Microsoft has announced the public preview of Zero Trust DNS (ZTDNS), a new feature in Windows 11 Insider builds designed to enhance security by enforcing domain-name-based network access controls. ZTDNS integrates the Windows DNS client with trusted Protective DNS (PDNS) servers, ensuring that outbound traffic is only permitted to IP addresses resolved by these servers. This approach adheres to the “deny by default” principle of Zero Trust. Read further to understand why Zero Trust DNS is important and how PDNS can preemptively block threats.
Threat actors have an unfair advantage
Threat actors are increasingly leveraging AI to automate and accelerate cyberattacks, making them more sophisticated and harder to detect, and significantly reducing the time and effort required to execute these attacks. They also use malicious adtech that leverages traffic distribution systems (TDSs) to lure victims to malicious sites and deliver infostealer malware, that are at the heart of corporate data breaches. This rapid evolution in attack methodologies poses a significant challenge for cybersecurity professionals, who must continuously innovate to stay ahead of these AI-driven threats.
Shortcomings of Traditional Security and the Value of PDNS
Traditional security is malware centric and identifies threats after patient zero. They focus on detecting and mitigating threats after they have already been activated and after they have been executed in the system—often when the damage has already started. This approach is insufficient in the face of AI-powered cyberattacks. The “wait till the boom” mentality causes delays in threat detection, leading to continued high-profile breaches.
PDNS is a preemptive cybersecurity approach that leverages DNS-focused threat intelligence to identify and block threats before they can cause harm. It works by continuously monitoring domain registrations and DNS queries to detect high-risk domains owned by threat actors, even before those domains are weaponized and used in attacks, significantly reducing the likelihood of successful breaches. According to the NSA, DNS can block 92 percent of malware attacks, meaning PDNS can intercept threats earlier in the chain, at the intent to communicate, and reduce the burden on downstream security devices.
Benefits of PDNS include:
- Preventing initial infection by refusing to resolve domains that are high risk or malicious
- Stopping ongoing command-and-control (C2) communications
- Blocking data exfiltration via DNS
Zero Trust DNS
Organizations are adopting Zero Trust as a way to get ahead of threat actors. A Zero Trust approach can greatly reduce the likelihood of a breach and if an initial breach does happen, it can limit the scope and impact of the breach. General Zero Trust principles include:
- Assuming a breach mindset
- Never trusting, always verifying
- Using a least-privilege approach
- Constant monitoring
- Ensuring segmentation
But Zero Trust is not really zero trust if you are implicitly trusting your DNS.
DNS has a very important role to play in trust and security. For example:
- From a never-trust-always-verify perspective, you should ensure that your DNS is not resolving any request to a high-risk or malicious domain. In addition, you should use encryption and authentication to ensure trusted connection to a DNS server.
- From a constant monitoring perspective, you should monitor your DNS traffic for data exfiltration, DGAs and zero-day DNS threats.
This is where PDNS comes in. Microsoft, with its latest announcement of its public preview of Zero Trust DNS, validates this approach. With Microsoft’s ZTDNS, the Windows DNS client forces the use of encrypted DNS and ensures queries are only sent to the configured PDNS servers. Outbound traffic is permitted only to IP addresses resolved by these trusted PDNS servers with some exceptions. This approach helps mitigate threats, such as DNS hijacking, malicious communications, data exfiltration and more.
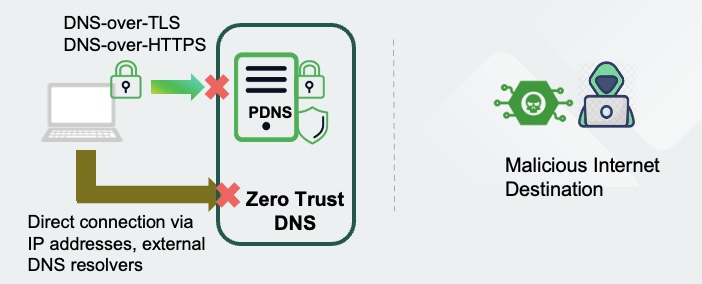
Infoblox Threat Defense™ is an industry-leading PDNS solution that uses predictive DNS-focused threat intelligence and algorithmic detections to block cyberthreats preemptively across an organization’s entire hybrid, multi-cloud environment. Infoblox blocks threats on an average 63 days earlier than the rest of the industry, blocks 75.4 percent of threats even before the first DNS query goes out and has an ultra-low false positive rate of 0.0002 percent.
Sign Up for a Free Security Workshop
To learn more about Zero Trust and all the ways threat actors can abuse DNS, sign up for a free security workshop here.









