The way we live and work today has significantly changed over the last two years. Gartner forecasts that 31% of all workers and 47% of all knowledge workers worldwide will continue to be remote in 2022. This hybrid workplace model puts huge digital demands on enterprise networks including things like ensuring remote connectivity, increased scalability and modernizing the underlying infrastructure. In addition to enabling remote work, enterprises are undergoing other network transformations like accelerated adoption of multi-cloud environments, SaaS and SD-WAN enabled branches. This greatly increases the attack surface causing security headaches, limits visibility of network connected assets and limits the control that IT teams have across on-premises, cloud, branch and home environments.
Challenges with security silos
One of the ways that organizations secure their networks is through a defense in depth strategy, implementing NGFWs, web gateways, email security, and endpoint security tools. The unintended consequence of defense in depth is the proliferation of disparate security tools that lack interoperability among themselves and with frequently used network tools. There is a lack of data sharing, different interfaces, and duplicate alerts that overburdens already strained security operations teams. This problem is more pronounced for larger enterprises that may be distributed and undergoing transformations such as WFA, multi-cloud adoption, SAAS and SD-WAN.
It’s no wonder that the average time to identify a breach is still more than 200 days, according to a Ponemon study, and 53% of security operations teams take more than 8 hours to investigate a threat, according to a recent Forrester survey.
Breaking down silos starts with integrations
While there may not be much that can be done about siloed reporting structures of security and networking teams (although there are indications that this is changing), integrating security tools and networking tools provide a pathway to sharing data that can be critical to speeding up investigations and response times.
SIEM and SOAR – Networking services like DNS, DHCP and IPAM (DDI) hold a goldmine of contextual information around network assets and tapping into that data by integrating SIEM/SOAR tools with your DDI platform helps SOC teams gain unprecedented visibility. This includes information such as where the asset is located in the network, what type of OS it is running, who it is assigned to and an audit trail of all destinations accessed by the device. This information can be used for efficient event correlation and for making threat intelligence actionable.
Triggering a scan – DNS security provides a first line of defense against a lot of known bad threats including ransomware, phishing, exploits and other malware, blocking DNS resolution to destinations that may be hosting malware. In addition, the solution can integrate with a vulnerability scanning solution to trigger a scan in real time when a device makes a C&C communication so that it can be cleaned up. This minimizes dwell time for threats since we are not waiting for the next scan window to detect the compromised asset.
Raising an IT ticket – Similar to triggering a scan, when the DNS security solution detects bad DNS requests, it can automatically raise an IT ticket by integrating with the ITSM solution so that the IT admin is made aware of the threat in real time. This again minimizes dwell time.
Cyber Security Ecosystem
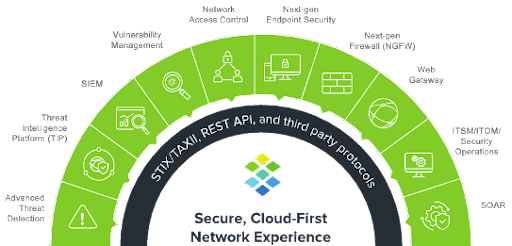
BloxOne Threat Defense provides a highly interconnected set of integrations that enable security teams to eliminate silos, optimize their security orchestration automation and response (SOAR) solution and improve the ROI of their entire cybersecurity ecosystem. It reduces the time and cost of threat response through enhanced automation and real-time, two-way data sharing across the ecosystem enabled by extensive APIs. For more information on all the integrations available with the solution, please visit the Cybersecurity Ecosystem page.








