You cannot secure what you cannot see!
If you think organizations automatically know when new devices join the network and if they are compliant, think again. Devices, data and people are seeing an explosive growth in organizations. To add to this, an organization’s IT network is becoming heterogeneous; spreading to multiple remote locations, satellite offices and hybrid clouds all over the globe. This explosion in devices, data and people over multiple locations, some of which are not fully managed by IT, pose a tremendous challenge in maintaining visibility and security for the network. IT managers have to know what devices are connected on their network, detect devices that pose a security threat and are rogue or infected, spend hours on investigating the context behind these devices and finally determine how to block these devices.
Let us go through these challenges in more detail.
The first challenge is in gathering inventory of the devices connected to the network. There may be unauthorized/rogue devices on the internal network with access to sensitive corporate data and resources. In the case of one particular retail company, there were 6000 IP addresses on the network when there should only have been 4000! If even a few of the remaining 2000 IP addresses belonged to malicious devices, the company pays a heavy price for not detecting their presence.
The second challenge is in identifying devices that might be infected with malware or may be part of botnets and might be either consuming resources or worse ex-filtrating sensitive data. Detecting the presence of malicious activity can be a challenge and there are a number of agent-based and agentless solutions to tackle this problem.
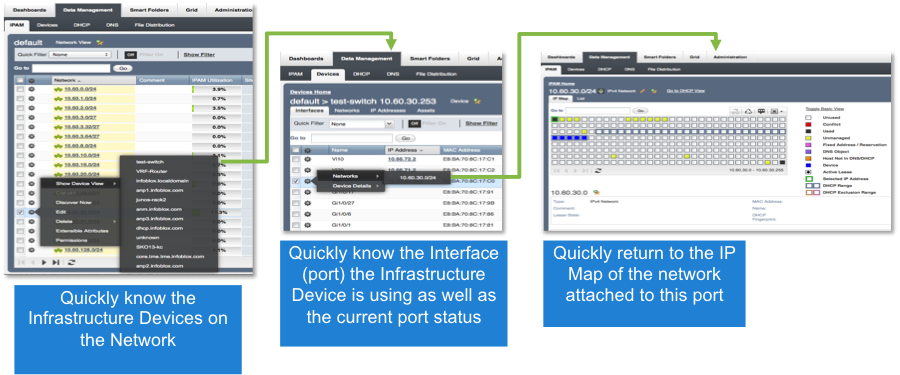
The third challenge is to understand how the rogue device or an infected device is connected to the wired or wireless network for remediation actions like severing its network connectivity. This involves locating the network, VLAN and eventually the specific switchport that the device is connected to. The security team typically initiates this process with trouble tickets or emails sent to the network infrastructure or security operations team. Typically, it takes several minutes to hours to go through spreadsheets to determine where a device is located and the network, VLAN, VRF or wireless access point it is connected to. If the device is a VM, it will be necessary to discover the server, virtual switch and cloud management platform that it is part of.
Finally, security teams might want more network context to perform thorough security forensics, address vulnerabilities, understand compliance violations and improve security best practices. Information such as the device’s MAC address, the time when it appeared on the network, its DHCP lease history, DNS hostname, different locations it has been at, its firmware and software versions etc. are critical for such investigations. It can be time/resource intensive and sometimes even impossible to access all this information by scraping data from several sources.
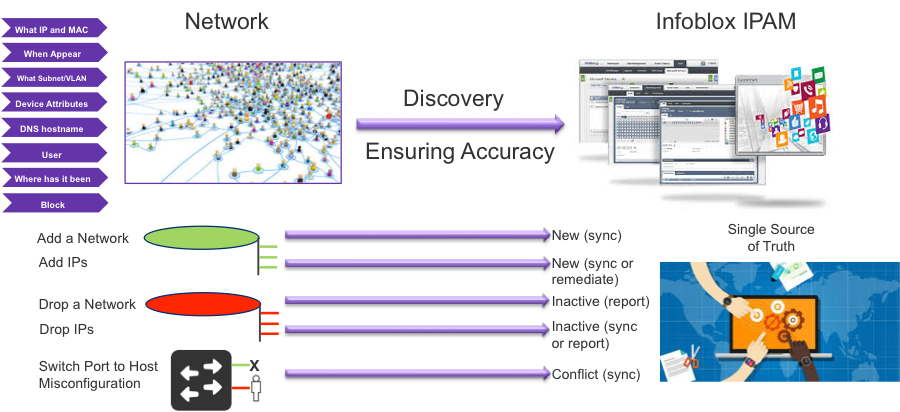
Infoblox solves this problem using actionable network intelligence and with a comprehensive network discovery solution. The discovery process finds all IP devices on the organization’s wired and wireless network along with their associated context such as location, connected switchport or wireless access points. These devices can be printers, PCs, phones, video cameras etc., on the enterprise campus network or virtual machines, servers, switches and routers in the data centers or virtual instances on the public cloud like AWS. Detailed information about devices can be pulled in with DHCP fingerprinting. All this device data is visible on a single console. The devices can be tagged with extensible attributes or metadata to easily classify, sort and search these devices according to their attributes. For example, you can pull a report of all the iphones that are running version IOS version 8.0.
All the discovered devices/IP addresses in the system are reconciled with the IP address database to flag unmanaged devices or rogue devices in the system. When malware or botnets are discovered by Infoblox security solutions such as DNS Firewall and Threat Insight, the sophisticated Infoblox IPAM can automatically zero in on the source/location of the IP address and its device context for security forensics and share this contextual information with existing security systems for faster remediation. This saves precious downtime and greatly improves the efficiency of the remediation process.
You cannot secure what you cannot see! When it comes to complex networks with large numbers of devices that is definitely true. Luckily, you can use intelligent IPAM to discover, analyze and secure your network.