Update May 17, 2021
The story behind and around the Colonial Pipeline breach continues to evolve. Over the last 3 days we have learned that:
- Colonial Pipeline actually paid $5 million in ransom,
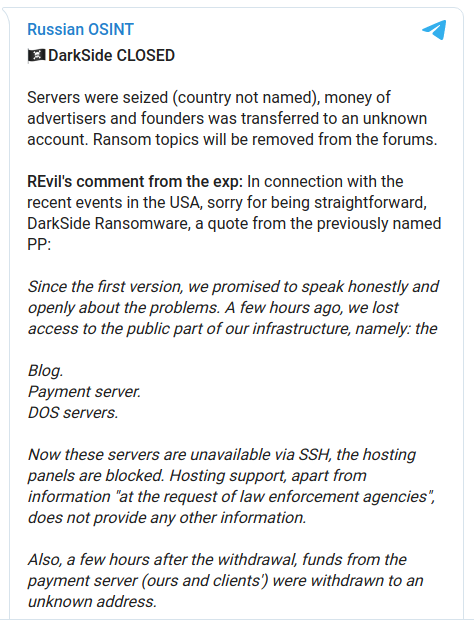
- DarkSide claims they are shutting down because they lost their infrastructure and wallets (a screen shot of their announcement is below),
- A popular cryptocurrency mixing service used by DarkSide and other cybercriminal groups, BitMix, also appears to be down, and
- Other criminal RaaS providers have announced new rules for their customers to avoid a similar situation.
But there is still a great deal to learn from this incident to help us better understand how to address the ransomware industry, reduce the risk of becoming the next victim, and minimize the impact of a ransomware event when it does happen.
One thing that has not come up in the Colonial Pipeline discussion so far is cyber insurance, which may have served a critical role. Cyber Insurance policies typically offer coverage for repairing the damage caused by a cyber incident, but also offer “Cyber Extortion” options to address a ransom as well any ransom related expenses. In such cases, it would not be uncommon to use a consultant to help with negotiations and other aspects of paying the ransom.
If Colonial Pipeline carried cyber extortion coverage, with a pipeline carrying roughly 3 million barrels of fuel each day, a $5 million ransom may have been much less than the size of any cyber insurance payout, making it a viable option for everyone involved.
So the final question investors will want answered is regarding premium costs. In addition to the size of the policy and the risk of the covered threats, the ability of the insured to defend against those threats is a significant contributing factor. While the rest of us may judge the defense capabilities and response activities at Colonial Pipeline at a distance, any cyber insurance provider would base their premium decision on a closer inspection of their entire security profile. The presence of a single security tool could have a significant impact on premiums. For example, one Infoblox customer noted that they saved $1.3M in cyber insurance fees over a 3 year period after deploying DNS security.
So the gas might be flowing again, but groups operating in both legal and illegal arenas continue to struggle to understand and digest all that is going on – and keeping an eye out for what might be next.
Original post May 14, 2021
Headlines around the globe are proclaiming the Colonial Pipeline breach a “wake up” call for cybersecurity. And, with the help of a few less-principled security vendors, there are plenty of “possible”, “potential”, or otherwise “Hollywood-worthy” scary scenarios being spun about “what could have happened”.
But an attack on US infrastructure did not really surprise anyone in the security industry.  If this was a wake-up call for your security team, then they have truly been sleeping. Many papers and conference talks have been dedicated to infrastructure risks and security for two decades. And we have plenty of real-world examples from the last 10-years alone, including:
If this was a wake-up call for your security team, then they have truly been sleeping. Many papers and conference talks have been dedicated to infrastructure risks and security for two decades. And we have plenty of real-world examples from the last 10-years alone, including:
- A ransomware attack on Taiwan oil and gas infrastructure caused disruptions in early 2020
- Power Grid breaches in the US, Ukraine, and more since 2014
- Attacks aimed at poisoning the water supplies in the US and Israel over the last year
- A dam in New York was hacked with the potential to kill US citizens with a flood
- Hospitals across Ireland were crippled by a ransomware attack on the Irish health service.
In short, cybersecurity professionals have been aware of the significant potential for even life-or-death consequences of cyberattacks on infrastructure, in healthcare, and other areas of modern life. And to prepare for when (not if) it will happen to us, cybersecurity professionals try to learn from others who have gone through this experience.
So let’s see what we can learn from the Colonial Pipeline breach.
How to respond to a breach
It has long been an accepted reality that, while avoiding a breach is ideal, it will happen. So it is surprising how many companies still get their response wrong. And while the Colonial Pipeline response has not been perfect, they have done a few things right that many organizations do not.
First, they made the hard choice to shut down services to avoid a potentially bigger impact later.  It will be fascinating to learn about the Colonial process that allowed them to reach an agreement on such a dramatic and costly decision so quickly. But, clearly, decision-makers wisely refused to rely on crossing their fingers to slow down the spread of ransomware. (A time-honored management practice, often followed by finger-pointing and buck-passing.)
It will be fascinating to learn about the Colonial process that allowed them to reach an agreement on such a dramatic and costly decision so quickly. But, clearly, decision-makers wisely refused to rely on crossing their fingers to slow down the spread of ransomware. (A time-honored management practice, often followed by finger-pointing and buck-passing.)
This is even more startling because they claim that the ransomware was found on Colonial’s ‘business systems’, and the shutdown was done to protect the systems used to ‘control and operate the pipeline’, even though they are likely segmented. For security professionals, that makes sense because we understand how these things can spread. So it was a refreshingly aggressive decision by Colonial to shut down the pipeline control and operation-related systems primarily as a preventive measure.
Second, communications about the incident have been fairly proactive and reasonably transparent. Working with all the right authorities, Colonial appears to have only filtered or delayed information in cooperation with those authorities. Initial reports indicated a ransomware attack, a few more details came out in the first few days, and the FBI produced a fact-filled “Flash Alert” within a few days providing IoCs and other details about the attack.
Sorry, we’ll do better in the future!
The DarkSide (the ransomware used in the Colonial Pipeline attack) cybercrime group is not shy about getting coverage as they sent out a press release to introduce themselves in August of 2020. But, while most ransomware attacks are designed to cause enough fear or pain that the victim becomes willing to pay an exorbitant ransom, the DarkSide group seems to feel they have gone too far, so they recently issued an apology. Their apology is ironically similar to those issued by politicians and corporations who get caught doing something unpopular or illegal. It includes the apology and a commitment to do a better job in the future, which is scary in its professionalism.
But this raises a question that may teach us the most from this situation. Why did the people behind DarkSide feel a need to so quickly issue such a public apology, with a commitment not to cause such a public disruption in the future?
The answer is simple. Fear.
In this specific case, we see the President of the United States has become directly involved in responding to the attack and bringing the full weight of the US government with him.  While there are always law enforcement efforts to curb cybercrime, this amount of attention puts DarkSide on the top of the wanted list! And it means that allies are more likely to make DarkSide a law enforcement priority as well, which means extraordinarily high levels of international coordination to find and shut down DarkSide.
While there are always law enforcement efforts to curb cybercrime, this amount of attention puts DarkSide on the top of the wanted list! And it means that allies are more likely to make DarkSide a law enforcement priority as well, which means extraordinarily high levels of international coordination to find and shut down DarkSide.
The need for better global law enforcement
Don’t let the section title fool you. We are all about the need to continually review and uplift our security skills, tools, and best practices. But all of our combined efforts as cybersecurity professionals are only keeping pace with cybercrime. It might be nice if someone could shut down these attacks at the source, the threat actors.
So, ignoring those attacks rumored or suspected to be nation-state sponsored, consider all the attacks over the last decade tied to cybercriminal organizations based in countries like Russia, China, North Korea, and Iran. Now try to think of an example of a cybercrime group operating in those countries who were caught and prosecuted for offenses they committed outside of those countries. (Spoiler: The list will be short or blank.)
This is due to some common principles used by organizations, like DarkSide, to reduce their risk of being caught. Beyond the technology used to make it hard to trace the attacks or the ransom, these include:
- Operate from a country that is less likely to cooperate with extradition and similar requests.
- Avoid attacking victims within the country you operate from.
- Avoid doing anything, anywhere, that impacts the ‘interests’ of the country you operate from.
In the case of DarkSide, they even went to the effort to ensure the attacks facilitated by their ‘Ransomware-as-a-Service’ (RaaS) would avoid infecting any system where Russian was the default language.
In other words, these groups do all they can to stay off the radar of local law enforcement.  Even in a world of anywhere, anytime news, it remains human nature to prioritize the things that can happen to you or near you. This strategy makes it much more likely that local law enforcement will spend most of their time looking for local criminals who are causing problems locally. There is a clear correlation between choosing your location and your victims carefully – and remaining free.
Even in a world of anywhere, anytime news, it remains human nature to prioritize the things that can happen to you or near you. This strategy makes it much more likely that local law enforcement will spend most of their time looking for local criminals who are causing problems locally. There is a clear correlation between choosing your location and your victims carefully – and remaining free.
A wake-up call, after all?
This is where change is needed most if we are to tackle ransomware and other cyber threats at the root, the threat actors themselves. The Internet operates without borders, and effective policing of malicious behavior will require enforcement across all borders.
So, as they say, write your local representatives. They need to be reminded of how a breach affects them personally, so they are more motivated to prioritize this issue. And write to them often to remind them to keep it prioritized for more than 30 days after the Colonial Pipeline starts up again.
Actionable Next Steps
There are some things you can do to protect your organization. In the case of the Colonial Pipeline breach, there are reports that security hygiene failures were involved. So, if you haven’t done so recently, it might be time for a review and possibly some testing of your organizations’ defenses. Since DarkSide has been around for almost a year now, many of the IoCs shared by the FBI were already known.
And we wouldn’t be surprised if phishing was somehow involved in the Colonial breach since it remains the most common attack tactic, and it is not uncommon for a single user falling for a phishing email to result in a major breach. Even globally recognized security organizations have suffered from phishing attacks. So this might serve as another opportunity for user education.
DNS Security for Detecting and Blocking Ransomware activity
An attack involving DarkSide, like the vast majority of attacks, involves a great deal of internet activity.  There are the links used in email, malicious web ads, etc., where the users’ click’ will require DNS to resolve and connect to the initial point of infection. And there are plenty of subsequent communications to request/receive additional code, establish encryption keys, steal data for extra ransom pressure, provide attackers with status updates, and so on. So this might be the time to invest in DNS Security to be that crucial canary in the coal mine.
There are the links used in email, malicious web ads, etc., where the users’ click’ will require DNS to resolve and connect to the initial point of infection. And there are plenty of subsequent communications to request/receive additional code, establish encryption keys, steal data for extra ransom pressure, provide attackers with status updates, and so on. So this might be the time to invest in DNS Security to be that crucial canary in the coal mine.
Most ransomware, once inside a network, leverages DNS for C&C callbacks and to spread laterally. DarkSide is no exception, and this behavior exposes them to detection by Infoblox BloxOne Threat Defense at the DNS layer using IoCs such as those shared by the FBI and noted in an Cyber Threat Advisory from the Infoblox Cyber Intelligence Unit (CIU). Using highly accurate threat intelligence with ML/AI analytics in internal DNS servers can also detect threat activity through its malicious behavior to block those C&C communications and interrupt its activities. Threat Intelligence sharing as well as automated incident response can be coordinated throughout the rest of the security ecosystem to uplift defenses and drive network-wide remediation.
And DNS is a source of ‘truth’ that counters many evasive techniques while also providing analysts and responders with a goldmine of information to drive shorter threat investigation and faster incident response.
So the Colonial Pipeline breach may be a ‘wake up call’ for non-security professionals in regard to the potential of such a threat and may help drive some important changes at government levels. But for those in security, it is just another reminder that most breaches are a failure to use the knowledge and tools available today.
Continue to grow your teams’ skills and capabilities, make adjustments to your toolsets, and then enjoy a well-earned nap.








