Over the years, organizations started putting together a security stack as part of their defense-in-depth strategy. Each tool was built to address a specific threat vector. However, these tools did not talk to each other or readily share data, forcing security operations teams to manually gather information needed to correlate events.
Microsoft has announced a dozen new connectors that automatically collect data from several leading security solutions, including Infoblox, into Azure Sentinel. These connectors help security teams to gather and analyze data from various sources much faster, lowering time to remediation.
Visibility is Key for Security Operations
The first place to start addressing operational challenges is with visibility. You need a platform that provides ubiquitous visibility of everything that’s on the network – physical, virtual, cloud, branch, and IoT resources. In order to help understand the severity of network and security events, leveraging network context is key. Network context includes things like criticality of the compromised asset, location of the asset, audit trail, and history of destinations accessed.
Your DDI (DNS, DHCP, and IPAM) platform knows, at any given point in time, what devices are on your network. This is because any time a device joins a network, the first thing it will do is to request an IP address from the DHCP server. The DHCP server is also able to identify the characteristics of the device (type of device, OS, version) based on the initial DHCP request. This information is collected and put into a database (IPAM). Additional discovery data can also be gathered to further augment the information of the device (e.g. username, switch port, access point, physical location). All of this information becomes really important if you have to conduct an investigation based on an IP address.
Value of DNS, DHCP to a SIEM for Threat Correlation and Hunting
DHCP/DNS data is a gold mine that can be leveraged in a SIEM, like Azure Sentinel, to help accelerate threat correlation and hunting.
Event Correlation – Without DHCP data, it’s hard to correlate disparate events related to the same device under investigation, especially in dynamic environments. DHCP servers are responsible for allocating IP addresses that are used to identify the specific devices involved in security events. A DHCP assignment signals the insertion of a device onto the network and hence is an audit trail of devices on the network.
Scope of breach – DNS query data provides a “client-centric” record of activity. This includes internal activity inside the security perimeter, BYOD, and IoT devices and provides an excellent basis to profile device and user activity. Without DNS and DHCP, operations teams may have limited visibility into what resources a client has been accessing. DNS provides a universal audit trail of services and resources it has recently accessed.
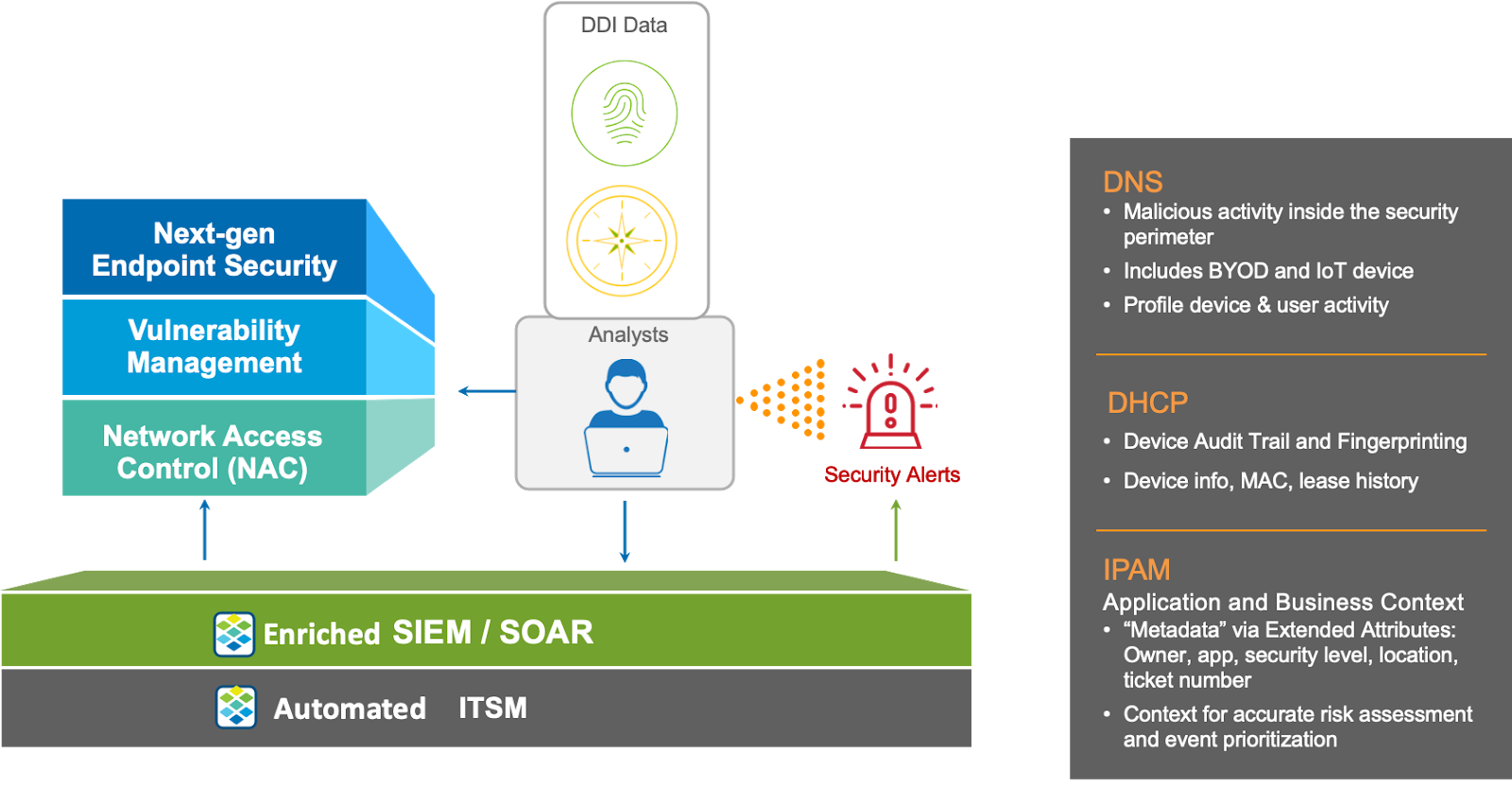
Using the Infoblox connector, Azure Sentinel users can get quick and easy access to this gold mine of data, analyze and correlate the information, and respond to events more efficiently.
Learn how to implement the Infoblox connector for Azure Sentinel here.
Read more about Infoblox solutions here.








