Authors: Stelios Chatzistogias, Laura da Rocha, Darby Wise
This blog contains an excerpt of our new paper that unveils a previously unpublished technique used by actors to scale their operations and avoid detections. This technique uses DNS CNAME records to create a traffic distribution system (TDS). We describe the technique in detail and how it is being used by an actor to create investment scams. Read the full research paper here.
Executive Summary
DNS threat actors never cease to surprise us. Every day, we learn about creative, new campaigns they have devised to exploit victims. Investment scams are one of these. The US Federal Trade Commission reported that more money was lost to investment scams in the US during 2023 than any other type of scam, totaling over USD $4.6 billion dollars stolen from victims.1 Savvy Seahorse is a DNS threat actor who convinces victims to create accounts on fake investment platforms, make deposits to a personal account, and then transfers those deposits to a bank in Russia. This actor uses Facebook ads to lure users into their websites and ultimately enroll in fake investment platforms. The campaign themes often involve spoofing well-known companies like Tesla, Facebook/Meta, and Imperial Oil, among others.
Savvy Seahorse’s campaigns are sophisticated. They involve advanced techniques such as incorporating fake ChatGPT and WhatsApp bots that provide automated responses to users, urging them to enter personal information in exchange for alleged high-return investment opportunities. These campaigns are known to target Russian, Polish, Italian, German, Czech, Turkish, French, Spanish, and English speakers, while specifically protecting potential victims in Ukraine and a handful of other countries.
Savvy Seahorse abuses the Domain Name System (DNS) in an obscure way: they leverage DNS canonical name (CNAME) records to create a traffic distribution system (TDS) for sophisticated financial scam campaigns. As a result, Savvy Seahorse can control who has access to content and can dynamically update the IP addresses of malicious campaigns. This technique of using CNAMEs has enabled the threat actor to evade detection by the security industry; to our knowledge, this is the first report to focus on the use of CNAMEs as a TDS engineered for malicious purposes.
In this paper, we introduce the concept of a CNAME TDS and discuss how Savvy Seahorse uses CNAME records to conduct large-scale scam campaigns that have “swum” under the radar of the security industry, until now. The major findings are:
- Savvy Seahorse delivers campaigns through Facebook advertisements.
- They have been operating since at least August 2021.
- They use dedicated hosting and change IP addresses regularly.
- Individual campaigns are short-lived (each subdomain is advertised for 5 to 10 days).
- They appear to use a phased deployment system in which the CNAME record for a campaign domain will change based on whether it is currently active or not.
- They utilize wildcard DNS entries, which allows them to create a large number of independent campaigns quickly but can add confusion to passive DNS (pDNS) analysis.
- Personal data of the victim is sent to a secondary HTTP-based TDS server to validate the information and apply geofencing to exclude Ukraine and a handful of other countries.
- The second HTTP-based TDS also tracks user IP and email addresses over time.
Savvy Seahorse has been operating since August 2021. Although participating domains are sometimes flagged by security tools, the greater infrastructure and actor behind them have gone undetected by the security industry. We have observed approximately 4.2k base domains with a CNAME record listing a subdomain of b36cname[.]site. To host campaigns, Savvy Seahorse creates several subdomains for each SLD using a domain generation algorithm (DGA), where the hostname is pseudo-random and in most cases, three characters long.
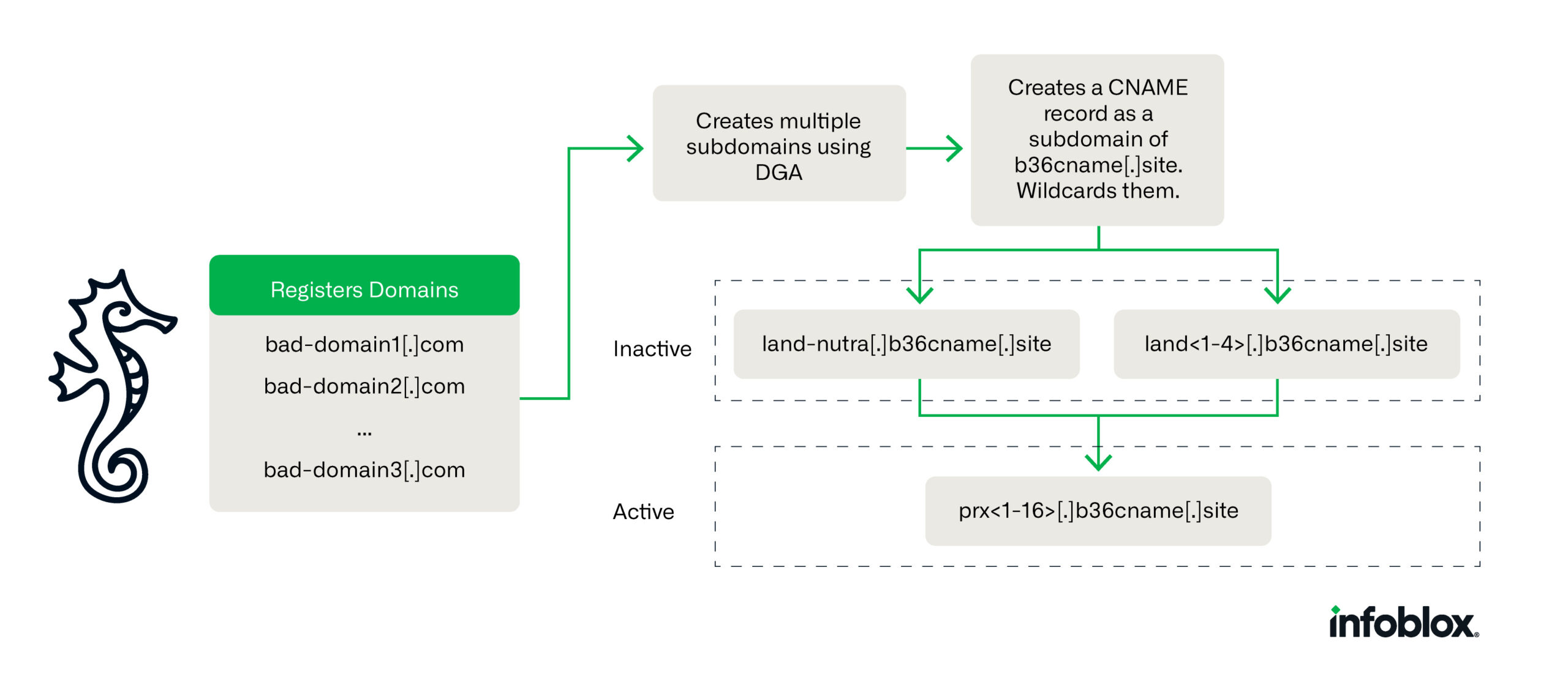
Figure 1: An overview of Savvy Seahorse’s operations
Savvy Seahorse uses registration forms embedded in each web page to gather the victim’s first and last name, email address, and phone number. Two examples of this registration form, one in Polish and the other in English, appear in Figure 2.
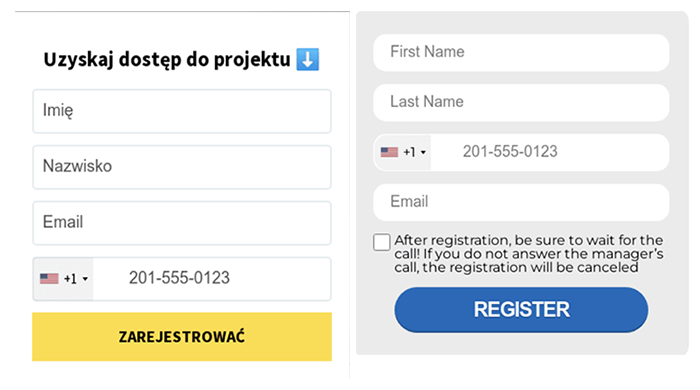
Figure 2: Registration forms used in Savvy Seahorse’s campaigns
After validating the user information, they will be redirected to the platform. The actor keeps track of users, preventing revisits from crawlers and security vendors. The video below provides a walkthrough of the fake trading platform.
At Infoblox, we remain focused on finding new ways that threat actors are abusing DNS to conceal their criminal operations. Savvy Seahorse’s technique of using DNS CNAMEs as a TDS to manage their malicious operations demonstrates how DNS is the most effective way of tracking and disrupting the activities of cybercriminals. Our analysis into CNAME patterns was ultimately what enabled us to discover this actor and the unique tactics, techniques, and procedures (TTPs) it employs to operate its large network of scam campaigns.
Indicators of Activity
Below is a sample of indicators used in Savvy Seahorse’s campaigns. Indicators are also available in our GitHub repository here.
| Indicator | Type of Indicator |
|---|---|
| getyourapi[.]site | Savvy Seahorse secondary TDS domain |
| land-nutra[.]b36cname[.]site | Subdomain used as CNAME record for parked domains |
| land<1-4>[.]b36cname[.]site | Subdomains used as CNAME records for inactive campaigns |
| prx<1-16>[.]b36cname[.]site | Subdomains used as CNAME records for active campaigns |
| new[.]xsdelx[.]top
bwn[.]objectop[.]xyz sej[.]progmedisd[.]site adin[.]czproftes[.]xyz visa[.]lukzev[.]xyz sun[.]autotrdes[.]top hmz[.]coivalop[.]xyz news[.]beneffit[.]top goiin[.]baltez-offic[.]xyz |
Subdomains for active Savvy Seahorse campaigns |
| ultra-vest[.]one
kingsman-adv[.]org abyss-world-asset[.]net |
Fake trading websites the user is redirected to in some campaigns |
| sci[.]pointpayment[.]net
makeyourpay[.]com qiwi[.]bppsa[.]com ymoney[.]bppsa[.]com processing[.]betatransfer[.]io crypto-payer[.]co |
Payment processing domains to collect victim’s financial information |
| ap-gateway[.]mastercard[.]com | Legitimate domain for Mastercard used collect victim’s financial information |
| checkout[.]flutterwave[.]com | Legitimate domain for Flutterwave, a Nigerian payment service used to collect victim’s financial information |
| auproject[.]xyz
badanie-pl[.]site blog-vcnews[.]site capital-inwest[.]site dasms[.]xyz duums[.]xyz esbopehan[.]xyz futtes[.]site gernik[.]site groovetonprogramz[.]xyz lintant[.]top mipinves[.]site mixx-today[.]site newprogrms[.]xyz oksitepl[.]site onlinedietslimm[.]xyz prostprogr[.]xyz rslimess[.]xyz satin1[.]xyz sunproflts[.]site |
Savvy Seahorse base domains |
Footnotes
- https://www.ftc.gov/business-guidance/blog/2024/02/facts-about-fraud-ftc-what-it-means-your-business









