Author: Nick Sundvall
1. Overview
On 5 and 6 October, Infoblox observed that a malspam campaign was distributing the remote access trojan (RAT) Ave Maria through a Microsoft Word file. The threat actors were using a DHL-themed lure to entice the targets into opening the malicious attachment. Ave Maria was first seen at the end of 2018,1 and cybersecurity company Yoroi first reported on it at the beginning of 2019.2 We have previously reported on Ave Maria campaigns in 20193 and 2020.4
2. Customer impact
The malware—dubbed Ave Maria due to a string in its code but marketed and sold as WARZONE RAT (the most basic version goes for as low as $22.95 a month)—is capable of remotely controlling infected machines, exfiltrating stolen credentials and other information to a command and control (C&C) server, taking screenshots, controlling webcams, logging keystrokes, and more.
The threat actors advertise regular updates to the malware, as well as a variety of exploits, to install the malware onto a victim’s computer.
3. Campaign analysis
The DHL-themed subject of the email, DHL NOTIFICATION: INV,PL AND BL, and part of its body, Kindly confirm if the address is Correct in tracking page attached, tried to lure the target into opening the malicious attachment.
4. Attack chain
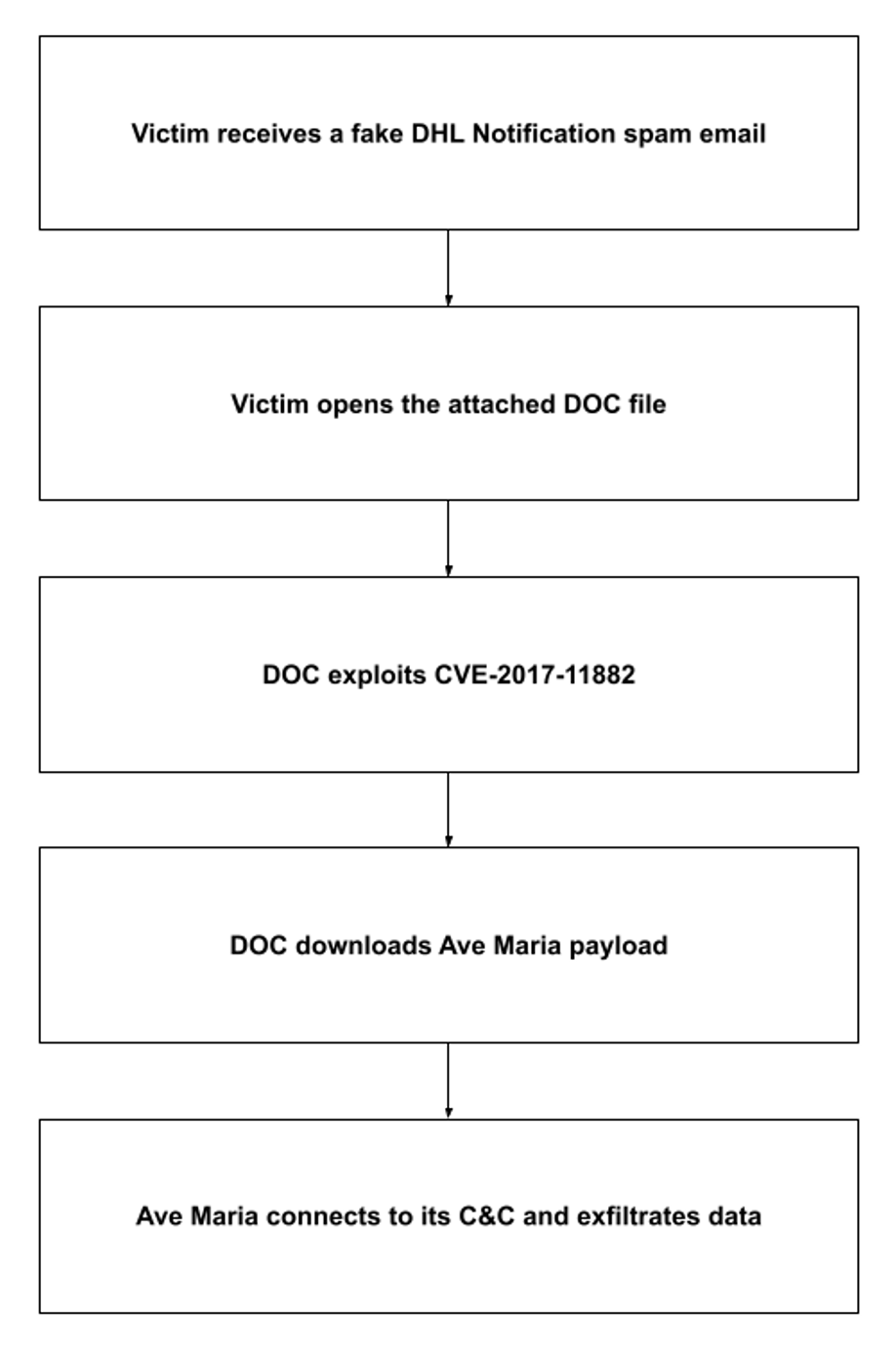
Opening the attached DHL_AWB_INV_PL_BL.doc launches an exploit of CVE-2017-11882: a vulnerability in Microsoft Equation Editor. The file then downloads and executes falcadhgy.exe, the Ave Maria payload. Ave Maria then connects to its C&C and sends it the stolen credentials.
5. Vulnerabilities and mitigation
Because malspam emails are a common distribution method for malware, Infoblox recommends the following precautions used to avoid malspam attacks:
- Always be suspicious of vague or empty emails, especially those with a prompt to open an attachment or click a link.
- To block known vulnerabilities that could be targeted by threat actors, keep computers and all endpoints up to date with the latest security patches.
- Scan downloaded files with antivirus software.
Endnotes
- https://any.run/malware-trends/avemaria1
- https://yoroi.company/research/the-ave_maria-malware/
- https://insights.infoblox.com/threat-intelligence-reports/threat-intelligence–11
- https://blogs.infoblox.com/cyber-threat-intelligence/avemaria-rat-malspam-campaign/









