Author: Christopher Kim
TLP: WHITE
Overview
During the week of 22 February, security researchers discovered email campaigns distributing a malware loader for Cobalt Strike,1,2,3 a legitimate penetration testing tool abused by threat actors for its post-exploitation capabilities. These campaigns, which some researchers have nicknamed “BazarStrike,” deliver the loaders using similar tactics, techniques, and procedures (TTPs) to that of BazarLoader campaigns.4
Customer Impact
Cobalt Strike is a commercial penetration testing solution that attackers use to deploy a program named “Beacon” on the victim’s machine. Threat actors can use Beacon to perform advanced post-exploitation functions such as:
- Command execution,
- Key logging,
- File transfer,
- Socks proxying,
- Privilege escalation,
- Mimikatz,5
- Port scanning, and
- Lateral movement.
In late 2020, Cobalt Strike was involved in several major cyberattacks, including the supply chain attack on SolarWinds’ Orion platform6 and ransomware attacks on the healthcare sector.7
Campaign Analysis
These campaigns used malware delivery methods typically seen in BazarLoader campaigns.8
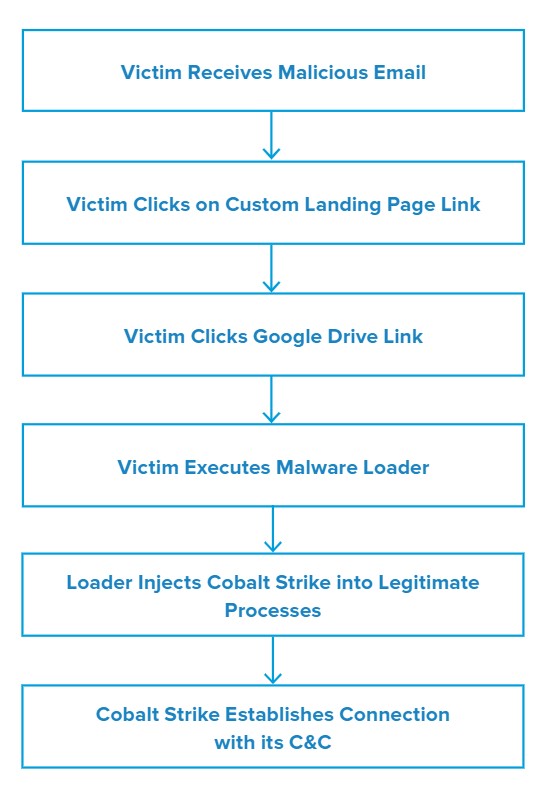
Email messages followed a customer complaint theme either in the form of a letter, report or request. Subject lines included Re: complaint on <lastname> and <Victim company> complaint. The email bodies contained a link that led the victim to a customized landing web page hosted on an online platform for email marketing and creating landing pages.
The threat actor(s) constructed the link name using a static prefix such as complaint-letter, as well as the email’s date. The landing page contained another link to a Google Drive that hosted the loader payload.
Although the delivery methods are similar, the binary of the loaders used in these campaigns is technically different from BazarLoader. Unlike BazarLoader, these loaders did not use .bazar top-level domains to calculate IPv4 command and control (C&C) addresses that returned the next payload instructions.
Attack Chain
The threat actors digitally signed the malware loaders with one of two spoofed organizations, OOO SMART or Orca System. All digital certificates used in the campaigns were issued by Certum Extended Validation Code Signing CA SHA2. Threat actors will often use valid certificates to sign malicious software so it can blend in with other legitimate applications.
When victims downloaded and executed the malware loader, it used process injection9 to run Cobalt Strike across several common processes, including dllhost.exe, svchost.exe, explorer.exe, wmiprvse.exe, and csrss.exe.
Cobalt Strike then established a channel session with its C&C over port 443. The domains used for the C&C communication were recently created in February and wholly registered by the actor for malicious purposes.
Vulnerabilities & Mitigation
Infoblox recommends the following to reduce the risk of this type of infection:
- Threat actors often inject Cobalt Strike into legitimate processes such as svchost.exe. To detect process injection, look for unusual parent and child process pairs. For example, it is unusual to see a svchost.exe process not spawned from services.exe.
- Implement strong antivirus solutions that are capable of detecting evasion techniques, such as process injection and process hollowing.
- Be cautious of emails that include unfamiliar links within its messages or iterates through several external web pages to deliver documents.
- Network traffic patterns from machines installed with Cobalt Strike are uniformly distributed.10 Examine the network traffic to distinguish human and machine generated traffic packets.
- The campaigns in this report used fraudulent domains wholly created for malicious purposes.
Endnotes
- https://twitter.com/James_inthe_box/status/1364587761529978880
- https://twitter.com/ffforward/status/1364893143536181249
- https://twitter.com/GossiTheDog/status/1364573917877264386
- https://twitter.com/hashtag/BazarStrike?src=hashtag_click
- https://github.com/gentilkiwi/mimikatz/wiki
- https://blogs.infoblox.com/cyber-threat-intelligence/teardrop-malware/
- https://blogs.infoblox.com/cyber-threat-intelligence/ransomware-attacks-target-healthcare-sector/
- https://resources.infosecinstitute.com/topic/bazarbackdoor-malware-what-it-is-how-it-works-and-how-to-prevent-it-malware-spotlight/
- https://attack.mitre.org/techniques/T1055/
- https://talos-intelligence-site.s3.amazonaws.com/production/document_files/files/000/095/031/original/Talos_Cobalt_Strike.pdf








