Author: Renée Burton, Christopher Kim and Laura da Rocha
Summary
On 25 January, 2023, the Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), and Multi-State Information Sharing and Analysis Center (MS-ISAC) released a joint Cybersecurity Advisory (CSA) regarding a phishing campaign that involves the malicious use of legitimate remote monitoring and management (RMM) software.1 This report highlights a tactic used to manipulate users, but was published nearly seven months after the campaign occurred. Since that time, multiple campaigns by the same actor were conducted but not included in the CSA. The advisory assessed that this activity was widespread, financially motivated, and related to malicious lookalike or typosquatting activity reported by security vendor Silent Push in October 2022.2
We performed retrospective analysis on the indicators published by CISA, Silent Push, and our own intelligence, to understand the breadth of the activity and impact to our customers. We found that this activity has been present since at least Spring 2021 and although it is widespread, it has had little impact on our customer base. Our intelligence was largely distinct from that published elsewhere; approximately 85% of the indicators published in OSINT reporting were never seen in our networks. The lack of overlap of different intelligence sources is a well-known phenomena.3 Our research and analytics produced 113 unique indicators related to this activity. We have made them available via our Threat Intelligence Data Exchange (TIDE) and our open GitHub repository. Finally, this brief also provides mitigation strategies and a description of solutions available to Infoblox BloxOne Threat Defense (B1TD) Advanced customers.
Infoblox identified many of the domains used in the subsequent campaigns as suspicious last year and included them in our Suspicious response policy zone (RPZ) feed to provide early protection to our customers. While the recently published, detailed analysis provided by public and private sector reporting is critical to understanding the threat landscape, such analysis is retrospective in nature and the release of indicators often comes long after the attack occurred. Consumers and corporations are best protected by a proactive, low regret model where threats are blocked before they are validated. As the security community matures its understanding of a particular threat, more detail can be provided to users, creating intelligence-in-depth. This strategy is particularly effective as part of a DNS-based security solution.
Background
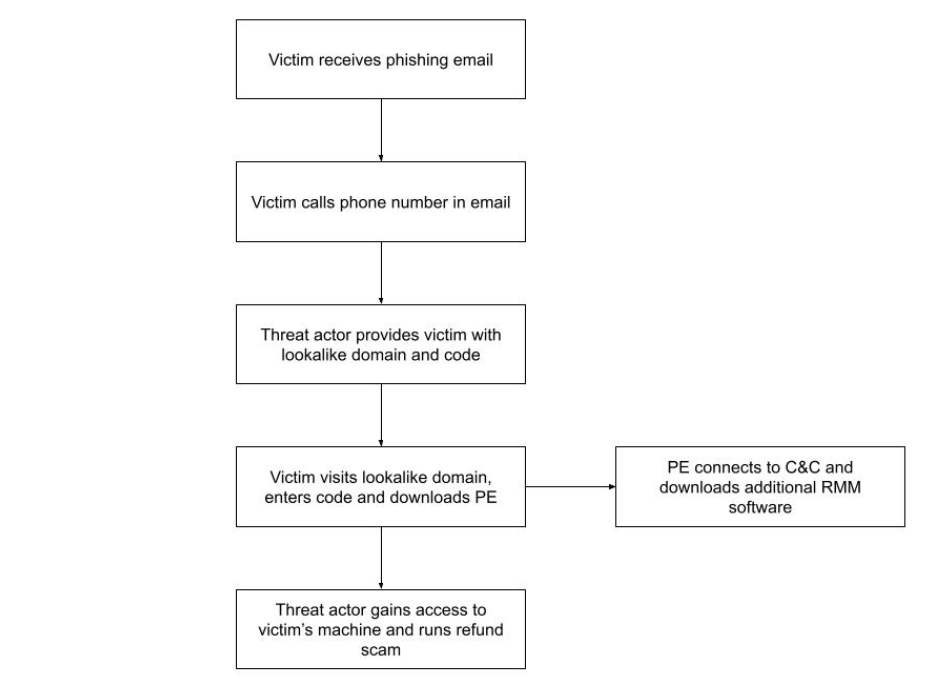
According to the CSA, in October 2022, CISA used trusted third-party reporting to conduct retrospective analysis of EINSTEIN — a Federal Civilian Executive Branch (FCEB)-wide intrusion detection system (IDS) operated and monitored by CISA—and identified suspected malicious activity on two FCEB networks. The CSA reported that a phishing email was sent to an employee’s government email address, prompting them to place a phone call to the actor, after which they were asked to visit a malicious website. From this first-stage domain, the victim downloaded malicious software, which then connected to a second-stage domain.
After compromising and gaining access to the victim’s machine with RMM software, the actor attempts to steal funds from the victim using a refund scam tactic. Although these campaigns appear to be financially motivated and target individuals, the authors of CSA assess that these kinds of activities can be more destructive than simple financial fraud. The actor could potentially sell victim account information to other cyber criminals or advanced persistent threat (APT) actors.
Additionally, malicious cyber actors, including cybercriminals and nation-state sponsored APTs, are known to use legitimate RMM software as a backdoor for persistence and/or command and control (C&C). In the campaign CISA described, the actor did not install the RMM software, but ran it as self-contained, portable-executables that connected to the actor’s RMM server. Since portable executables do not require administrator privileges, they can bypass the victim organization’s risk management controls and launch unapproved software.
Retrospective analysis and customer impact
Review of our historical data indicates that while the actor has been active for nearly two years and regularly conducts campaigns, the impact on our customer base is low. Our analysis found that:
- These campaigns were active since at least Spring 2021, over a year before the incidents CISA and Silent Push described.4 The domain xpchelp[.]us was observed in a campaign in March 2021.
- The domains are lookalikes to well-known services, meaning they are visually similar to the original domain, which when combined with other aspects of the activity, may raise the victim’s trust that the site is legitimate. For those victims who receive the domain over the telephone, the likelihood to accept any variation is higher due to the additional social engineering of the call.
- The majority of the domains were aged, meaning that they were not utilized for malicious activity for some period after registration. For example, win01[.]xyz was registered in December 2021, but we did not observe active use of this domain until June 2022. In most cases, we identified the domain as suspicious at least three weeks prior to observing them in a campaign.
- There is some domain re-use. The domain amzsupport[.]live was part of an active campaign in April 2020.5 The domain was used again in October 2021.6 Then the domain registration lapsed,but was re-registered in January 2023 for the same behavior.
- Many of the domains are variants of one another. For example, there are several variants of win01[.]xyz registered under different TLDs, at different times, with slight name variations, including win03[.]life, and win03xb[.]cf.
- The domains exist within TLDs that have a moderately high to high risk score due to abuse, according to our reputation algorithm. They include: .live, .life, .info, .xyz, .buzz, .ga, .top, .us, and .cc.7
- The actor abuses nameservers such as dnsowl[.]com and cloudflare[.]com, which are controlled by commercial providers. Our reputation algorithm recognizes this behavior and therefore gave the nameservers used by this actor a higher than average risk score.
- The domains were registered through registrars with a higher than average abuse score according to our registrar reputation score, including Name Silo and Name Cheap.
We compared the CISA-reported domains and our own Suspicious feed domains with the queries we have observed at our DNS resolvers. This gives us an aggregate view of our cloud customers and the potential impact on their networks. We found the number of queries related to this malicious activity to be low with only a handful of queries over time across all domains. The vast majority of domains we have associated with this malicious activity have never been observed in our networks. This may be due, in part, to the tactic requiring victims to make phone contact in order to receive the malicious domain. Still, as noted by CISA, the potential damage of actor-controlled remote access tools is extensive.
Following the availability of our Suspicious feed in November 2022, the majority of the related domains were identified before, or shortly after, they were first observed in our customer networks. Table 1 shows CISA-reported domains, as well as domains we previously detected, and highlights those that were seen at our resolvers. Domains marked in bold font were observed in queries at our DNS resolvers; domains with an asterisk are those Infoblox identified prior to publication of the CSA. Recently discovered domains are in the Appendix and in our GitHub repository.
| Domains reported by CISA | Domains not in CISA or Silent Push Reporting |
| 247secure[.]us *
deskcareme[.]live gscare[.]live hservice[.]live myhelpcare[.]cc myhelpcare[.]online nhelpcare[.]cc nhelpcare[.]info win01[.]xyz win03[.]xyz |
247secure[.]info *
amzsupport[.]live * custom01[.]top * custom03[.]top * fsupportcare[.]com mycare247[.]cc mycare247[.]live * myhelpcare[.]me psupport[.]cc win01[.]top * win03[.]life * windesk[.]info windesk[.]top |
| Table 1. A comparison of domains reported in OSINT and Infoblox Suspicious domains. Domains shown in bold font were observed at Infoblox B1TD cloud resolvers.
* Domains with an asterisk were identified by Infoblox prior to CSA publication. |
|
In the aggregate list of lookalike domains published in OSINT we are able to attribute to this activity, the vast majority (85%) were never seen in our customer networks. This is likely due to a combination of vigilance on the part of our customers, anti-phishing technologies in place within their networks, and natural variation that occurs between networks. The DNS traffic between any two given networks has little overlap as a percentage of domains. At the same time, the sheer volume and variety of newly observed domains make automatic detection of threats very challenging for the security industry. Infoblox has observed a steady rise in the use of lookalike domains at multiple places within the attack chain; for threat actors, they are a cheap commodity that increase victims’ trust.
Attack chain
The actor targets victims and distributes helpdesk-themed phishing emails that either contain a link to a first-stage lookalike domain or a prompt to call the actor’s phone number. Victims who make the call are verbally instructed to visit the first-stage lookalike domain. When they do so, the website drops RMM software in the form of a portable executable. This program then connects to a second-stage lookalike domain, from which it downloads additional RMM software. The RMM software that CISA detected in the campaigns they discovered were AnyDesk and ScreenConnect.
The actor then uses the RMM software to access the victim’s machine and begin conducting a refund scam. First, they entice the victim to log into their bank account from the compromised system or host. Next, they manipulate the bank account summary and show that a large refund had been deposited into the victim’s account. Finally, the actor instructs the victim that the refund amount was incorrect (too large), and so the victim must return the difference back to the scam operator.
Vulnerabilities and mitigation
Lookalike domains are frequently used in social engineering and phishing attacks. They are used to distribute a broad spectrum of malware, such as phishing, ransomware, and banking trojans. These RMM phishing campaigns used a variety of tactics and techniques, including local accounts, user execution, and remote access software.8,9,10 To mitigate these, as well as other attacks that leverage lookalike domains:
- Use defense-in-depth security solutions that will preemptively block potential threats.
- Expand user training to include awareness of lookalike domains and social engineering techniques that require human interaction from the victim.
- Block and quarantine executable files that are not signed by a trusted organization.
- Check instances of RMM software only being loaded in memory.
- Restrict use of RMM solutions in the organization’s network only and over-approved remote access solutions, such as virtual private networks (VPNs) or virtual desktop interfaces (VDIs).
- Monitor network for signs of activity related to unauthorized RMM software.
- Block both inbound and outbound connections on common RMM ports and protocols at the network perimeter.
Infoblox Solutions
Infoblox B1TD Advanced customers have access to DNS RPZs that protect against suspicious activity. This data is also available through the Threat Intelligence Data Exchange (TIDE) and our Dossier research portal. The Suspicious data is a combination of multiple automated analytics and indicators found by individual Infoblox researchers. Our analytics leverage our openly published reputation scoring system and consider the TLD, nameserver, and registrar reputation, among other domain characteristics. Infoblox evaluates domains from a wide variety of sources, allowing for the early detection of potential threats, and re-evaluates every domain that is newly observed within our customer network. This approach allows us to renew our suspicion of a domain so that it is present in the RPZ during active use by a threat actor. As of late January 2022, there are nearly 3 million active Suspicious domains in our collection.
Furthermore, Infoblox has analytics to identify lookalike domains, both based on common targets, such as Amazon and Microsoft, as well as customer-specified targets. We identify textually similar domains, including those associated with typosquatting. The results of these algorithms are available in both policy and threat protection feeds. As of late January 2022, there are nearly 300k active lookalike domains in TIDE.
Appendix
The table below provides a sample list of the IOCs relevant to our recent findings. The complete list, in addition to the indicators from CISA and Silent Push can be found in our GitHub repository, with credit to the applicable source.11
| Sample of Indicators of Compromise |
| 247care[.]cc
247helpcare[.]live 247helppc[.]us 247secure[.]info 247us[.]support ahelps[.]cc ahelps[.]live amzsupport[.]live ask4support[.]live bhelp[.]online bhelps[.]cc bhelps[.]live cancell[.]info cancell[.]live cancell[.]online carehelp[.]cc carehelp[.]live carehelp[.]online careme247[.]us careme[.]cc cscare[.]cc custom01[.]top custom03[.]top deskhelp[.]care dhelp[.]cc dhelp[.]live dhelps[.]cc fback[.]xyz ghelps[.]cc gscare[.]cc gscare[.]online helpcare247[.]us helpcare[.]cc hide03[.]xyz hsupport[.]cc ihelps[.]cc itcare247[.]cc itcare[.]info jcare[.]info jhelp[.]info khelp[.]cc liveform[.]us mcare[.]cc mcare[.]help melogin101[.]fun melogin[.]xyz mhelp[.]info mhelp[.]live mhelps[.]info mycare247[.]live myhelpcare[.]me nhelpcare[.]live nhelpcare[.]online nntv[.]xyz ntcare247[.]live ntcare[.]online pahelp[.]net payhelp[.]cc pcare[.]cc pcservice[.]cc phelp[.]cc phelp[.]online qcare[.]cc qhelp[.]online qhelps[.]cc rcare[.]cc rhelp[.]cc rhelp[.]online rhelpcare[.]us rhelps[.]us rsdrs[.]top rsfed[.]xyz securesupport[.]us shelp[.]cc shelp[.]info shelp[.]live shelps[.]info shelps[.]us support01[.]cc support01[.]us techcare[.]life thelp[.]cc thelp[.]info thelp[.]live uhelp[.]info uhelp[.]live vhelp[.]cc vhelp[.]info vhelp[.]live vhelps[.]cc vhelps[.]info wcare[.]cc wcare[.]live whelp[.]info win01[.]top win03[.]life winbackup01[.]xyz winbackup03[.]xyz windesk[.]top yhelp[.]cc yhelp[.]info yhelp[.]live yhelp[.]online yhelp[.]us zcare[.]cc zhelp[.]cc zhelp[.]info zhelp[.]live zhelp[.]online fsupportcare[.]com mycare247[.]cc psupport[.]cc windesk[.]info |
| Table 2. Lookalike domains that drop malicious RMM software that were not reported by CISA or Silent Push. |
Endnotes
- https://www.cisa.gov/uscert/ncas/alerts/aa23-025a
- https://www.silentpush.com/blog/silent-push-uncovers-a-large-phishing-operation-featuring-amazon-geek-squad-mcafee-microsoft-norton-and-paypal-domains
- https://www.usenix.org/conference/usenixsecurity19/presentation/li
- https://urlscan.io/result/c009f36d-c2aa-4246-8feb-1a6a62e350a3/
- https://urlscan.io/result/59e7be57-926e-4cc0-8725-cf62f656aa6c/
- https://urlscan.io/result/46077f5d-3dda-4ab5-b81d-dbe1f3f5369e/
- https://insights.infoblox.com/resources-whitepapers/infoblox-whitepaper-reliable-reputation,
https://blogs.infoblox.com/cyber-threat-intelligence/q3-2022-cyber-threat-intelligence-report/ - https://attack.mitre.org/techniques/T1078/003/
- https://attack.mitre.org/techniques/T1204/
- https://attack.mitre.org/techniques/T1219/
- https://github.com/infobloxopen/threat-intelligence/tree/main/