The Domain Name System (DNS) is a fundamental component of the internet, with a great deal of value beyond that of a simple ‘Internet Phonebook’ as many tend to see it. Threat Actors recognize that value, leveraging DNS in many ways to carry out phishing, data theft, and other malicious activities.
High-Risk Domains

High-risk domains are a significant concern in the realm of DNS abuse. These domains, registered by threat actors, exhibit behaviors suggesting malicious intent, even before any overtly malicious activity starts. These domains often share characteristics with known malicious domains, making them difficult to detect. High-risk domains can be newly registered domains, lookalike domains, or domains that show suspicious activity patterns.
Command and Control (C2) Communication
DNS is also used by threat actors for C2 communication. By using DNS to send commands to malware installed on a victim’s machine, attackers can maintain control over the compromised system and avoid detection by most security tools that are overly HTTP(S) focused. This method is particularly effective because DNS traffic is often allowed through firewalls and other security measures unmonitored, making it a stealthy way to manage infected devices.
Leveraging Various DNS Record Types
Threat actors often leverage various DNS record types to avoid detection by security tools that only monitor select types of DNS records. For example, while many security tools focus on monitoring A (address) records, attackers might use CNAME (canonical name) records or TXT (text) records to carry out their malicious activities. By using less commonly monitored DNS record types, attackers can evade detection and maintain their malicious activity.
DNS Tunneling
DNS tunneling is a sophisticated technique where attackers often use DNS queries and responses to exfiltrate data from a compromised network. By encoding data within DNS queries, cybercriminals can bypass traditional security measures and communicate with their command and control (C2) servers. This method is often used in advanced persistent threats (APTs) and can be difficult to detect without specialized tools.
Zero-Day DNS
Another tactic used by cybercriminals is the registration of zero-day domains. These are domains that are registered and used almost immediately to launch spearphishing and other targeted attacks. Because these domains are newly registered, they often bypass traditional security measures that rely on reputation-based detection. This allows attackers to quickly and effectively carry out their attacks before the domains are flagged as malicious. (see figure 1)
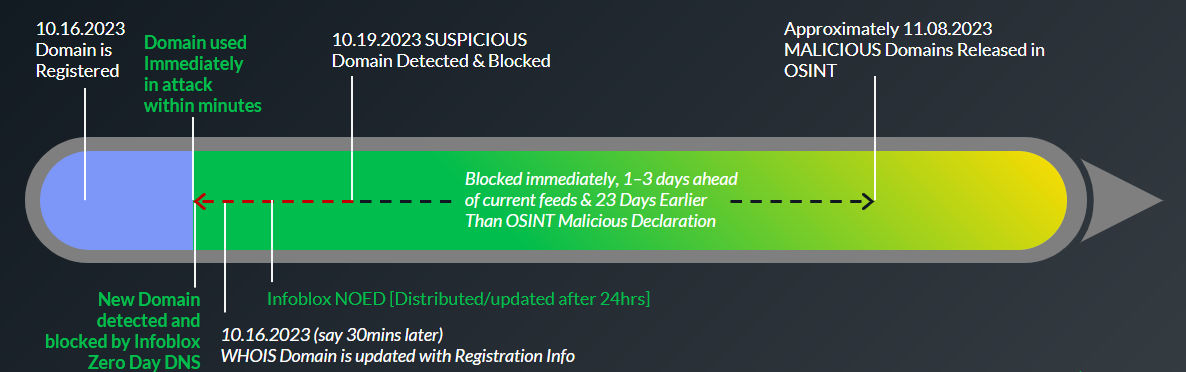
Figure 1: Threat Actors can launch attacks shortly after registering domains, using them ahead of defense updates.
Lookalike Domains
One of the most common tactics used by cybercriminals is the creation of lookalike domains. These domains are designed to closely resemble legitimate websites, often with minor misspellings or variations. For example, a threat actor might register “micros0ft.com” instead of “microsoft.com”. These lookalike domains are then used in phishing attacks to bypass defenses and trick users into revealing sensitive information such as login credentials or financial details.
Traffic Distribution Systems (TDS)
Threat actors have built massive TDSs that direct victims through a maze of domains to deliver malicious content at scale with a high degree of efficiency. If you try to block each individual end domain, the threat actors will just rotate and serve the malware a different way using thousands of other malicious domains. So, defenses need to go after the TDS infrastructure instead of individual domains to be effective. (see figure 2)
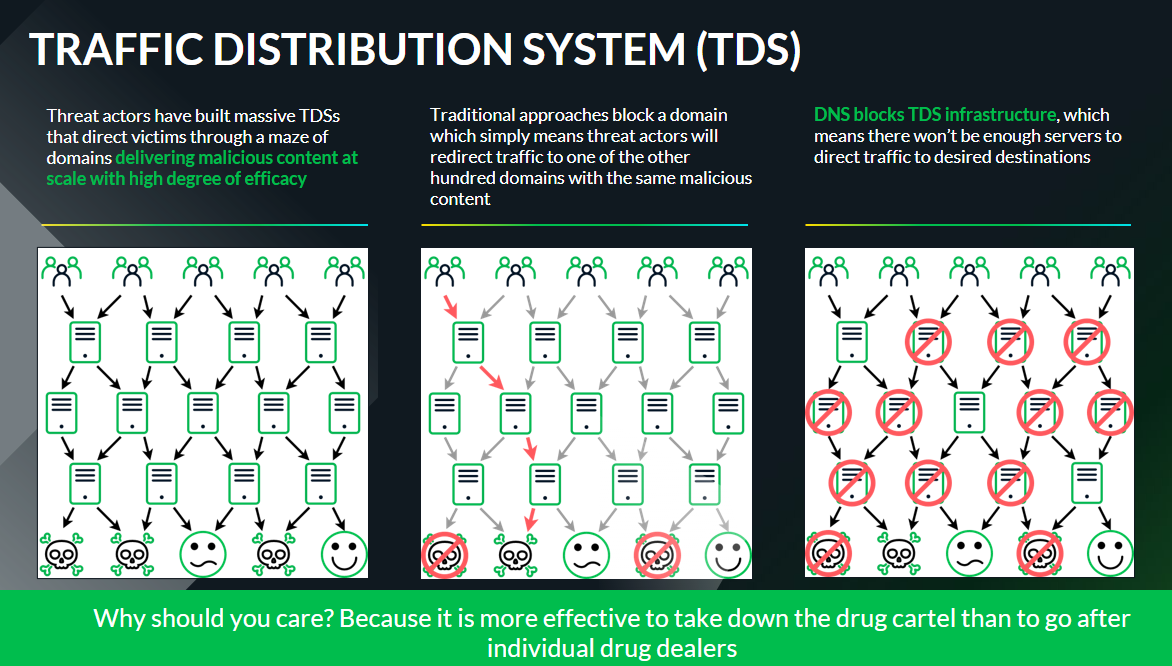
Figure 2: Threat Actors leverage massive TDS to counter traditional domain filtering defenses.
Dangling CNAMEs
A dangling CNAME is a type of DNS record that points to a domain or resource that no longer exists or is no longer controlled by the original owner. This creates a vulnerability that can be exploited by attackers to take over the subdomain and use it for malicious purposes. Dangling CNAME records can lead to domain hijacking, where attackers can redirect traffic intended for the original domain to a malicious site.
Conclusion
The abuse of DNS by threat actors could be a blind spot for cybersecurity professionals. By understanding the various ways DNS can be exploited, organizations can implement more effective security measures to protect their networks. Regular monitoring of DNS traffic, using DNS as a proactive shield against cyberthreats, and using advanced threat detection tools are essential steps in defending against these sophisticated attacks.
Sign up for a Free Security Workshop
To learn more about all the ways threat actors can abuse DNS, and how you can stay protected, sign up for a free security workshop here.