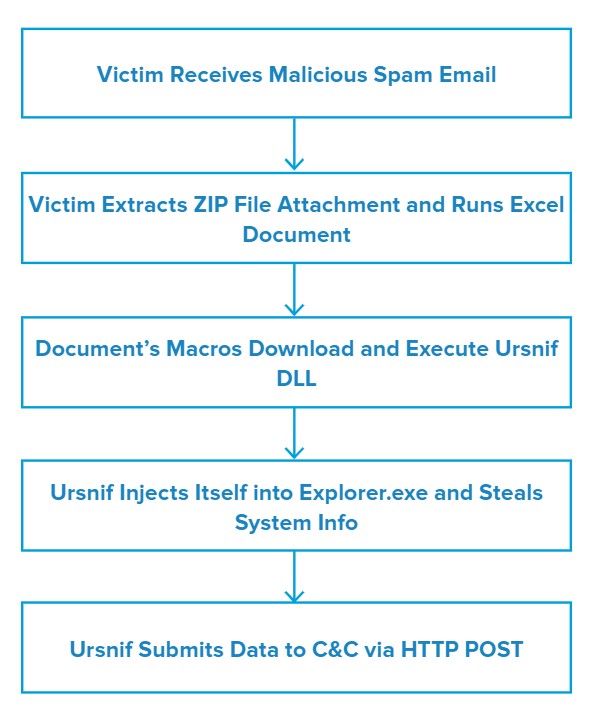
Attack Chain
In one of the emails, we found a Microsoft Excel document named lista_575.xlsb after extracting the ZIP file attachment with the password contained in the email message.
When we executed the spreadsheet, the macro embedded in the document downloaded a dynamic-link library (DLL) file and wrote it to C:\Users\Admin\AppData\Local\Temp\signin.jpg.dll. The actors behind this campaign used geofencing6 to limit the distribution of the DLL payload to only users geolocated in Italy. After this, the macro executed the DLL with the Windows program, RegSvr32.exe.
Next, Ursnif spawned a new explorer.exe process and injected its code into it. This rogue process then injected itself into the legitimate explorer.exe, which allowed Ursnif to run credential stealing functions. Ursnif then formatted the stolen information into key-value pairs that included various identifiers, such as software, version, user, server, and ID.
The malware encrypted the key-value pair string into ciphertext, and then encoded it with base64. Finally, it appended the .dwg file extension to the encrypted string and submitted it to the C&C server over HTTP.
Vulnerabilities & Mitigation
Infoblox recommends the following to reduce the risk of this type of infection:
- Ursnif spawns its own explorer.exe and injects its code into it. This is unusual behavior for a legitimate application and a well-performing security tool should flag this process behavior.
- Be cautious of emails that provide plain text passwords in the message to open attachments.
- Subscribe to Infoblox threat feeds that contain curated C&C domains. This data can be coupled with DNS Response Policy Zones (DNS RPZ) to disrupt malicious C&C communications.
- Monitor firewall logs for unusual HTTP requests. Ursnif HTTP POST traffic contains unusually long and high entropy uniform resource identifiers (URI) since the malware sends stolen data via encrypted HTTP parameters.
Endnotes
- https://success.trendmicro.com/solution/000283513
- https://www.zdnet.com/article/gozi-virus-mastermind-ordered-to-pay-7-million-in-damages/
- https://www.fortinet.com/blog/threat-research/new-variant-of-ursnif-continuously-targeting-italy
- https://www.zdnet.com/article/ursnif-trojan-has-targeted-over-100-italian-banks/
- https://blog.avast.com/ursnif-victim-data








