Author: James Barnett
1. Overview
On 8 September, Infoblox observed a malspam campaign that used DocuSign-themed lures to entice users to download and open Microsoft Word documents with malicious macros that installed embedded copies of the trojan downloader Hancitor.
We have written about previous Hancitor campaigns in April 2020,1 December 2020,2 March 2021,3 and June 2021.4 Hancitor’s core characteristics have not changed, but in this campaign, Hancitor has yet another URL-redirection stage that precedes the delivery of the malicious document payload.
2. Customer Impact
Hancitor targets businesses and individuals around the world. Threat actors distribute it via malspam sent by compromised servers in the United States, Japan, Canada, and many other countries. To entice the targets into downloading weaponized Microsoft Office documents, the malspam mimics notifications from legitimate organizations.
3. Campaign Analysis
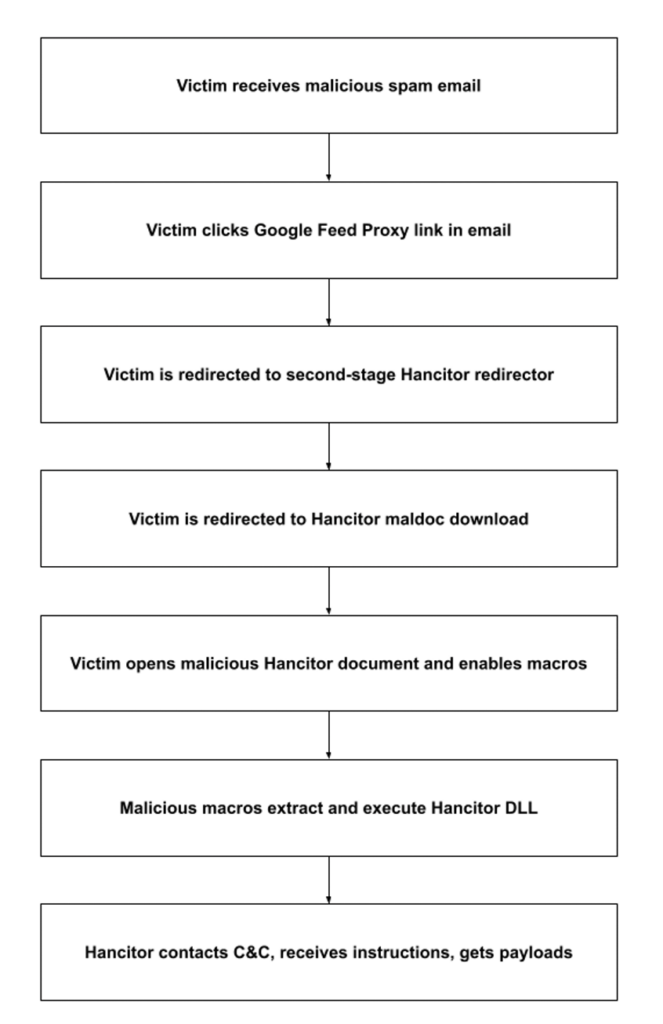
An email in this campaign uses a DocuSign-themed lure to entice a target into opening a link in the message. The subject line indicates that the target has a pending invoice or notification from DocuSign. Embedded in the email is a link that uses Google’s Feed Proxy service to redirect the target to a compromised website that hosts a second redirector, which ultimately points to a malicious Microsoft Word document uploaded to Microsoft OneDrive.
4. Attack Chain
Upon clicking the link in the initial Hancitor malspam email, the victim is redirected to a website that immediately downloads a malicious Word file from Microsoft OneDrive (Hancitor has several websites like this). When the victim opens this file, it displays a message instructing the victim to enable content. Opening the message executes the malicious macros in the document. The macros then extract and execute the Hancitor payload’s dynamic link library (DLL) embedded within the Word document, thus establishing the initial Hancitor infection.
After infecting the victim’s system, Hancitor sends basic information about the system to one of its hardcoded command and control (C&C) servers. The server responds with further instructions, which normally direct Hancitor to download and execute one or more additional malware payloads. We did not observe any additional payloads in this campaign, but the most common payloads in recent Hancitor campaigns have been the Cobalt Strike penetration-testing tool and Ficker Stealer infostealer. The lack of payloads in this campaign may indicate that the threat actor has enhanced the malware by adding methods for avoiding detection; however, we cannot confirm or deny this without further analysis.
5. Vulnerabilities and Mitigation
Hancitor uses several advanced detection countermeasures to bypass antivirus software and firewall-based security. The best way for users to protect themselves from Hancitor is to be wary of links in incoming emails. Namely, a user should:
- Before clicking a link in an email, ensure that the link points to the domain of the company where the email appears to have originated. For example, if the sender is FedEx, that domain would be http://fedex[.]com.
- If clicking a link immediately causes a file to download, delete the file immediately, without opening it.
- Avoid enabling macros in a Microsoft Office attachment, especially if the file’s only apparent content is a message with instructions for enabling macros.
Endnotes
1. https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–69
2. https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–96
3. https://blogs.infoblox.com/cyber-threat-intelligence/cyber-campaign-briefs/hancitor-downloader-delivers-cobalt-strike-and-ficker-stealer/
4. https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–125











